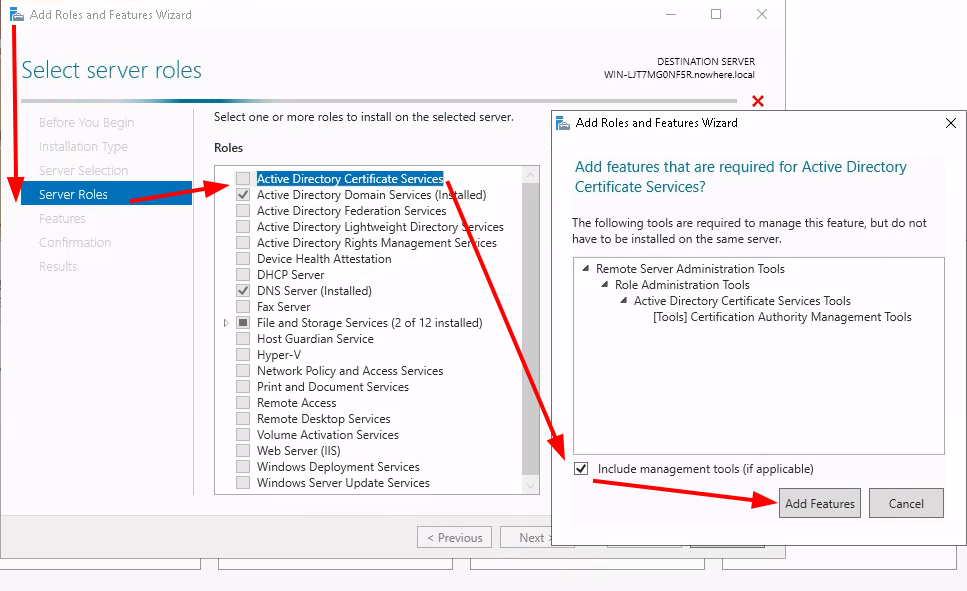
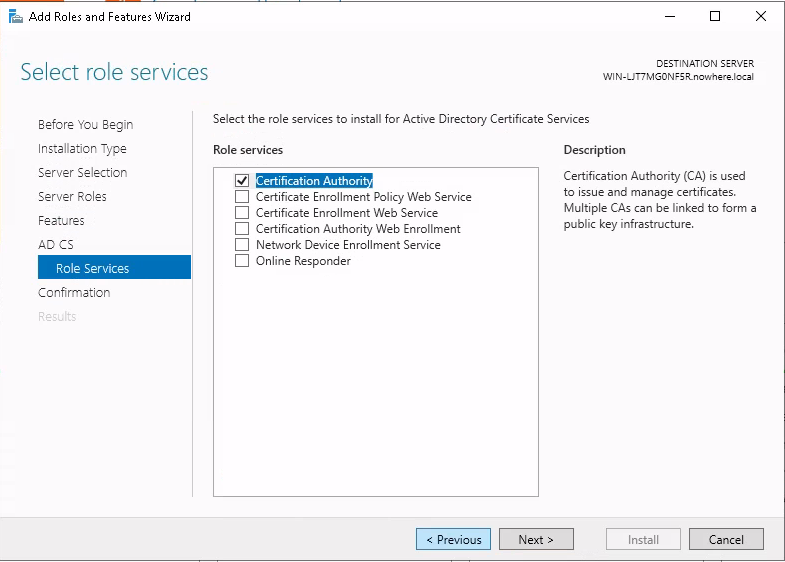
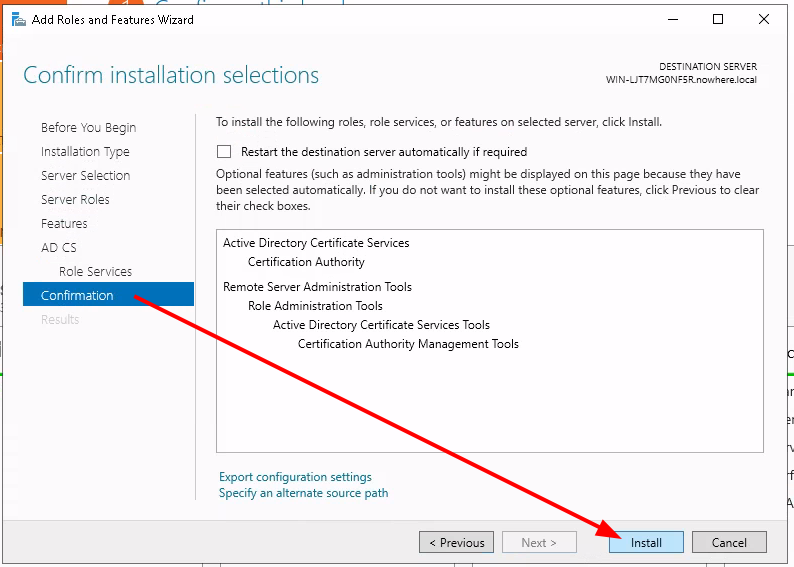
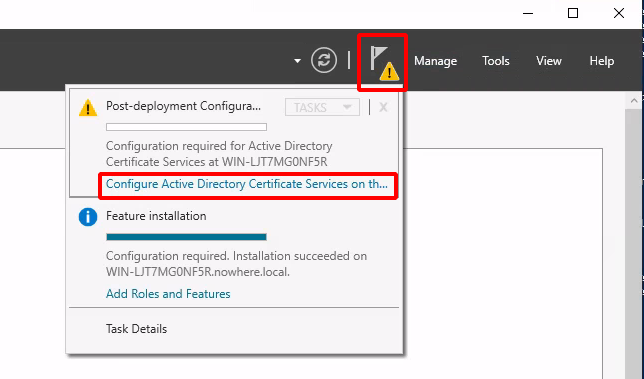
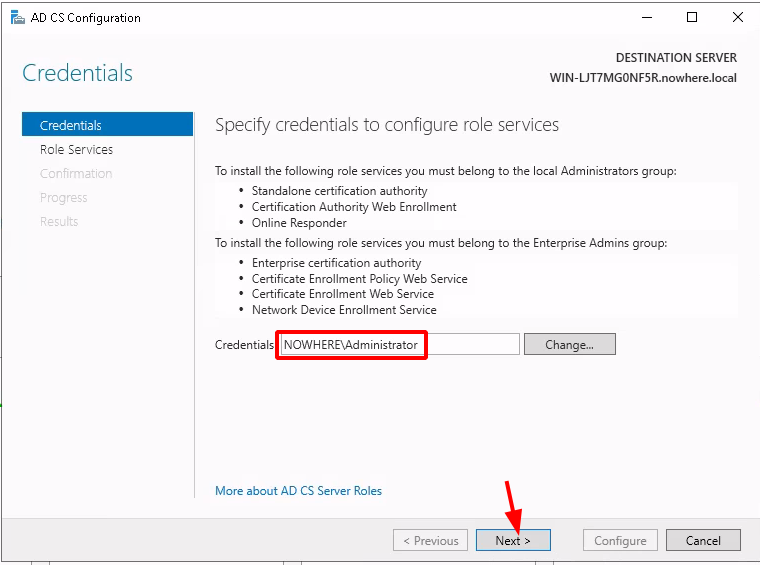
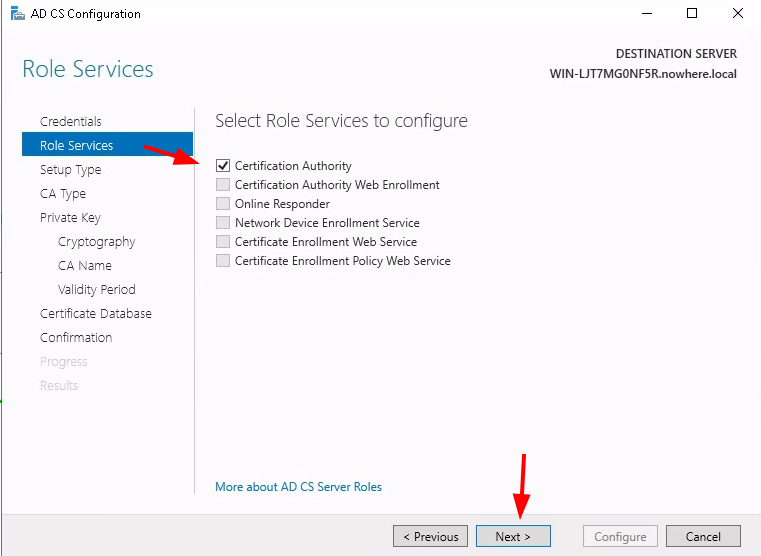
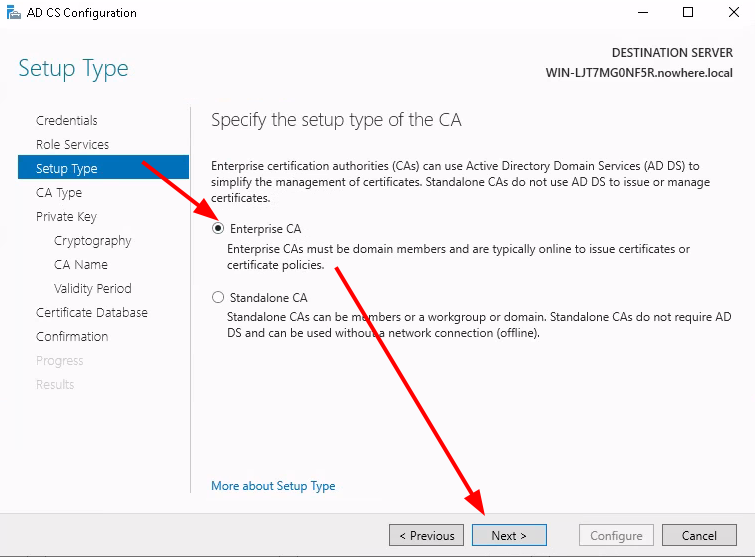
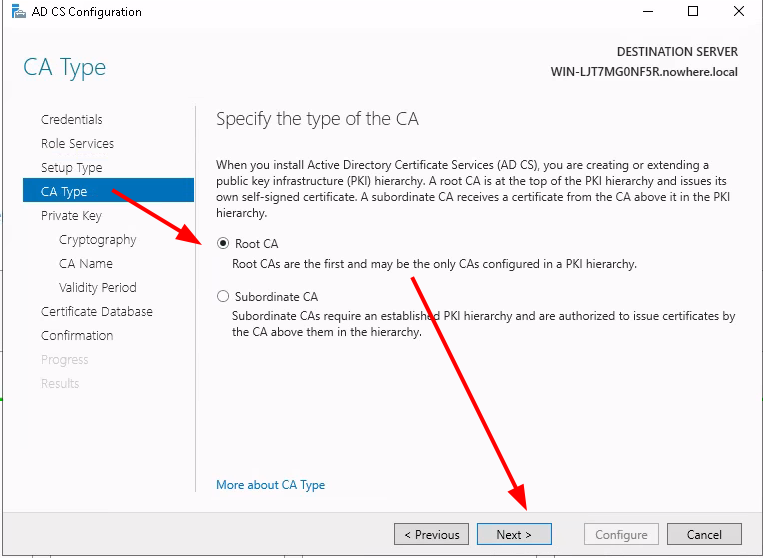
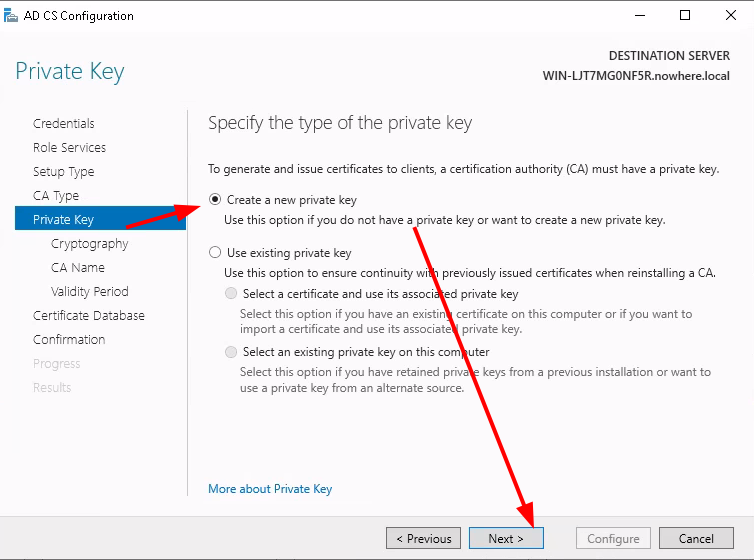
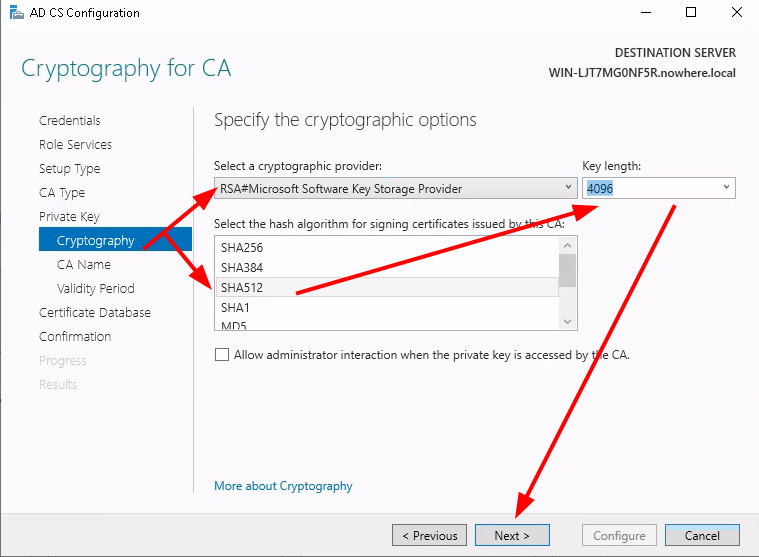
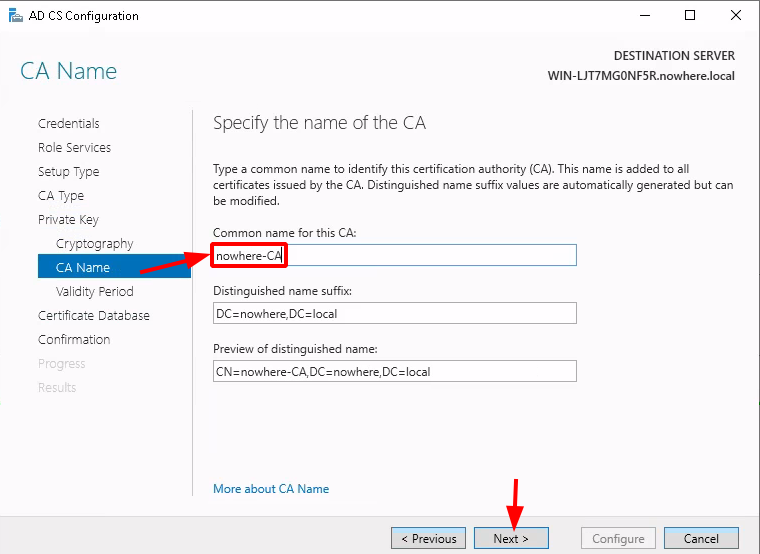
Testing the LDAPS connection
However most importantly we need to check if other hosts on the local network can see the new certificate correctly, so before we check that, let's check if we can check our own certificate from the windows server host:
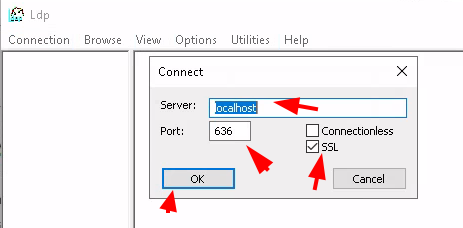
So we are able to see our own LDAPS SSL certificate:
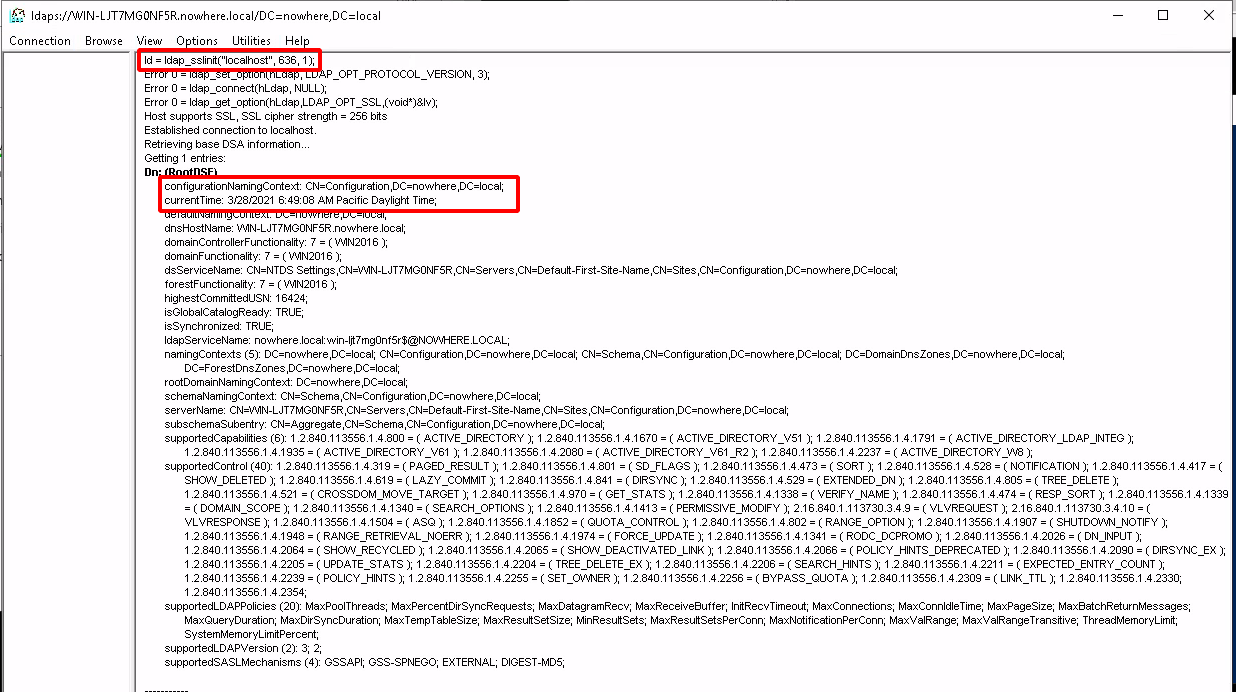
So now we need to stee if pfsense can see the ldaps SSL certificate:
To do so we can use the 'ldapsearch' tool available in the openldap package :
[ 10.0.0.10/16 ] [ /dev/pts/45 ] [~]
→ sudo pacman -S openldap
[sudo] password for nothing:
resolving dependencies...
looking for conflicting packages...
Package (1) New Version Net Change Download Size
core/openldap 2.4.57-1 4.15 MiB 1.42 MiB
Total Download Size: 1.42 MiB
Total Installed Size: 4.15 MiB
:: Proceed with installation? [Y/n] y
[ 10.0.0.10/16 ] [ /dev/pts/45 ] [~]
→ which ldapsearch
/usr/bin/ldapsearch
[ 10.0.0.10/16 ] [ /dev/pts/45 ] [~]
→ openssl s_client -showcerts -connect 10.0.0.204:636
CONNECTED(00000003)
Can't use SSL_get_servername
depth=0 CN = WIN-LJT7MG0NF5R.nowhere.local
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN = WIN-LJT7MG0NF5R.nowhere.local
verify error:num=21:unable to verify the first certificate
verify return:1
depth=0 CN = WIN-LJT7MG0NF5R.nowhere.local
verify return:1
---
Certificate chain
0 s:CN = WIN-LJT7MG0NF5R.nowhere.local
i:DC = local, DC = nowhere, CN = nowhere-CA
-----BEGIN CERTIFICATE-----
MIIG+zCCBOOgAwIBAgITVQAAAAKR6/iCOHueEQAAAAAAAjANBgkqhkiG9w0BAQ0F
ADBFMRUwEwYKCZImiZPyLGQBGRYFbG9jYWwxFzAVBgoJkiaJk/IsZAEZFgdub3do
ZXJlMRMwEQYDVQQDEwpub3doZXJlLUNBMB4XDTIxMDMyODEzMzMxM1oXDTIyMDMy
ODEzMzMxM1owKDEmMCQGA1UEAxMdV0lOLUxKVDdNRzBORjVSLm5vd2hlcmUubG9j
YWwwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCRQ0d8ZYEYy8es0Dix
6UDS8fwRRmhZ+TsBRIy8bwrwWYukcRxxo/Vijk1olvi3qS3nK6mZmT25g9zTHbPF
WalPVWtiZqQUL1dg9FBuzWHTD4+7uXa8KTy6I8ICa9GgfFleP1LzncKPJ/UYtEpT
MioQfOXz5XmAZqgVIFx3onkdVM9XHYt6T9mnOJMw/JiE9o54z64PCGg/IxcA7ZYV
lpMdIWhuO92sjhzJ8BEcyLvVrJjpPwlbQ0w46k35KY/j3oOrP01UEw6x+4teuiwn
bPo72GJQjP9qvKDj9H6sh4bSaue8wA39OlqT5eCYL57kxmIOJ0hSRWC9jIFJlyPK
GGLVAgMBAAGjggL/MIIC+zAvBgkrBgEEAYI3FAIEIh4gAEQAbwBtAGEAaQBuAEMA
bwBuAHQAcgBvAGwAbABlAHIwHQYDVR0lBBYwFAYIKwYBBQUHAwIGCCsGAQUFBwMB
MA4GA1UdDwEB/wQEAwIFoDB4BgkqhkiG9w0BCQ8EazBpMA4GCCqGSIb3DQMCAgIA
gDAOBggqhkiG9w0DBAICAIAwCwYJYIZIAWUDBAEqMAsGCWCGSAFlAwQBLTALBglg
hkgBZQMEAQIwCwYJYIZIAWUDBAEFMAcGBSsOAwIHMAoGCCqGSIb3DQMHMB0GA1Ud
DgQWBBSr+hTuXL/n4V7mTbXcKgPUQmvA8zAfBgNVHSMEGDAWgBQ1GNjpvSPea8eP
2DJGHHpmXOz7PTCB0gYDVR0fBIHKMIHHMIHEoIHBoIG+hoG7bGRhcDovLy9DTj1u
b3doZXJlLUNBLENOPVdJTi1MSlQ3TUcwTkY1UixDTj1DRFAsQ049UHVibGljJTIw
S2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz1u
b3doZXJlLERDPWxvY2FsP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9v
YmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBvgYIKwYBBQUHAQEEgbEw
ga4wgasGCCsGAQUFBzAChoGebGRhcDovLy9DTj1ub3doZXJlLUNBLENOPUFJQSxD
Tj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1
cmF0aW9uLERDPW5vd2hlcmUsREM9bG9jYWw/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29i
amVjdENsYXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwSQYDVR0RBEIwQKAfBgkr
BgEEAYI3GQGgEgQQxn6cUfiuyUaEppT8x7iyk4IdV0lOLUxKVDdNRzBORjVSLm5v
d2hlcmUubG9jYWwwDQYJKoZIhvcNAQENBQADggIBAKMGBpS4aAAAaTdn7CJnRnaD
jpWDnhO0PBisnOi1xQ/BZv6rqoglLlRSxXEQUSJKbpDPO46/vmQC0TA95fen9SW2
tWRfWgq6QjnhBiHR9CrJtnZEx+NrDEx93SLWFX4uC5MdEtuVZdE6yaWmMBaz4X+6
300BvF9hkTY5EWnb/jLtFqm3JhuXX9C5n6Z/3uVfq6RZCkw546Fh26f60Sz3J/c+
2f3YggzflgAsP5KiApfhzLdpTHG53o7nuO4KJHKC1NL03Swd2DV/sFwyLvK8jxlZ
r1BhU/8kWXwdof5qHGiSbLBaTVqF0sIoowNKsA2zY9NI3kaPGTHGfl3K7yuF/u5D
7vpR0x1eBrV5sYOcM0pVwQU5BkghwQ3CF+Opz+WLGCSnyfpxiAVWfKHfb3h4X6X+
2ZCXuBdoGvHIYOxlrYt1B+HN2PPgoWo9GHtjG/5cLvO6GrDk3LID+/CfRcXZ7ec/
yl0BDrTAhjJgvRtGOkalEa8tASdDpvqNPaC2oNdiIpL51y0UPlpJzaHpmBLhw134
gbqDMCUQcmGezs5jKv0COSj49VEGGqwn+jkuNfUd77Z2uj+o9+nyanbVebegt0ha
HI9ABZer/1lGSE8IQu/bu36eRyXvy1SkKEtnvep7gi2Jea0ehWMqHnaB+8nTIEAn
7+Ple+iGS+2VPDYt/Nkg
-----END CERTIFICATE-----
---
Server certificate
subject=CN = WIN-LJT7MG0NF5R.nowhere.local
issuer=DC = local, DC = nowhere, CN = nowhere-CA
---
No client certificate CA names sent
Client Certificate Types: RSA sign, DSA sign, ECDSA sign
Requested Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Shared Requested Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: ECDH, P-384, 384 bits
---
SSL handshake has read 2341 bytes and written 463 bytes
Verification error: unable to verify the first certificate
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 6C380000DE31D09F82EC8C531A3EC2F49F690C7DD3729D1678B2399207149AC4
Session-ID-ctx:
Master-Key: 9581A15DB6A1D6FC3EF0D114B9FF19AE73E3676493EB75738BD1A81A310F6C391D0FB1354A61668ED33E9D9590F3BE65
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1616939581
Timeout : 7200 (sec)
Verify return code: 21 (unable to verify the first certificate)
Extended master secret: yes
---
And that's it! We have been able to setup the LDAPS protocol on Windows Server 2019