
tpot Setup

Tpot is a All In One Honeypot Platform, it comes with pre-built ISOs ready to run inside of a VM. You need 8GB of ram, 128Gb disk space, and DHCP Networking. I'm going to set it up on my proxmox server:


Tpot is a All In One Honeypot Platform, it comes with pre-built ISOs ready to run inside of a VM. You need 8GB of ram, 128Gb disk space, and DHCP Networking. I'm going to set it up on my proxmox server:
Get the latest ISO of tpot onto the server, then create the VM with those specs:
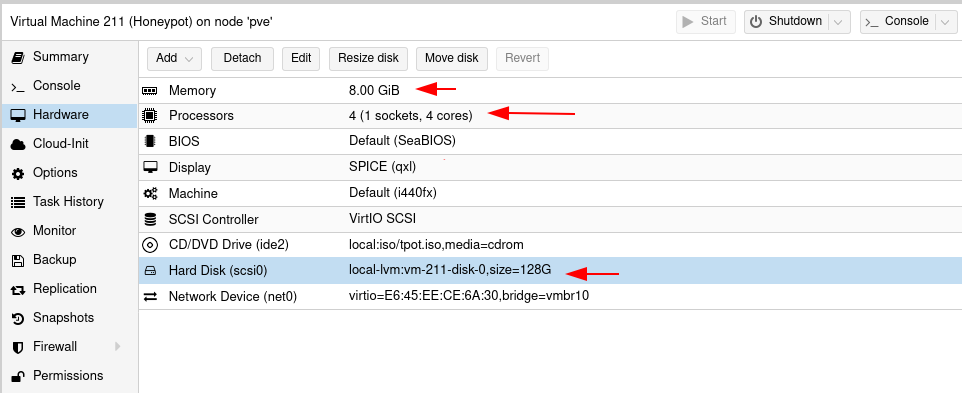
Then use the VNC or SPICE console to interact with your VM, simply install it like you would install a debian VM, Then let it reboot, as the tpot VM is going to download evertything it needs:

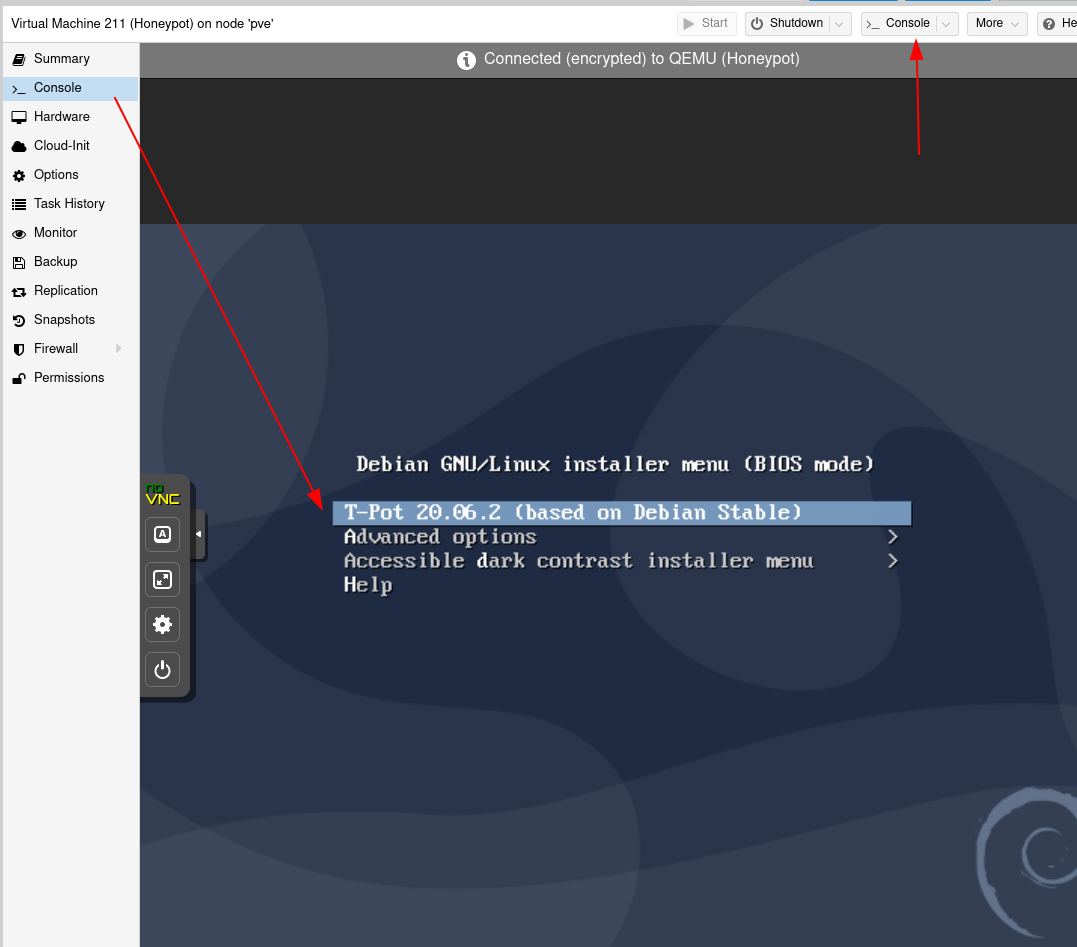
Once it's done installing, it will reboot and prompt you what follows:
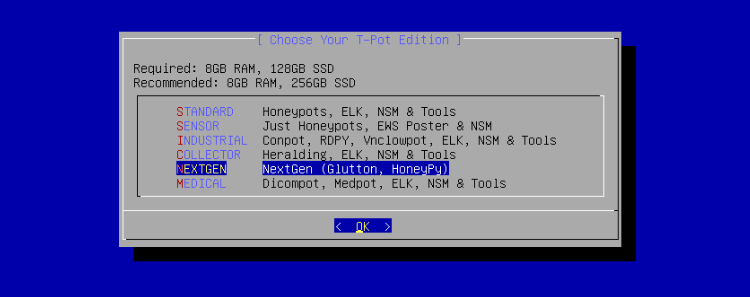
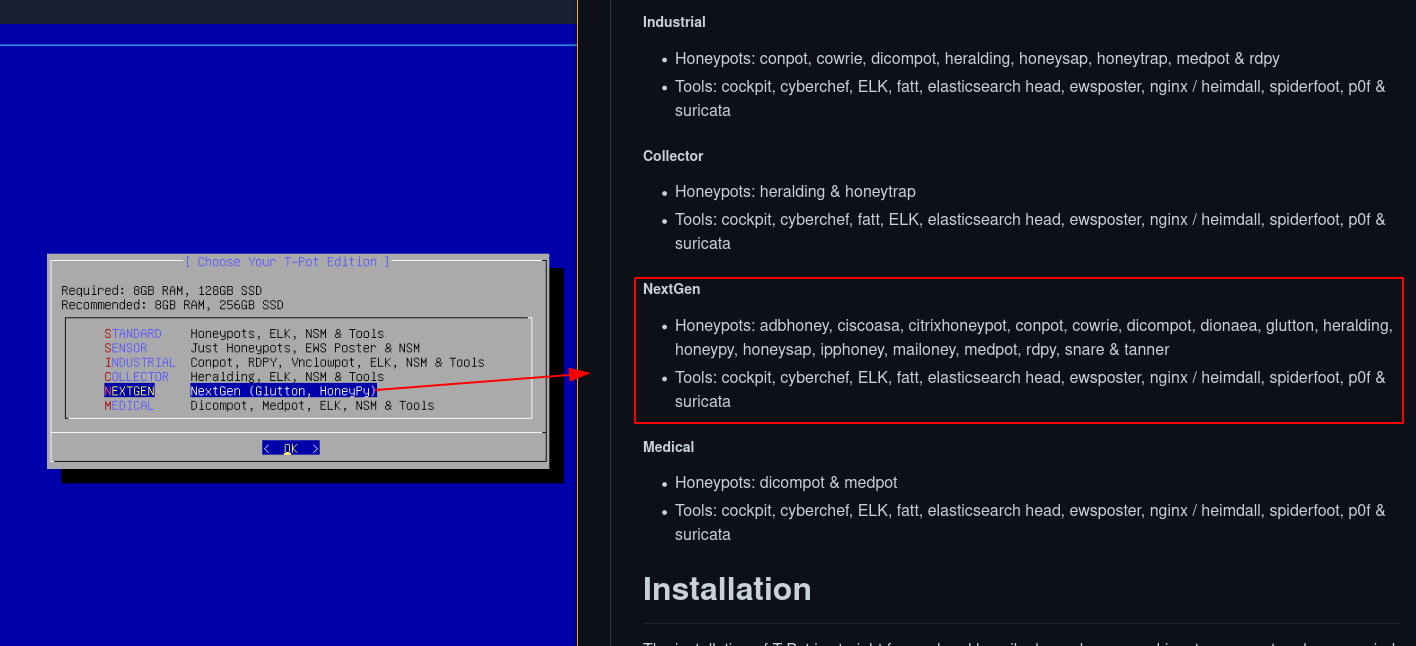
We're going to pick the NextGen one, then hit 'Ok', then it will ask you to create a user with a password, once that's done, Tpot is going to install it's dependencies:
(It can take up to 30 minutes)
Once it finished, you get the following result:
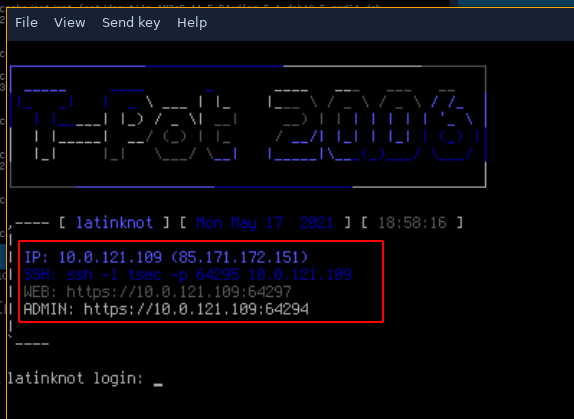
The vulnerable website is a wordpress default instance:
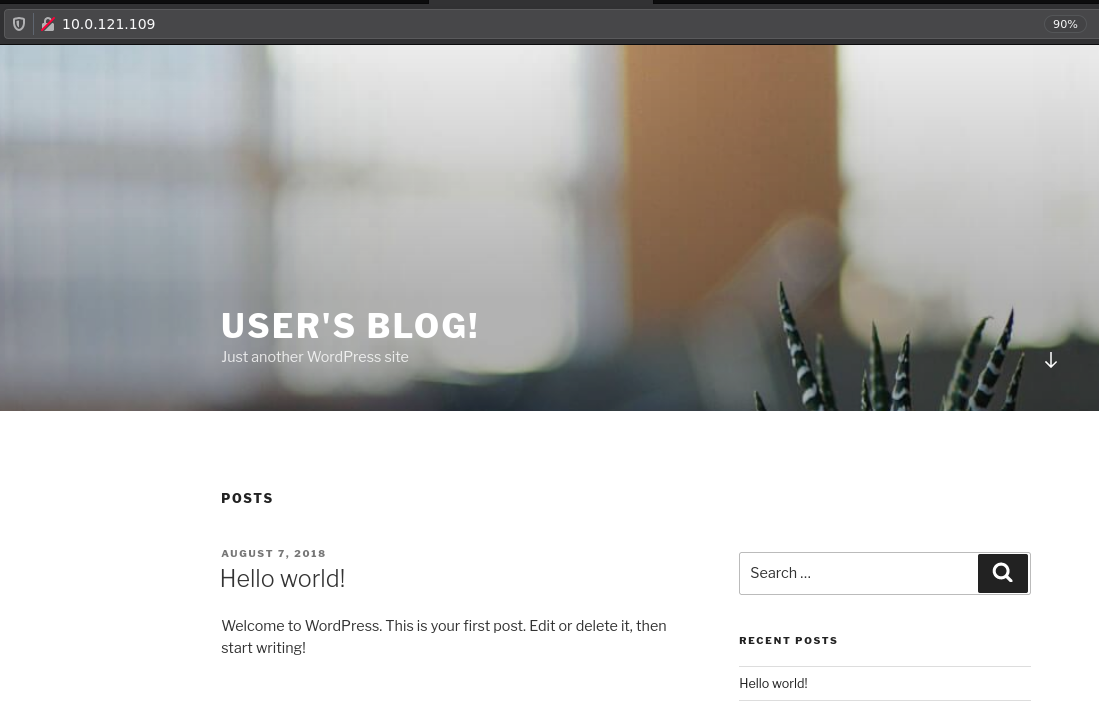
So let's take a look at the Web interface at port 64297, you need to use the user credentials you setup earlier:
Let's take a look at the Kibana interface:
Let's take a look at the TPot Dashboard:
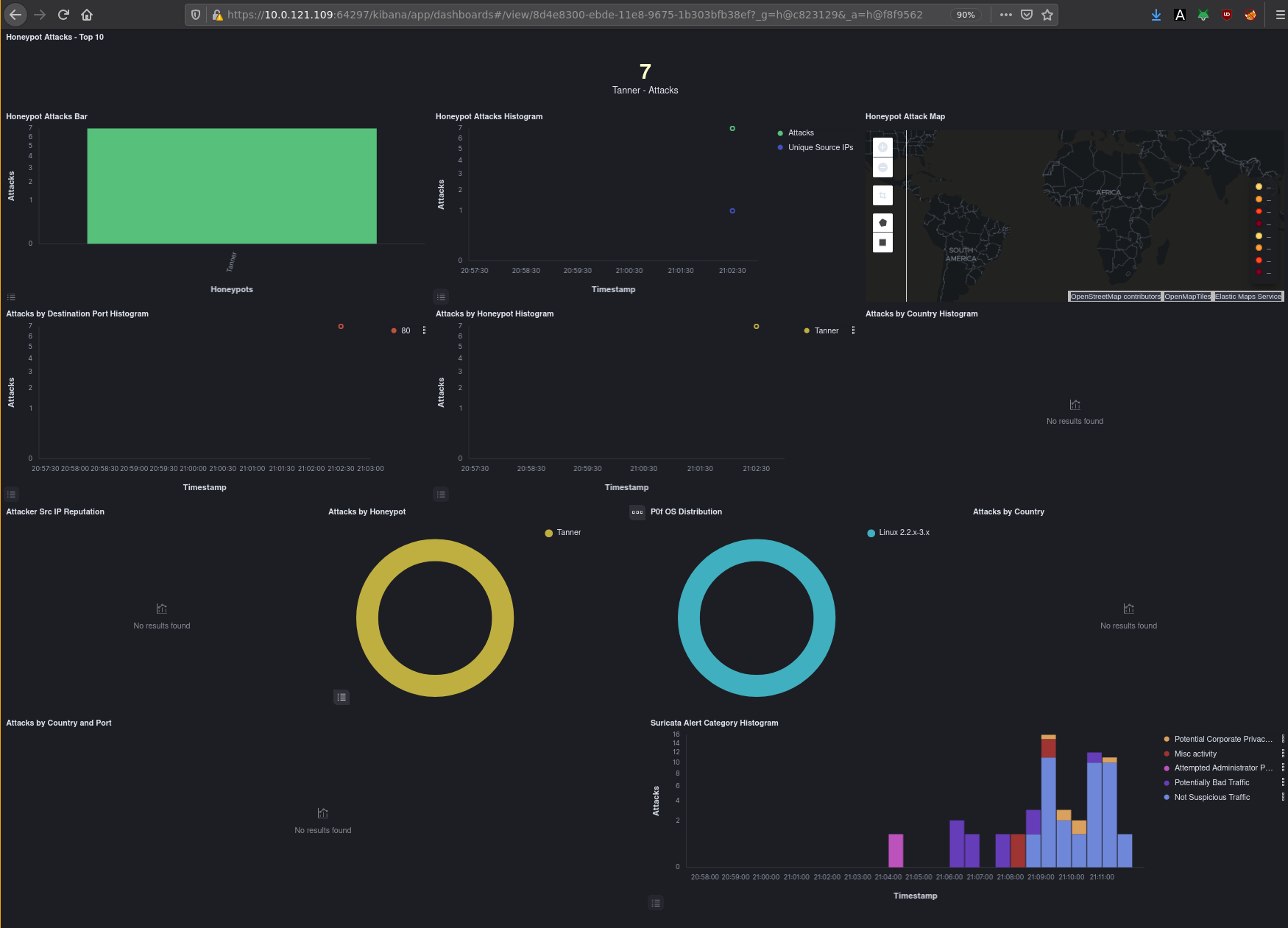
Not much there obviously, so let's run an intense directory scan to see the difference:
[ 10.0.0.10/16 ] [ /dev/pts/14 ] [Documents/Github/blog]
→ dirsearch -u http://10.0.121.109 -e html,txt,php,js,css -t 50 -x 500
/usr/lib/dirsearch/thirdparty/requests/__init__.py:91: RequestsDependencyWarning: urllib3 (1.26.4) or chardet (4.0.0) doesn't match a supported version!
warnings.warn("urllib3 ({}) or chardet ({}) doesn't match a supported "
_|. _ _ _ _ _ _|_ v0.4.1
(_||| _) (/_(_|| (_| )
Extensions: html, txt, php, js, css | HTTP method: GET | Threads: 50 | Wordlist size: 10863
Error Log: /home/nothing/.dirsearch/logs/errors-21-05-17_21-18-18.log
Target: http://10.0.121.109/
Output File: /home/nothing/.dirsearch/reports/10.0.121.109/_21-05-17_21-18-18.txt
[21:18:18] Starting:
[21:18:58] 200 - 37B - /admin/portalcollect.php?f=http://xxx&t=js
[21:19:26] 200 - 37B - /getfiles.php?f=http://xxx&t=js
[21:19:28] 200 - 51KB - /index.html
[21:19:46] 200 - 37B - /proxy.stream?origin=https://google.com
[21:20:04] 200 - 2KB - /wp-login.php
[21:20:04] 200 - 42B - /xmlrpc.php
Task Completed
let's also run simple vulnerability scans using nmap and nikto:
[ 10.0.0.10/16 ] [ /dev/pts/20 ] [Documents/Github/blog]
→ nmap -sCV -p 80 10.0.121.109
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-17 21:21 CEST
Nmap scan report for 10.0.121.109
Host is up (0.0018s latency).
PORT STATE SERVICE VERSION
80/tcp open http aiohttp 3.4.4 (Python 3.7)
|_http-server-header: Python/3.7 aiohttp/3.4.4
|_http-title: user's Blog! \xE2\x80\x93 Just another WordPress site
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.94 seconds
[ 10.0.0.10/16 ] [ /dev/pts/20 ] [Documents/Github/blog]
→ nikto -h http://10.0.121.109
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.0.121.109
+ Target Hostname: 10.0.121.109
+ Target Port: 80
+ Start Time: 2021-05-17 21:26:42 (GMT2)
---------------------------------------------------------------------------
+ Server: Python/3.7 aiohttp/3.4.4
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie sess_uuid created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-27487: Apache is vulnerable to XSS via the Expect header
[...]
+ OSVDB-35935: /rpc.php?q=\">
+ OSVDB-3092: /xmlrpc.php: xm
+ OSVDB-34879: /jsp-examples/
+ OSVDB-34878: /jsp-examples/
+ OSVDB-12721: /jsp-examples/
[...]
Run it yourself, you're going to see nikto find a trillion different vulnerabilities with this wordpress website. Now let's take a look at our dashboard once we finished running the scans:
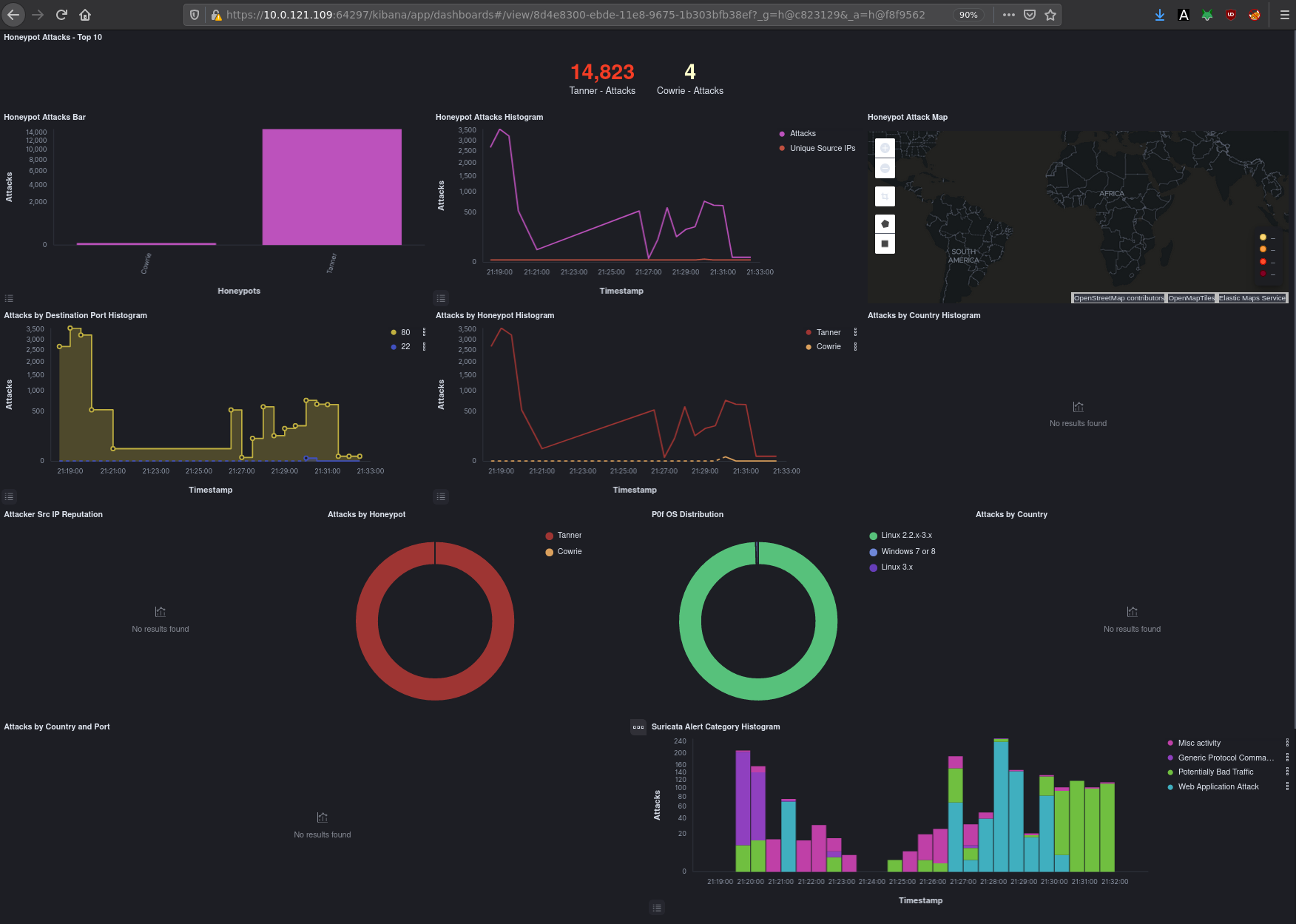
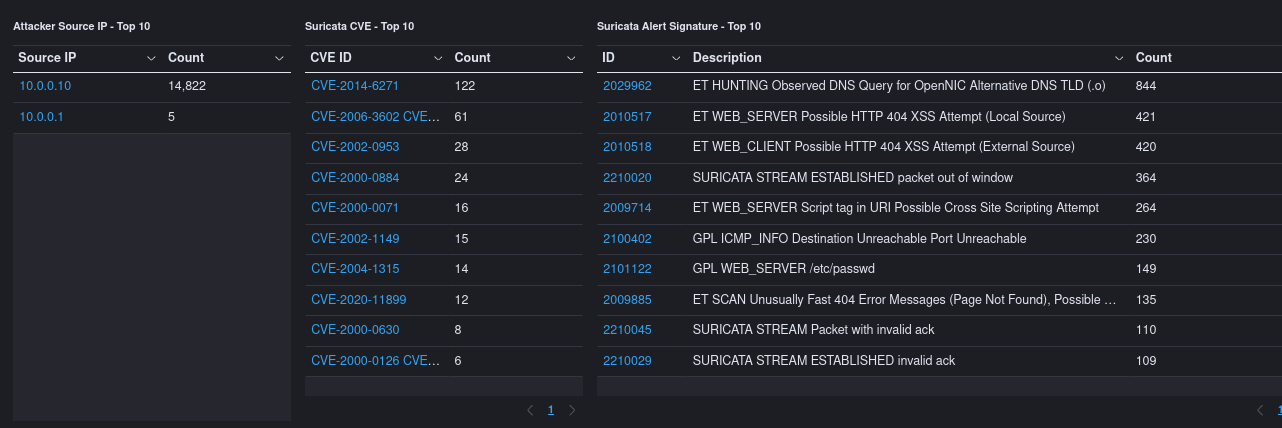
And that's it! We have been able to see a scanning attack on our honeypot TPot dashboard. Now we know that the 10.0.0.10 IP is doing malicious activities on the network. If we wanted, we could also port forward our honeypot's port 80 towards the internet, so that we could see the public IPs that are maliciously scanning us.
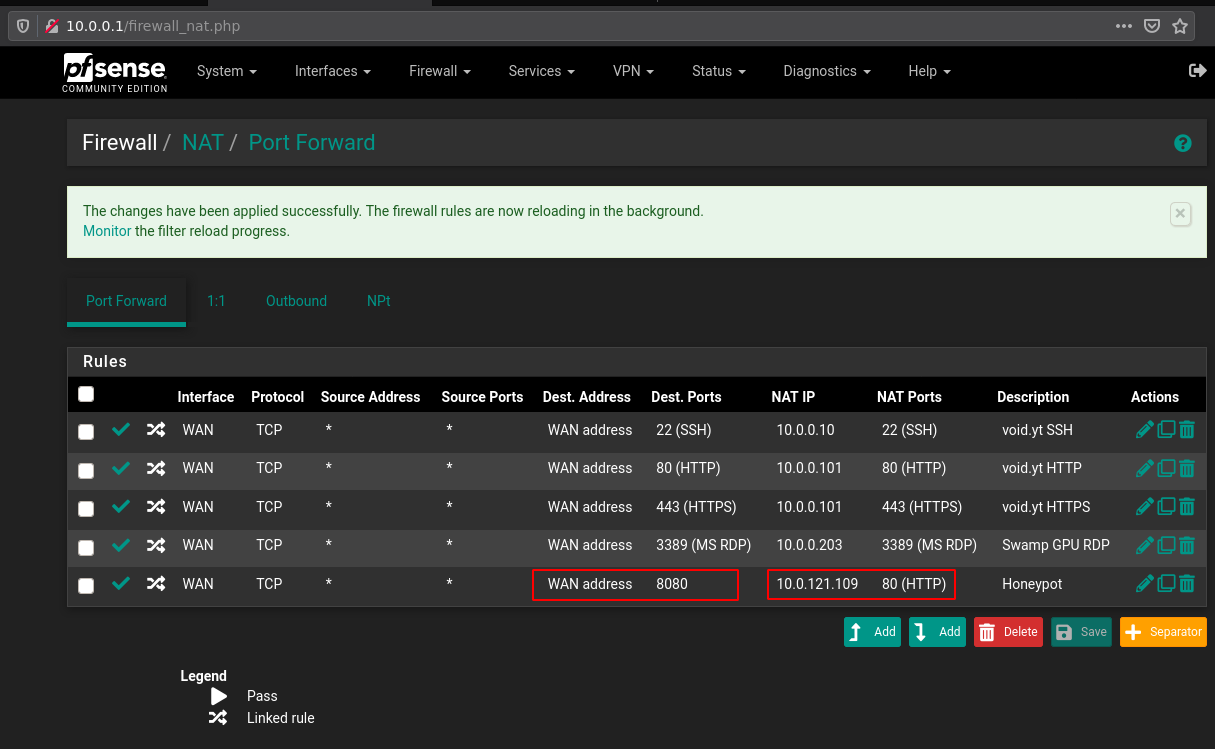
Once you do this and open up the port publicly you can immediately see changes on the TPot Dashboard:
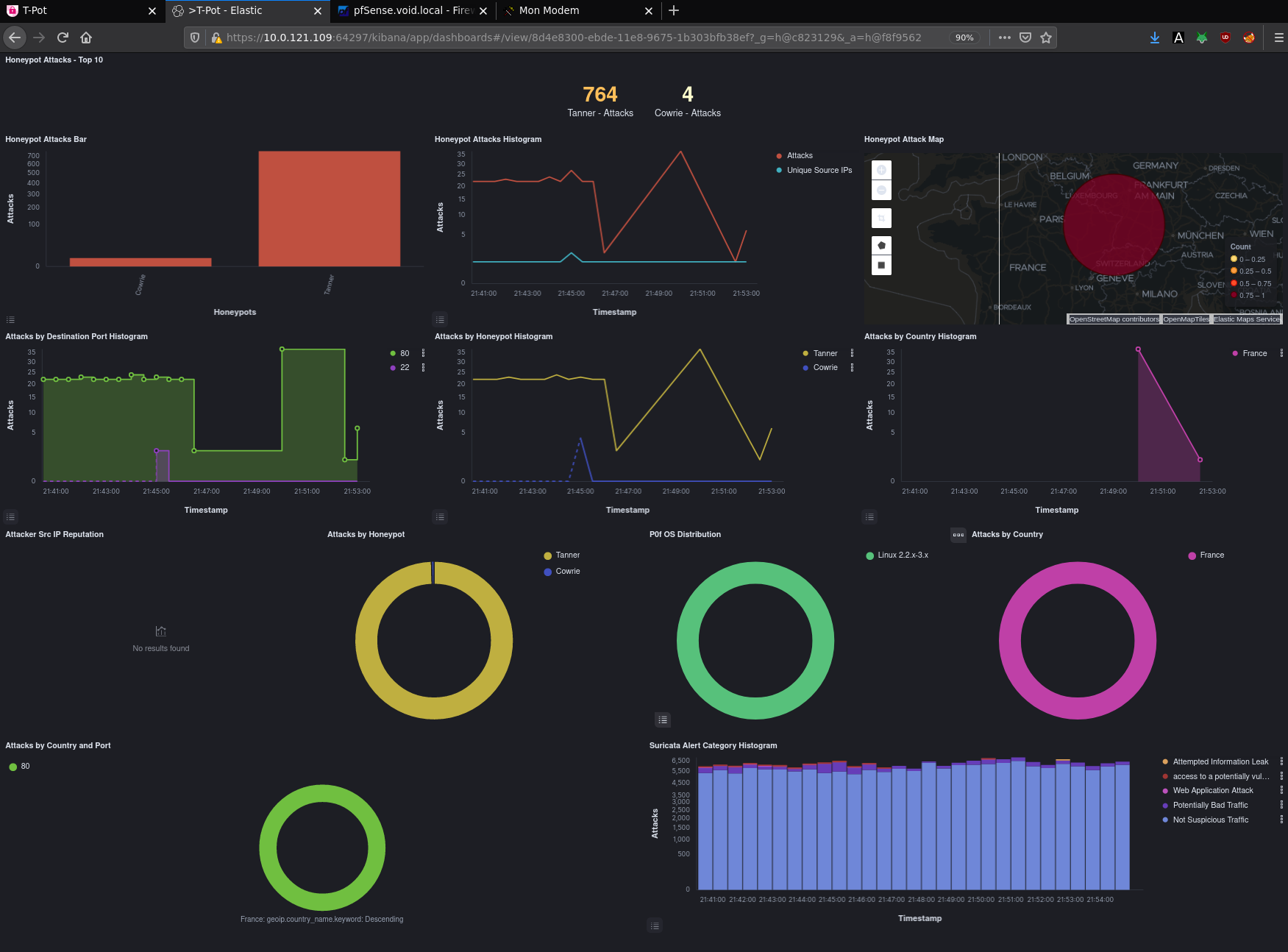
As the attacks now come from public IPs, the dashboard can tell you the geological origin of the attacks.
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.