
Installing Etherpad behind a nginx reverse proxy


apt install nodejs git npm -y
cd /srv
git clone --branch master https://github.com/ether/etherpad-lite.git
cd etherpad-lite
wget https://ech1.github.io/blog/servers/etherpad/etherpad.service -O /etc/systemd/system/etherpad.service
now since you can't run the server as root for the first time, we create an etherpad user:
adduser etherpad
cd /srv/etherpad-lite
chown etherpad. -R .
apt install sudo -y
usermod -aG sudo etherpad
sudo -u etherpad /srv/etherpad-lite/src/bin/run.sh
systemctl daemon-reload
systemctl enable --now etherpad
systemctl status etherpad
And that's it ! you should be able to access your etherpad instance on port 9001.
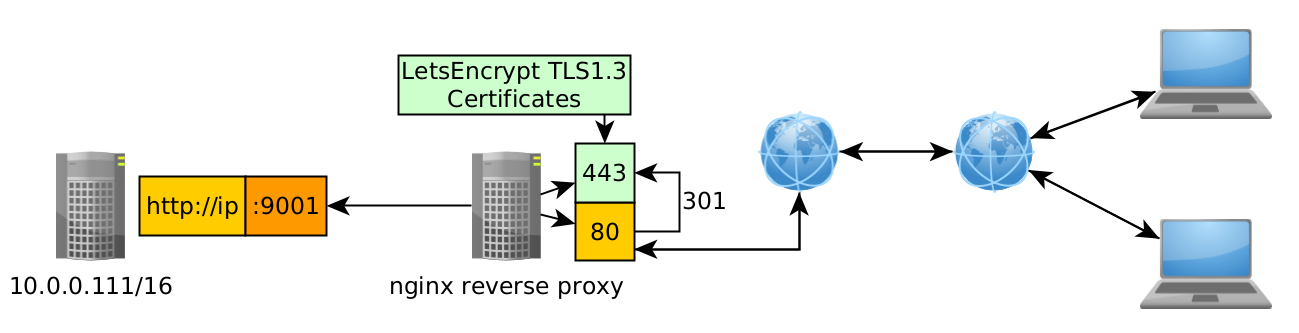
From there, you can setup your reverse nginx proxy, it can either be on the server itself or it can be on another machine in the same network:
root@etherpad:/srv/etherpad-lite# ip a | grep inet
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
inet 10.0.0.111/16 brd 10.0.255.255 scope global eth0
inet6 fe80::44ed:6ff:fef6:77a/64 scope link
For example here my debian host is in 10.0.0.0/16 so we can use another debian host with nginx on it in the same subnet:
root@home:~# ip a | grep inet
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
inet 10.0.0.101/8 brd 10.255.255.255 scope global ens18
inet6 fe80::94b0:53ff:fe08:49a6/64 scope link
inet6 2001:470:1f12:141::2/64 scope global deprecated
inet6 fe80::c0a8:65/64 scope link
Right now my other debian host is at 10.0.0.101, so we can configure nginx accordingly:
apt install nginx -y
rm /etc/nginx/sites-available/default
rm /etc/nginx/sites-enabled/default
vim /etc/nginx/sites-available/pad.void.yt.conf
Right now i named my nginx config as pad.domain.yt because i intend to host it with a TLS 1.3 certificate from letsencrypt. It doesn't matter that the previous debian host with etherpad on it only runs on http, the reverse proxying nginx will turn it into https:
upstream padbackend {
server 10.0.0.111:9001;
}
server {
listen 80;
listen [::]:80;
server_name pad.void.yt;
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name pad.void.yt;
ssl_certificate /root/.acme.sh/pad.void.yt/fullchain.cer;
ssl_trusted_certificate /root/.acme.sh/pad.void.yt/pad.void.yt.cer;
ssl_certificate_key /root/.acme.sh/pad.void.yt/pad.void.yt.key;
ssl_protocols TLSv1.3 TLSv1.2;
ssl_ciphers 'TLS13-CHACHA20-POLY1305-SHA256:TLS13-AES-256-GCM-SHA384:TLS13-AES-128-GCM-SHA256:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_session_tickets off;
ssl_ecdh_curve auto;
ssl_stapling on;
ssl_stapling_verify on;
resolver 80.67.188.188 80.67.169.40 valid=300s;
resolver_timeout 10s;
add_header X-XSS-Protection "1; mode=block"; #Cross-site scripting
add_header X-Frame-Options "SAMEORIGIN" always; #clickjacking
add_header X-Content-Type-Options nosniff; #MIME-type sniffing
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload";
location / {
proxy_pass http://padbackend;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
}
}
With this we are able to connect to our etherpad http service on port 9001, and make it so that for the end user he is connecting through port 443 (https) regardless of the initial http protocol and the weird port number. Next step is to install acme.sh to get the certificates:
wget -O - https://get.acme.sh | sh
source ~/.bashrc
#make sure that the domain name is actually working
curl ifconfig.me
ping pad.void.yt
systemctl stop nginx
acme.sh --issue --standalone -d pad.void.yt -k 4096
ln -s /etc/nginx/sites-available/pad.void.yt.conf /etc/nginx/sites-enabled/
nginx -t
systemctl start nginx
And now all that's left to do is to go and check if it is working properly:
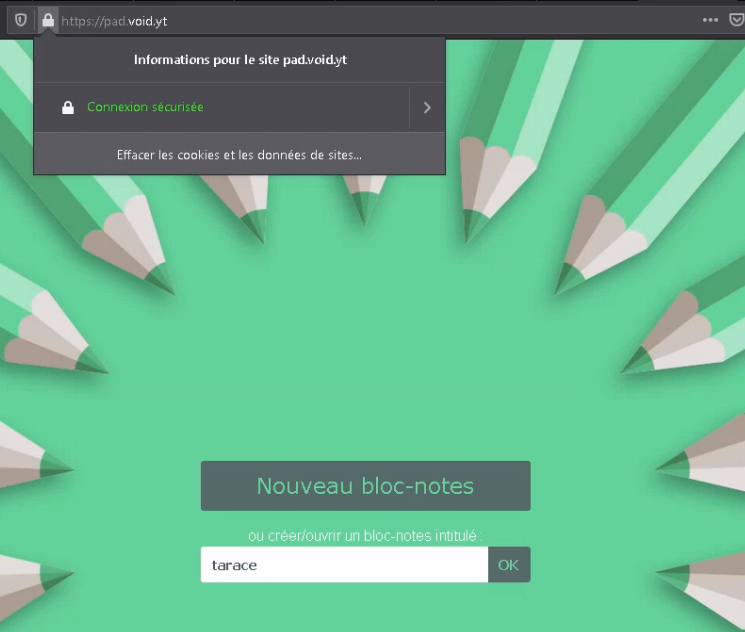
All that's needed from here is to just create a notepad (here i named it tarace)
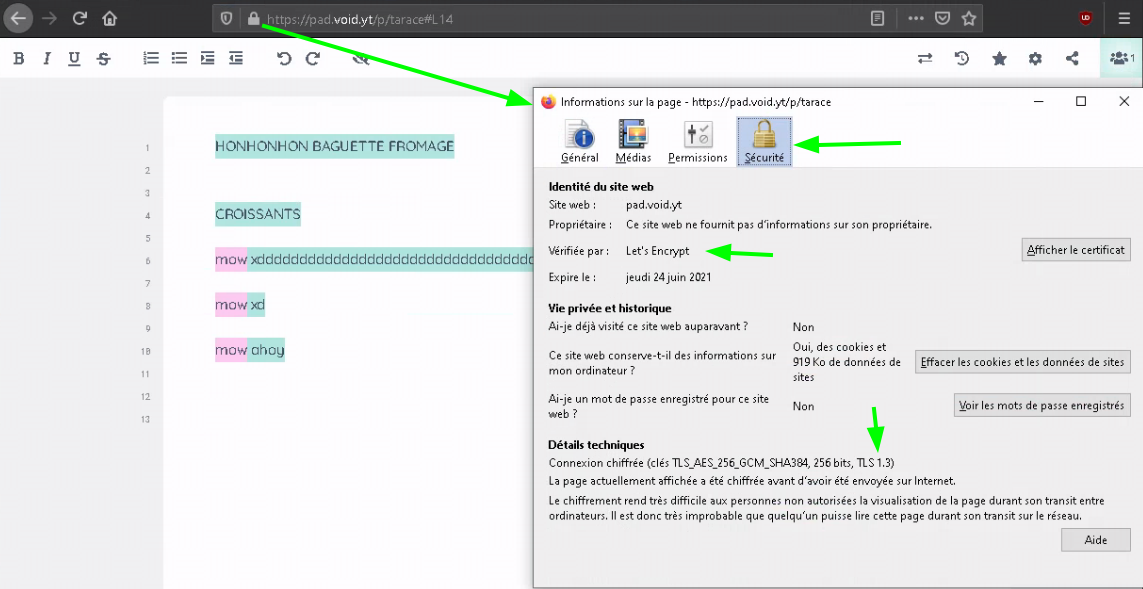
And if we give it to other people, we can let them write on it as we are writing on it.
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.