
CryptPad
CryptPad is the Zero Knowledge realtime collaborative editor. Encryption carried out in your web browser protects the data from the server, it relies on the ChainPad realtime engine.

CryptPad is the Zero Knowledge realtime collaborative editor. Encryption carried out in your web browser protects the data from the server, it relies on the ChainPad realtime engine.
We're going to install cryptpad inside of Proxmox as a debian10 CT:
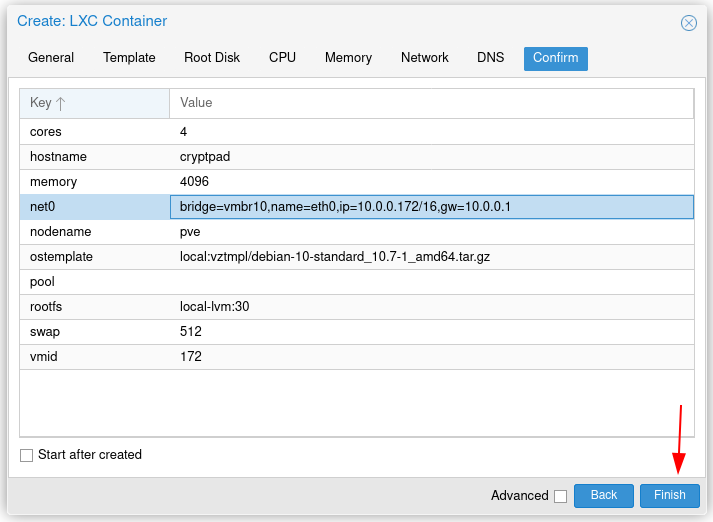
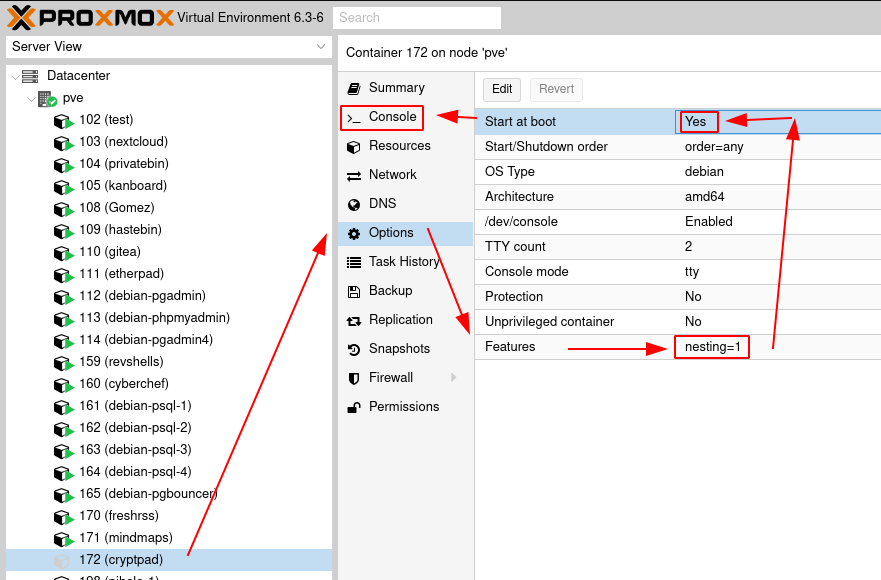
Once here, start the CT and go into the Web-based TTY console to setup key-based SSH authentication:
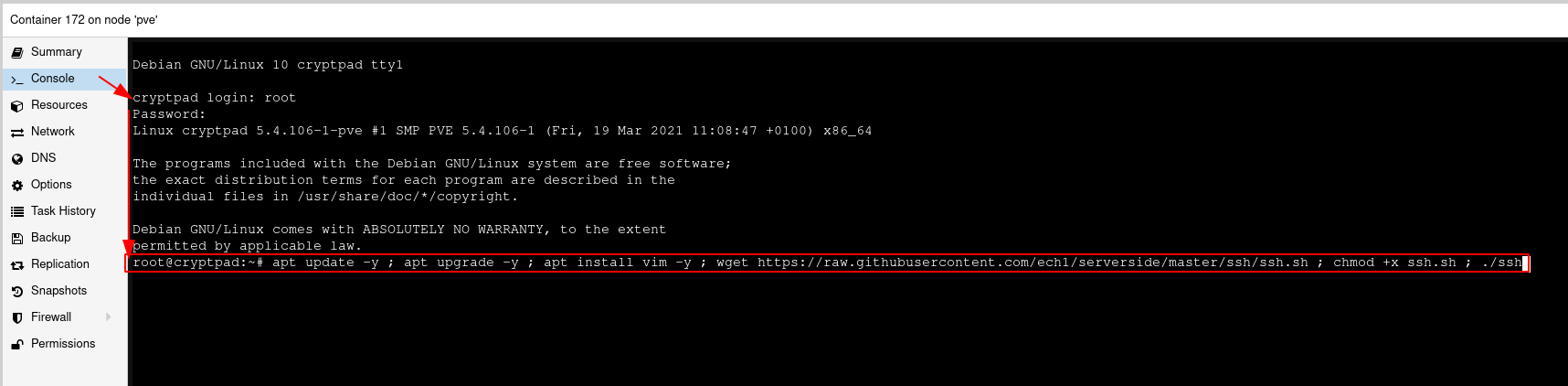
We're going to use my SSH setup script as follows:
Debian GNU/Linux 10 cryptpad tty1
cryptpad login: root
Password:
Linux cryptpad 5.4.106-1-pve #1 SMP PVE 5.4.106-1 (Fri, 19 Mar 2021 11:08:47 +0100) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@cryptpad:~# apt update -y ; apt upgrade -y ; apt install vim -y ; wget https://raw.githubusercontent.com/ech1/serverside/master/ssh/ssh.sh ; chmod +x ssh.sh ; ./ssh.sh
Generate the SSH Keys and then go get the private SSH key from port 8080:
Generating public/private ed25519 key pair.
Enter file in which to save the key (/root/.ssh/id_ed25519):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_ed25519.
Your public key has been saved in /root/.ssh/id_ed25519.pub.
The key fingerprint is:
SHA256:+5Jkmpo4NBcJBCRU48jkdYReSRzspMLW4Hp/4IHYX3Y root@cryptpad
The key's randomart image is:
+--[ED25519 256]--+
|=*o+*=o |
|=.=.o* |
|o++o=. |
| = +o. |
|oo.. . S |
|o * + o E. |
| o * = *.. |
| ..+.+ o. |
| ..oo .. |
+----[SHA256]-----+
* ssh.service - OpenBSD Secure Shell server
Loaded: loaded (/lib/systemd/system/ssh.service; enabled; vendor preset: enabled)
Active: active (running) since Thu 2021-04-15 09:40:04 UTC; 33s ago
Docs: man:sshd(8)
man:sshd_config(5)
Process: 9255 ExecStartPre=/usr/sbin/sshd -t (code=exited, status=0/SUCCESS)
Main PID: 9256 (sshd)
Tasks: 1 (limit: 7372)
Memory: 1.4M
CGroup: /system.slice/ssh.service
`-9256 /usr/sbin/sshd -D
Apr 15 09:40:04 cryptpad systemd[1]: Starting OpenBSD Secure Shell server...
Apr 15 09:40:04 cryptpad sshd[9256]: Server listening on 0.0.0.0 port 22.
Apr 15 09:40:04 cryptpad sshd[9256]: Server listening on :: port 22.
Apr 15 09:40:04 cryptpad systemd[1]: Started OpenBSD Secure Shell server.
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
inet 10.0.0.172/16 brd 10.0.255.255 scope global eth0
inet6 fe80::3800:77ff:fe37:7b68/64 scope link
[+] ON A REMOTE HOST RUN THE FOLLOWING:
[+] wget http://ip:8080/id25519 -O ~/.ssh/node.pkey
[+] chmod 600 ~/.ssh/node.pkey
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
From here you just get the private key to your local machine and ssh into the CT with it:
[ 10.0.0.10/16 ] [ /dev/pts/1 ] [~]
→ curl 10.0.0.172:8080
Directory listing for /
Directory listing for /
[ 10.0.0.10/16 ] [ /dev/pts/1 ] [~]
→ curl 10.0.0.172:8080/id_ed25519 > ~/.ssh/cryptpad
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 399 100 399 0 0 30692 0 --:--:-- --:--:-- --:--:-- 30692
[ 10.0.0.10/16 ] [ /dev/pts/1 ] [~]
→ chmod 600 ~/.ssh/cryptpad
[ 10.0.0.10/16 ] [ /dev/pts/1 ] [~]
→ ssh root@10.0.0.172 -i ~/.ssh/cryptpad
The authenticity of host '10.0.0.172 (10.0.0.172)' can't be established.
ED25519 key fingerprint is SHA256:WEQgq9oY+vNObJlpEPo+TEnABfrNhxrryDo4ZZy1xl0.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.0.172' (ED25519) to the list of known hosts.
Last login: Thu Apr 15 09:37:01 2021
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@cryptpad:~#
Now we can get started after you CTRL+C'd the python http server running from the CT's Webconsole TTY. Let's first install the dependencies required by cryptpad:
root@cryptpad:~# apt install nginx npm nodejs git curl -y
root@cryptpad:~# cd /var/www/html/
root@cryptpad:/var/www/html# git clone https://github.com/xwiki-labs/cryptpad.git
Cloning into 'cryptpad'...
remote: Enumerating objects: 97167, done.
remote: Counting objects: 100% (1695/1695), done.
remote: Compressing objects: 100% (601/601), done.
remote: Total 97167 (delta 1249), reused 1524 (delta 1091), pack-reused 95472
Receiving objects: 100% (97167/97167), 268.59 MiB | 4.94 MiB/s, done.
Resolving deltas: 100% (63585/63585), done.
Checking out files: 100% (39440/39440), done.
root@cryptpad:/var/www/html# cd cryptpad/
root@cryptpad:/var/www/html/cryptpad# ls -l
total 828
-rw-r--r-- 1 root root 272014 Apr 15 10:06 CHANGELOG.md
-rw-r--r-- 1 root root 3351 Apr 15 10:06 CODE_OF_CONDUCT.md
-rw-r--r-- 1 root root 34520 Apr 15 10:06 LICENSE
-rw-r--r-- 1 root root 44825 Apr 15 10:06 and_so_it_begins.png
-rw-r--r-- 1 root root 1441 Apr 15 10:06 bower.json
drwxr-xr-x 2 root root 4096 Apr 15 10:06 config
-rw-r--r-- 1 root root 202130 Apr 15 10:06 cryptofist.png
drwxr-xr-x 9 root root 4096 Apr 15 10:06 customize.dist
drwxr-xr-x 2 root root 4096 Apr 15 10:06 docs
drwxr-xr-x 6 root root 4096 Apr 15 10:06 lib
-rw-r--r-- 1 root root 103852 Apr 15 10:06 package-lock.json
-rw-r--r-- 1 root root 2111 Apr 15 10:06 package.json
-rw-r--r-- 1 root root 4457 Apr 15 10:06 readme.md
-rw-r--r-- 1 root root 118292 Apr 15 10:06 screenshot.png
drwxr-xr-x 4 root root 4096 Apr 15 10:06 scripts
-rw-r--r-- 1 root root 12576 Apr 15 10:06 server.js
drwxr-xr-x 33 root root 4096 Apr 15 10:06 www
once in here install bower with npm as well as the cryptpad dependencies:
root@cryptpad:/var/www/html/cryptpad# npm install -g bower
root@cryptpad:/var/www/html/cryptpad# npm install
Let it run, and once it is finished, run bower to install the other dependencies:
root@cryptpad:/var/www/html/cryptpad# bower install
root@cryptpad:/var/www/html/cryptpad# bower install
If bower fails run it again, then proceed:
root@cryptpad:/var/www/html/cryptpad# cd config
root@cryptpad:/var/www/html/cryptpad/config# ls -l
total 16
-rw-r--r-- 1 root root 13988 Apr 15 10:06 config.example.js
root@cryptpad:/var/www/html/cryptpad/config# cp config.example.js config.js
root@cryptpad:/var/www/html/cryptpad/config# vim config.js
This is the file you're going to edit later on, but for now let's simply run the server itself with node:
root@cryptpad:/var/www/html/cryptpad# node server
You can configure the administrator email (adminEmail) in your config/config.js file
m m mm mmmmm mm m mmmmm mm m mmm m
# # # ## # "# #"m # # #"m # m" " #
" #"# # # # #mmmm" # #m # # # #m # # mm #
## ##" #mm# # "m # # # # # # # # #
# # # # # " # ## mm#mm # ## "mmm" #
No 'httpSafeOrigin' provided.
Your configuration probably isn't taking advantage of all of CryptPad's security features!
This is acceptable for development, otherwise your users may be at risk.
Serving sandboxed content via port 3001.
This is probably not what you want for a production instance!
Cryptpad is customizable, see customize.dist/readme.md for details
[2021-04-15T10:36:43.125Z] server available http://127.0.0.1:3000
Now here we have a problem because the cryptpad npm server is only available on 127.0.0.1 on port 3000:
[ 10.0.0.10/16 ] [ /dev/pts/28 ] [~]
→ curl 10.0.0.172:3000
curl: (7) Failed to connect to 10.0.0.172 port 3000: Connection refused
[ 10.0.0.10/16 ] [ /dev/pts/28 ] [~]
→ ssh root@10.0.0.172 -i ~/.ssh/cryptpad
Last login: Thu Apr 15 10:00:19 2021 from 10.0.0.10
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@cryptpad:~# curl 127.0.0.1:3000 2>/dev/null | wc -l
16
Here you see the problem, so let's setup a nginx reverse proxy to access it on the network:
root@cryptpad:~# rm /etc/nginx/sites-available/default
root@cryptpad:~# rm /etc/nginx/sites-enabled/default
root@cryptpad:~# vim /etc/nginx/sites-available/cryptpad.conf
upstream backend {
server 127.0.0.1:3000;
}
server {
listen 80;
listen [::]:80;
location / {
proxy_pass http://backend;
proxy_http_version 1.1;
}
}
:wq
root@cryptpad:~# ln -s /etc/nginx/sites-available/cryptpad.conf /etc/nginx/sites-enabled/
root@cryptpad:~# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
root@cryptpad:~# nginx -s reload
root@cryptpad:~# cd /var/www/html/cryptpad/
root@cryptpad:/var/www/html/cryptpad# ls
CHANGELOG.md and_so_it_begins.png config data lib package.json scripts
CODE_OF_CONDUCT.md blob cryptofist.png datastore node_modules readme.md server.js
LICENSE bower.json customize.dist docs package-lock.json screenshot.png www
root@cryptpad:/var/www/html/cryptpad# node server
now try to access your website again, this time through nginx's port 80:
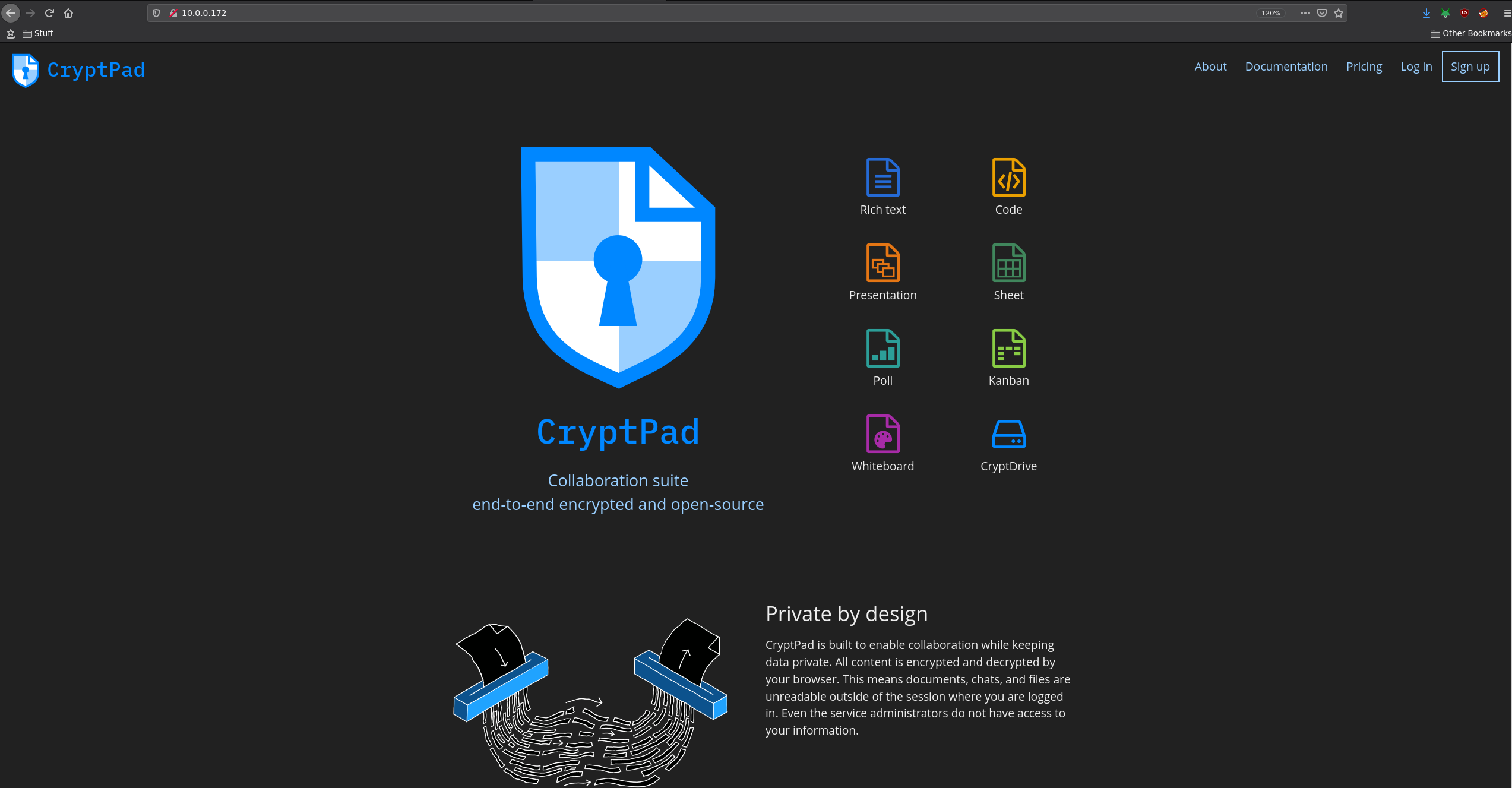
And that's it! We have installed a default instance of cryptpad.
First things first, let's configure our cryptpad instance:
[ 10.0.0.10/16 ] [ /dev/pts/28 ] [~]
→ base64 /dev/urandom
QEGWX7d7xoFZVTXhPpqc0hBOhgsH4Sh8+s5GTrOVLLWYWAreu8HQ7AfieS0o+mD3JqffsIpaxjPH
LsaMHvAf3Tlvw44DIMCu7TnLpGhMZOcAnfKQ6I7xWxC7PPJAj9qGsSHqxhTsOx29U1tJaFNZgsnF
root@cryptpad:/var/www/html/cryptpad/config# vim config.js
[...]
httpUnsafeOrigin: 'http://localhost:3000',
[...]
httpSafeOrigin: "https://cryptpad.void.yt",
[...]
adminKeys: [
"[nothing@cryptpad.void.yt/YZgXQxKR0Rcb6r6CmxHPdAGLVludrAF2lEnkbRANDOMx1vVOo=]",
],
[...]
adminEmail: 'nothing@void.yt',
defaultStorageLimit: 50 * 1024 * 1024,
inactiveTime: 90, // days
archiveRetentionTime: 15,
accountRetentionTime: 365,
disableIntegratedEviction: true,
[...]
:wq
Now once that's done, we're going to create the systemd service file that is going to run the node server command for us
root@cryptpad:/var/www/html/cryptpad/config# vim /etc/systemd/system/cryptpad.service
[Unit]
Description=Cryptpad service
After=network.target
After=systemd-user-sessions.service
After=network-online.target
[Service]
Type=simple
WorkingDirectory=/var/www/html/cryptpad/
ExecStart=node server
Restart=always
RestartSec=10
KillMode=process
[Install]
WantedBy=multi-user.target
:wq
root@cryptpad:/var/www/html/cryptpad/config# systemctl daemon-reload
root@cryptpad:/var/www/html/cryptpad/config# systemctl enable --now cryptpad
Created symlink /etc/systemd/system/multi-user.target.wants/cryptpad.service → /etc/systemd/system/cryptpad.service.
Once that's done, we should be able to access our cryptpad instance as we did earlier:
root@cryptpad:/var/www/html/cryptpad/config# systemctl status cryptpad
● cryptpad.service - Cryptpad service
Loaded: loaded (/etc/systemd/system/cryptpad.service; enabled; vendor preset: enabled)
Active: active (running) since Thu 2021-04-15 11:57:08 UTC; 1min 7s ago
Main PID: 19351 (node)
Tasks: 55 (limit: 7372)
Memory: 88.6M
CGroup: /system.slice/cryptpad.service
├─19351 /usr/bin/node server
├─19363 /usr/bin/node lib/workers/db-worker
├─19364 /usr/bin/node lib/workers/db-worker
├─19365 /usr/bin/node lib/workers/db-worker
└─19366 /usr/bin/node lib/workers/db-worker
Apr 15 11:57:08 cryptpad systemd[1]: Started Cryptpad service.
Apr 15 11:57:10 cryptpad node[19351]: Cryptpad is customizable, see customize.dist/readme.md for details
Apr 15 11:57:10 cryptpad node[19351]: [2021-04-15T11:57:10.177Z] server available http://127.0.0.1:3000
root@cryptpad:/var/www/html/cryptpad/config# curl 10.0.0.172 2>/dev/null | wc -l
16
Now that's done and we know it's working, we're going to setup the reverse nginx proxy instance at 10.0.0.101 to make sure we are able to reach our cryptpad node 10.0.0.172:3000 via the domain name cryptpad.void.yt. Let's first edit the config.js file to be able to access it:
root@cryptpad:/var/www/html/cryptpad# cd config/
root@cryptpad:/var/www/html/cryptpad/config# vim config.js
[...]
httpUnsafeOrigin: 'http://10.0.0.172:3000',
[...]
httpAddress: '10.0.0.172',
[...]
:wq
root@cryptpad:/var/www/html/cryptpad/config# systemctl stop nginx
root@cryptpad:/var/www/html/cryptpad/config# systemctl disable nginx
Synchronizing state of nginx.service with SysV service script with /lib/systemd/systemd-sysv-install.
Executing: /lib/systemd/systemd-sysv-install disable nginx
Removed /etc/systemd/system/multi-user.target.wants/nginx.service.
root@cryptpad:/var/www/html/cryptpad/config# systemctl restart cryptpad
root@cryptpad:/var/www/html/cryptpad/config# systemctl status cryptpad
● cryptpad.service - Cryptpad service
Loaded: loaded (/etc/systemd/system/cryptpad.service; enabled; vendor preset: enabled)
Active: active (running) since Thu 2021-04-15 12:39:41 UTC; 5s ago
Main PID: 19761 (node)
Tasks: 55 (limit: 7372)
Memory: 85.4M
CGroup: /system.slice/cryptpad.service
├─19761 /usr/bin/node server
├─19773 /usr/bin/node lib/workers/db-worker
├─19774 /usr/bin/node lib/workers/db-worker
├─19775 /usr/bin/node lib/workers/db-worker
└─19781 /usr/bin/node lib/workers/db-worker
Apr 15 12:39:41 cryptpad systemd[1]: Started Cryptpad service.
Apr 15 12:39:43 cryptpad node[19761]: Cryptpad is customizable, see customize.dist/readme.md for details
Apr 15 12:39:43 cryptpad node[19761]: [2021-04-15T12:39:43.460Z] server available http://10.0.0.172:3000
Then we're going to setup the reverse nginx proxy file following cryptpad's documentation:
[ 10.0.0.10/16 ] [ /dev/pts/33 ] [~]
→ ssh root@10.0.0.101
root@10.0.0.101's password:
Linux home 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Apr 15 11:10:38 2021 from 10.0.0.10
root@home:~# cd /var/www/void.yt/config/
root@home:/var/www/void.yt/config# cp test.void.yt.conf cryptpad.void.yt
root@home:/var/www/void.yt/config# vim cryptpad.void.yt
root@home:/var/www/void.yt/config# cp cryptpad.void.yt /etc/nginx/sites-available/cryptpad.void.yt
root@home:/var/www/void.yt/config# vim /etc/nginx/sites-available/cryptpad.void.yt
upstream cryptbackend {
server 10.0.0.172:3000;
}
server {
listen 80;
listen [::]:80;
server_name cryptpad.void.yt;
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name cryptpad.void.yt;
ssl_certificate /root/.acme.sh/cryptpad.void.yt/fullchain.cer;
ssl_trusted_certificate /root/.acme.sh/cryptpad.void.yt/cryptpad.void.yt.cer;
ssl_certificate_key /root/.acme.sh/cryptpad.void.yt/cryptpad.void.yt.key;
ssl_protocols TLSv1.3 TLSv1.2;
ssl_ciphers 'TLS13-CHACHA20-POLY1305-SHA256:TLS13-AES-256-GCM-SHA384:TLS13-AES-128-GCM-SHA256:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_session_tickets off;
ssl_ecdh_curve auto;
ssl_stapling on;
ssl_stapling_verify on;
resolver 80.67.188.188 80.67.169.40 valid=300s;
resolver_timeout 10s;
add_header X-XSS-Protection "1; mode=block"; #Cross-site scripting
add_header X-Frame-Options "SAMEORIGIN" always; #clickjacking
add_header X-Content-Type-Options nosniff; #MIME-type sniffing
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload";
add_header Access-Control-Allow-Origin "*";
location / {
proxy_pass http://cryptbackend;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
}
}
:wq
Once that's done, disable nginx and use acme.sh to get your LetsEncrypt TLS certificates
root@home:/var/www/void.yt/config# ln -s /etc/nginx/sites-available/cryptpad.void.yt /etc/nginx/sites-enabled/
root@home:/var/www/void.yt/config# systemctl stop nginx
root@home:/var/www/void.yt/config# acme.sh --issue --standalone -d cryptpad.void.yt -k 4096
root@home:/var/www/void.yt/config# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
root@home:/var/www/void.yt/config# systemctl start nginx
Once that's done, go to your web browser and see the following result:
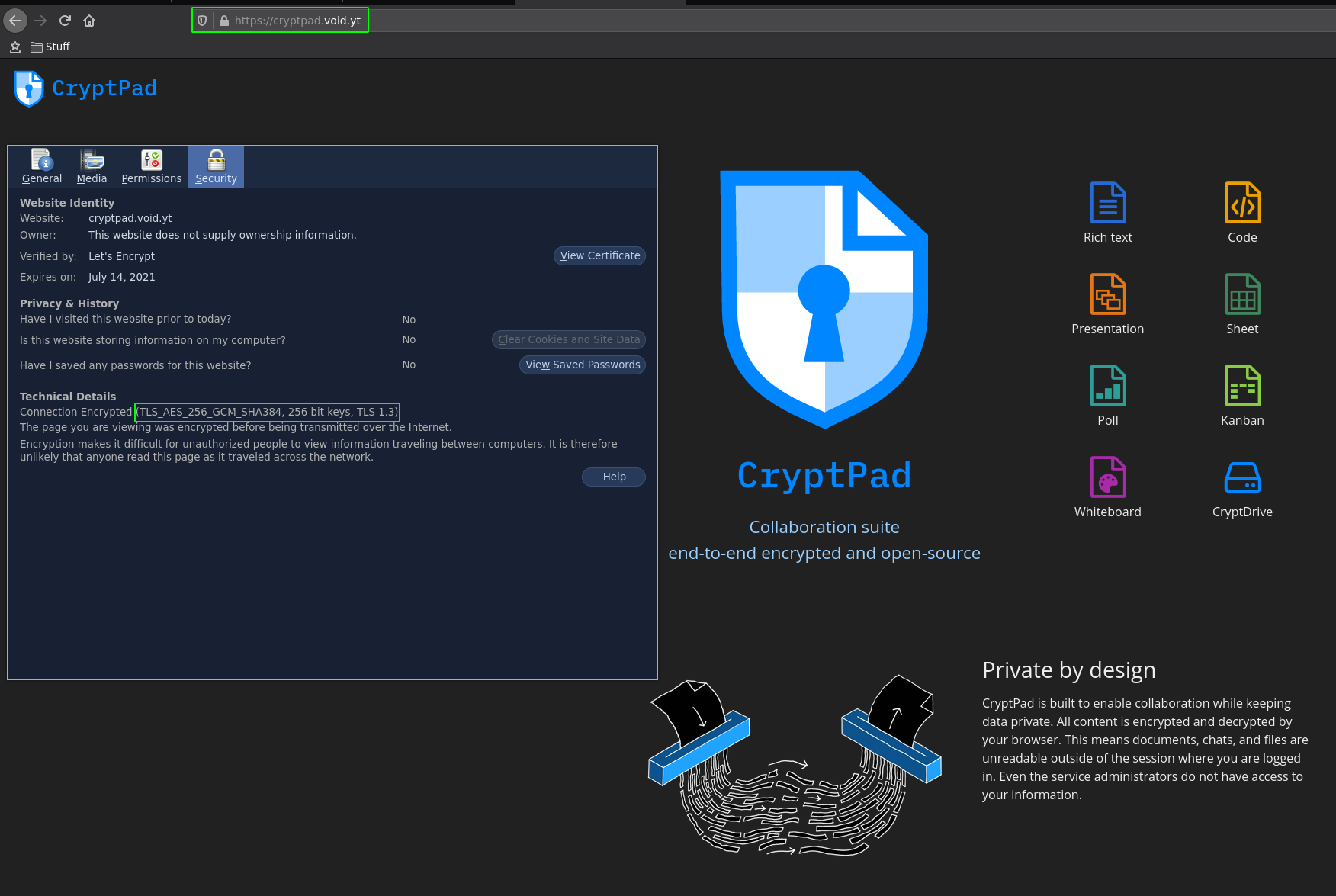
Here you can see that we get HTTPS with LetsEncrypt's TLS1.3 Certificates. Let's create an account:
Let's create an account:
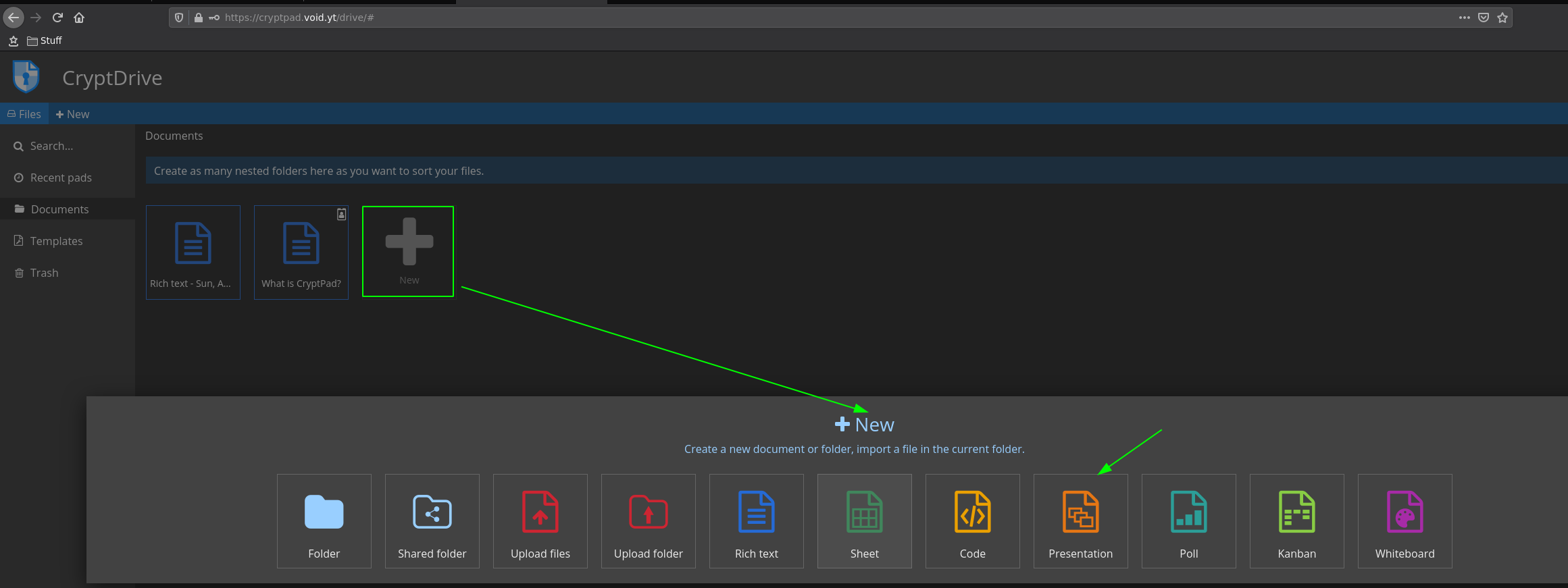
Once your account is created, you can create any type of documents you want:
So for instance let's create a Slide that expires in 1 hours and has a password:
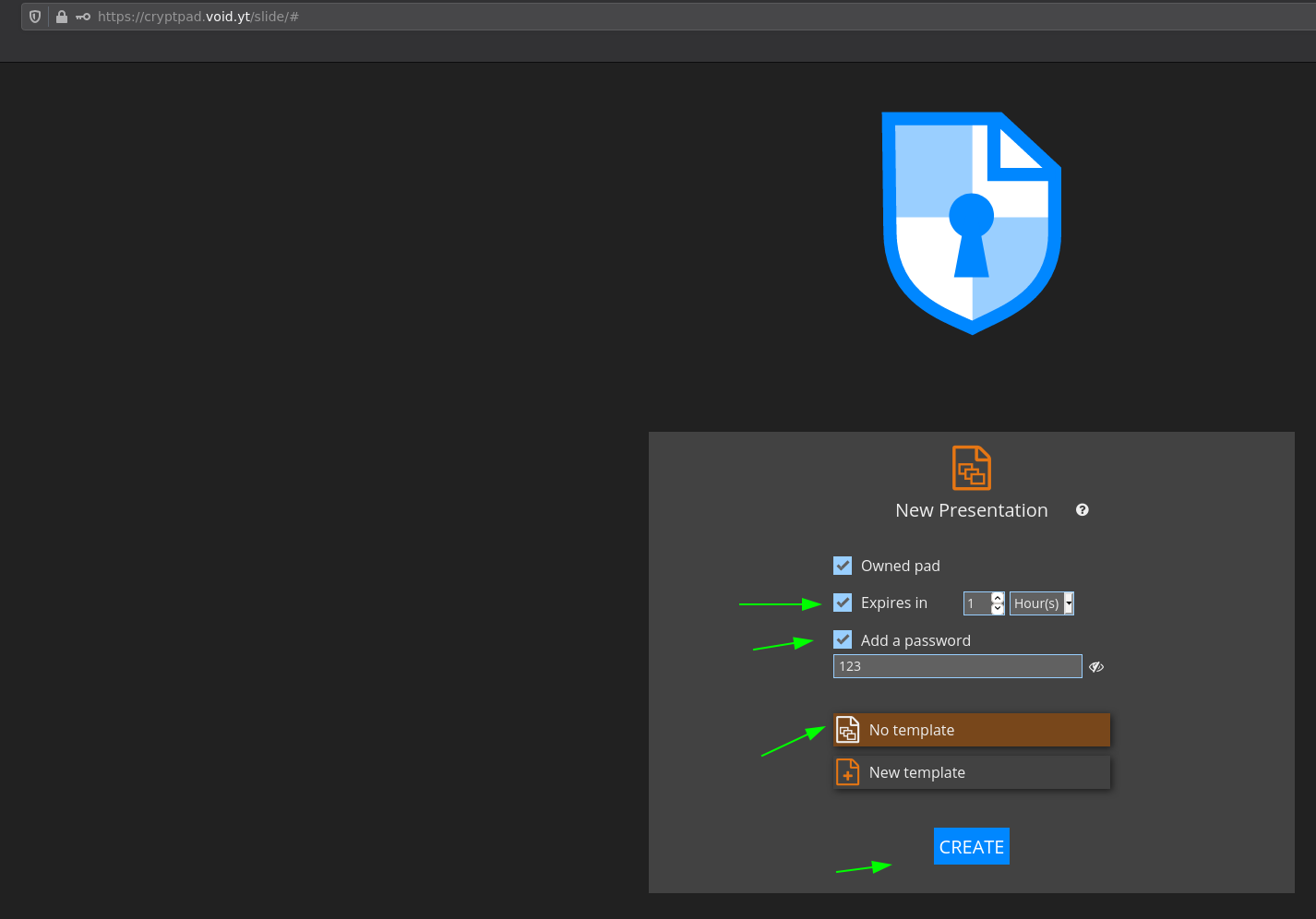
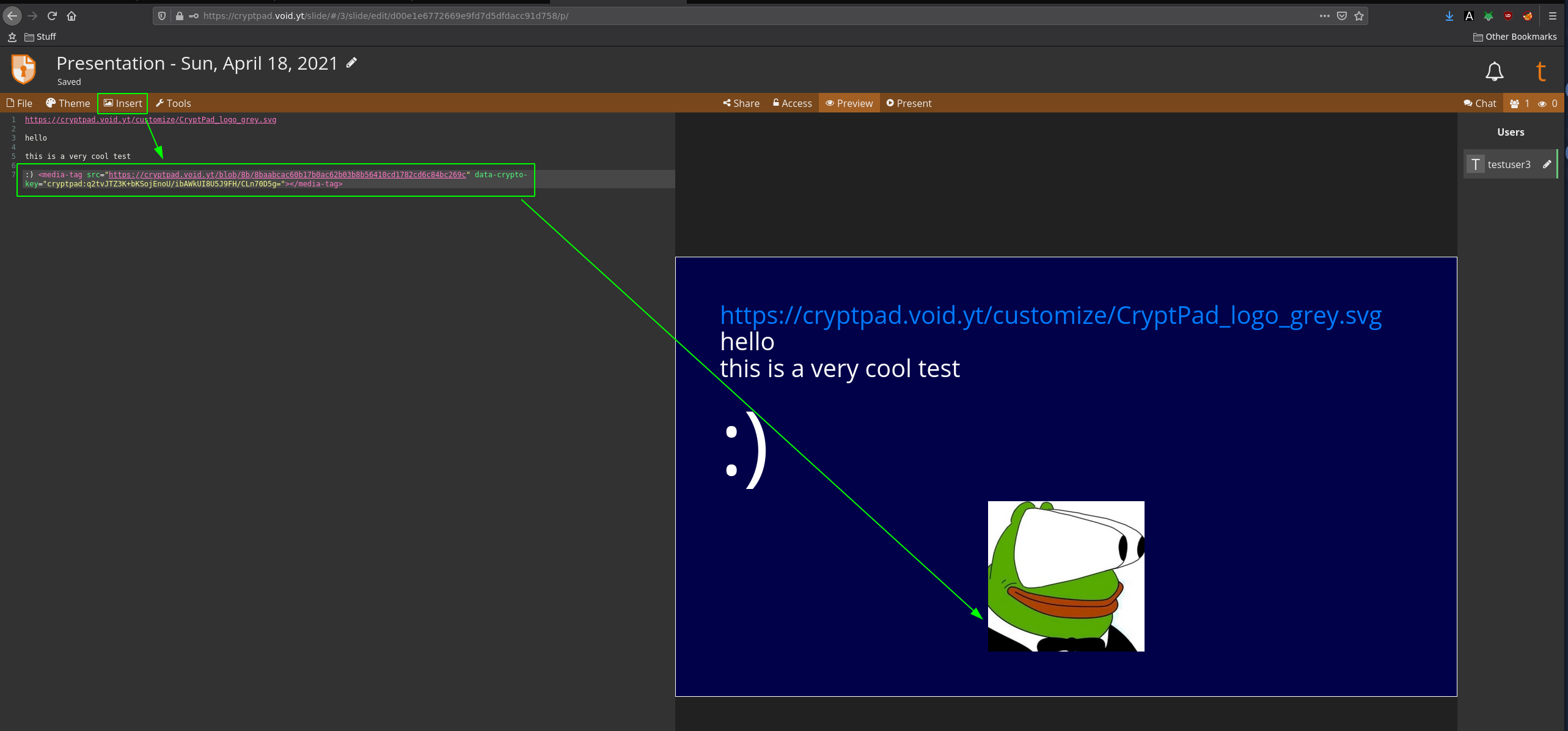
One of cryptpad's coolest features is to be able to collaborate on the same files thanks to the sharing feature:
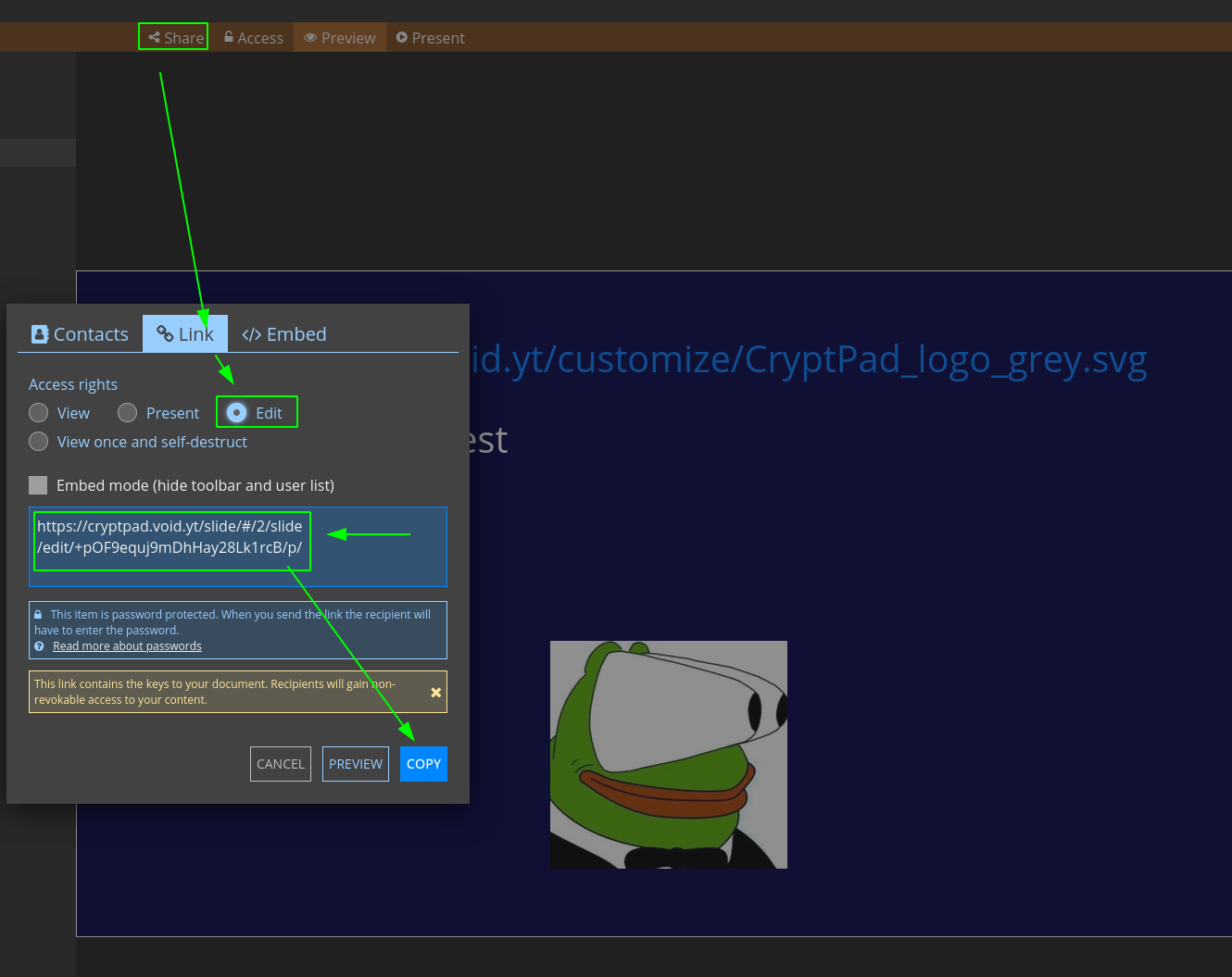
You can just give the link to someone and they will be able to view or edit your file after clicking on your link. If you set a pssword like i did, they will need to type in the password (here it's 123) to be able to enter. If you disconnect however, you need to clear the cache from your browser (CTRL+F5) because Cryptpad stores data in the browser cache. Only after clearing your cache can you use cryptpad as the anonymous user once again.
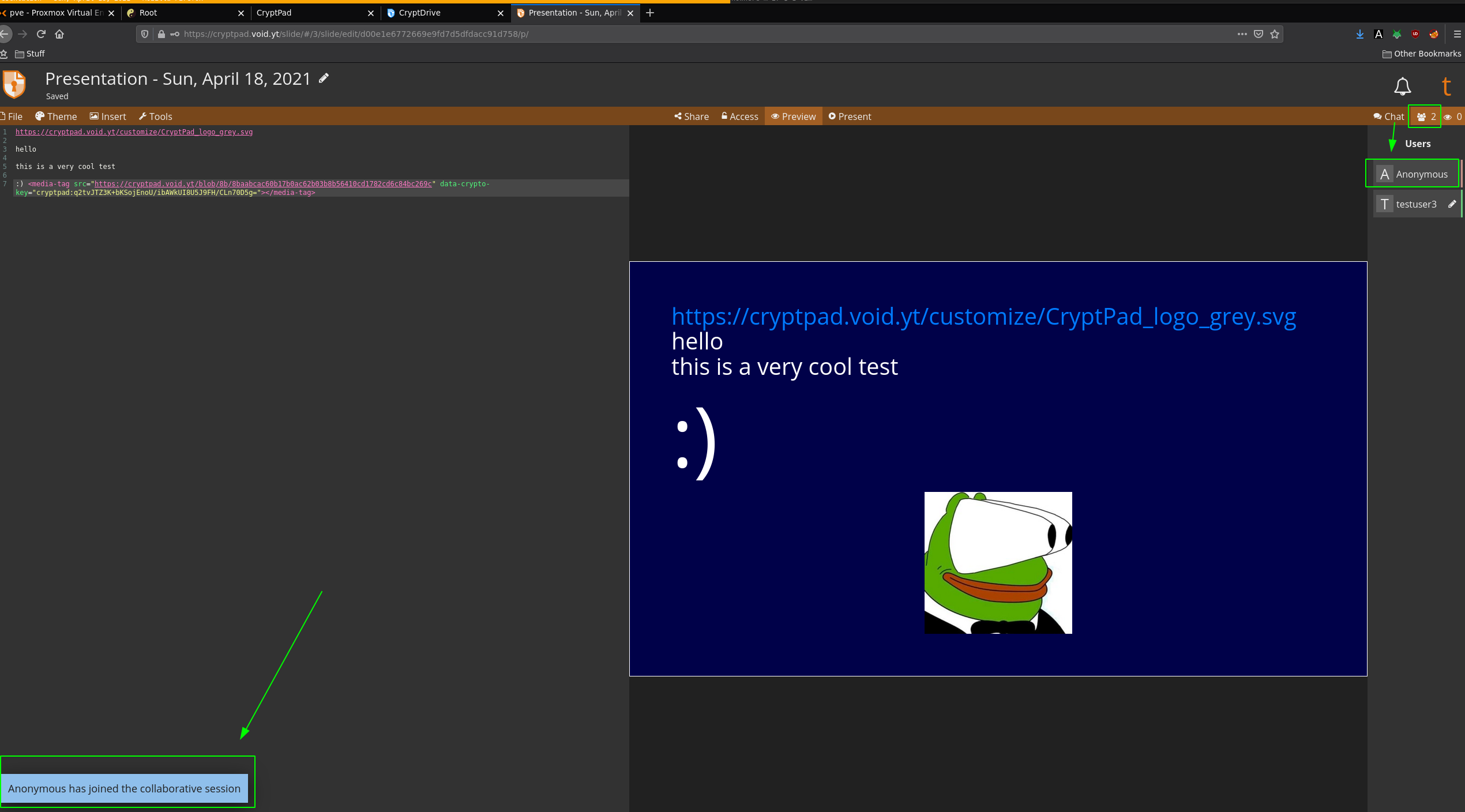
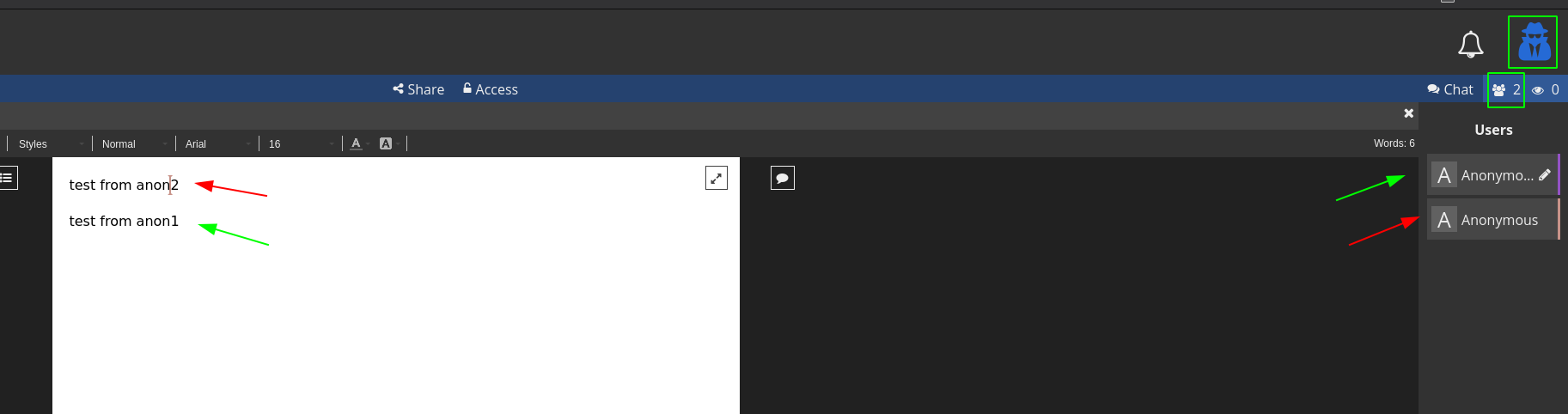
And there you go! You can also collaborate on a cryptpad instance as 2 anonymous users.
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.